Threat Hunting Certifications
Here are some of the images for Threat Hunting Certifications that we found in our website database.

Why Threat Hunting Certifications Will Change Your Life

How Does Proactive Threat Hunting Work Tools Techniques Concertium
Threat Modeling vs Threat Hunting: Understanding the Differences

Gift Video Courses eBooks and Certifications

Top 10 Cyber Threat Intelligence Certifications for 2023 Flare

Cyber Threat Hunting Coursera

Threat Hunting: Strategies and Key Capabilities Fidelis Security

Top 20 Best Threat Hunting Tools in 2025

What is Threat Hunting? The Complete Guide Updated 2025

What is Threat Hunting? The Complete Guide Updated 2025

Cyber Threat Hunting: Types Methodologies Best Practices

Threat Hunting and Threat Hunting Frameworks by Chemiron Adam Medium

Cyberthreat Hunting Threat Hunting Gcore

Certified Threat Hunting Professional • Emilio Pancubit • INE Expert

What is Threat Hunting? Check Point Software

Threat Hunting using Proxy Logs Soc Incident Response Procedure
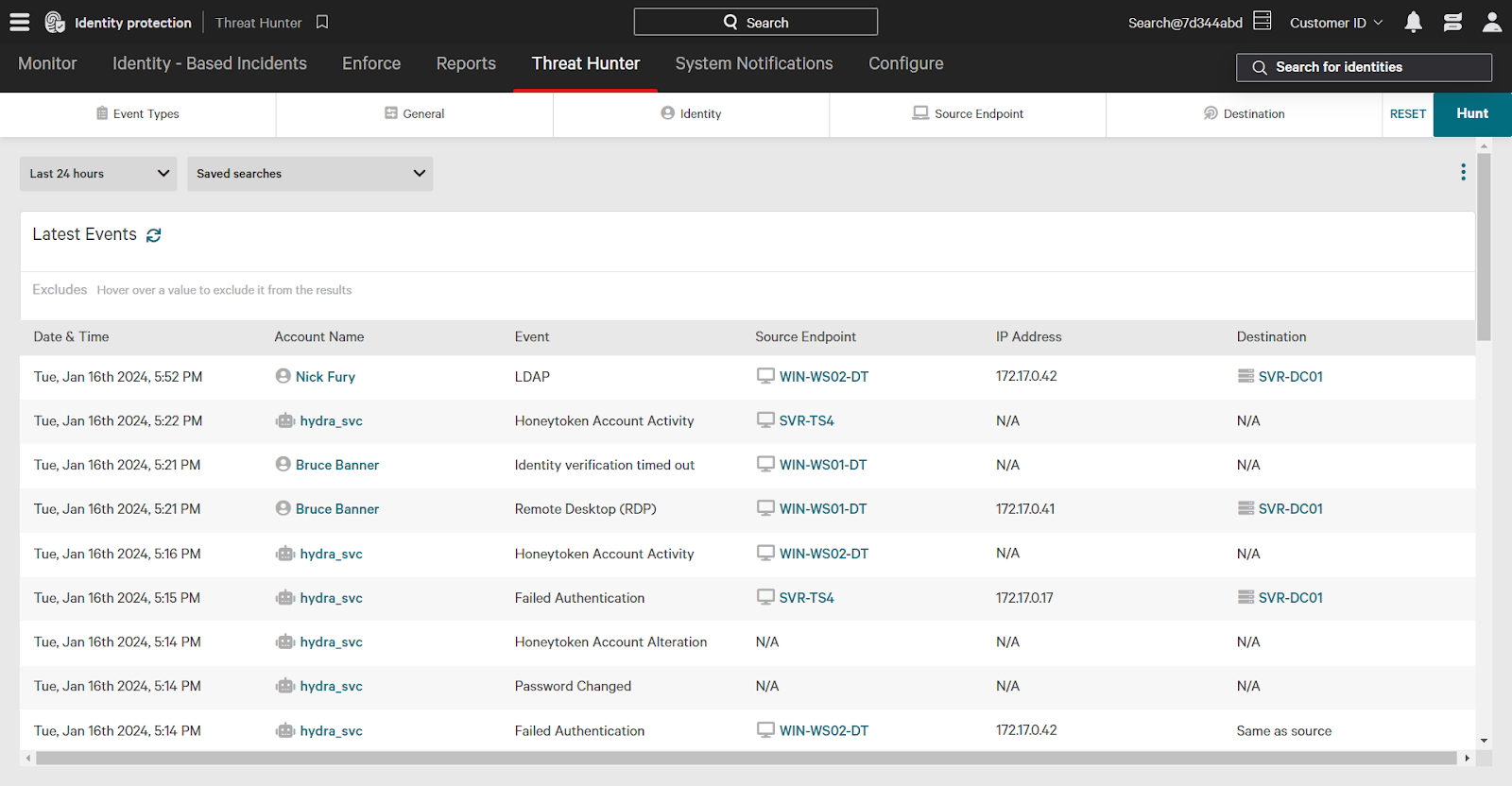
Threat Hunting With Falcon Identity Protection Tech Hub

Threat Hunting and Detection Engineering Certification Credly

FOR508™: Advanced Incident Response Threat Hunting and Digital

A Deep Drive on Proactive Threat Hunting

Best SOC Analyst Certifications in 2025

Entrenamiento en Caza de Amenazas Certificación y Aprendizaje en Línea
Threat Hunting Introduction TryHackMe Write Up by Joseph Alan Medium

Security Blue Team Certifications Freelancer

🛡️ Leveraging Wazuh AI for Threat Hunting My End to End Lab

Threat Hunting Metrics: The Good Metrics to Focus On by Danny Jan

Cyber Threat Intelligence

Cyber Threat Maps : Threat Intelligence by Kavitha Bangalore Medium

Threat Intelligence Analyst: Key Job Roles and Requirements for Success

Certified Threat Hunting Professional • Dario Ojeda • INE Expert IT

Hunting Impacket Part 3 Impacket Enumeration/System Tools by Raven

Elevate Xchange on LinkedIn: Cybersecurity Job Hunting May Come Down to

Microsoft Defender Experts for Hunting proactively hunts threats

FOR508: Advanced Incident Response Threat Hunting and Digital

Training Wood Lake Kennels

Blog Igor sec #39 s Blog

MAD20 MITRE ATT CK Training and Certifications for Practitioners

SANS Cyber Security Certifications Research

SANS Cyber Security Certifications Research

SecurityTube Strengthen your resume with our API security badges

Life at Virtusa Sri Lanka Life at Virtusa Sri Lanka

20 Best Cybersecurity Memes That Will Make You LOL

20 Best Cybersecurity Memes That Will Make You LOL

20 Best Cybersecurity Memes That Will Make You LOL

Erick Velazquez Certified cybersecurity professional looking for

I #39 m happy to share that I have successfully passed GNFA from GIAC
STRRAT: Malware Analysis of a JAR archive ANY RUN #39 s Cybersecurity Blog

OSCP Exam Guide: What to Expect How to Pass First Time
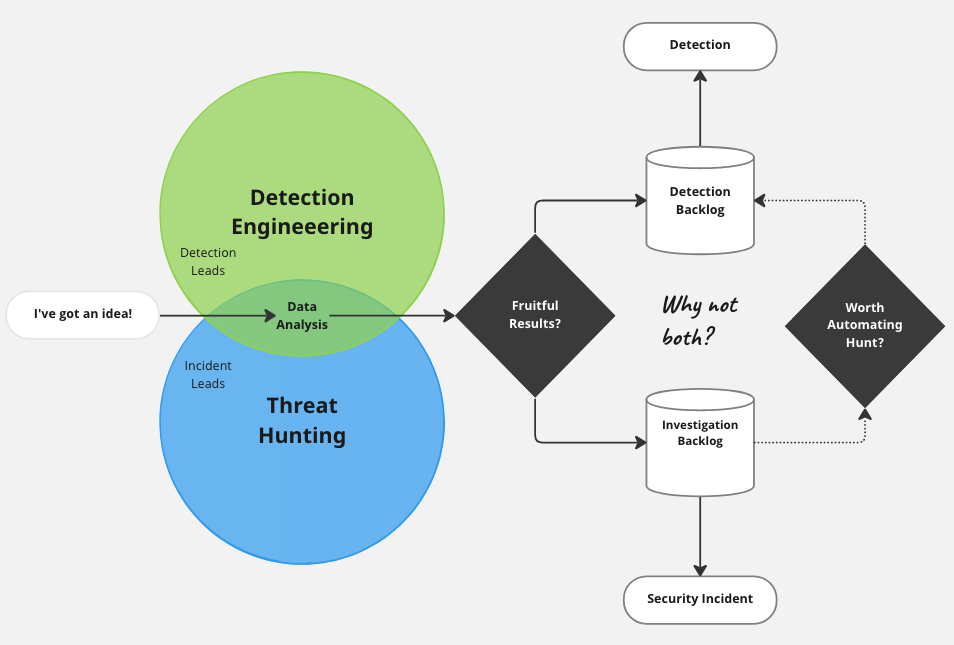
Detection Engineering Series: Detection Engineering Explained by

How is AI Transforming the Cybersecurity Landscape? USCSI® PDF

Hey gents any feedbacks with the FOR578 by SANS (threat intelligence

CyberChef : Cyber Swiss Army Knife by Adarsh Pandey Medium

TryHackme AtomicRedTeam WriteUp by DefenderFela Medium

Blockchain in Cybersecurity Protecting Data Integrity by RocketMe

Preparing for a Cyber Security Career in Emerging Technologies pdf

Red Team vs Blue Team: Strategies for AdvancedTesting

Miguel Angel De Castro Navaja Negra Conference Albacete

DevOps 보안은 좌측으로 이동하지만 해커를 통과하려면 수 마일이 소요됨 : 네이버 블로그

La Plateforme OpenCTI Installation guidée by Daouda Diallo Medium
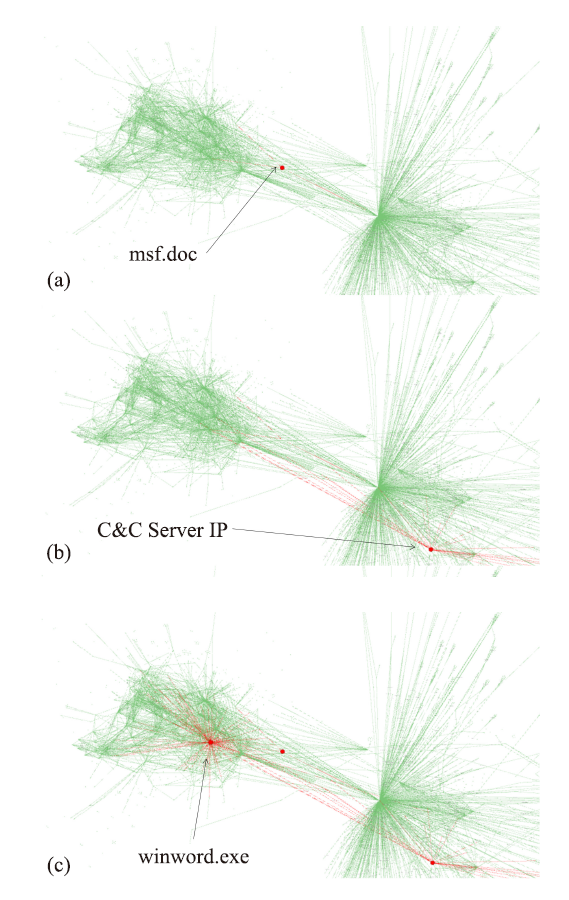
数据驱动的威胁狩猎语言模型研究进展