Vulnerability Management Plan Template
Here are some of the images for Vulnerability Management Plan Template that we found in our website database.

Enterprise Risk Management Plan Template
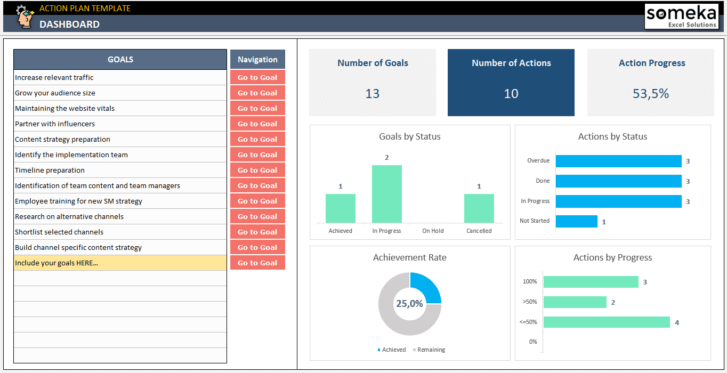
Action Plan Excel Template Free Download

Enterprise Risk Management Report Template Sample Design Templates Riset
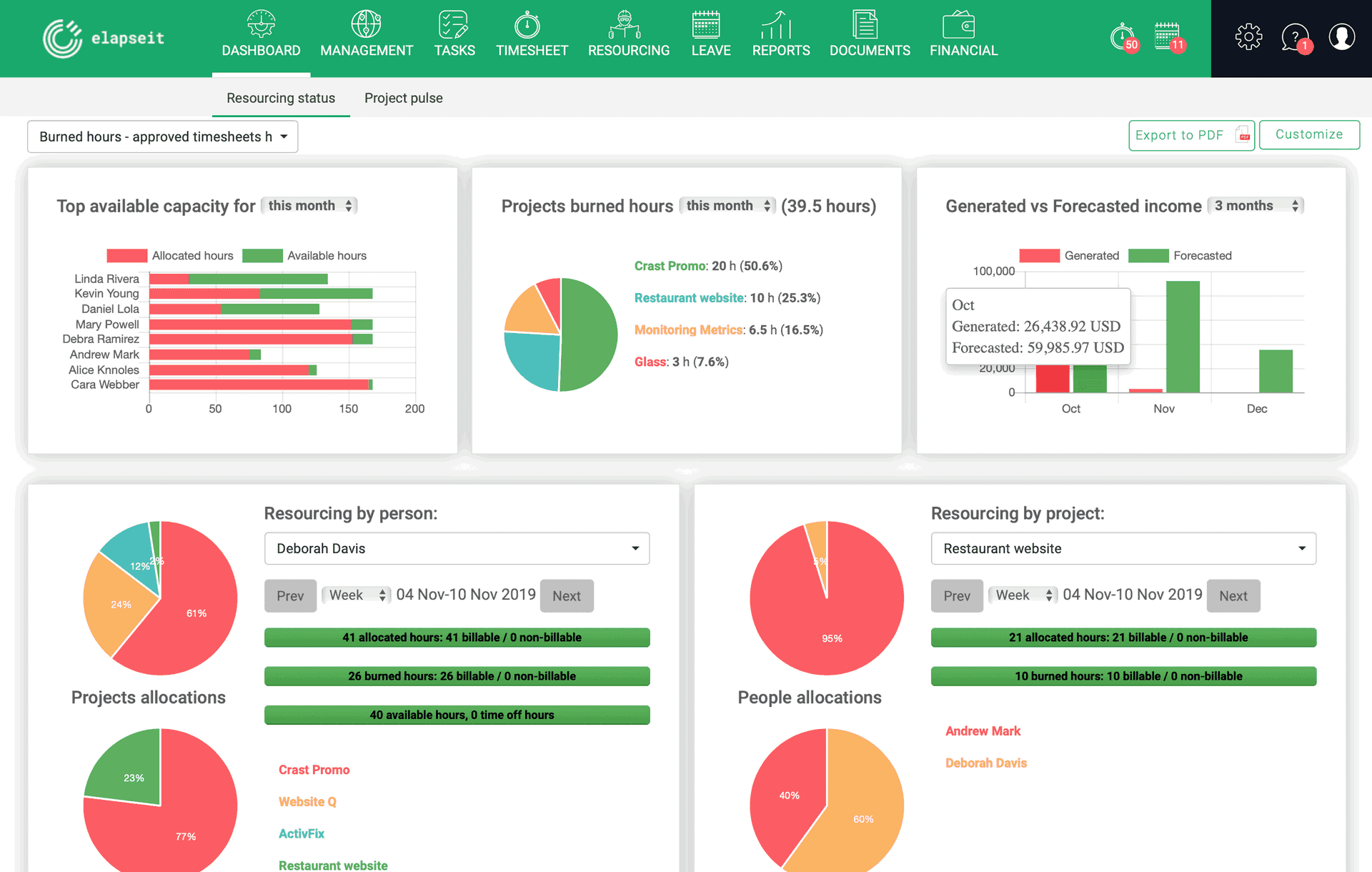
Essential Report Types in Project Management elapseit
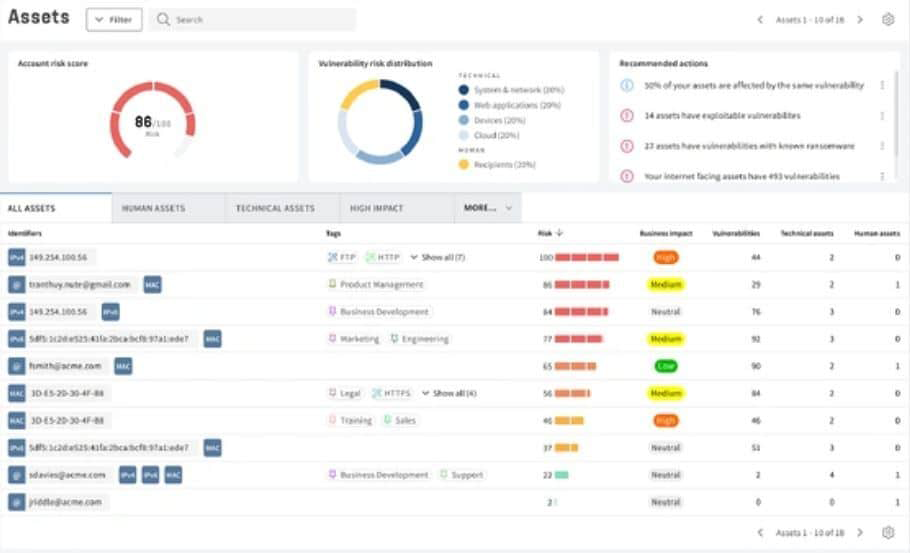
6 Best Vulnerability Management Tools Compared

Treva Bootstrap Admin Template and UI KIT CodedThemes
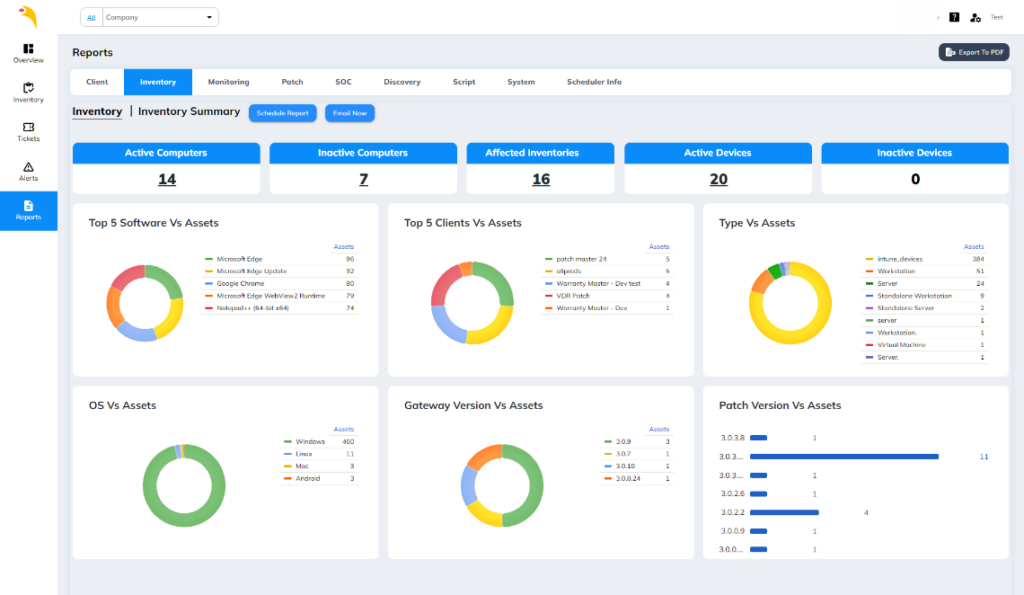
Asset Management Beakops
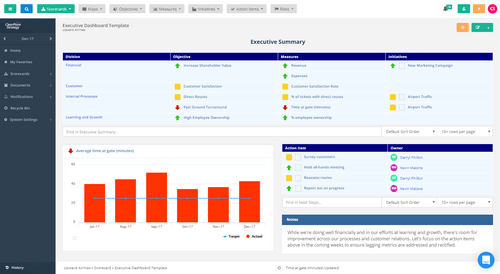
Executive Dashboard Template ClearPoint Strategy
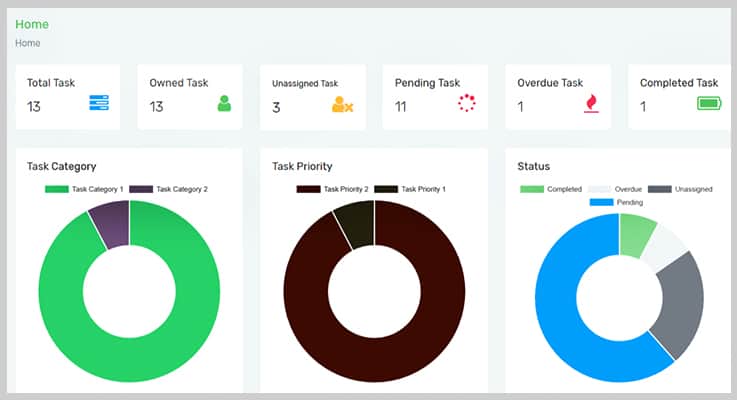
5 Best Task Management PHP Script 2022 FormGet
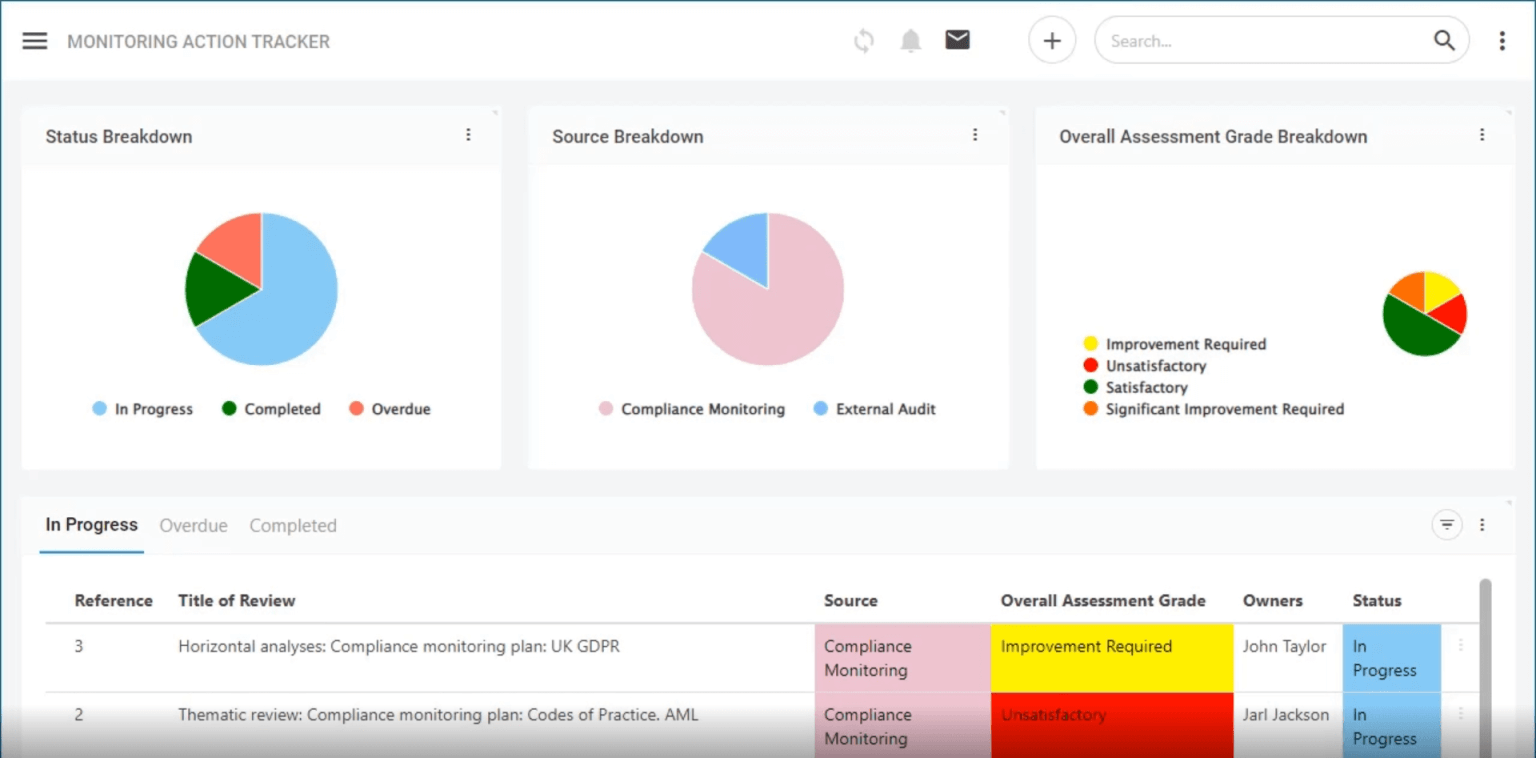
Should You Be Using Spreadsheets for GRC and Audit? Symbiant

Should You Be Using Spreadsheets for GRC and Audit? Symbiant
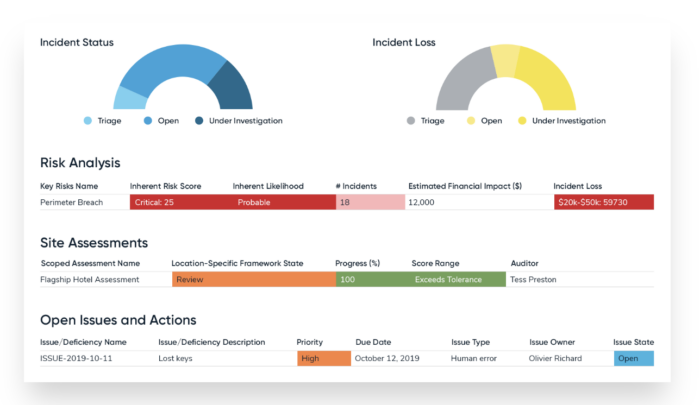
15 Best Risk Management Software 2025 Risk Management Tools
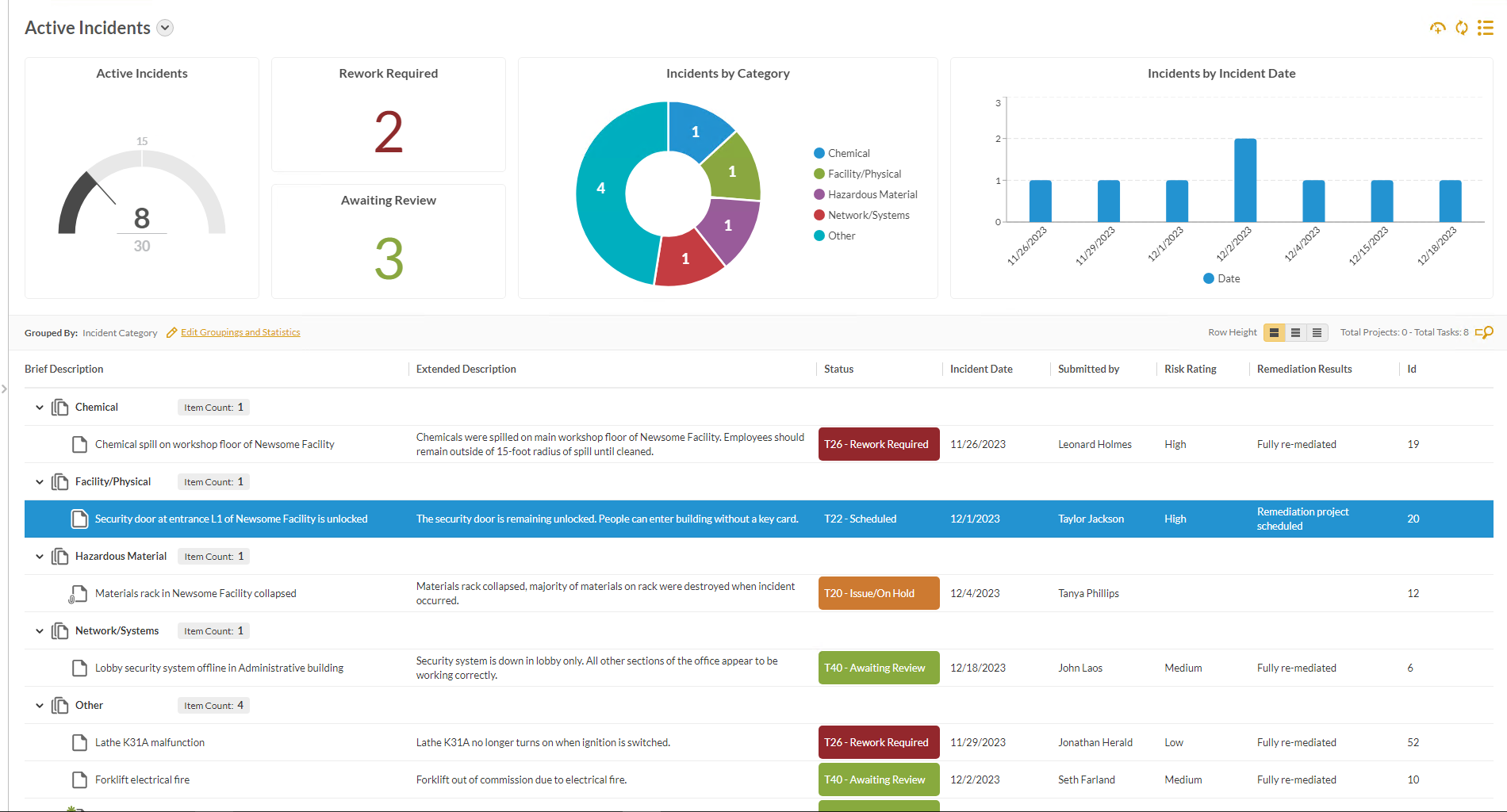
Incident Tracking Template HighGear
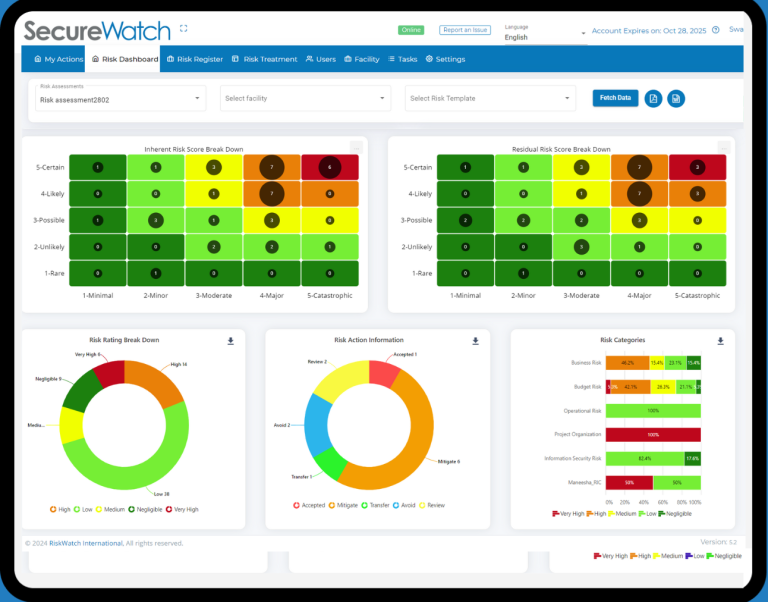
Best Risk Management Software RiskWatch

All you need to know about project portfolio reports Nordantech
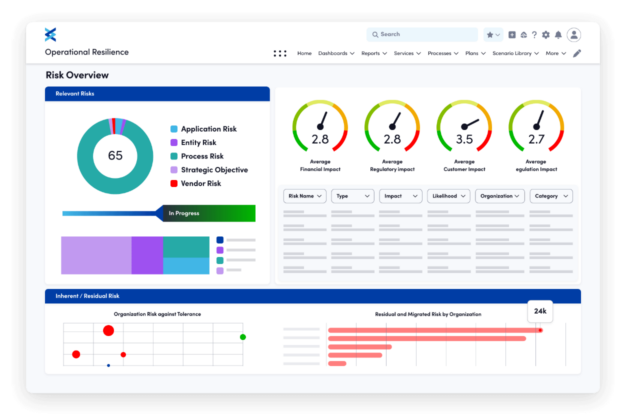
Third Party Risk Management Software Fusion Risk Management
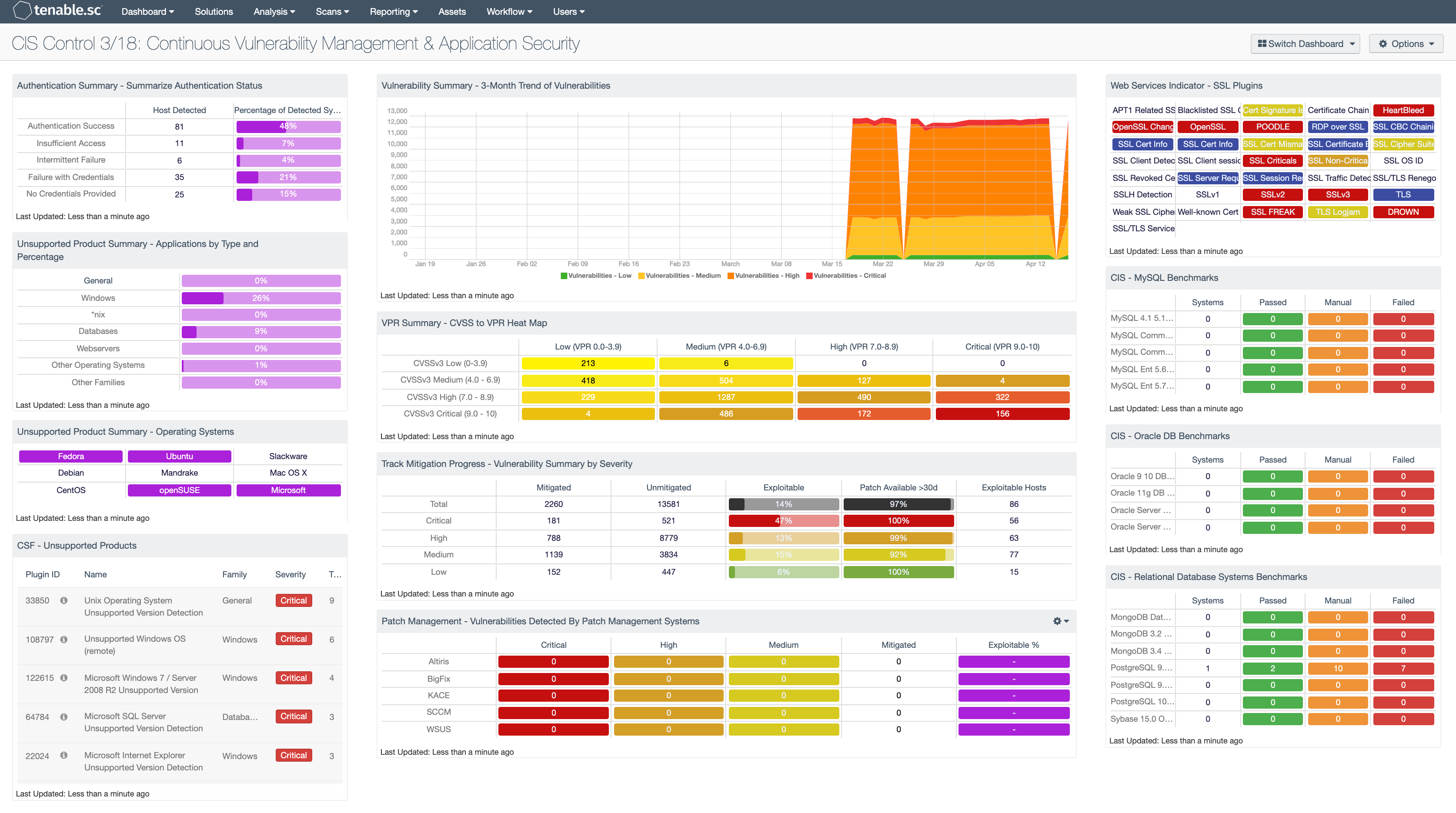
CIS Control 3/18: Continuous Vulnerability Management Application
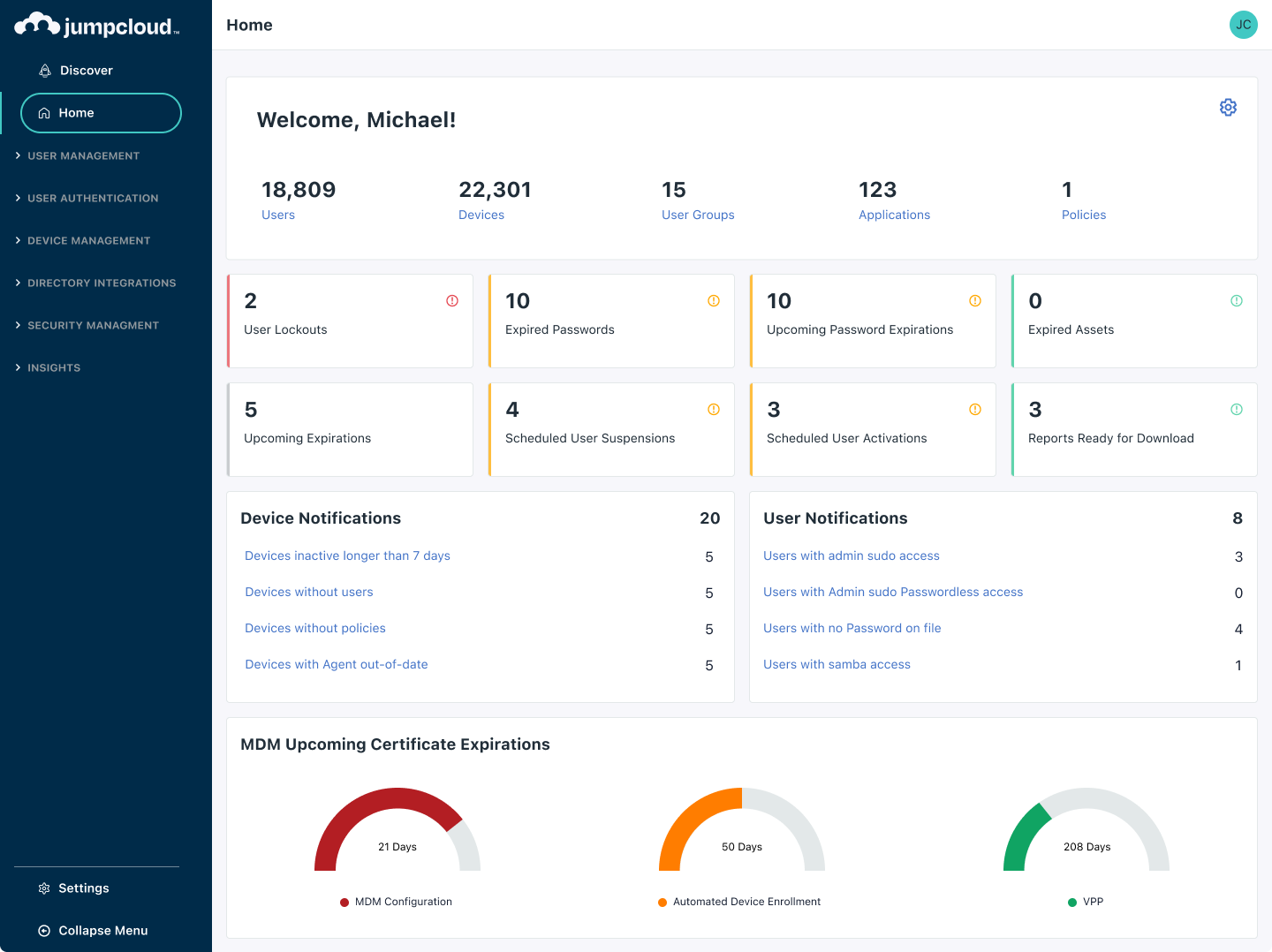
User Lifecycle Management: Strategies and 11 Essential Tools Esevel
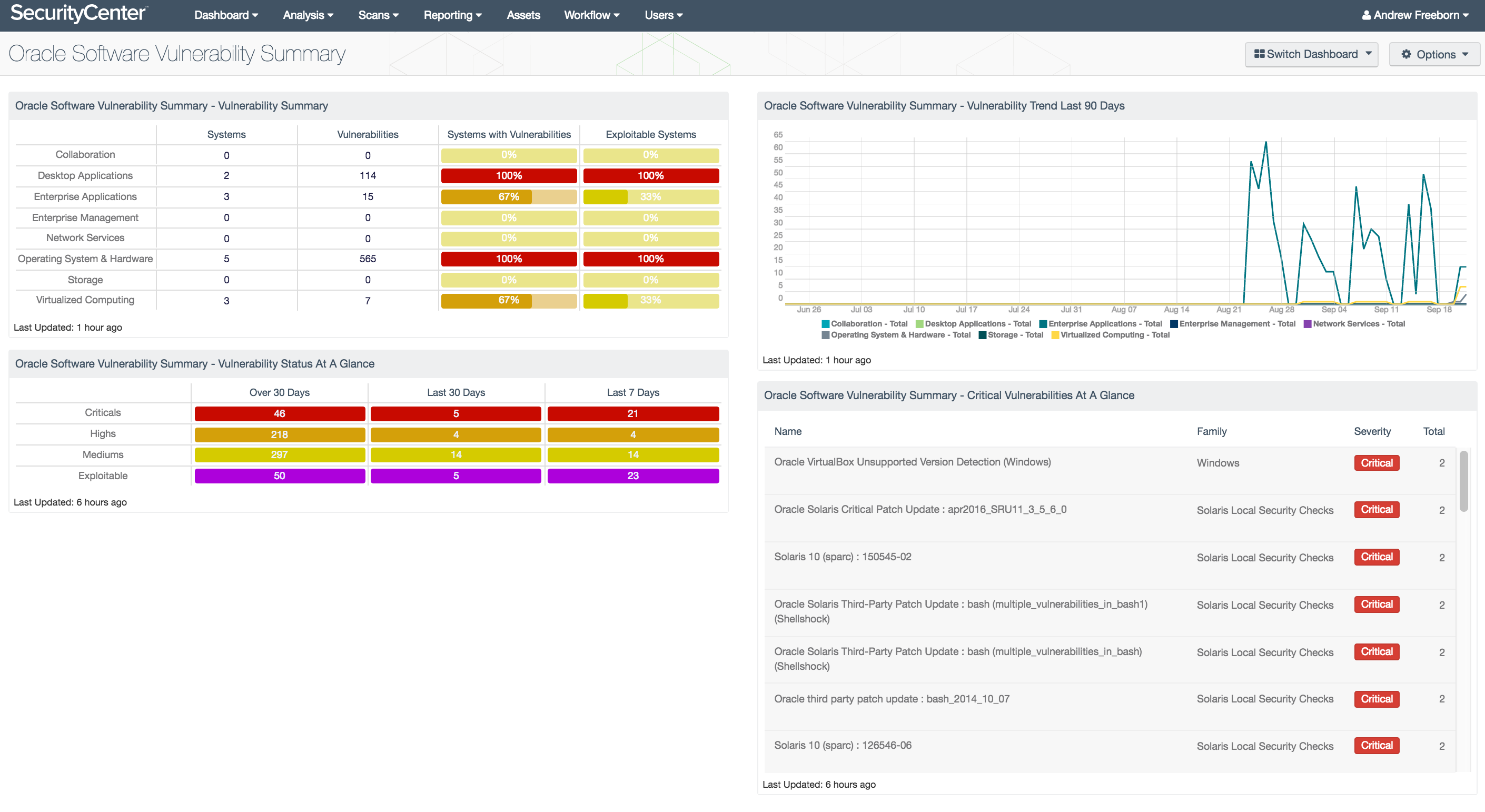
Oracle Software Vulnerability Summary SC Dashboard Tenable®

Building Management System Dashboard by Swathi Kirthyvasan for
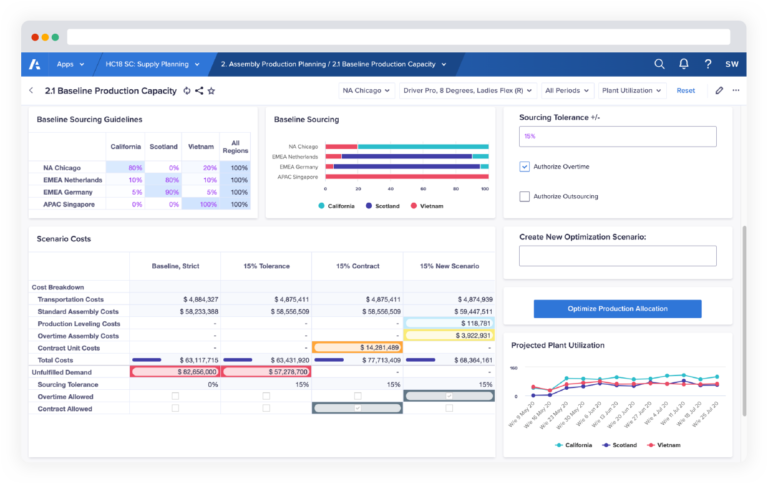
Supply chain management

Threat Stack s centralized cybersecurity vision attracts $45M in
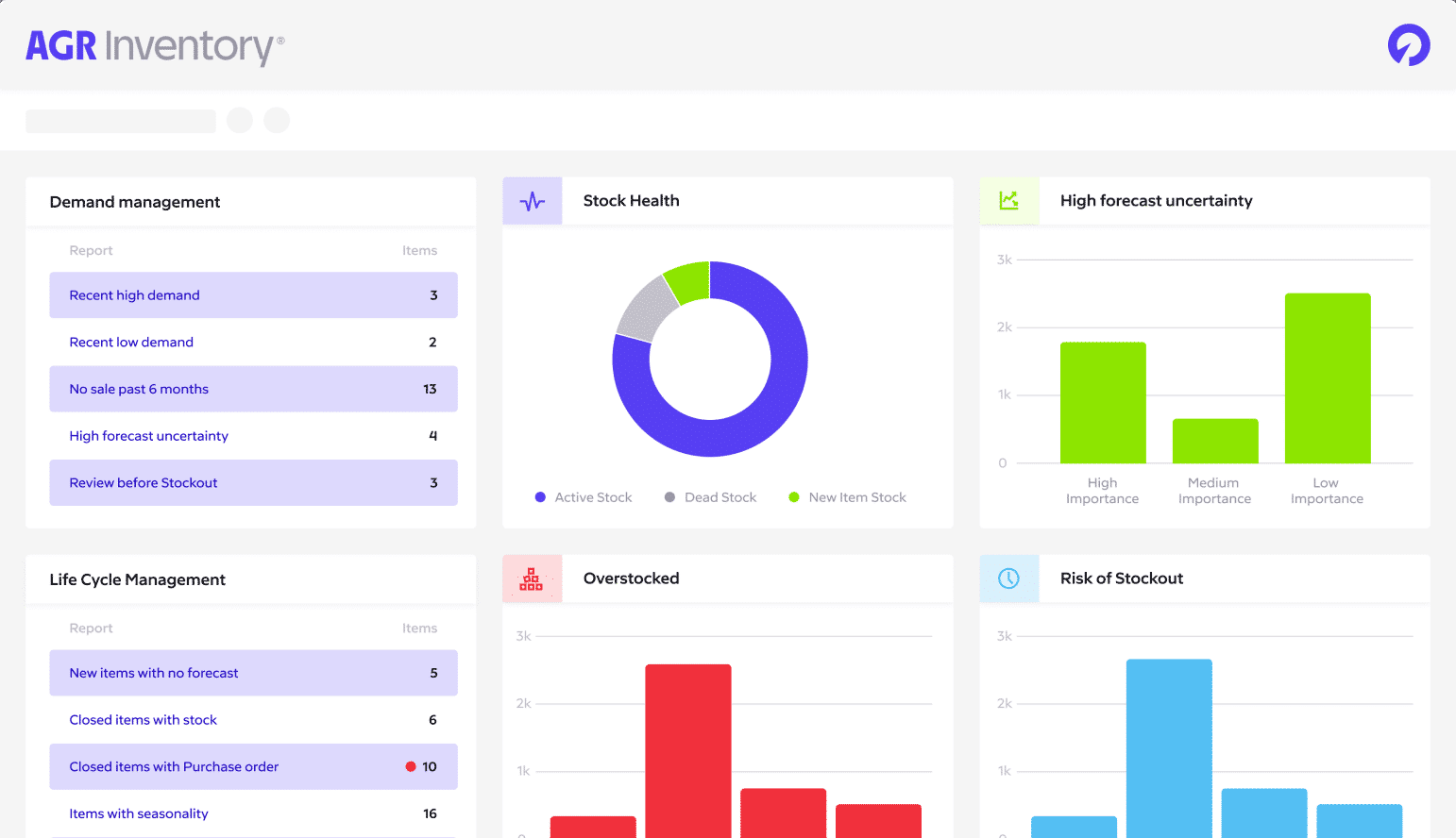
Inventory Management Software AGR Inventory
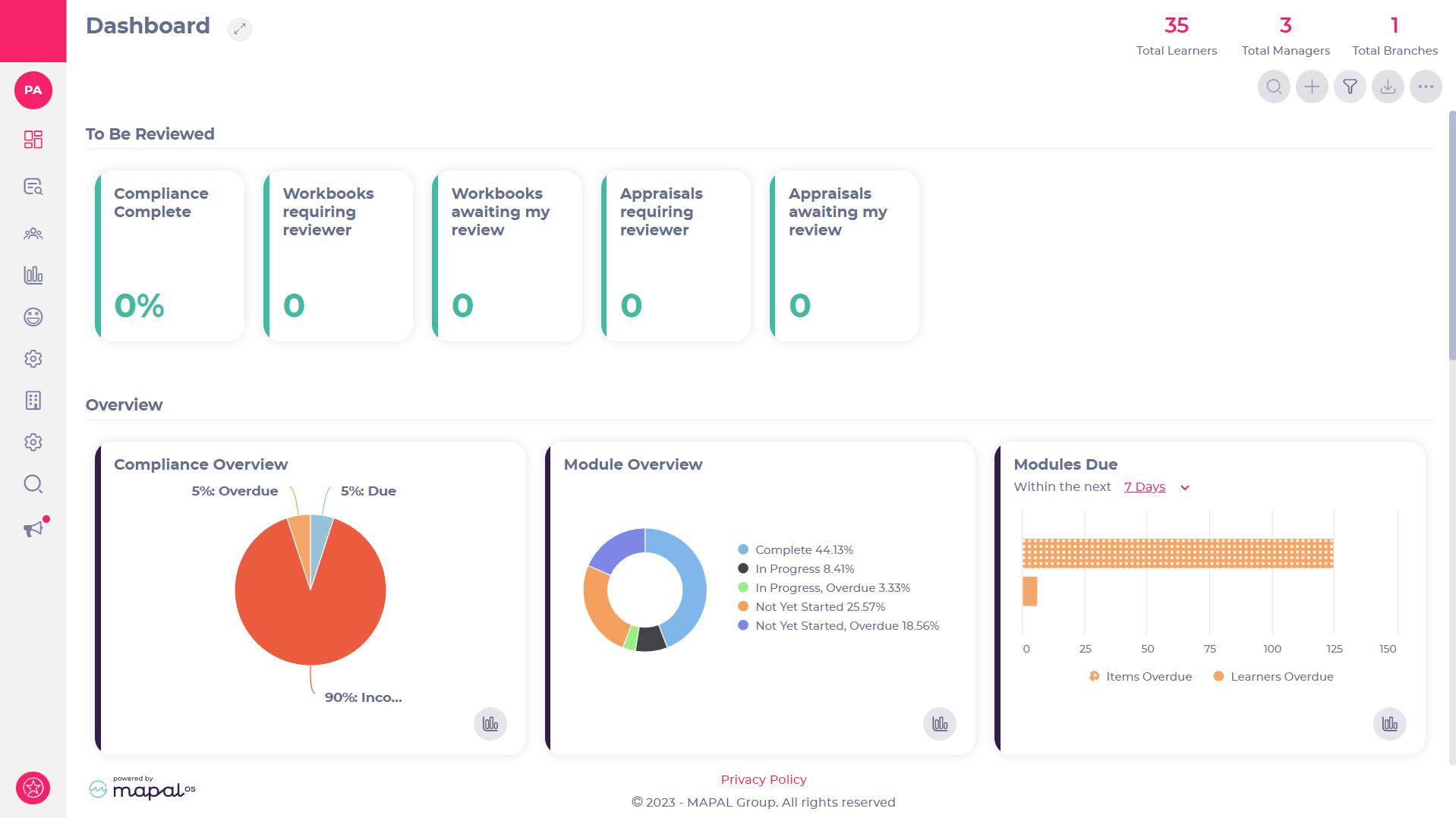
Access the Flow Management System as a training manager Knowledge Base

Carbon Labelling for Food Kafoodle

Enterprise management system isorobot E SPIN Group

Enterprise management system isorobot E SPIN Group

Arqflow Connect Collaborate Control

Operational Resilience Software Solution MetricStream

10 Best Endpoint Management Tools for 2024
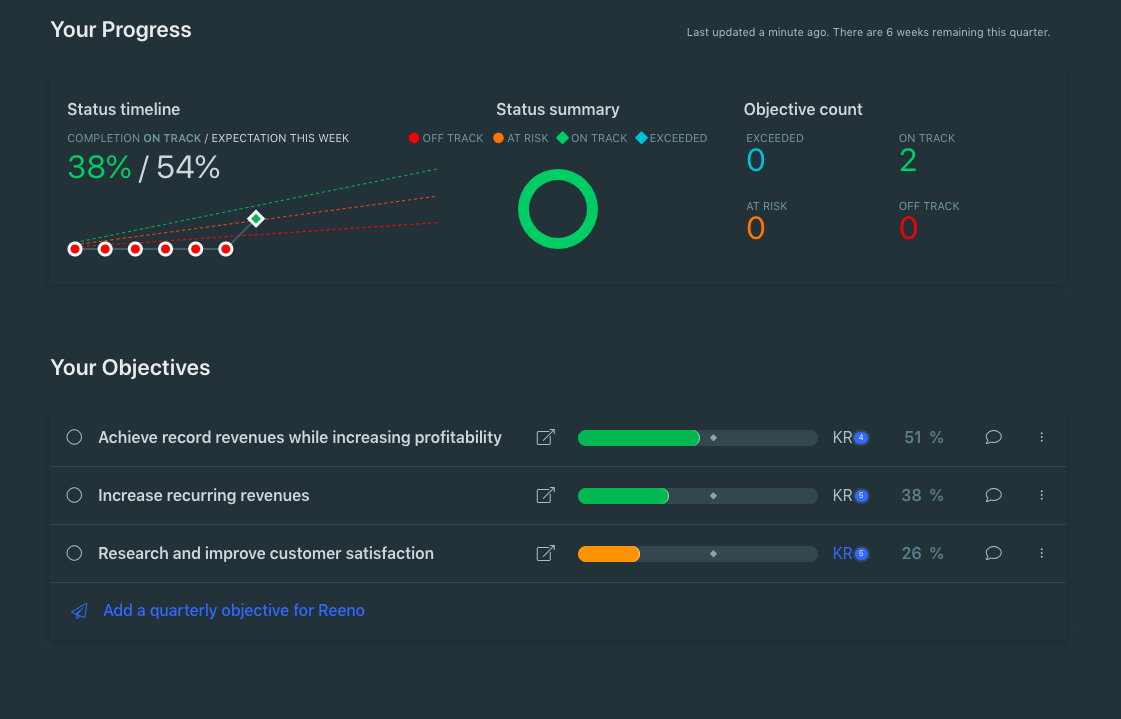
There is More to Know About the Dark Mode Trend
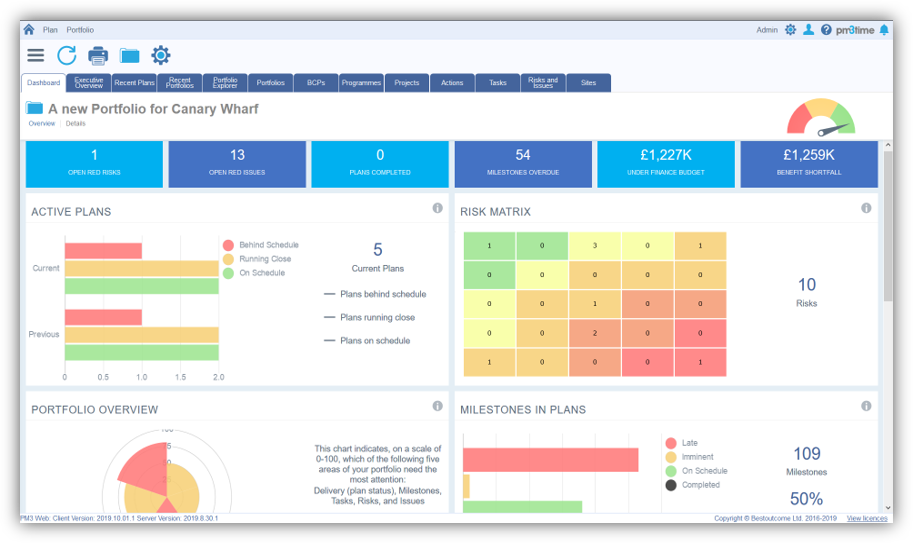
PM3 Software Reviews Demo Pricing 2023
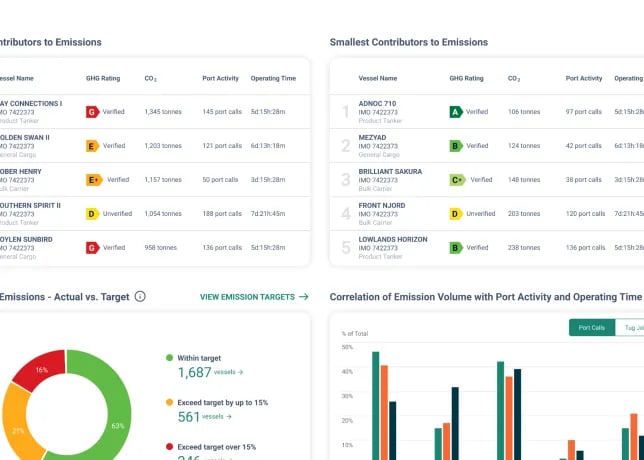
Maritime Emissions Portal Rightship

Identity Theft Prevention Program Software Tandem
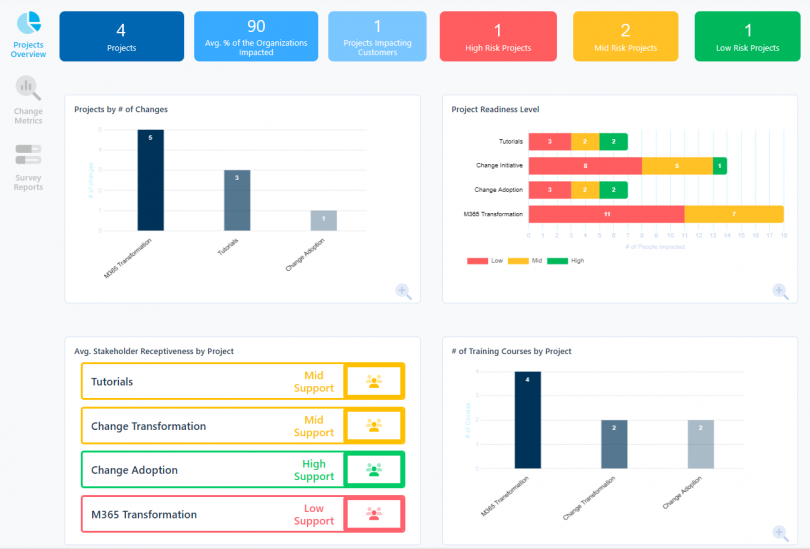
Best 2024 Stakeholder Engagement Guide with Template and Samples for

Patch Manager Plus A Complete Automated Patch Management Tool

10 Best Remote Administration Tools for Enterprise Businesses