Threat Report Template
Here are some of the images for Threat Report Template that we found in our website database.

Premium Vector Threat levels gauge vector illustration
Cybersecurity in the Age of Remote Work: Best Practices and Common
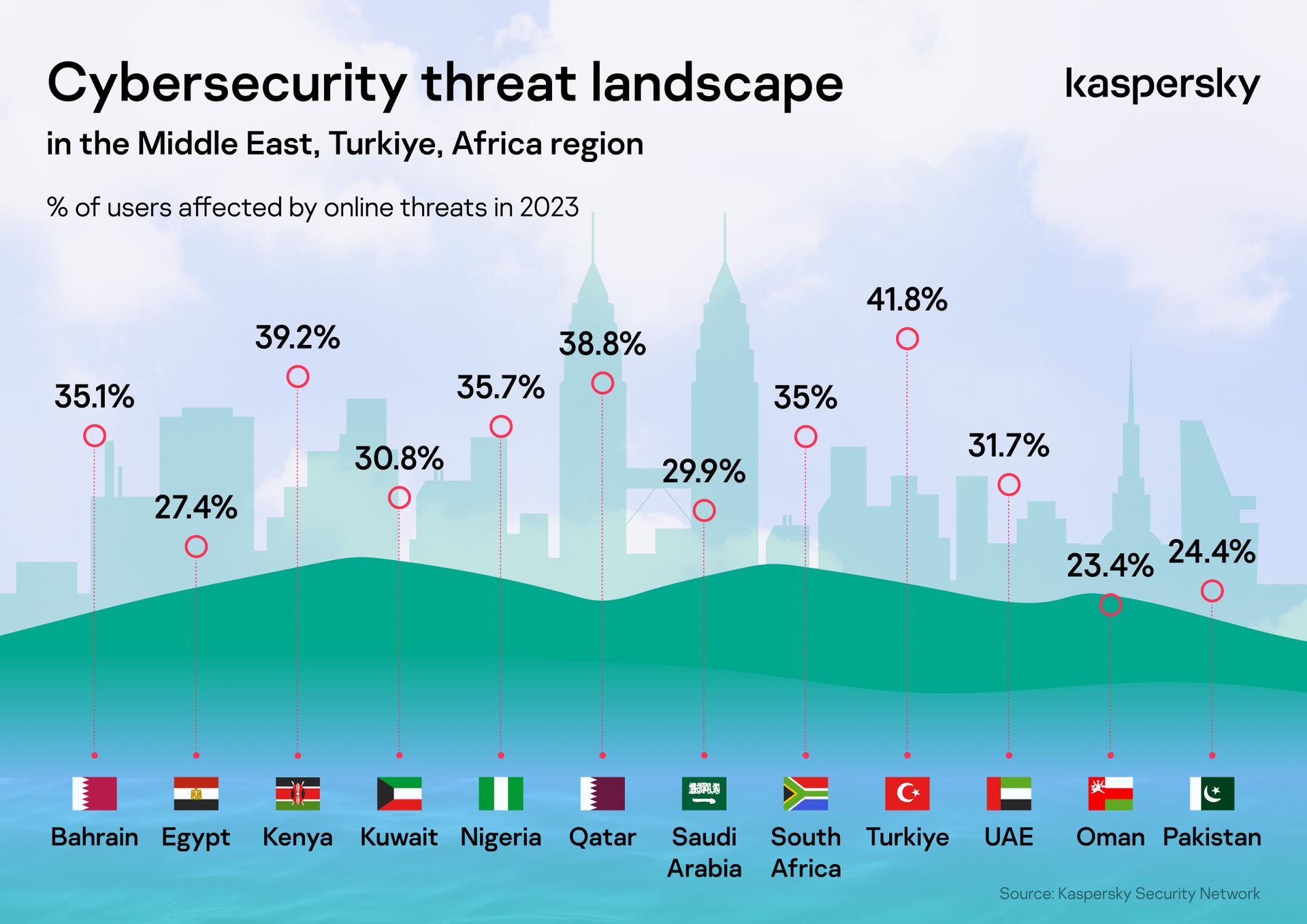
Kaspersky shares cyberthreat landscape insights for the African region

Tenet #1: Elevating Threat Intelligence Tenets of TIOps
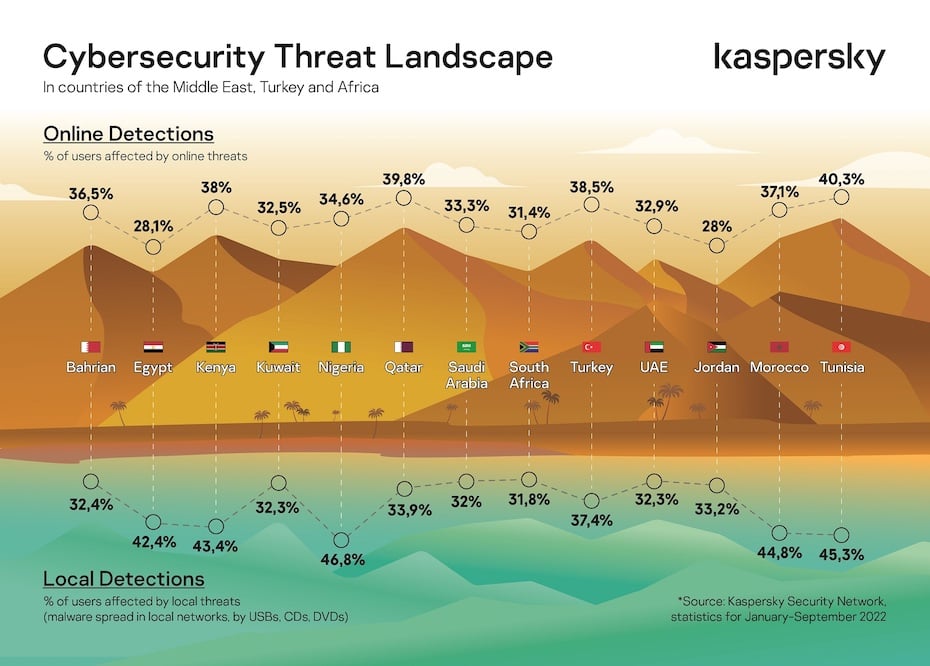
Threat landscape insights and predictions for 2023
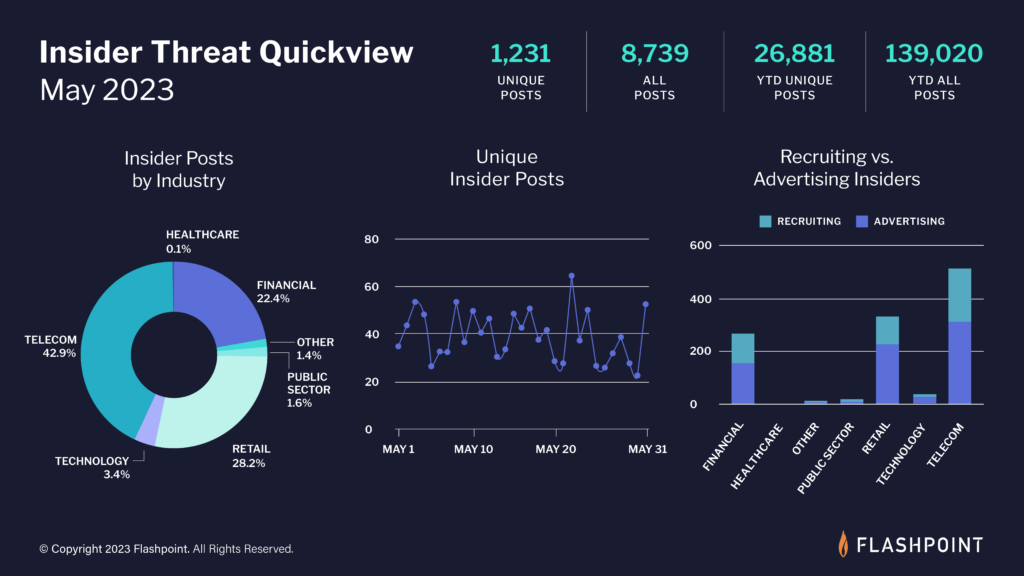
Cyber Threat Intelligence Index: May 2023 Security Boulevard

Top 9 Threat Hunting Tools for 2023 Security Boulevard

What Is An Insider Threat Definition And Examples vrogue co
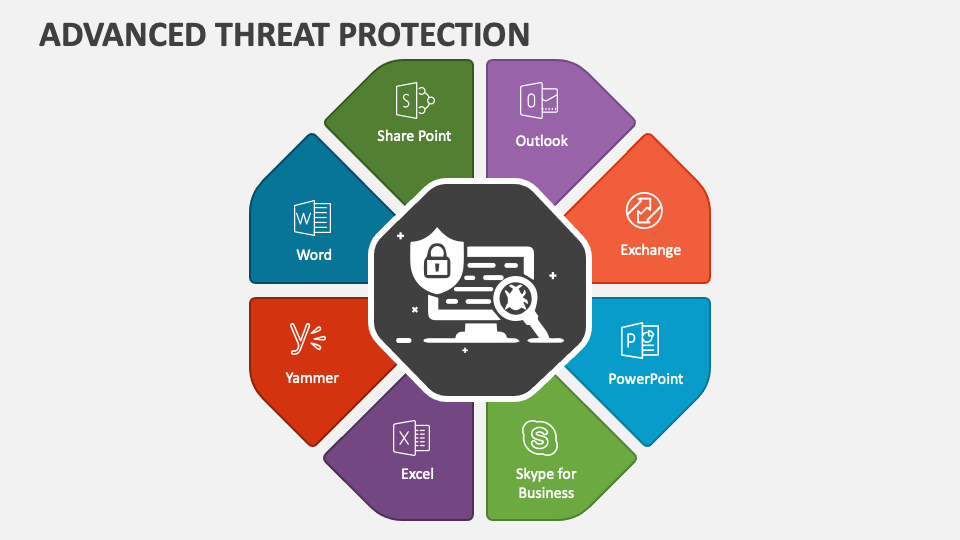
Advanced Threat Protection PowerPoint and Google Slides Template PPT

What is Endpoint Detection Response? Technology Solutions

Download Digital Threat Concept: Malware Attack Wallpaper Wallpapers com
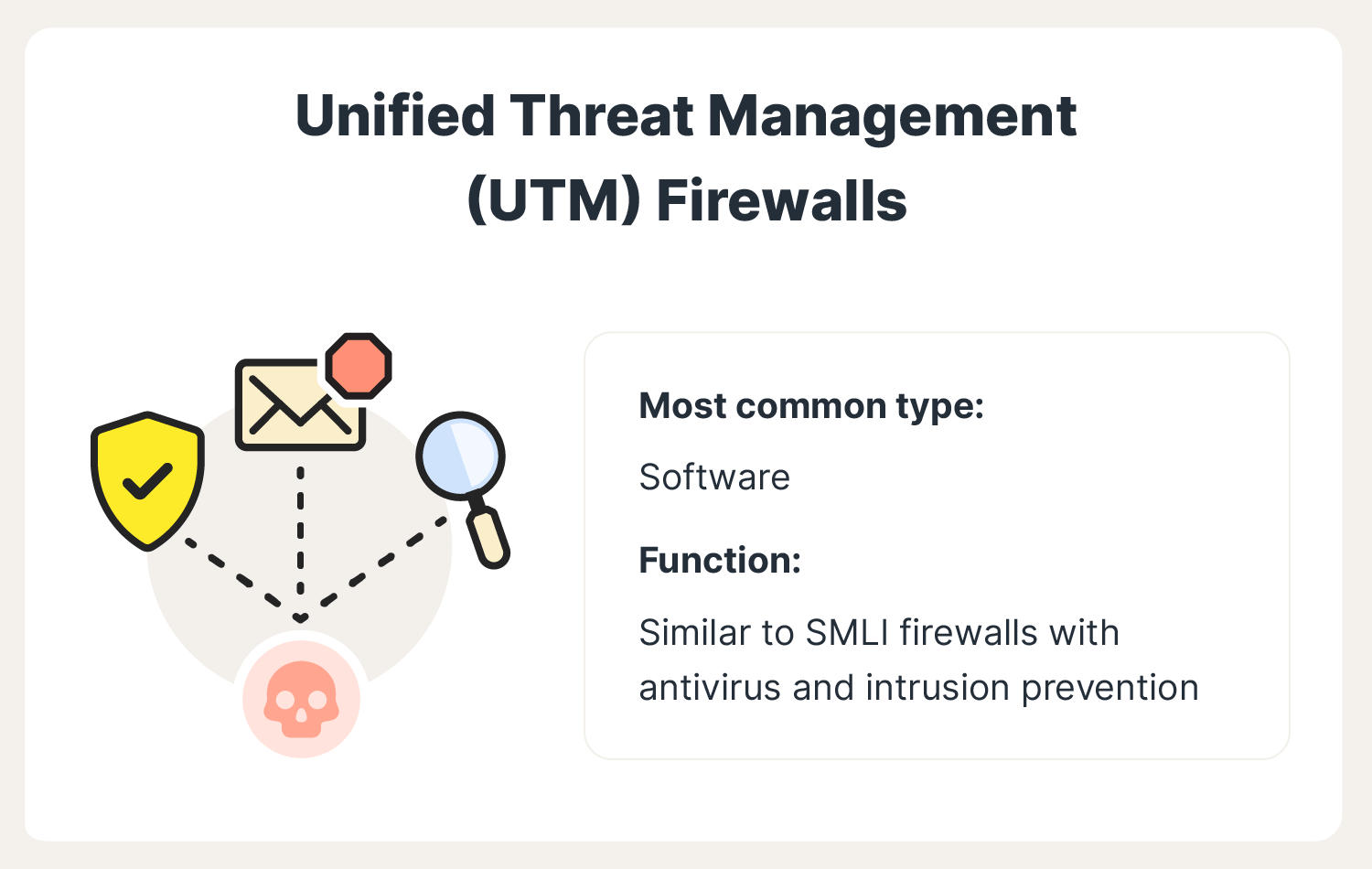
What is a firewall? Firewalls explained and why you need one Norton

The Iran Threat Geiger Counter: Moving Toward Extreme Danger

Cyber Threat Hunting vs Incident Response: What #39 s the Difference?

Evolving Cyber Threat Landscape Management in 2023

Cyber security threat detection and mitigation using IT discovery Virima

WHAT IS CYBER THREAT INTELLIGENCE?

Purpose Of Threat Hunting In A Soc at Karin Wright blog
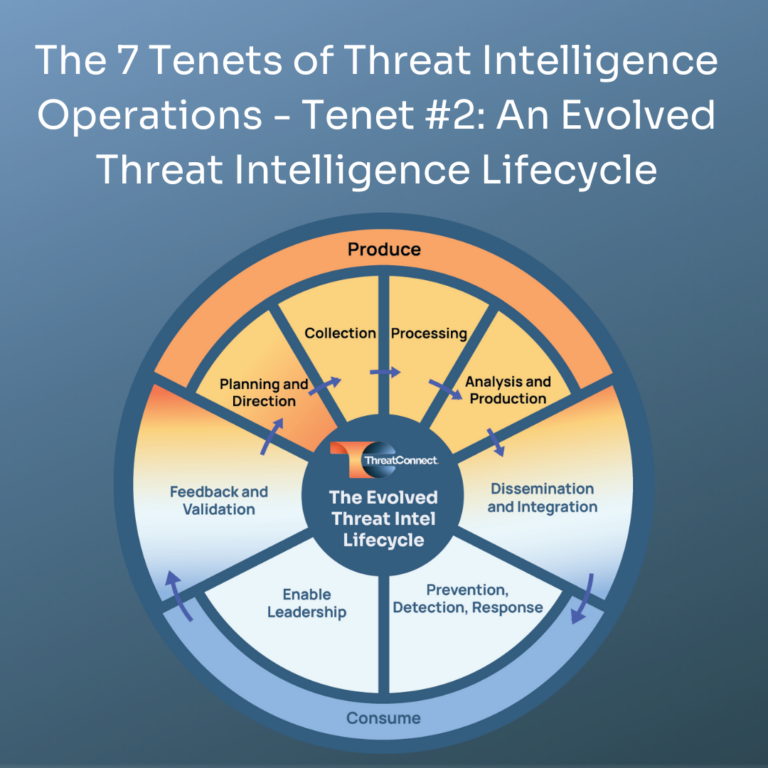
Tenet #2: Requires an Evolved Threat Intelligence Lifecycle

Smarter Schools: Leveraging AI for Real Time Threat Detection and Response
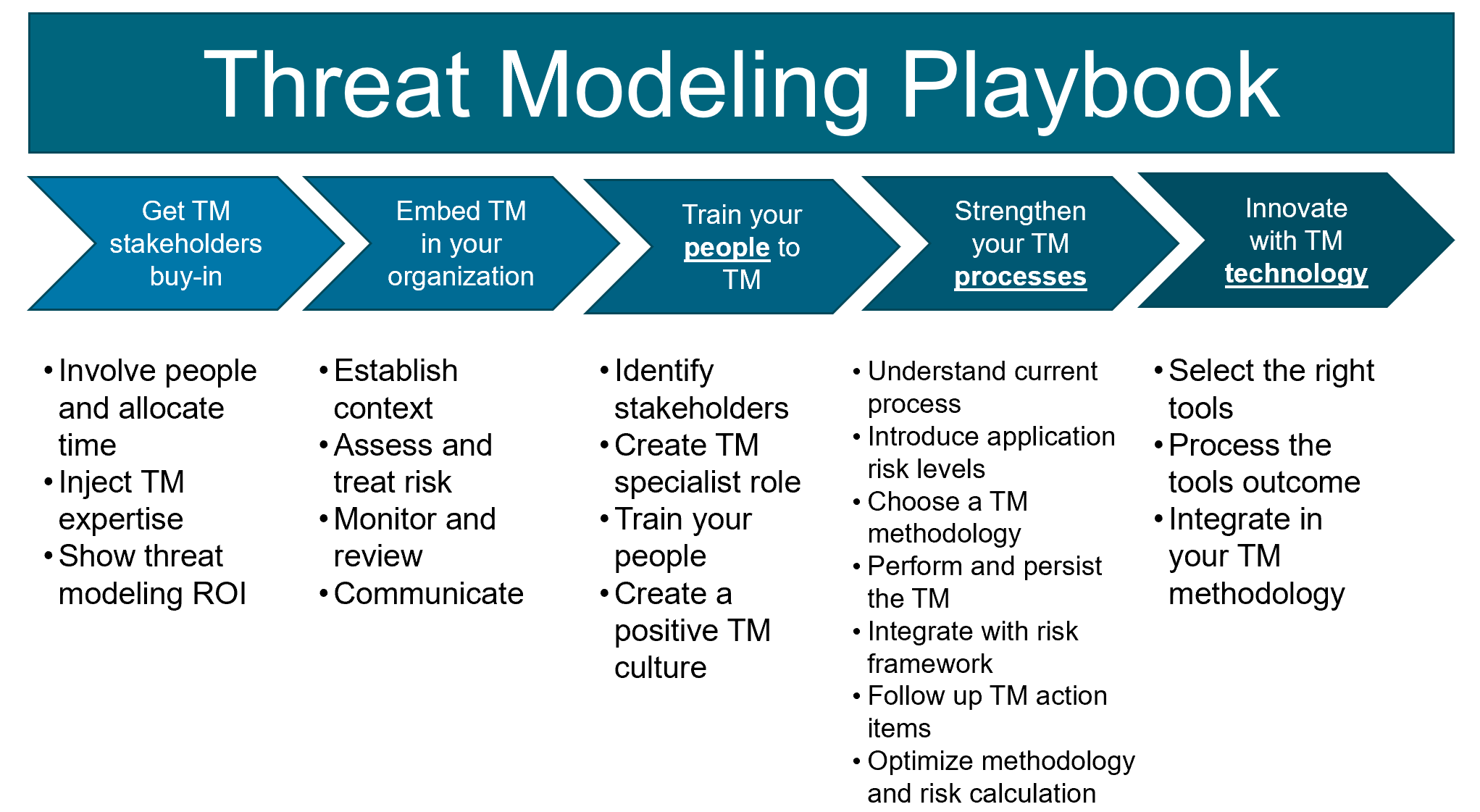
Threat Modelling Tools Download at Brett Pennell blog
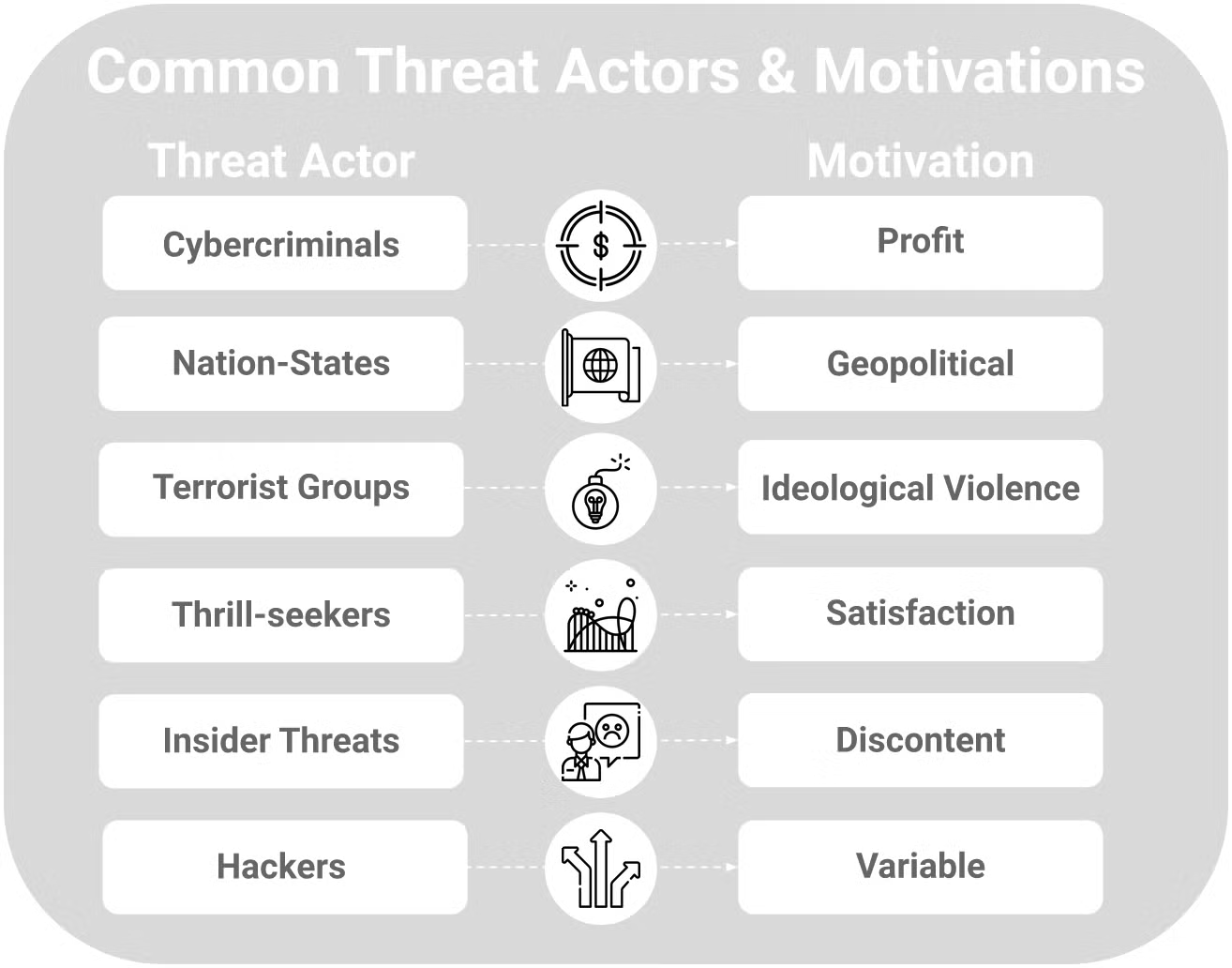
What Is A Threat Actor? Types Examples Of Cyber Threat 54% OFF

10 Types of Threat Modeling Methodology To Use in 2025

Cyber Security (Why For Me?): Threat Actors

What is Cyber Threat Intelligence (CTI)? Xcitium

Threat Intelligence: Definition Types Benefits and More

Intelligence Report Template

Strategic Tactical Operational Cyber Threat Intelligence PPT Template

Threat Hunting: Definition Process Methodologies and More

Hunting for the use of DNS Over HTTPS

What Is Cyber Threat Intelligence 3 Types Examples
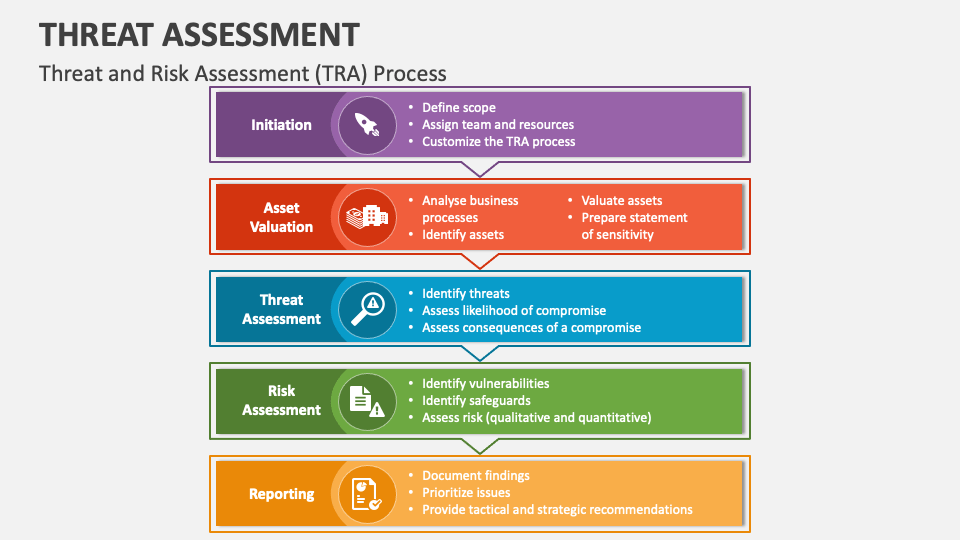
Threat Assessment PowerPoint Presentation Slides PPT Template

Defining Advanced Persistent Threat Definition Process and its

Mastering OSINT Techniques: Advanced Strategies for Information

What is Continuous Threat Exposure Management (CTEM)? Resmo