Threat Hunting Template
Here are some of the images for Threat Hunting Template that we found in our website database.

Open Hunting Hunting Template
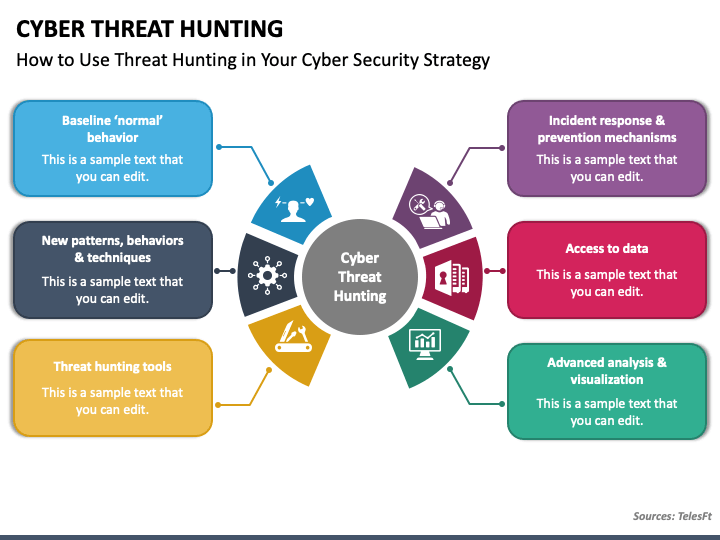
Threat Hunting Template
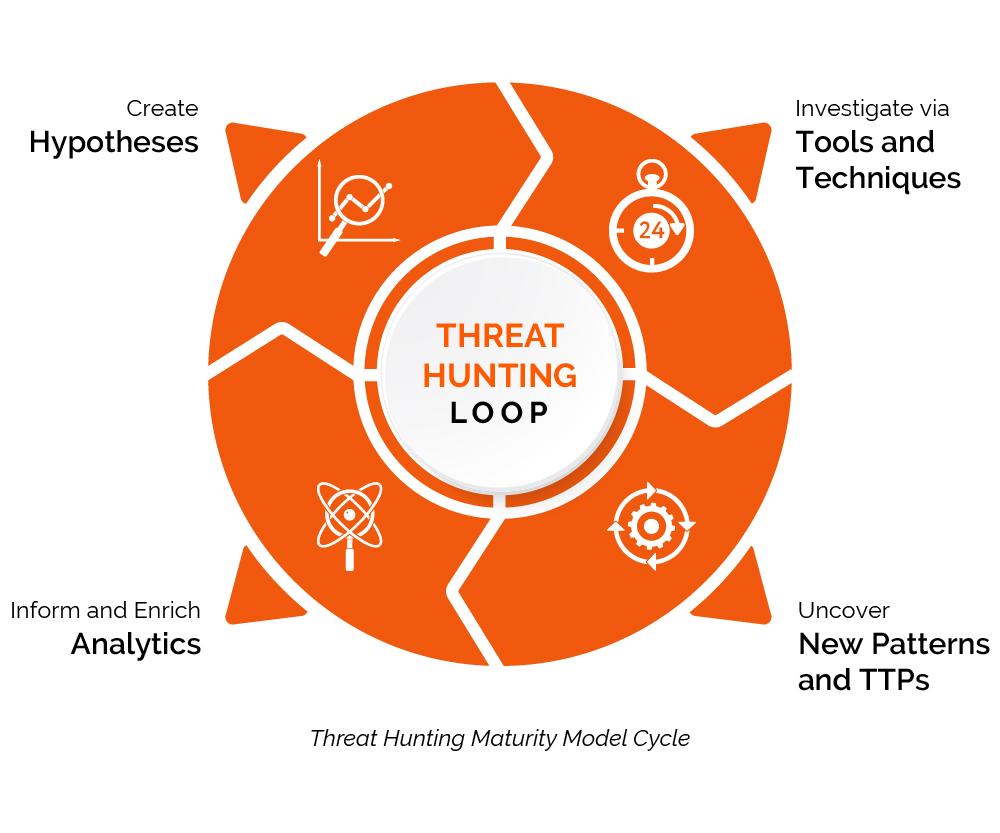
Threat Hunting Template
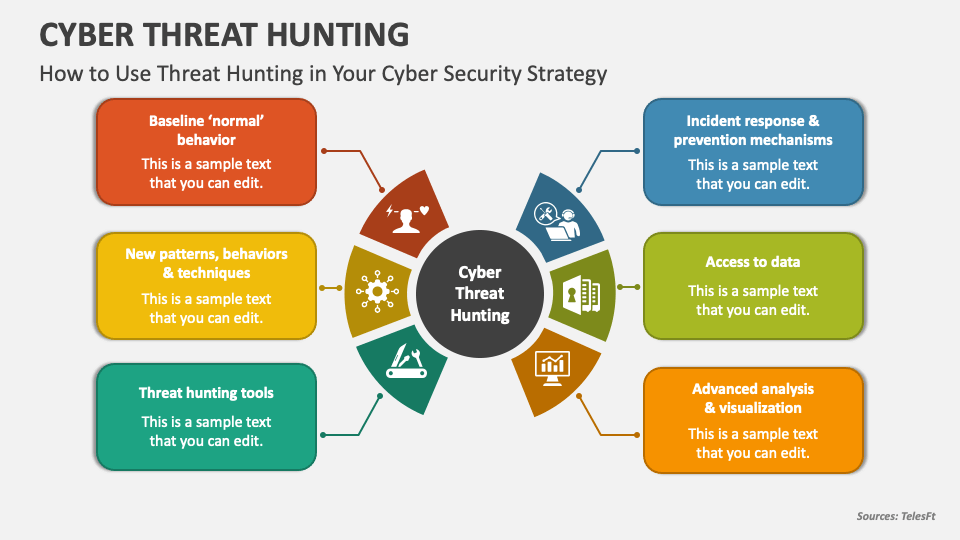
Threat Hunting Template
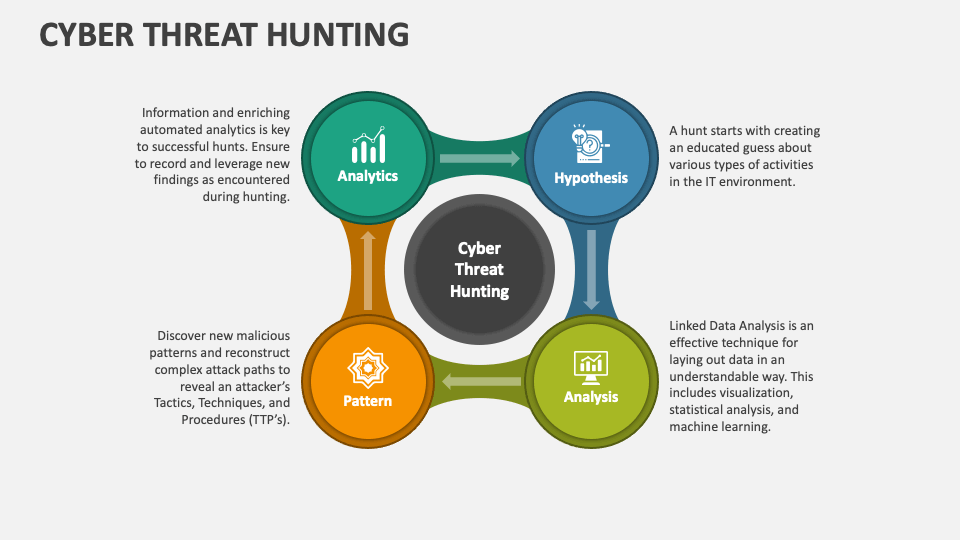
Threat Hunting Template
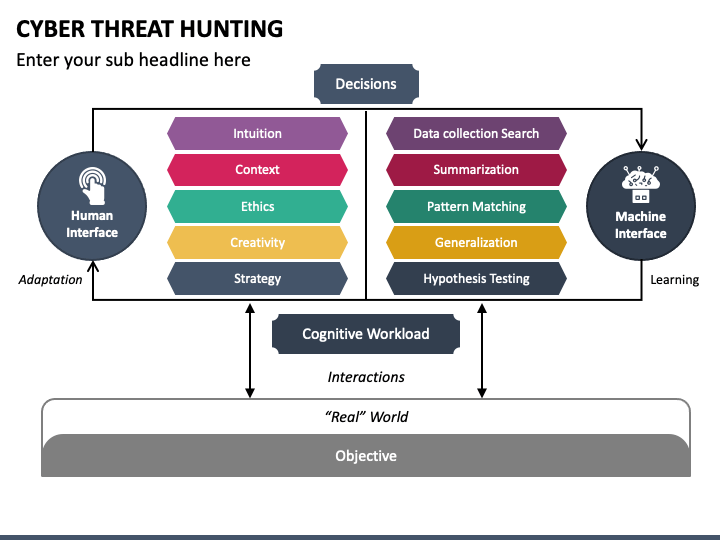
Threat Hunting Template
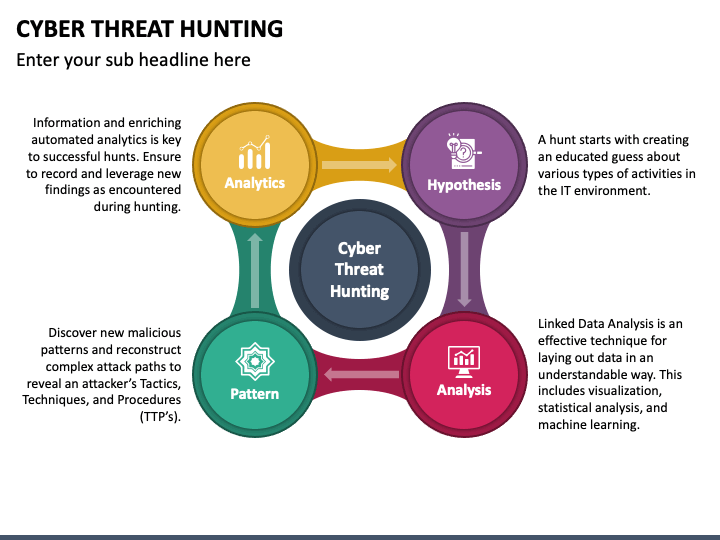
Threat Hunting Template
Threat Hunting Template
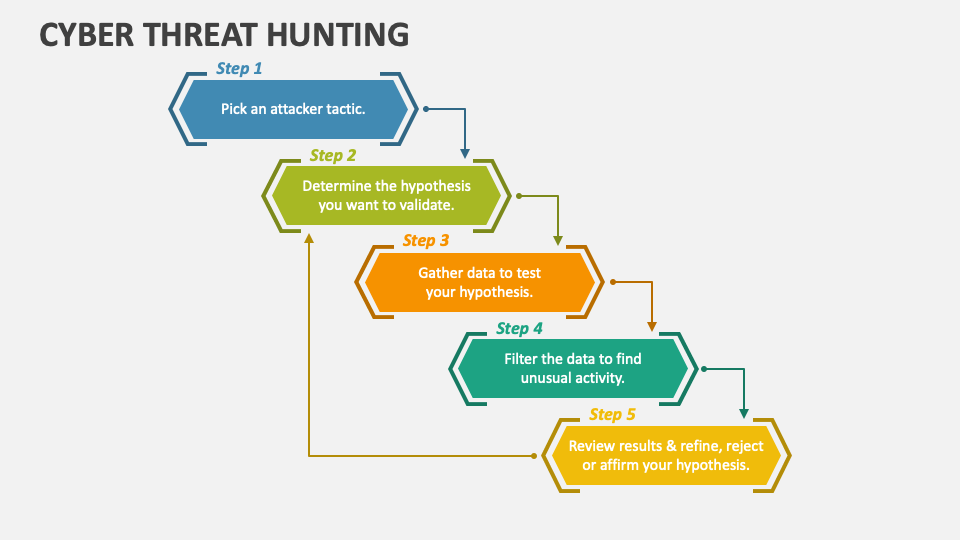
Threat Hunting Template
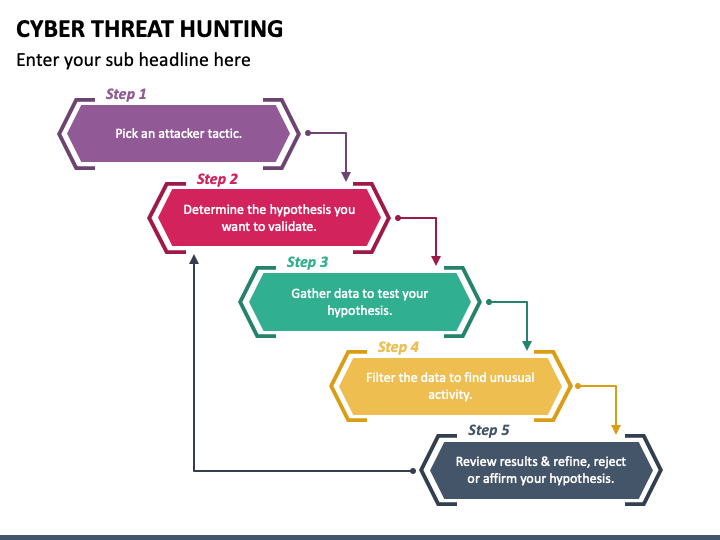
Threat Hunting Template
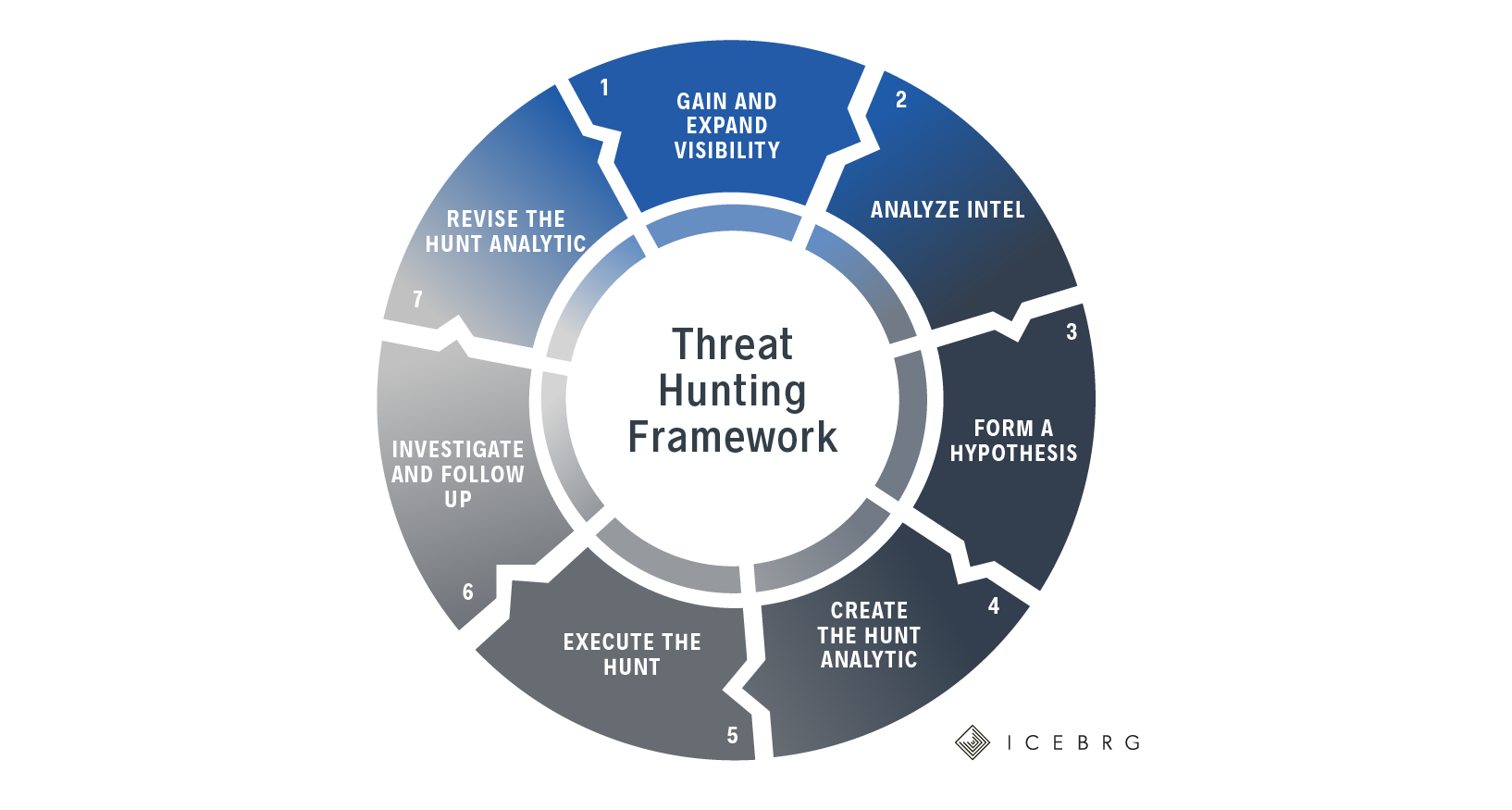
Threat Hunting Template

Threat Hunting Report Template

Threat Hunting Report Template

Threat Hunting Report Template
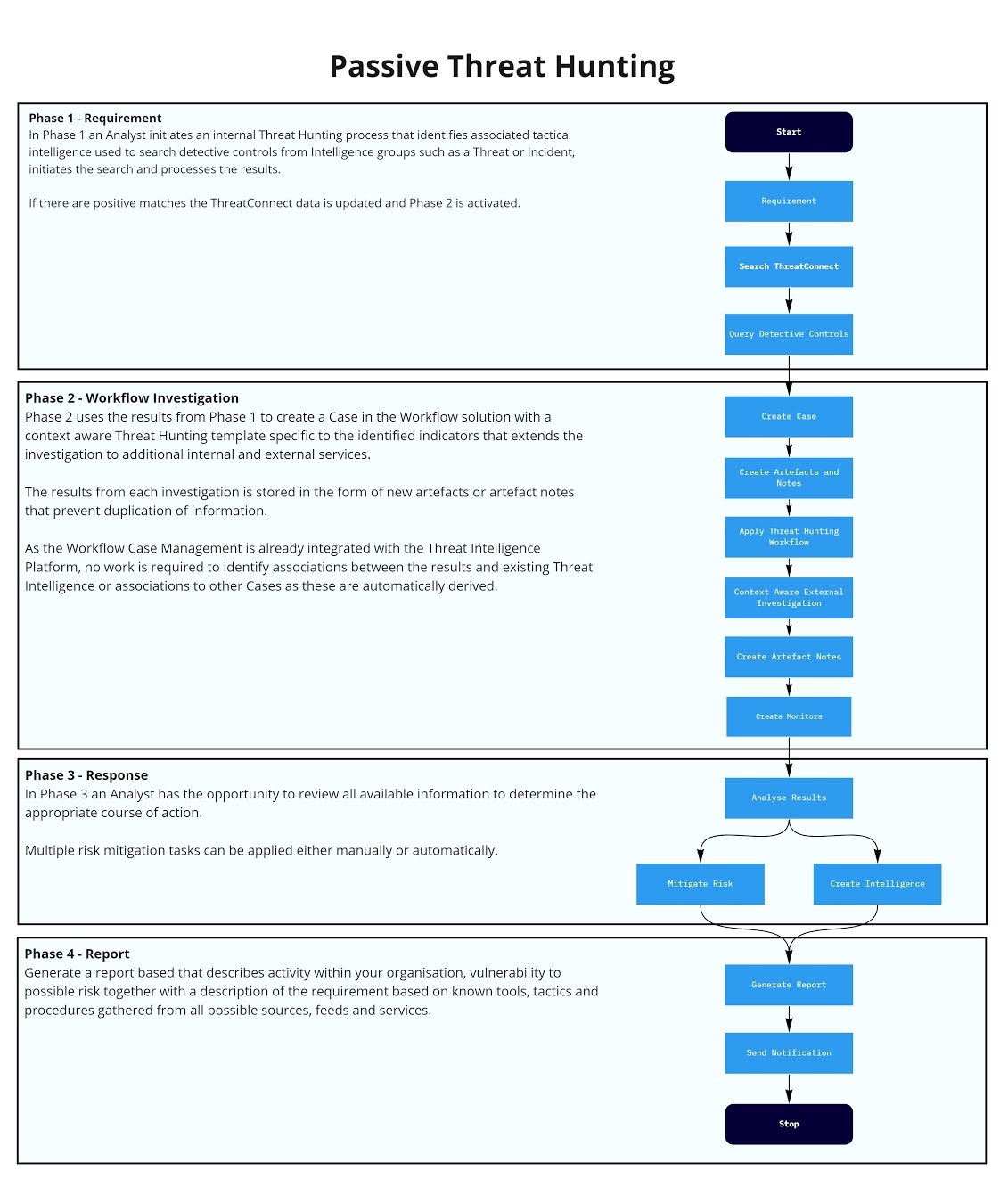
Threat Hunting Report Template
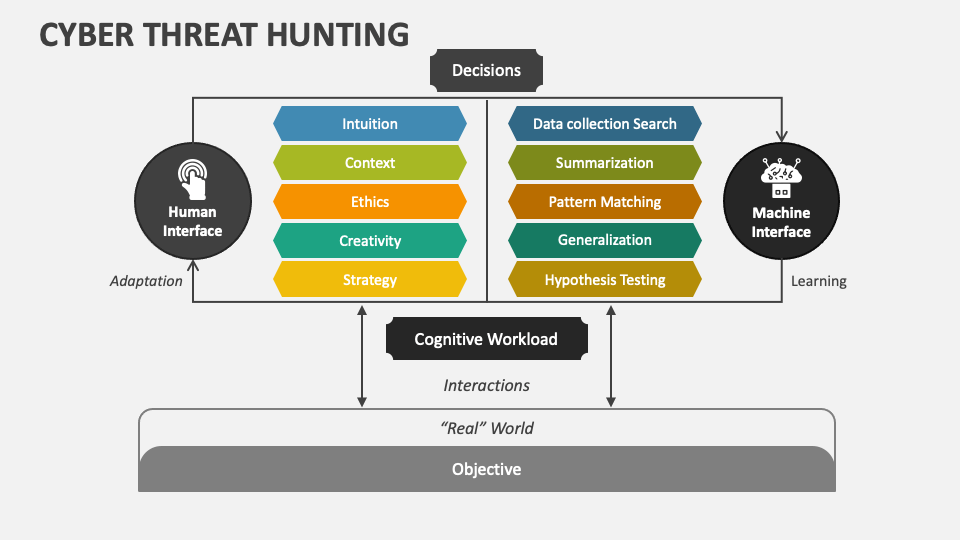
Cyber Threat Hunting PowerPoint Presentation Slides PPT Template
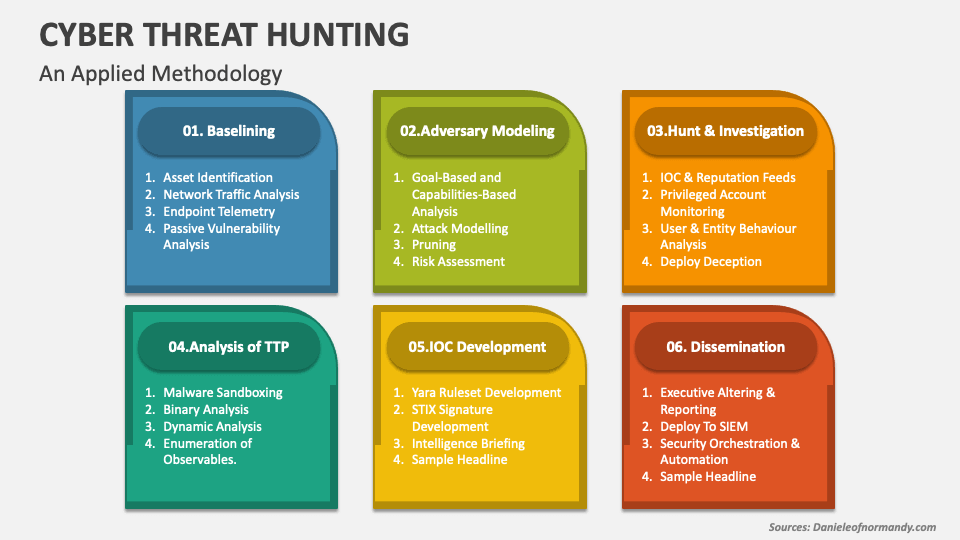
Cyber Threat Hunting PowerPoint Presentation Slides PPT Template

Cybersecurity Threat Intelligence Report Template in Word PDF Google

Cyberthreat Hunting Threat Hunting Gcore

Cyber Threat Hunting (Coursera) MOOC List

Free PSD Job hunting template

Introduction into Threat Hunting Bookory
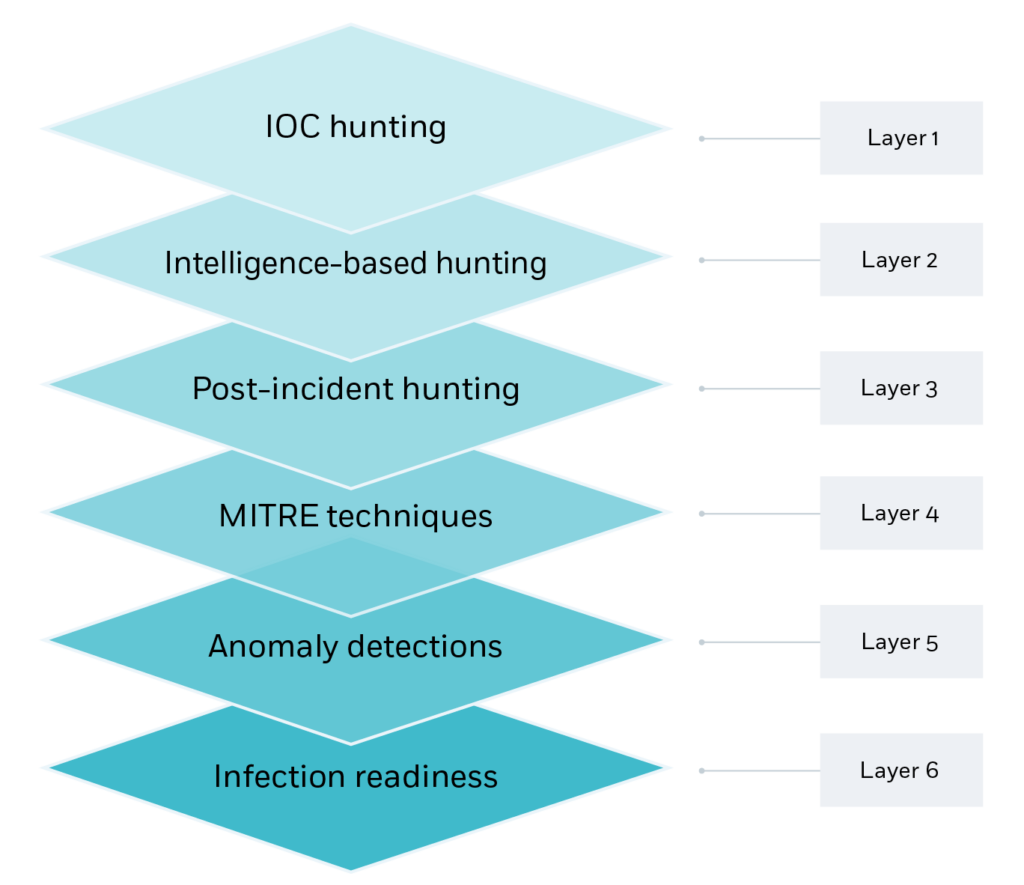
What is threat hunting? CyberProof

Threat hunting Splunk

Free PSD Job hunting template

Threat Hunting Series: Using Threat Emulation for Threat Hunting by

Threat Intelligence Report Template

Threat Hunting Loop: A Practical Guide

Angry deer hunting template Royalty Free Vector Image

Threat Hunting and Threat Hunting Frameworks by Chemiron Adam Medium

Threat Hunting Techniques Checklist Examples Execution Metrics

Mark Thomas Talks about Threat Hunting

Threat Hunting Techniques Checklist Examples Execution Metrics

Threat Intelligence Report Template prntbl concejomunicipaldechinu gov co

Deer Hunting Log Book Pro Template 35566148 Vector Art at Vecteezy

Getting Started with Threat Intelligence and Hunting Credly
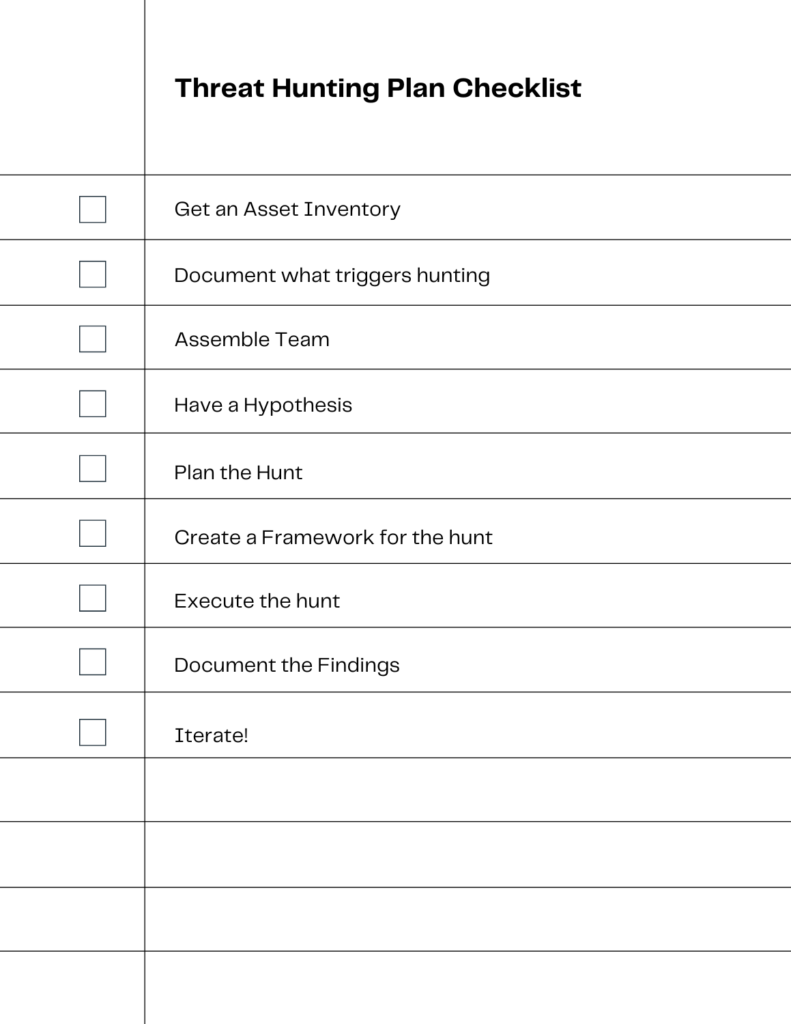
How To Do Threat Hunting: A step by step guide
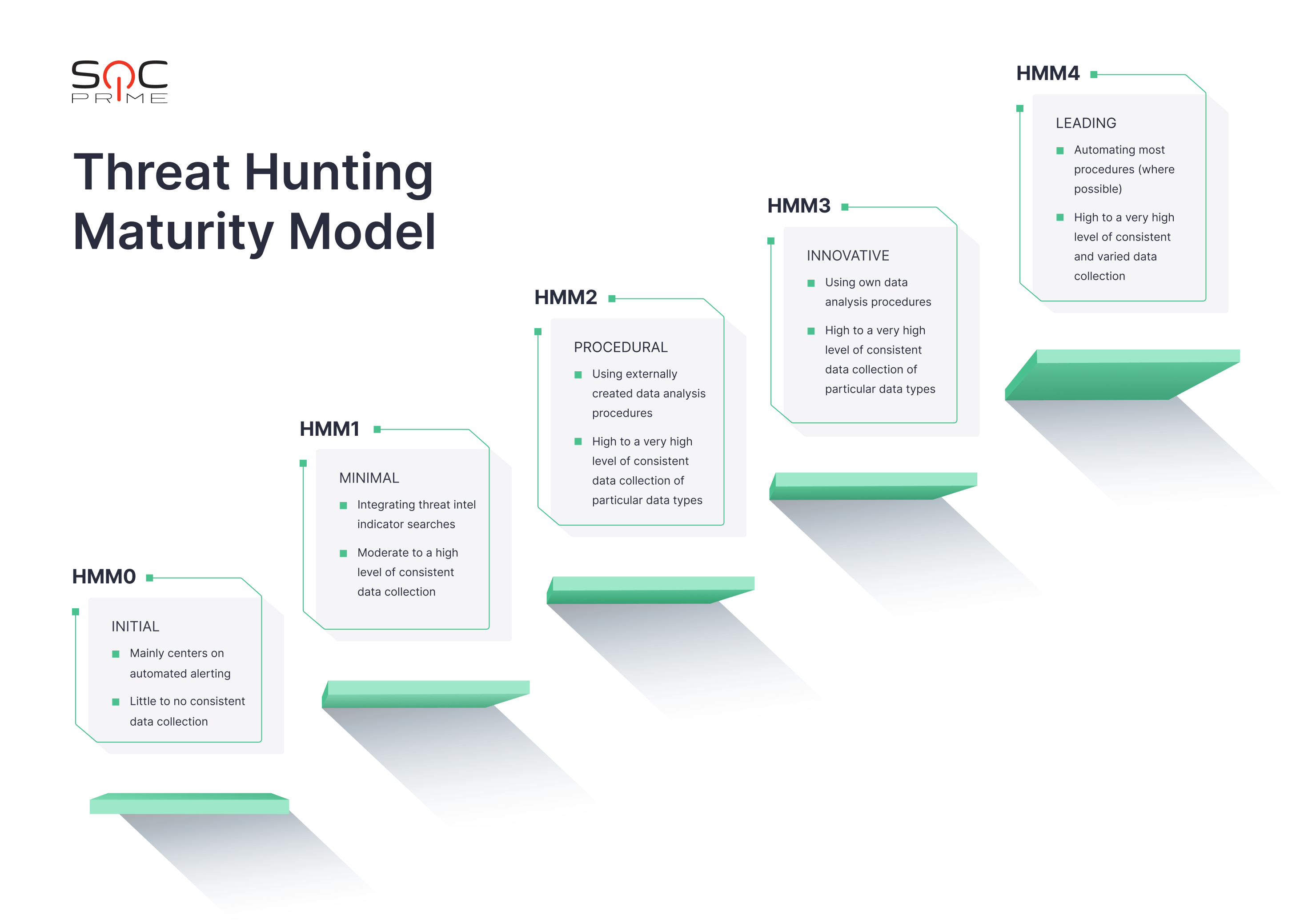
Threat Hunting Maturity Model Explained With Examples SOC Prime

Threat Hunting: Techniques Process Vaia

Proactive ClickFix Threat Hunting with Hunt io
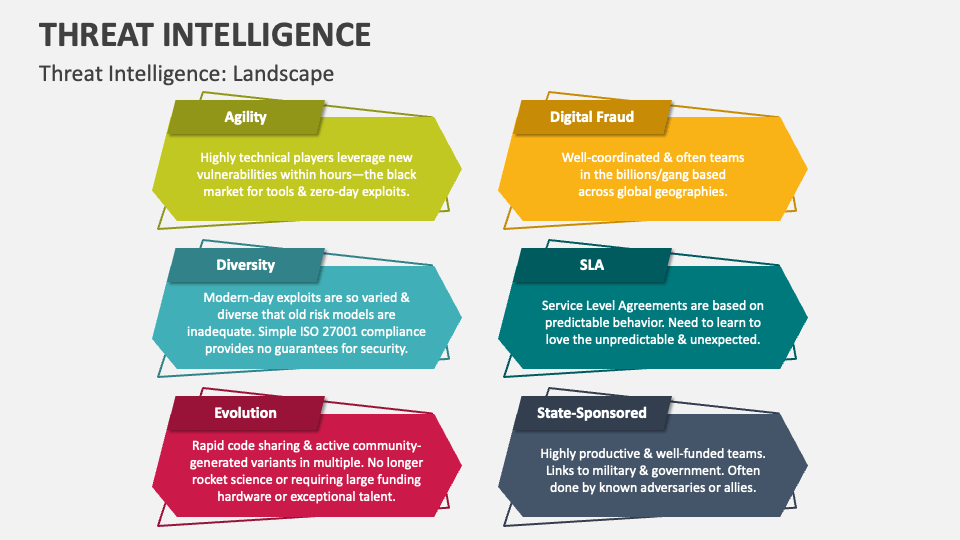
Threat Intelligence PowerPoint Presentation Slides PPT Template
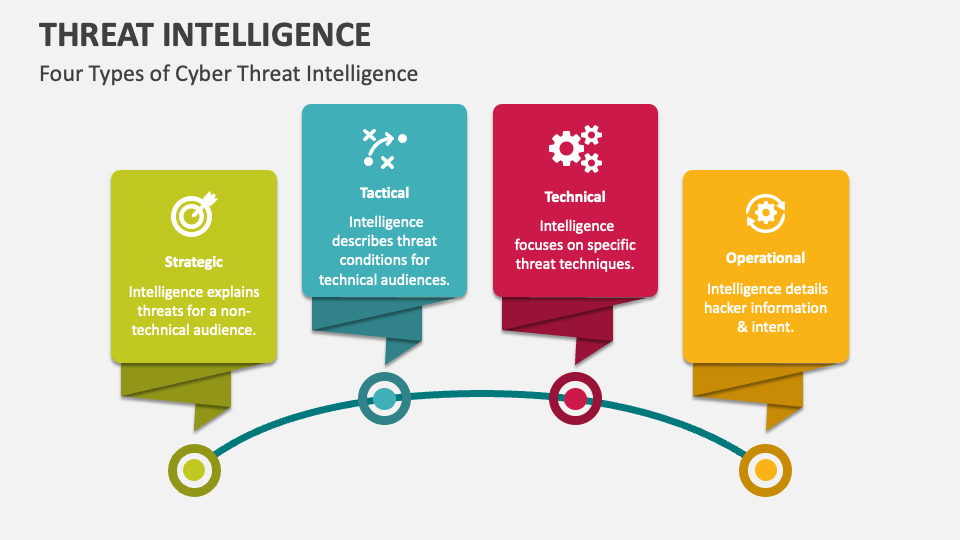
Threat Intelligence PowerPoint Presentation Slides PPT Template

Dallas Texas USA: Threat Hunting Strategies PDF

The PEAK Threat Hunting Framework Splunk

Find your Dream Job Notion Job Hunting Template Business Template

Threat Hunting III: Hunting with Velociraptor by Adam Goss InfoSec
Threat Vs Opportunity Matrix PowerPoint Presentation Slides PPT Template

Introduction to Threat Hunting Adil Salim

Threat Hunting With YARA Walkthrough with Answers TryHackMe Write Up
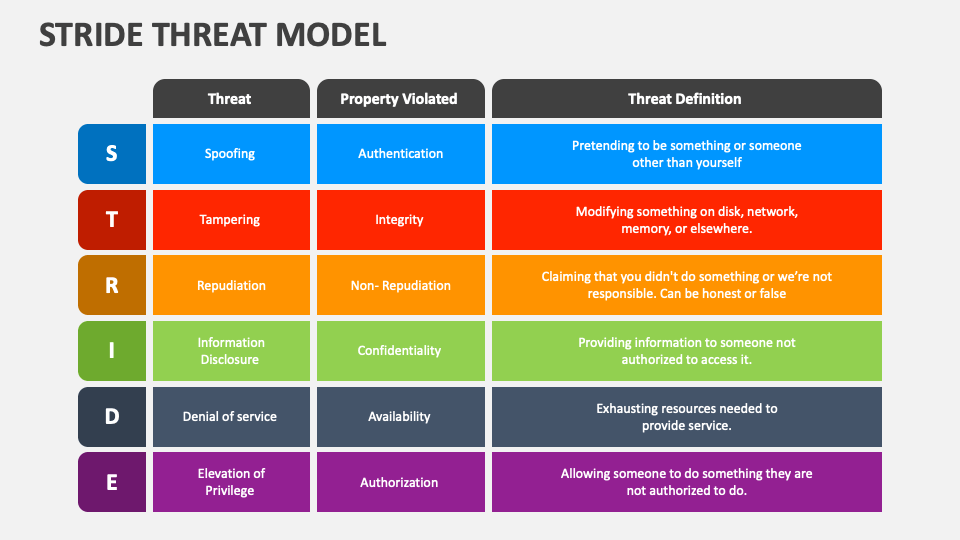
Stride Threat Model PowerPoint Presentation Slides PPT Template
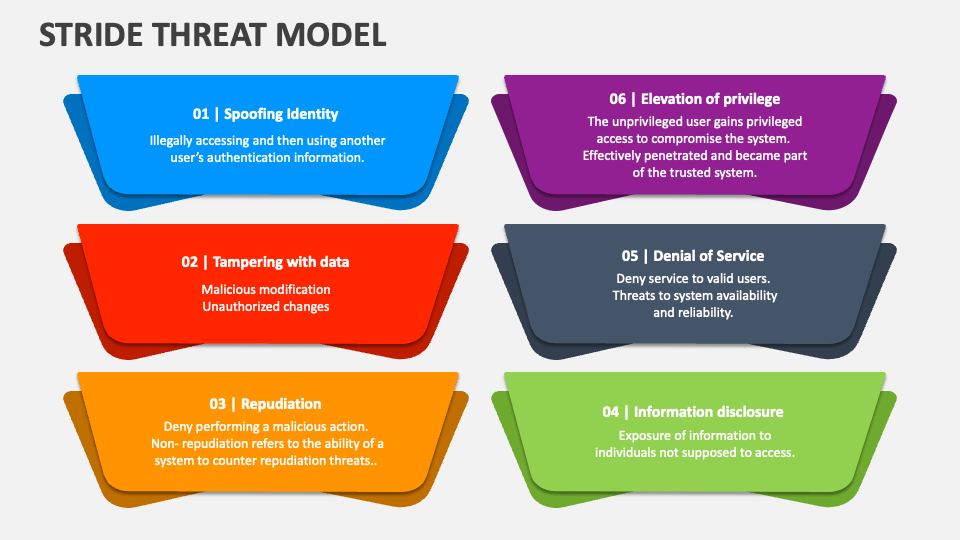
Stride Threat Model PowerPoint Presentation Slides PPT Template
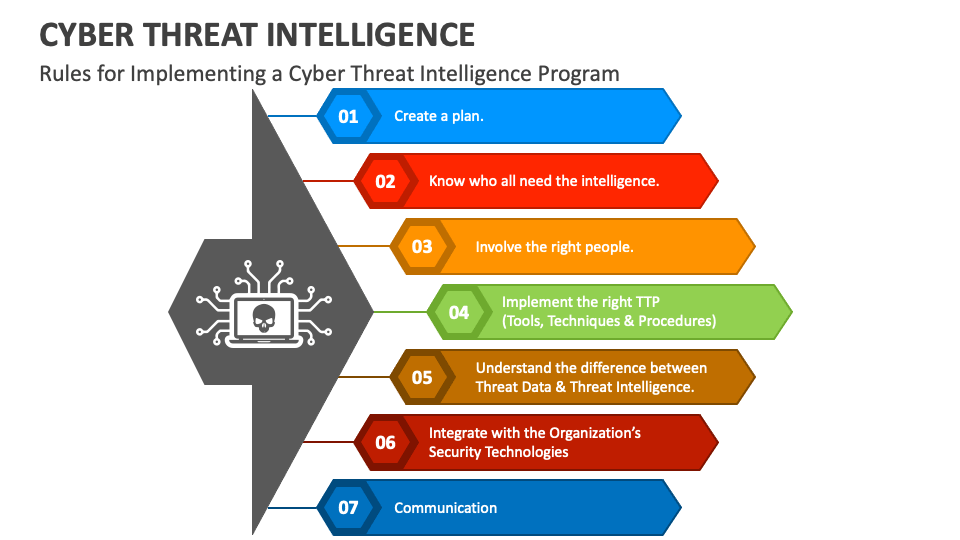
Cyber Threat Intelligence PowerPoint and Google Slides Template PPT
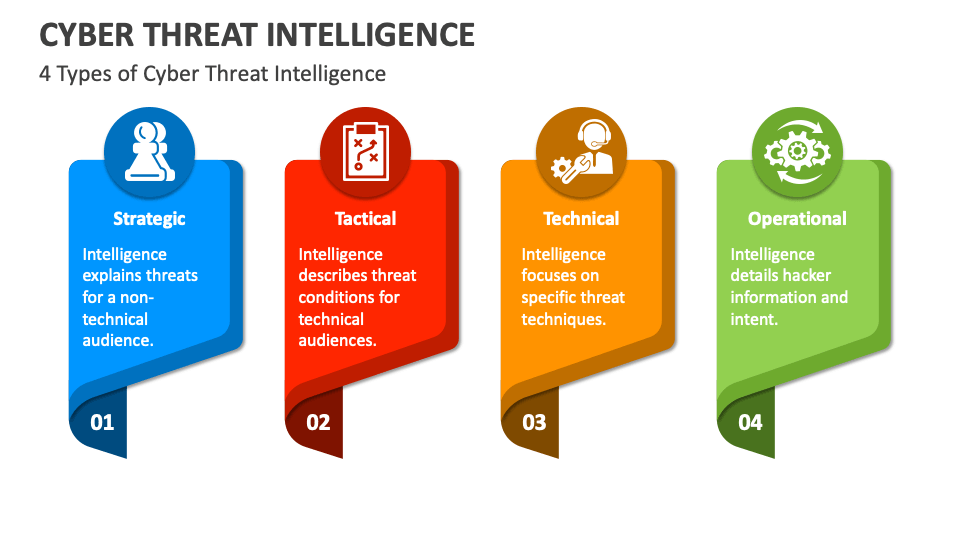
Cyber Threat Intelligence PowerPoint and Google Slides Template PPT

Deep Dive into Threat Hunting with the ELK Stack by Dhruv Patel

Threat Hunting with Wazuh FIM and Yara for Linux Endpoints by Ekene

Top 10 Threat Kpi PowerPoint Presentation Templates in 2025

Top 10 Computer Threat Hunting PowerPoint Presentation Templates in 2025

From soup to nuts: Building a Detection as Code pipeline by David