Threat Hunting Certification
Here are some of the images for Threat Hunting Certification that we found in our website database.

Cyber Threat Hunting Capability Certification
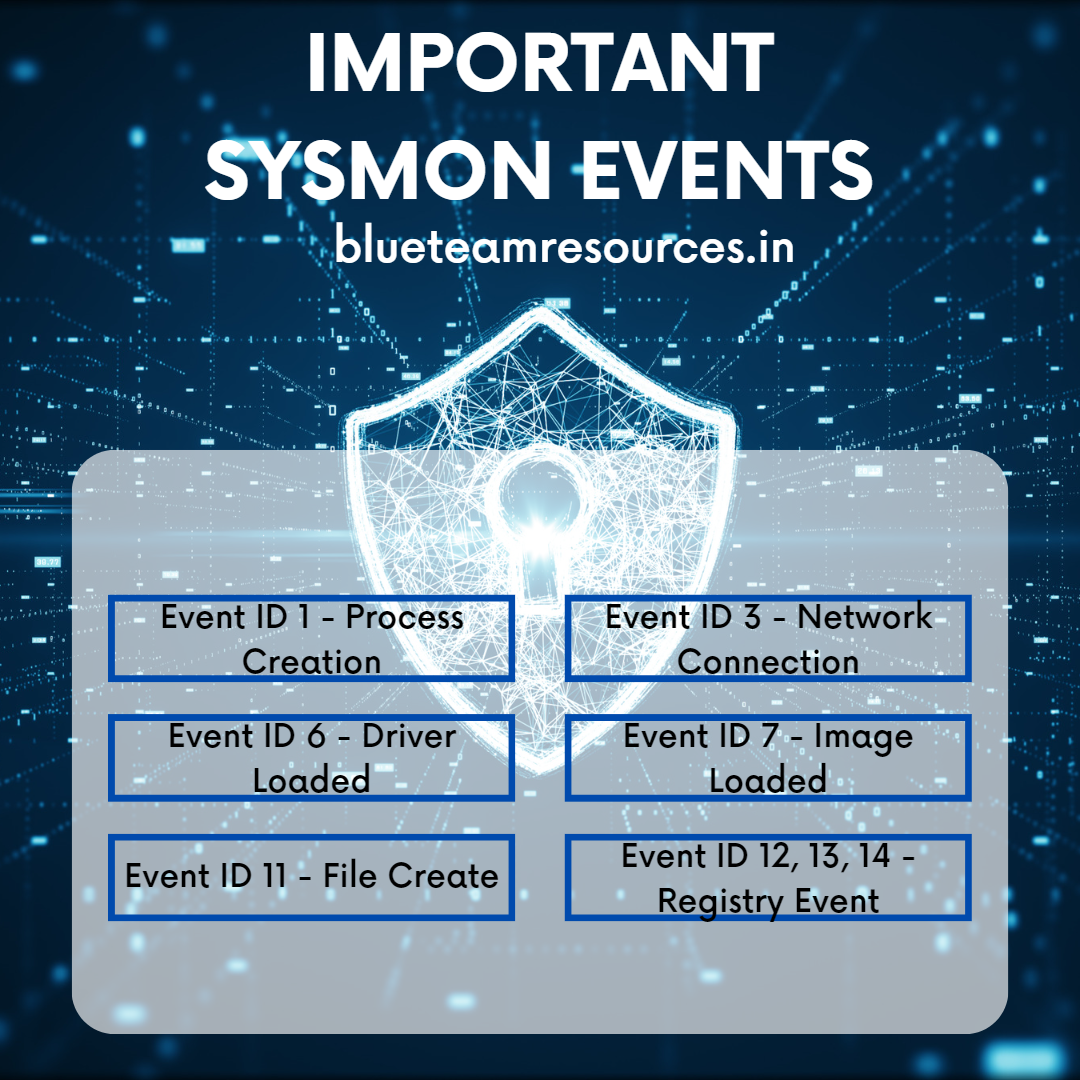
Threat Hunting Blue Team Resources

New eCTHP Certification: Master Real World Threat Hunting INE

New eCTHP Certification: Master Real World Threat Hunting INE
Threat Hunting Methods PenTesting Org

Threat Hunting Course Expert Training

Threat Hunting Training Certification and Online Learning : r/SOCPrime

Cyber Threat hunting training CTH Training CTH 1191

SecurityTube 🎯 Ready to level up your threat hunting game? The

INE Security Launches Updated Certified Threat Hunting Professional

Cisco Certified Specialist Threat Hunting and Defending (300 220) CBRTHD

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Cyber Threat Hunting: Types Methodologies Best Practices

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

PPT SentinelOne IR 2 Threat Hunting Certification Exam (S1 301

I m excited to share that I ve officially earned the Certified Threat

BEST 7 Threat Hunting Certifications in 2025

eLearning Security Threat Hunting Professional Certification ~ An

Threat Hunting and Detection Engineering Certification Credly

Cyber Threat Hunting Certification Training Boot Camp Infosec

Ling Yang on LinkedIn: ATT CK Threat Hunting and Detection Engineering

Threat Hunting: A Proactive Approach to Identifying and Neutralising

Aaron Furlong on LinkedIn: Just attained my Cyber Threat Hunting
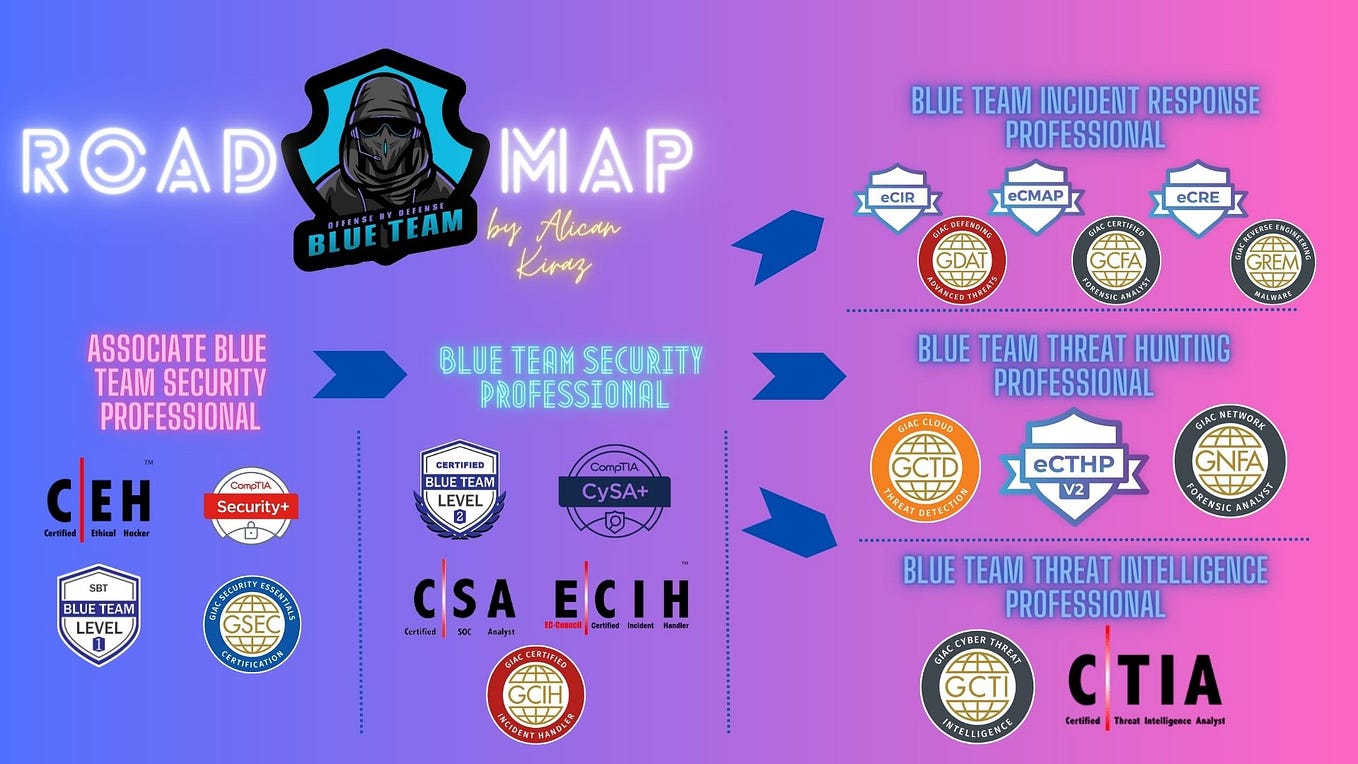
Threat Hunting for Windows Event Logs by Alican Kiraz Medium
eCTHP Certification Guide: Threat Hunting Professional

CEH Certification Overview PenTesting Org

Threat Hunting with Velociraptor Cybersecurity threats are constantly

#soc analyst #threat hunting #cybersecurity #certification #blueteam #

How to Build and Measure an Effective Threat Hunting Program ThinkCloudly

Just completed a comprehensive course on threat hunting with

Certified Threat Hunting Professional v2 (eCTHPv2) Review by Ismayil
Threat Hunting Summarizing the Techniques Used in Security

HITRUST Certification: Everything You Need To Know

Cybersecurity Certification for Contractors Autonomos AI Threat Hunting

eCTHPv2 Certification eLearnSecurity Certified Threat Hunting

Completed Threat Intelligence and Hunting certification Subhash J

Vendor Specific Vs Vendor Neutral Certification in Cloud Security

OffSec Launches New Incident Response Course Certification to Help

MITRE ATT CK Framework For Threat Hunting Seth Brunt and Abby Warnes

ATT CK Threat Hunting and Detection Engineering Certification • MITRE

Tekikons Academy

GuideM 🔒 2024 is the Year of Security Excellence Make

🎉 Thank you Nashville for an incredible Dark Lab event A huge