Threat Hunting Report Template
Here are some of the images for Threat Hunting Report Template that we found in our website database.

Threat Hunting Report Template

Threat Hunting Report Template

Threat Hunting Report Template

Threat Hunting Report Template
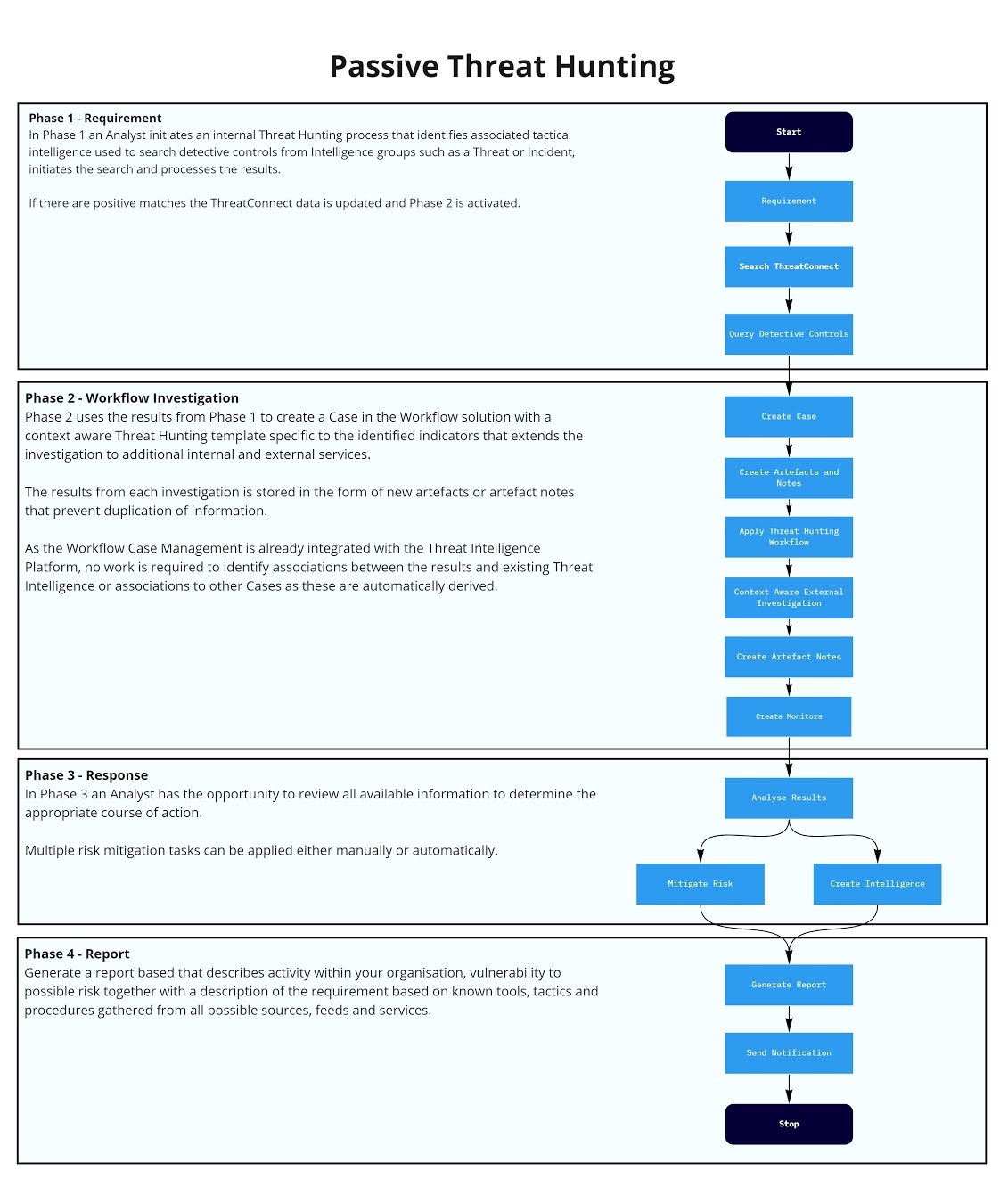
Threat Hunting Report Template

Threat Hunting Report Template

Building an Effective Threat Hunting Report Template

2021 Threat Hunting Report Download CrowdStrike

Sample Threat Hunt Report/Hunting Adversaries Demo Company Threat
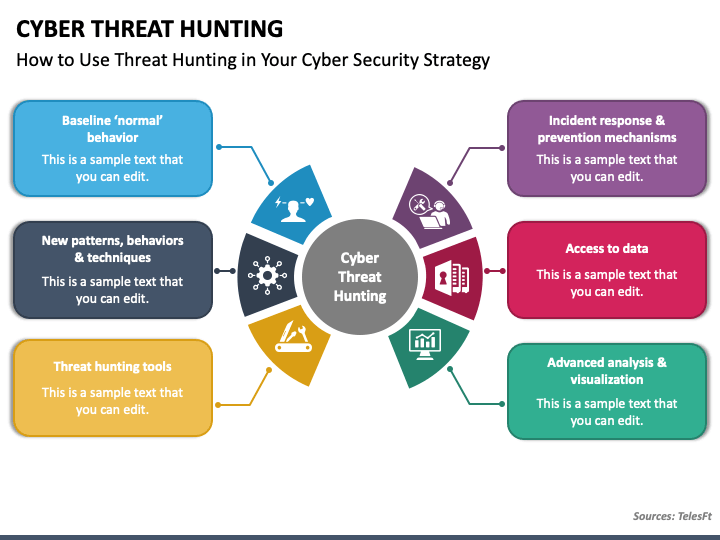
Threat Hunting Template

Cybersecurity Threat Intelligence Report Template in Word PDF Google
Threat Hunting Template
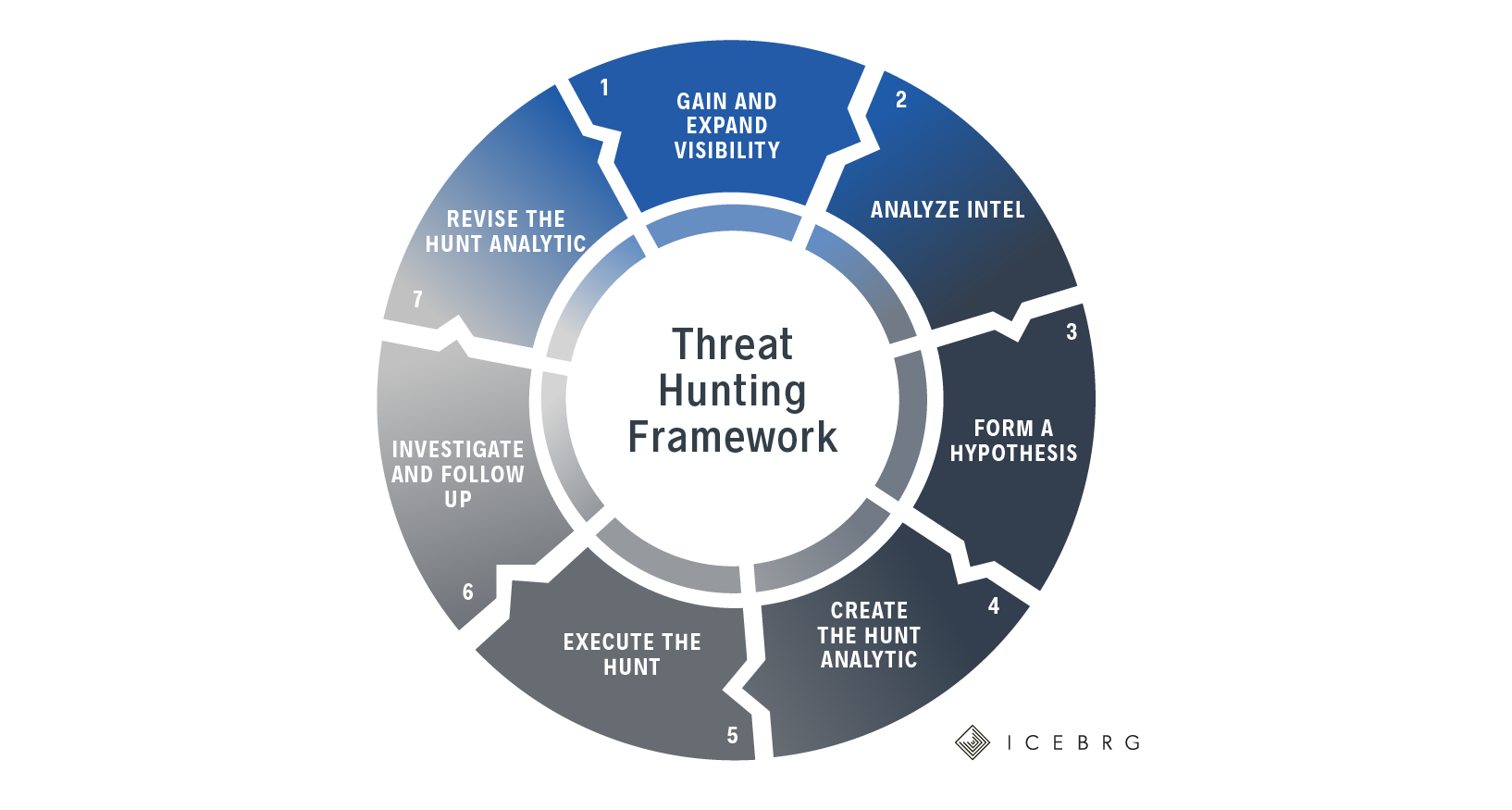
Threat Hunting Template

Threat Hunting Assessments

Threat Report Template Printable Word Searches
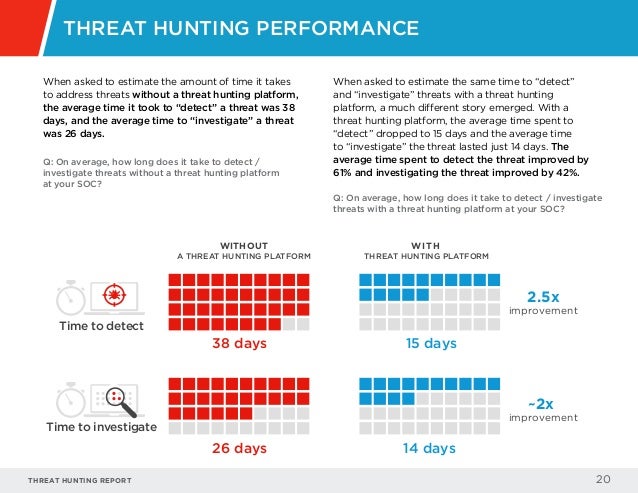
Threat Hunting Report
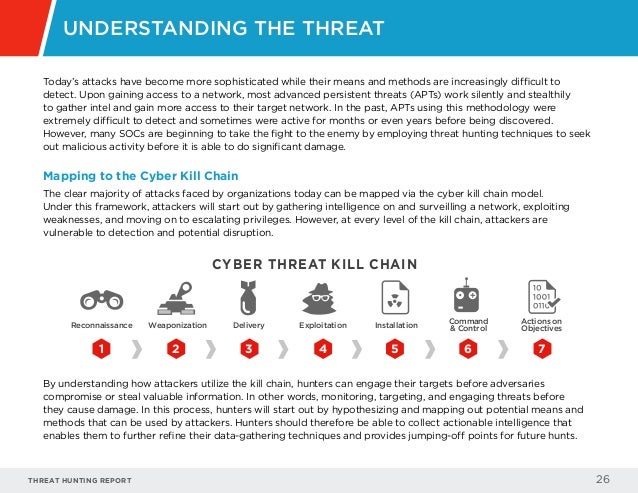
Threat Hunting Report

Report Template for Threat Intelligence and Incident Response
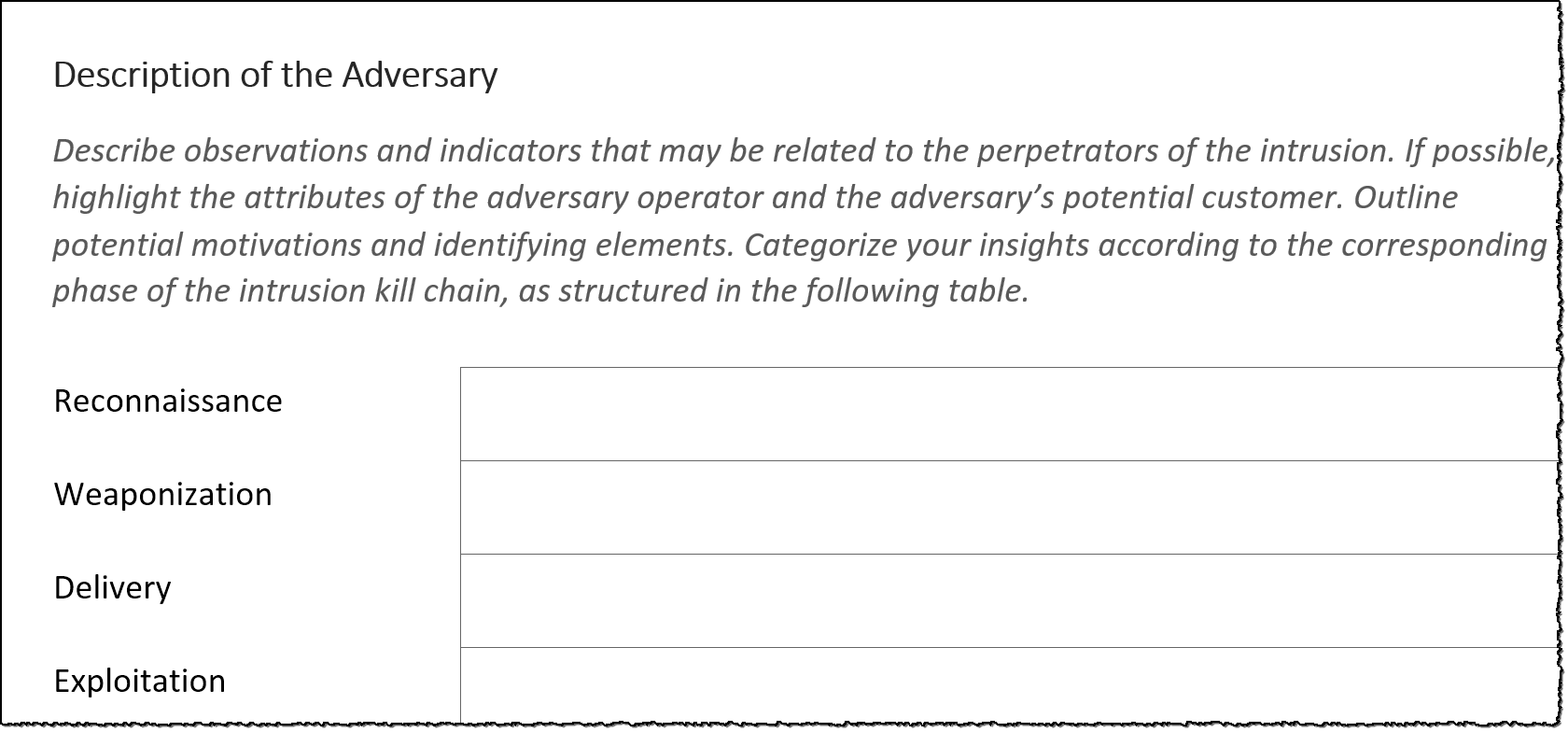
Report Template for Threat Intelligence and Incident Response

Threat Intelligence Report Template

Threat Hunting: Process Methodologies Tools And Tips

Threat Hunting Report: Volt Typhoon

Ir Report Template TEMPLATES EXAMPLE TEMPLATES EXAMPLE

Ir Report Template TEMPLATES EXAMPLE TEMPLATES EXAMPLE

Ir Report Template TEMPLATES EXAMPLE TEMPLATES EXAMPLE
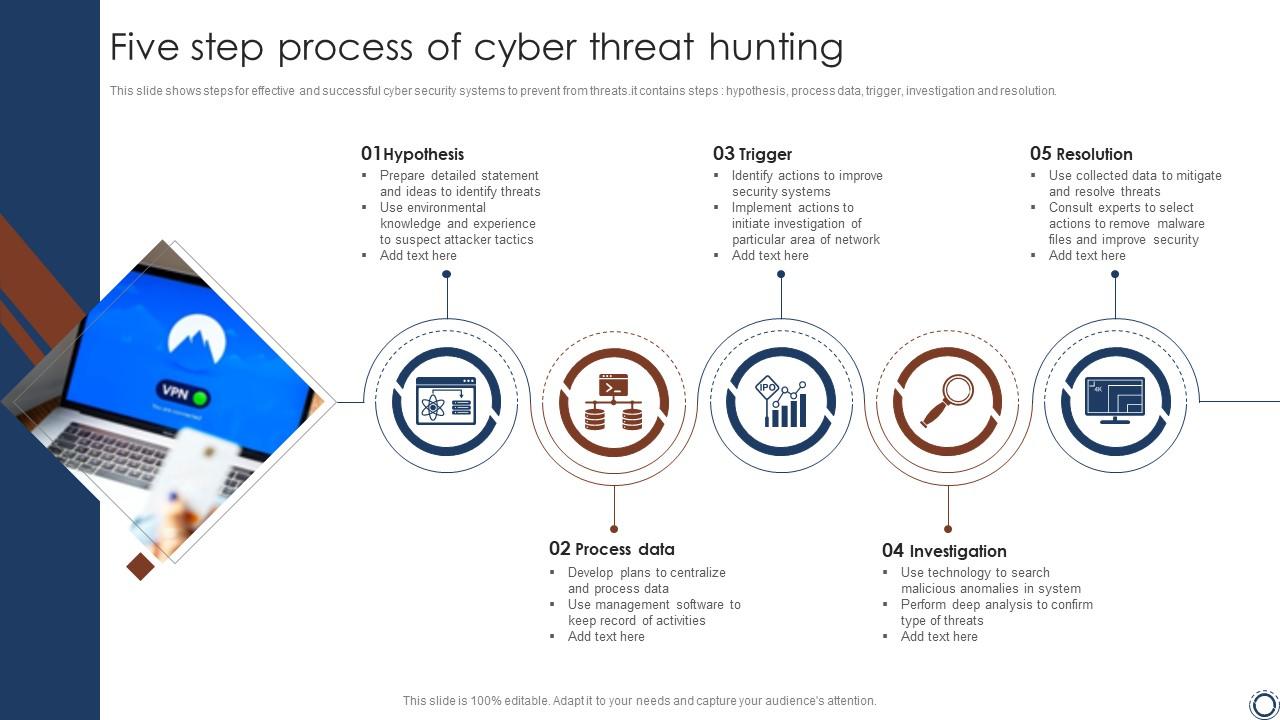
Five Step Process Of Cyber Threat Hunting PPT Slide

Threat Hunting Report: Volt Typhoon
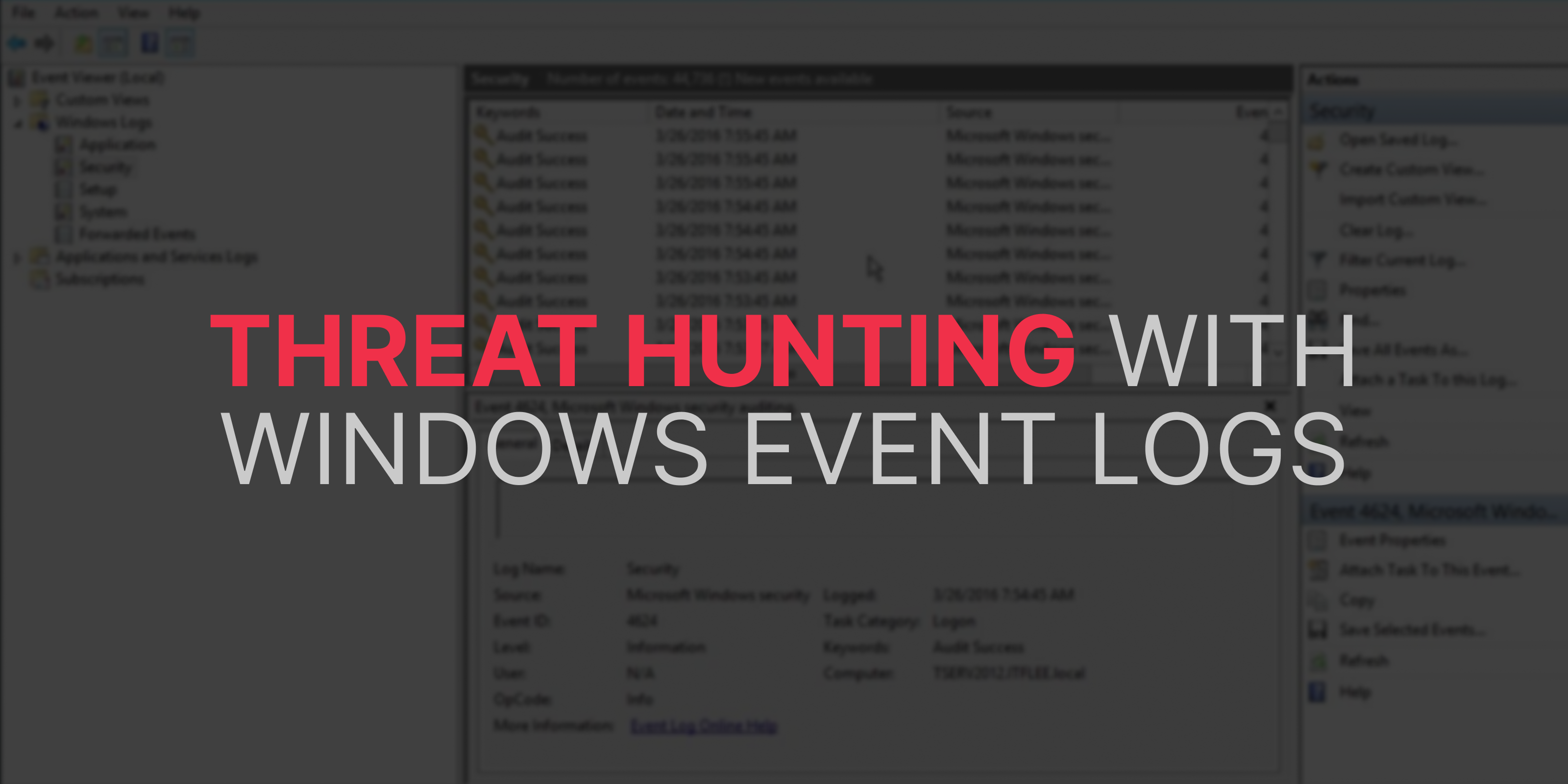
Threat Hunting with Windows Event Logs

Requirements for effective Threat Hunting

Bomb Threat Report form (Free and editable template)

an exemplet laboratory report is shown in the text above it and below
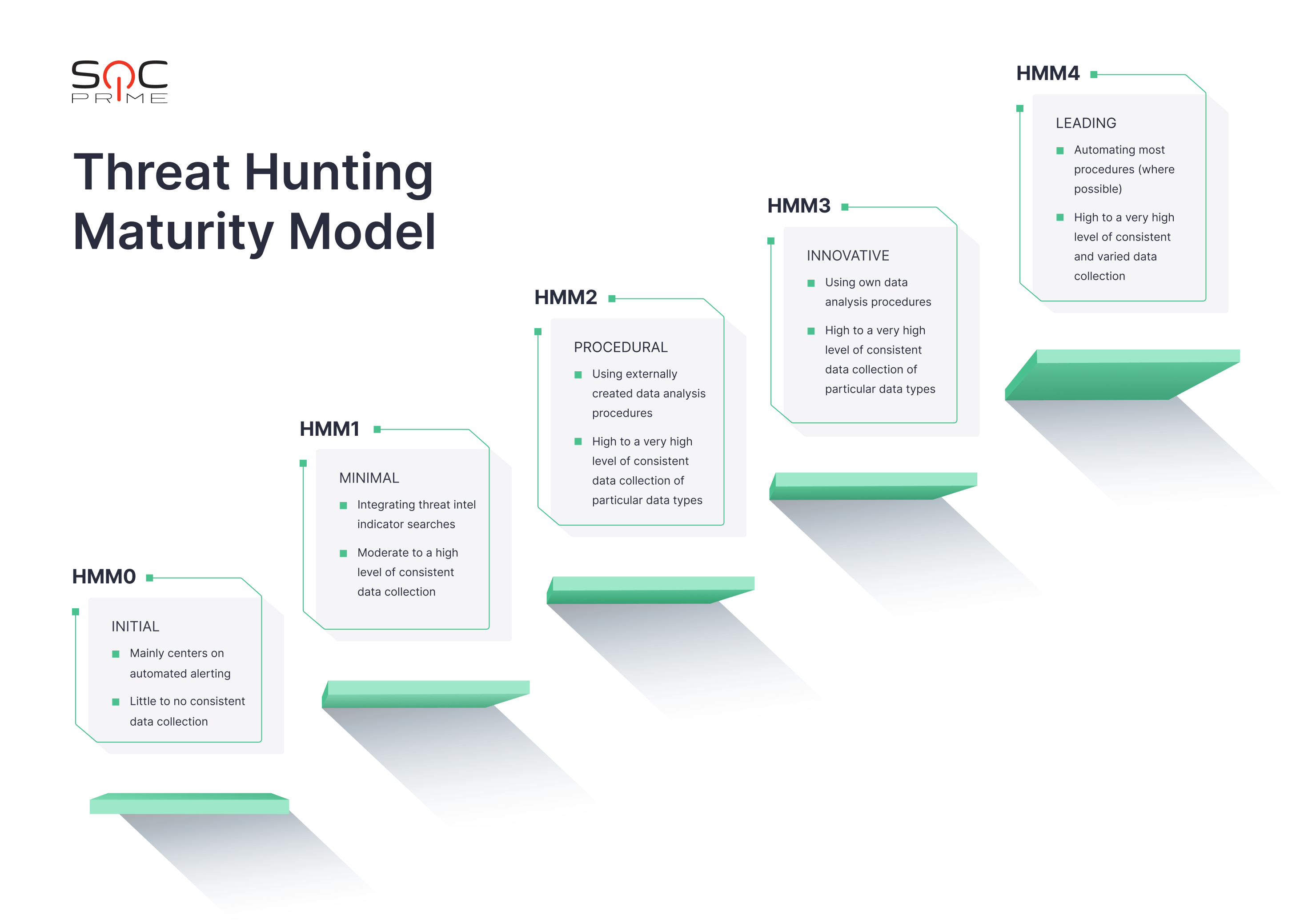
Threat Hunting Maturity Model Explained With Examples SOC Prime

Threat Intelligence Threat Hunting by Anas Affane Aug 2024 Medium

Ir Report Template (6) TEMPLATES EXAMPLE TEMPLATES EXAMPLE Report
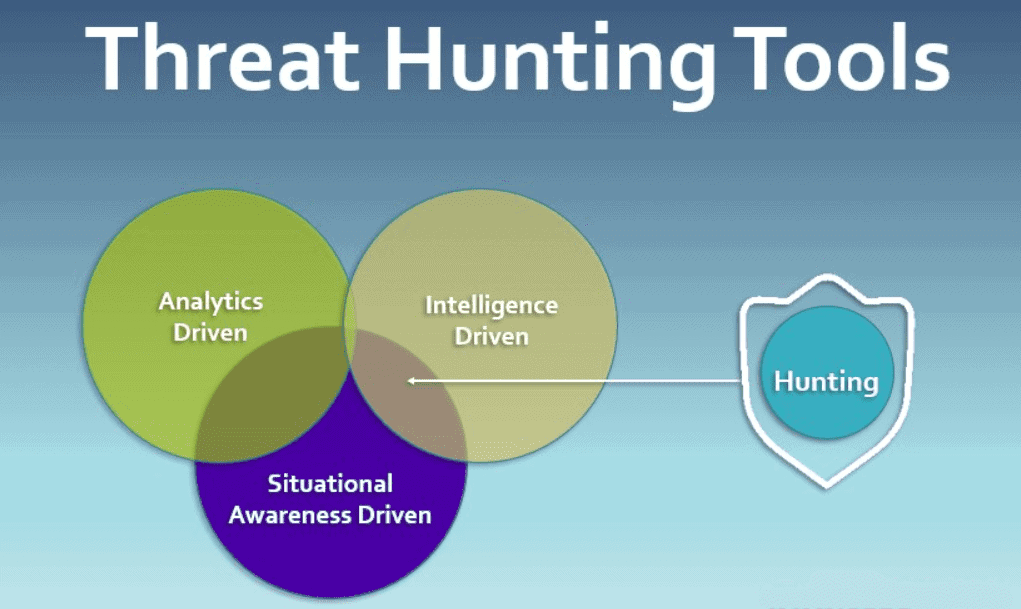
Top 10 Best Threat Hunting Tools in Cyber Security (Pros Cons)

Ir Report Template (1) TEMPLATES EXAMPLE TEMPLATES EXAMPLE Report

Ir Report Template (4) TEMPLATES EXAMPLE TEMPLATES EXAMPLE

2021 Threat Hunting Report Cyentia Cybersecurity Research Library
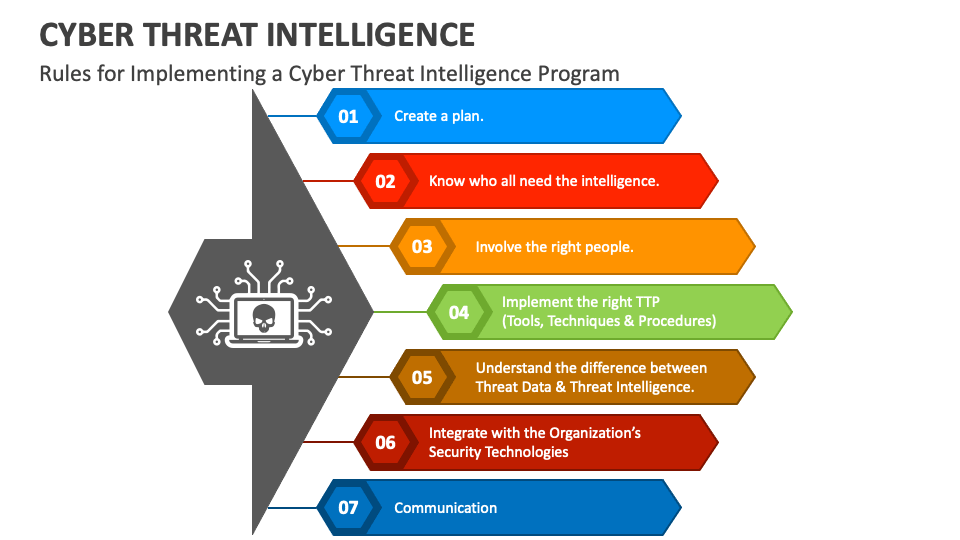
Cyber Threat Intelligence PowerPoint and Google Slides Template PPT

Ir Report Template (1) TEMPLATES EXAMPLE TEMPLATES EXAMPLE Report

CrowdStrike 2023 Threat Hunting Report All About Security

What is Threat Detection Investigation and Response (TDIR)? CrowdStrike

Nowhere to Hide: CrowdStrike Threat Hunting Report 2023
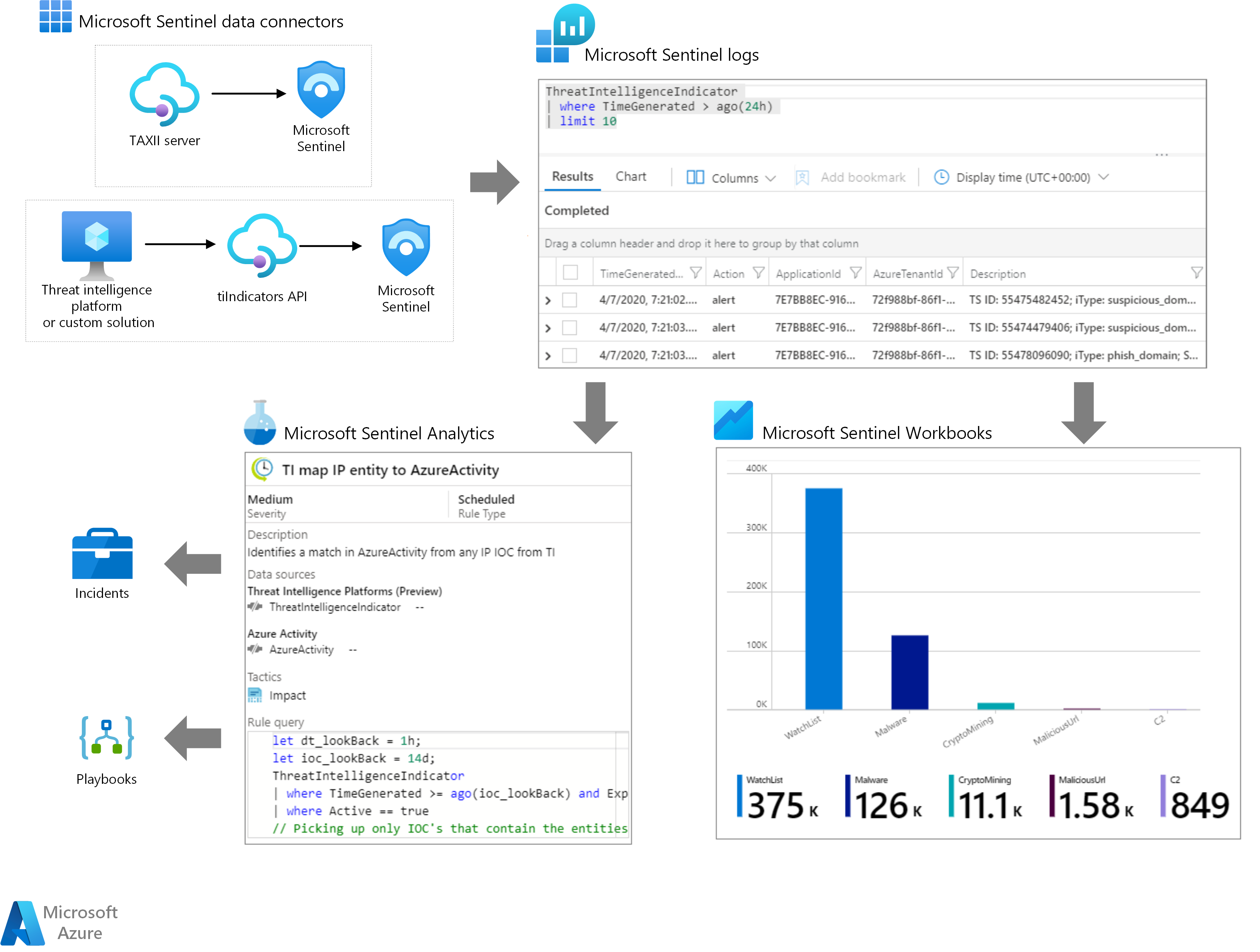
Cyber threat intelligence in Microsoft Sentinel Azure Example

Você sabe o que é Threat Hunting?

Pin on Report Template

Pin on Report Template

Ir Report Template (5) TEMPLATES EXAMPLE TEMPLATES EXAMPLE Cyber

DomainTools The first place to go when you need to know

#microsoftsecurity #ai #cybersecurity #rsac2025 #innovation Vinayak

Vinayak Latthe on LinkedIn: Introducing Microsoft 365 Copilot your

Vinayak Latthe on LinkedIn: Cybersecurity experts predict this will be