Vulnerability Management Certifications
Here are some of the images for Vulnerability Management Certifications that we found in our website database.

What is a Vulnerability? Balbix

vulnerability Lanworks
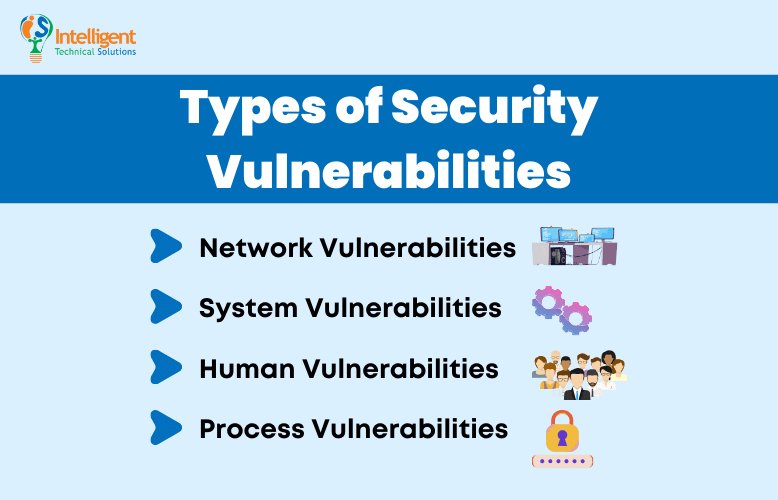
What is a Security Vulnerability? (Definition Types and Remediation)
What is a security vulnerability? Debricked

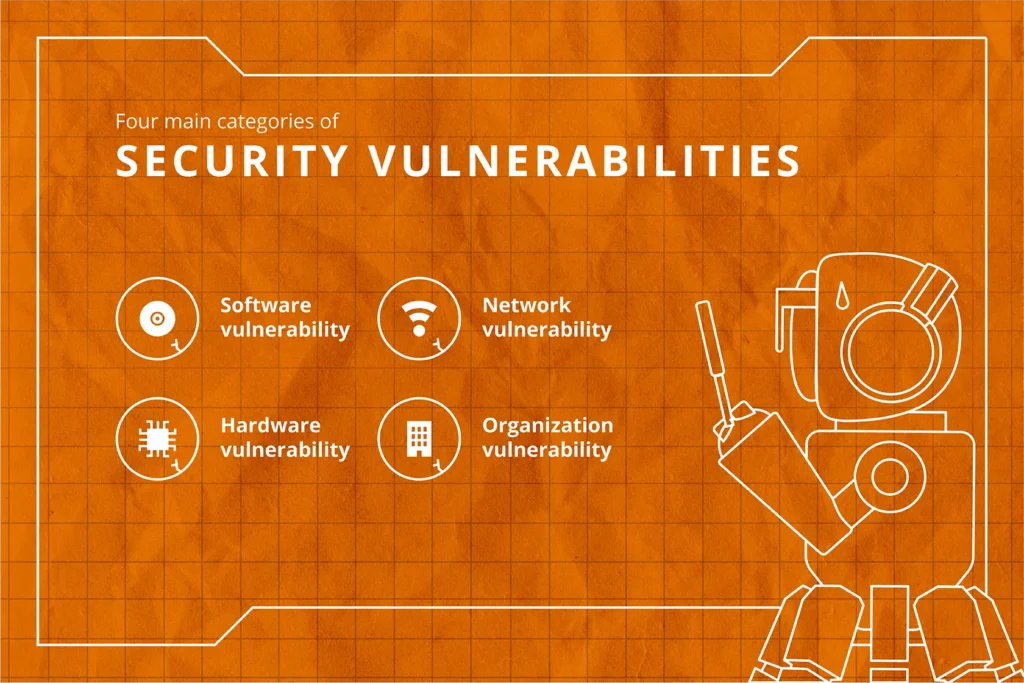
WHAT ARE THE 4 MAIN TYPES OF VULNERABILITY?
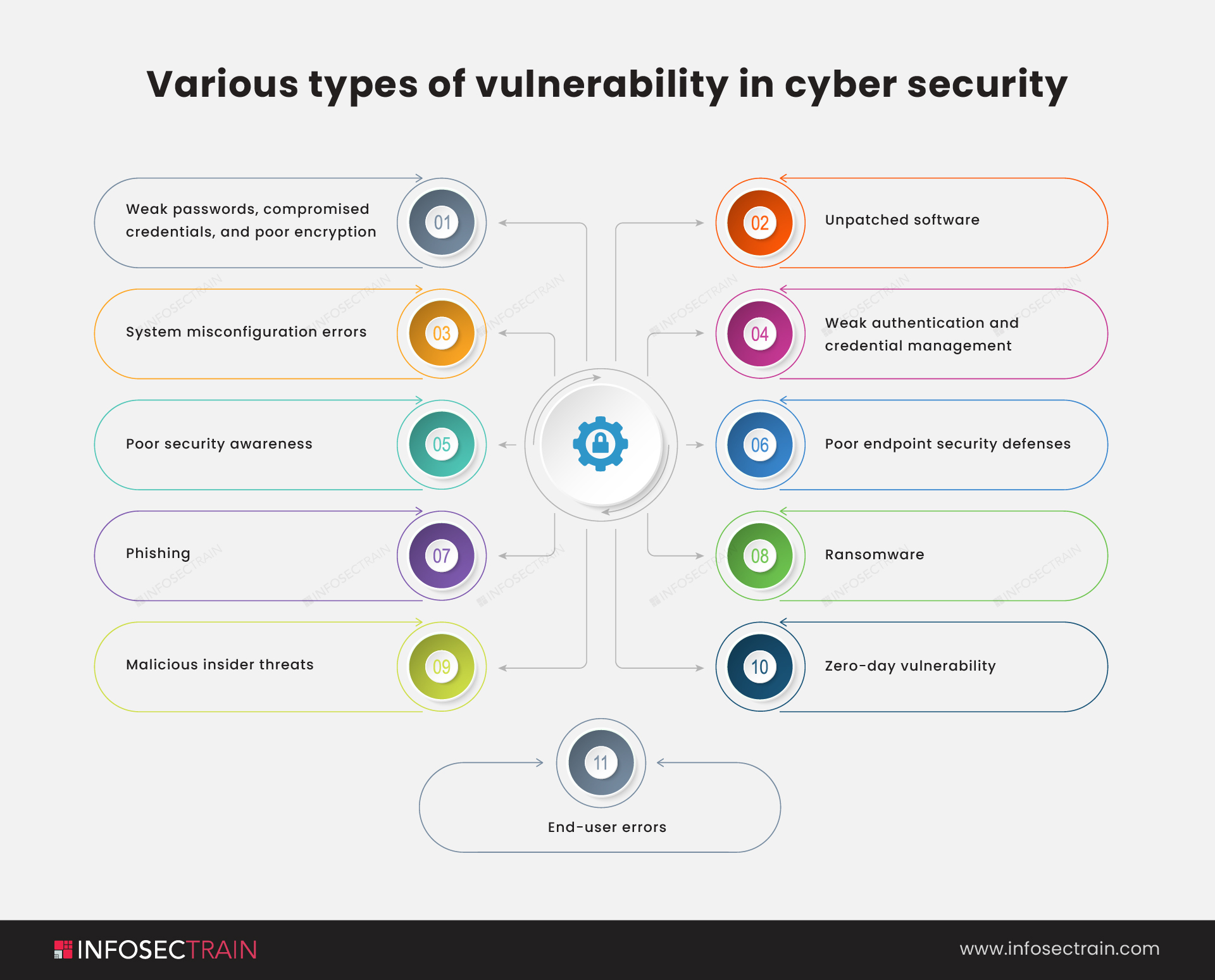
OWASP Top 10 Vulnerabilities 2021 Revealed InfosecTrain

PPT Perspectives on Vulnerability PowerPoint Presentation free

Vulnerability Assessment Tools Checklists ManageEngine

Part 1: An In Depth Look at the Latest Vulnerability Threat Landscape
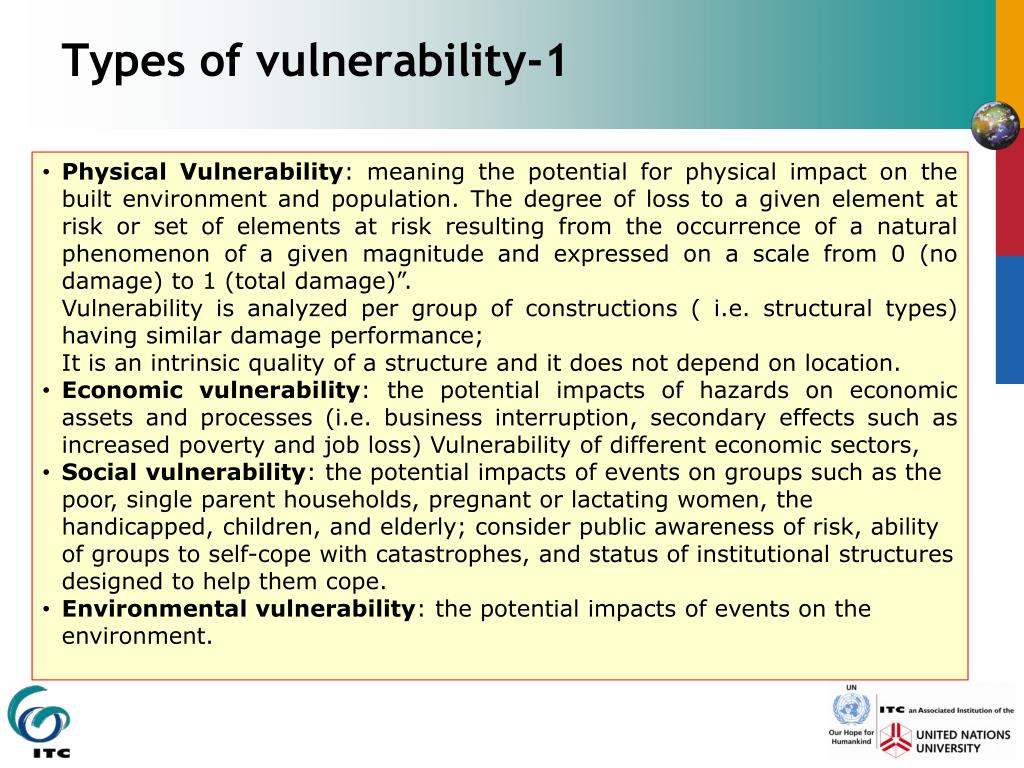
PPT Session 5: Vulnerability assessment PowerPoint Presentation free
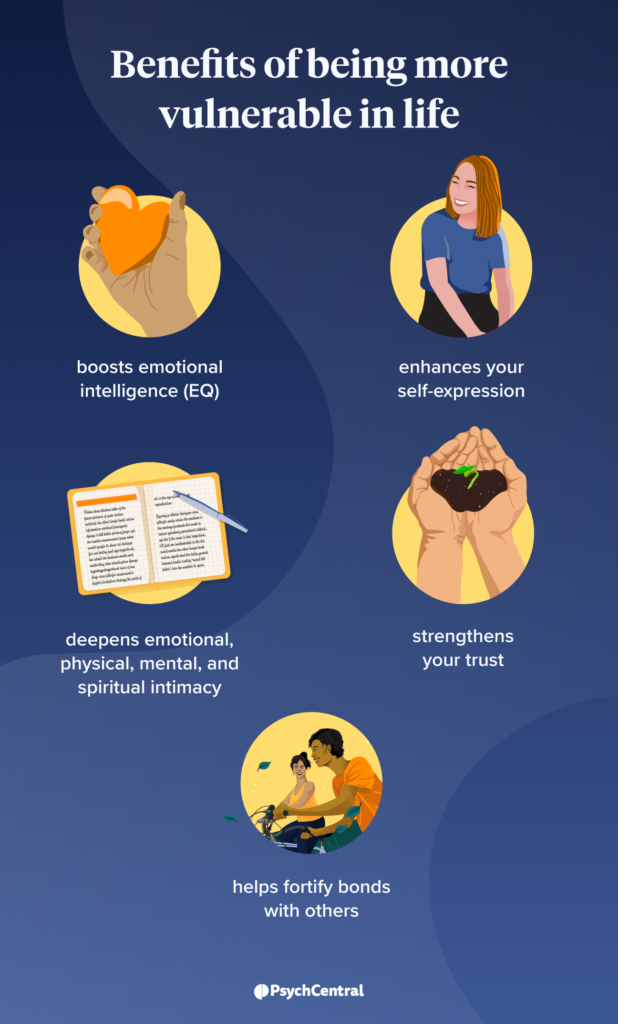
Vulnerability: An Important Trait of the Emotionally Mature

The Importance of Vulnerability Remediation for System Security

What is Vulnerability Intelligence? The 5 Data Challenges It Solves

Common types of cyber vulnerabilities
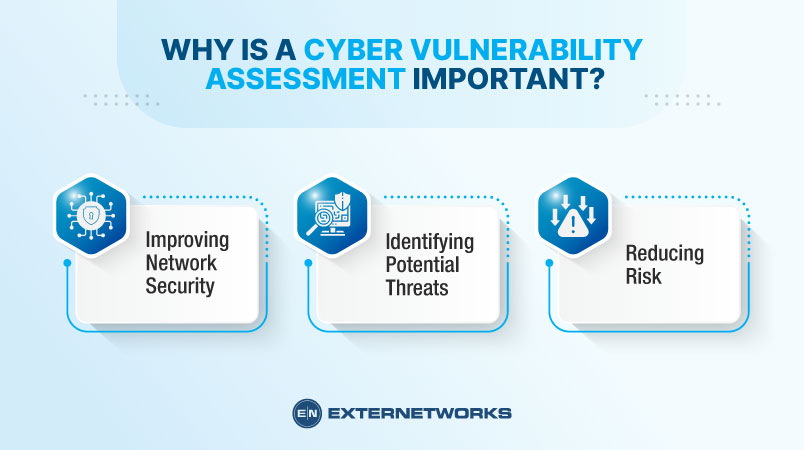
Vulnerability Assessment

Vulnerability Scanning Definition In Network Security at Karima Parker blog

Vulnerability Scanning: What It Is and Why You Need It
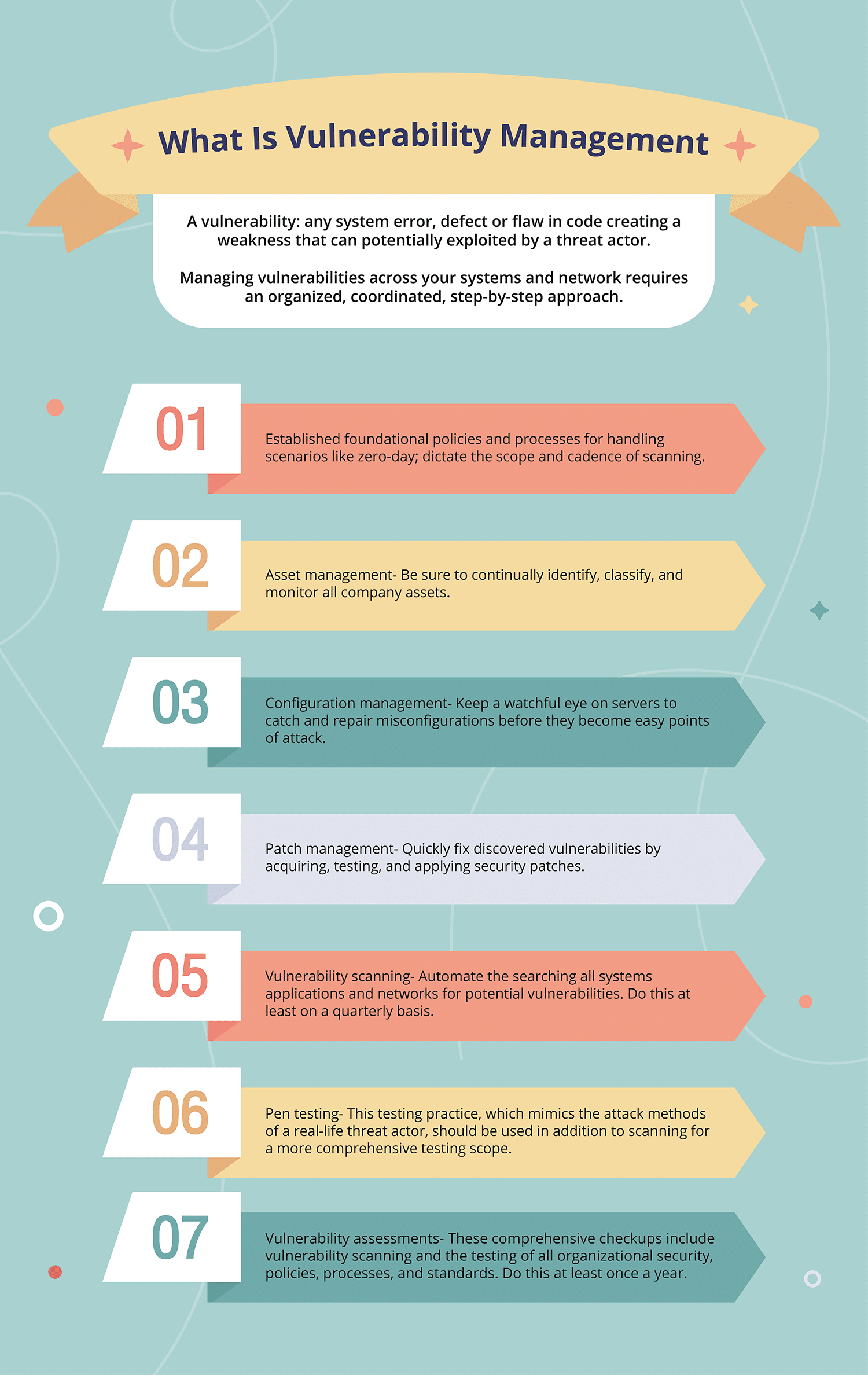
The Ultimate Guide to Vulnerability Management Hyperproof

Brene Brown Vulnerability Definition and Quotes with Images Ann
:max_bytes(150000):strip_icc()/fear-of-vulnerability-2671820-Final-e6ee1795fd364dafa943934bc3b021cc.png)
How to Be Vulnerable and Open Up
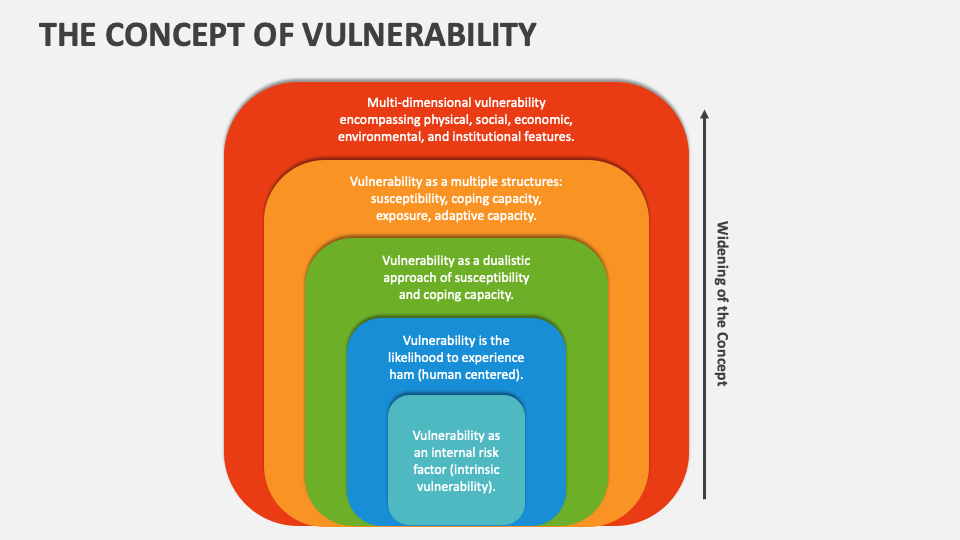
The Concept of Vulnerability PowerPoint Presentation Slides PPT Template

Threat vs vulnerability vs risk what s the difference?

Risk Threat and Vulnerability 6clicks

Vulnerability PPT

50 Vulnerability Examples (2024)

What is Vulnerability?

Vulnerability Scanning WebCheck Security

What is vulnerability and why is it important? Oudel Inc
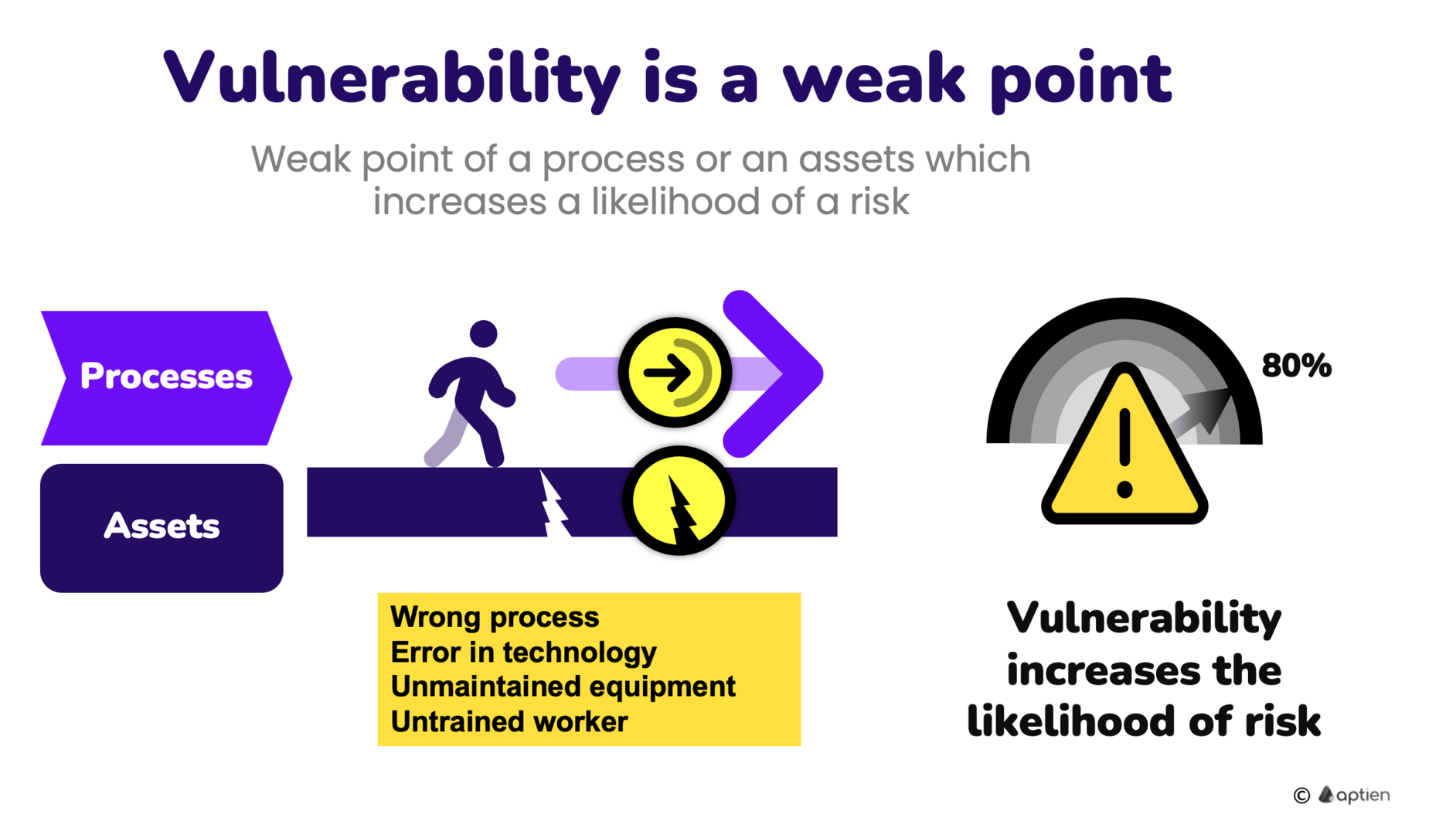
What is Vulnerability GRC Glossary Aptien

Mastering the Art of Vulnerability Management in the Modern Security

The Power of Vulnerability Restoring Balance Counseling

What Are The Benefits Of Using Vulnerability Management Software
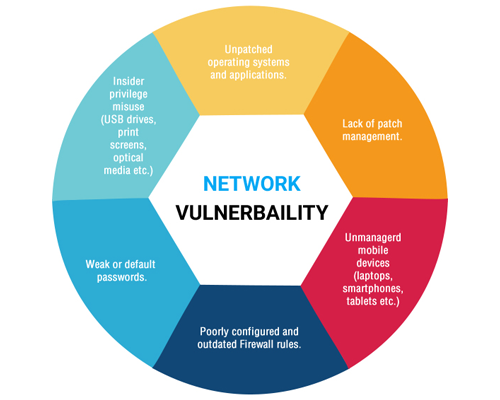
How To Check Tls Connection In Chrome
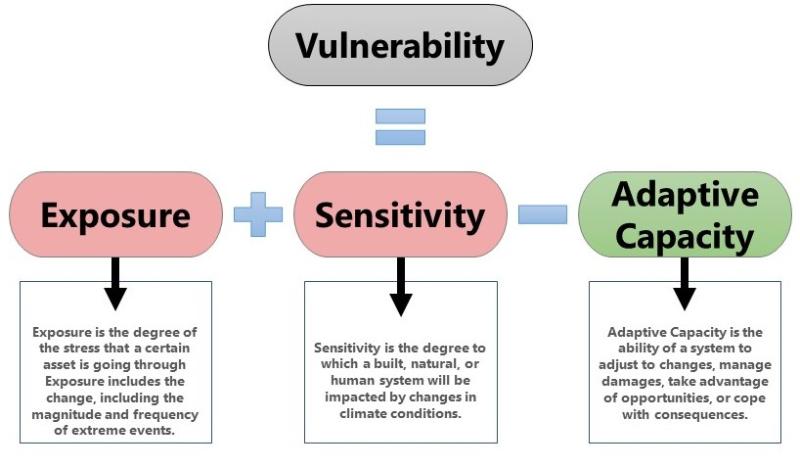
Understanding Vulnerability

The Vulnerability and the Human Condition Initiative Emory University