Ssl Certificate Signed Using Weak Hashing Algorithm
Here are some of the images for Ssl Certificate Signed Using Weak Hashing Algorithm that we found in our website database.

Solved: 9800 L F WLC SSL Certificate Signed Using Weak Hashing

SSL Certificate Signed Using Weak Hashing Algorithm Vulnerability
SSL Certificate Signed Using Weak Hashing Algorithm turingsecure

Ssl Certificate Signed Using Weak Hashing Algorithm prntbl

Ssl Certificate Signed Using Weak Hashing Algorithm prntbl

Ssl Certificate Signed Using Weak Hashing Algorithm prntbl

Ssl Certificate Signed Using Weak Hashing Algorithm prntbl

Ssl Certificate Signed Using Weak Hashing Algorithm prntbl
Ssl Certificate Signed Using Weak Hashing Algorithm prntbl

SSL Certificate Signed Using Weak Hashing Algorithm in windows server

SSL Certificate Signed Using Weak Hashing Algorithm in windows server
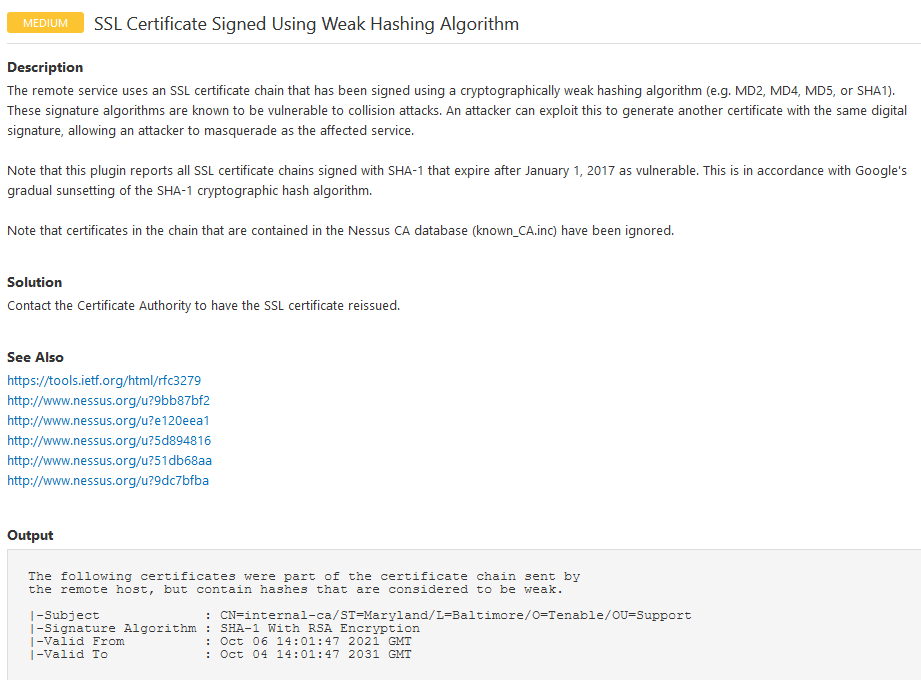
How to whitelist a CA from plugin 35291 quot SSL Certificate Signed Using
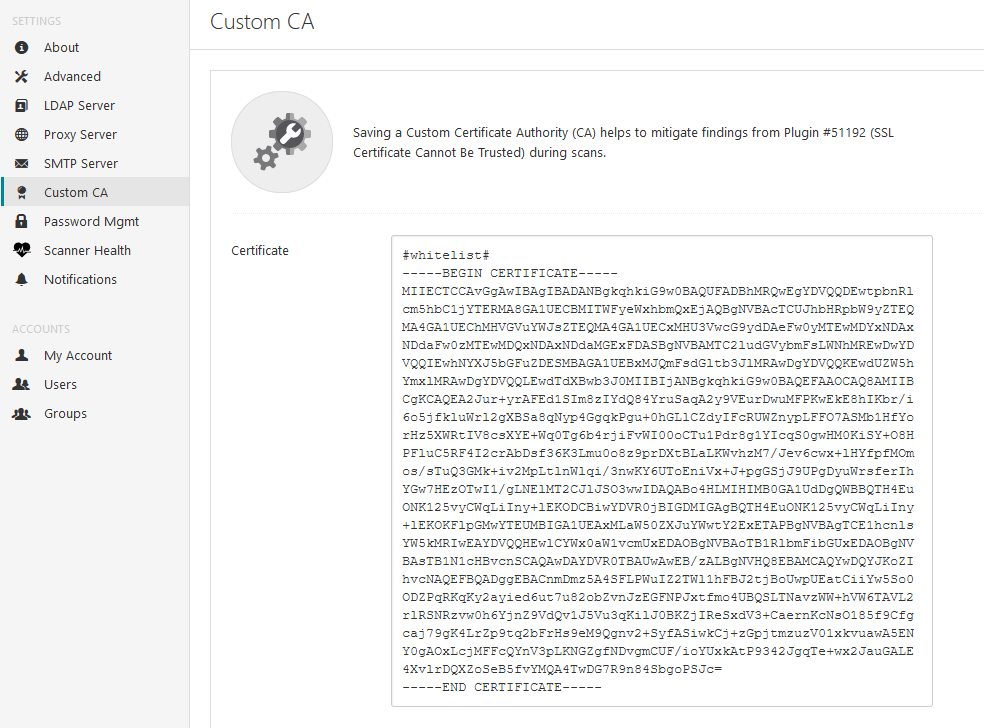
How to whitelist a CA from plugin 35291 quot SSL Certificate Signed Using

How to whitelist a CA from plugin 35291 quot SSL Certificate Signed Using
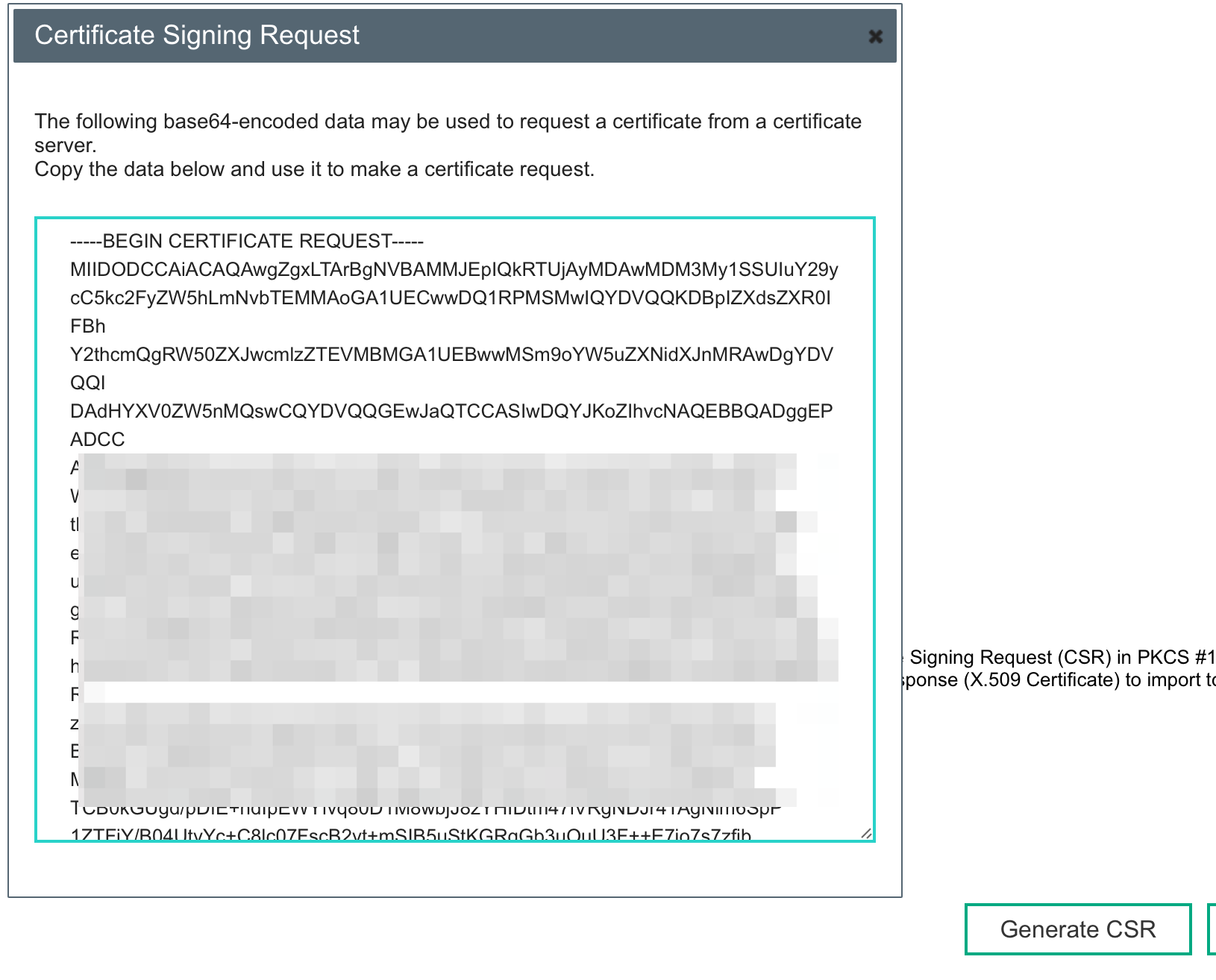
HP iLo 4 Weak Hashing Algorithm Patch megaw co za
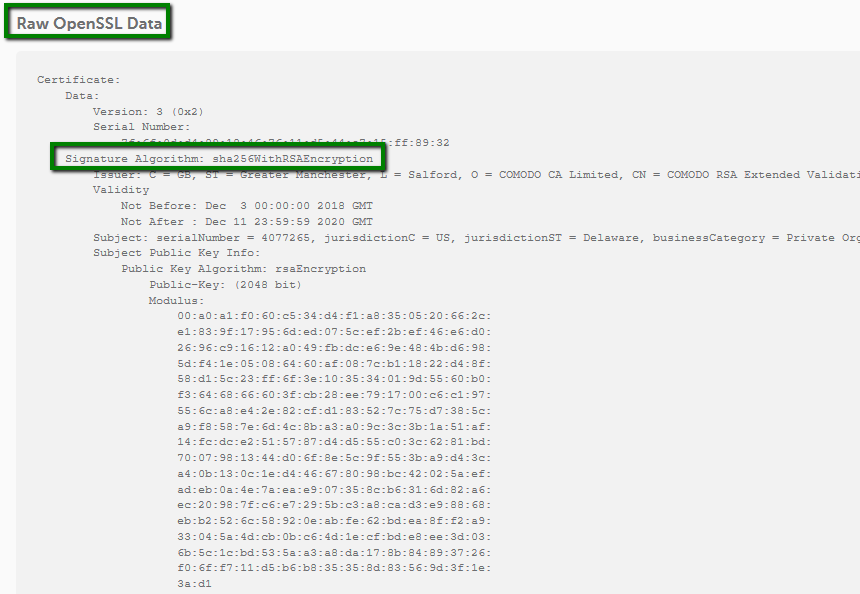
How do I check my hashing algorithm? SSL Certificates Namecheap com
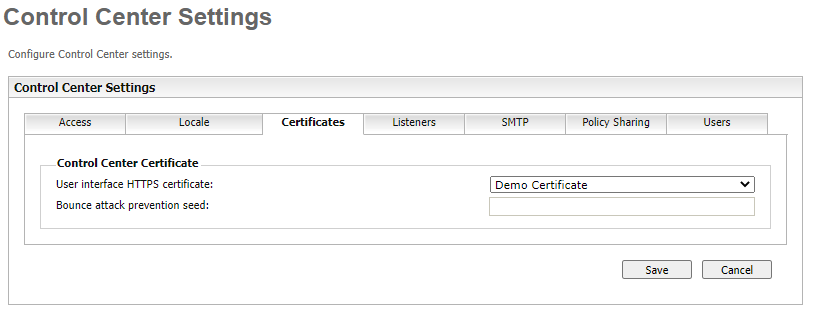
has been added to administration certificates the control center web
What Is Hashing In Cryptography? Crypto Legacy
SSL Self Signed Fallback SQL Server Der Windows Papst IT Blog Walter
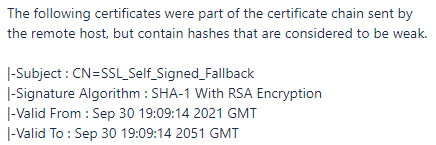
SSL Self Signed Fallback SQL Server Der Windows Papst IT Blog Walter

Migrating AD certificate services to SHA 2: Considerations and

CVE 2004 2761 High Level Vulnerability Observed: SSL Certificate

Nessus Vulnerability Scan ppt download

SSL Certificate Signed Using Weak Hashing Algorithm Tenable®

SSL Certificate Signed Using Weak Hashing Algorithm Tenable®
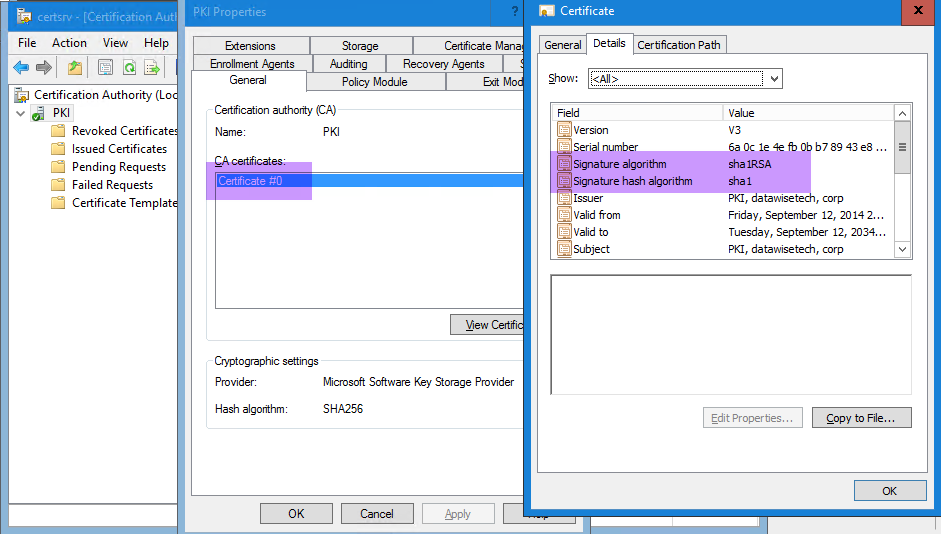
Rsa256
.jpeg)
Protecting Against Weak Cryptographic Algorithms Microsoft Learn

Sr2T Converts Scanning Reports To A Tabular Format
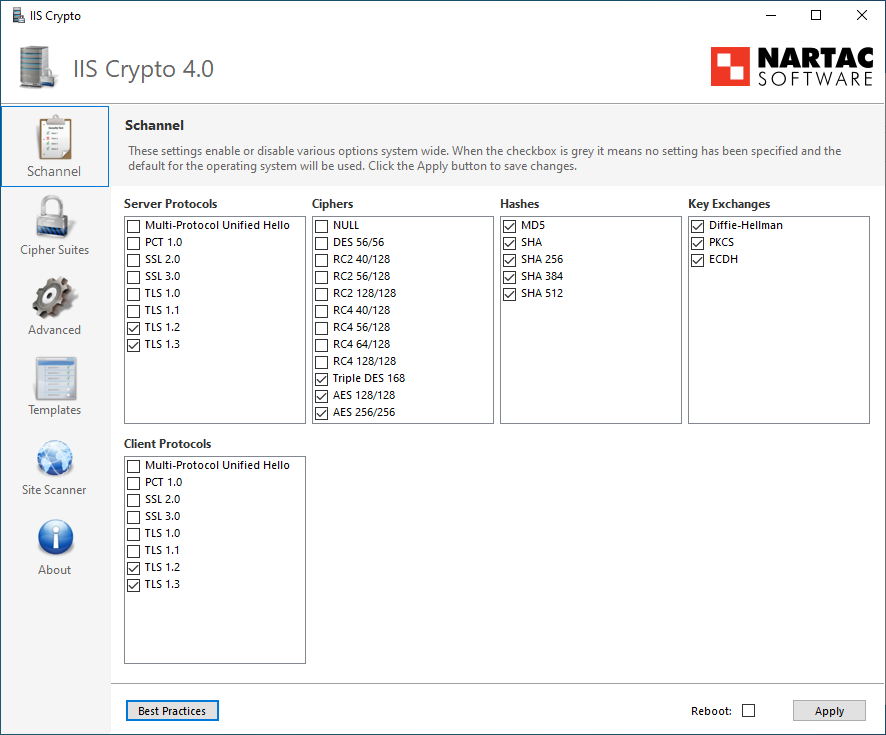
Nartag

Nartac

SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) 源码巴士
【漏洞复现】CVE 2004 2761 使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【漏洞复现】CVE 2004 2761 使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

SSL Certificate Signed Using Weak Hashing Algorithm 使用弱哈希算法签名的 SSL 证书的

SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
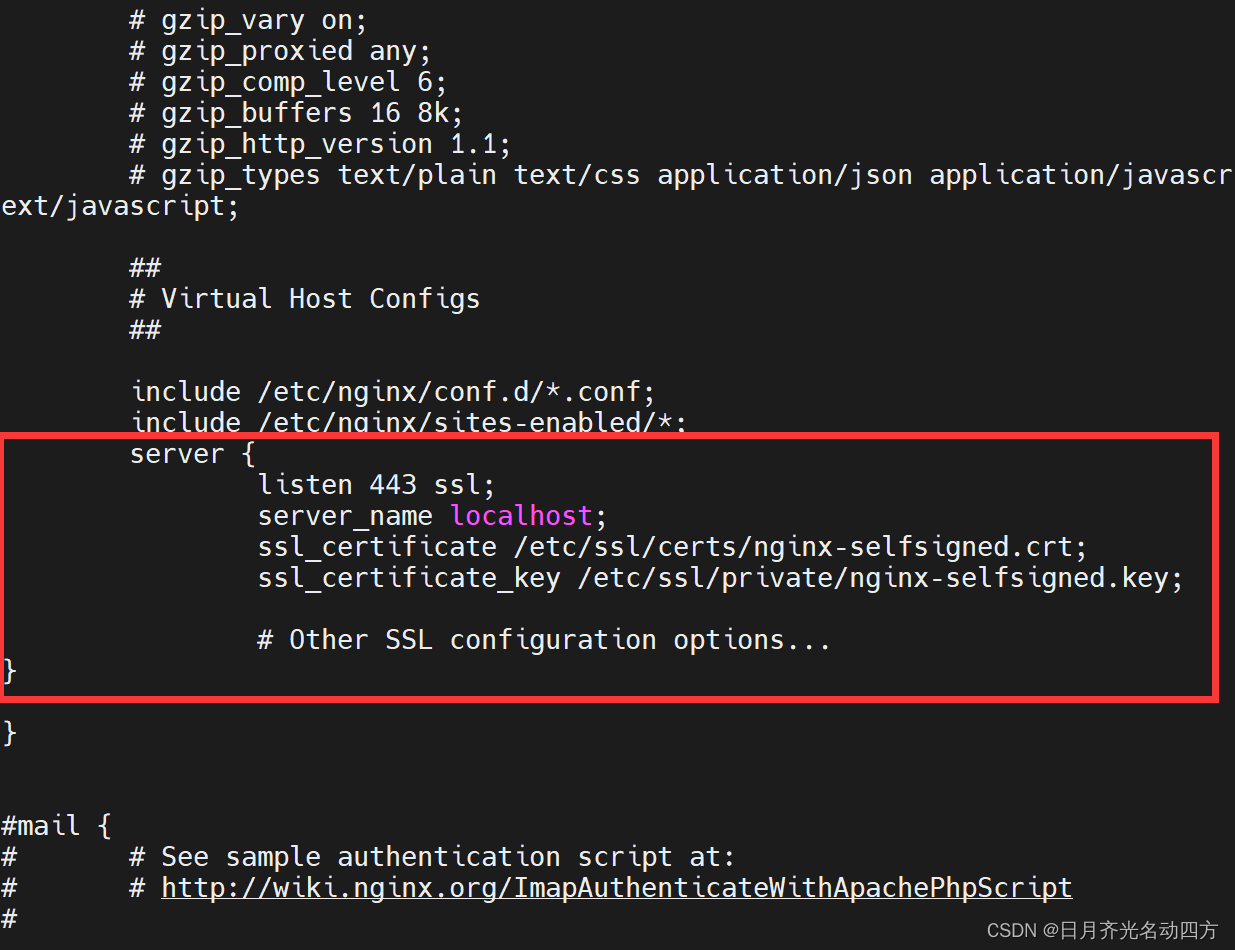
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
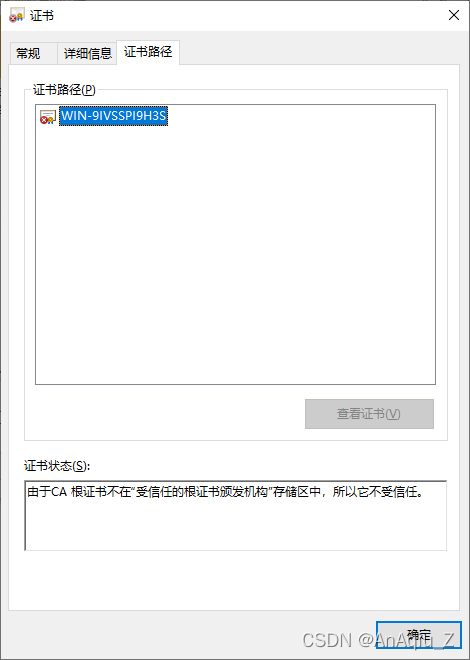
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
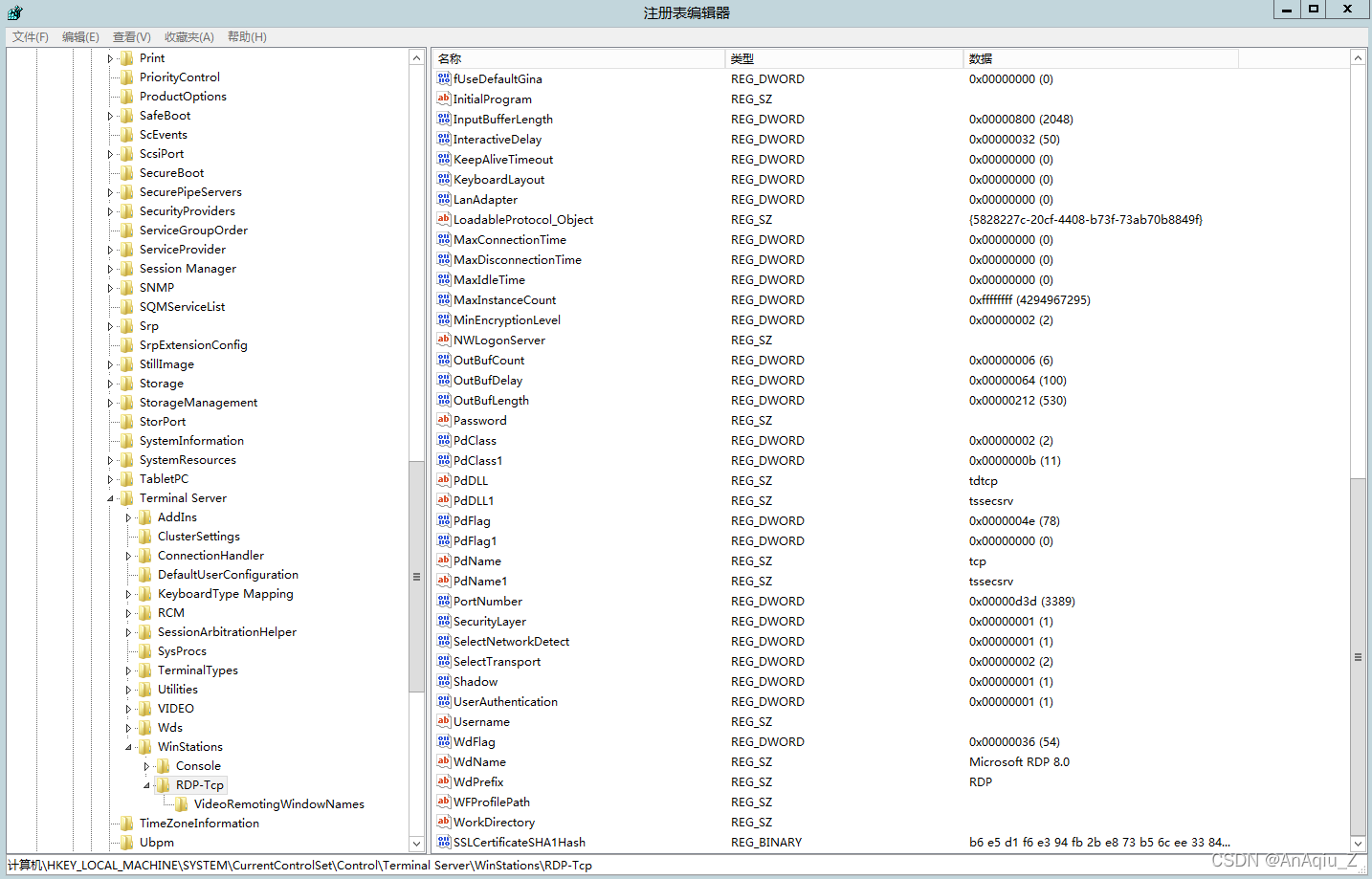
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
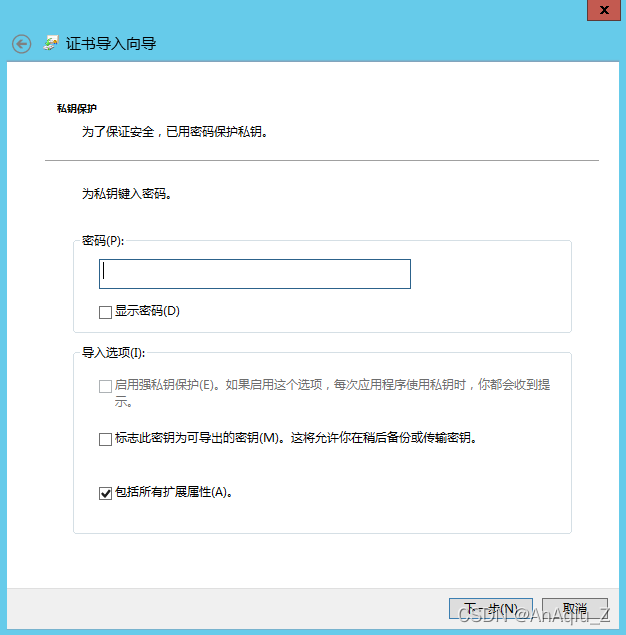
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
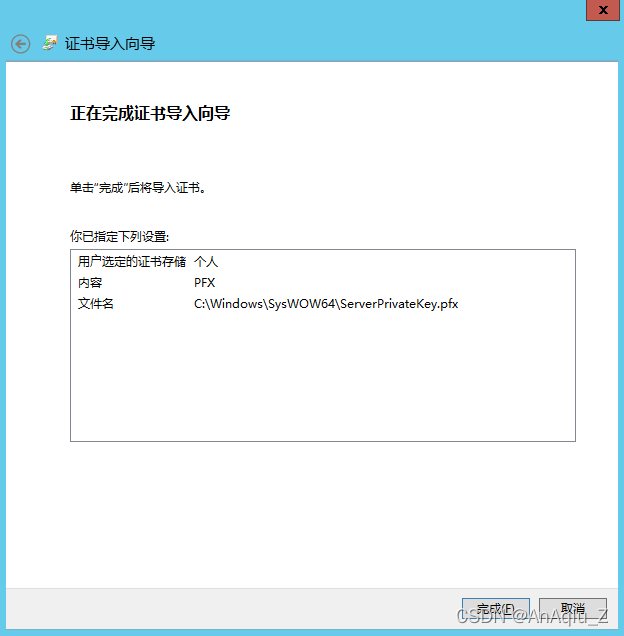
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客

SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客

SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
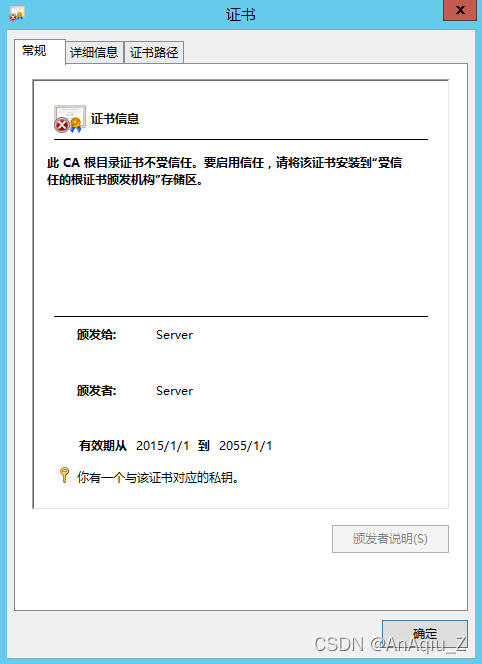
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
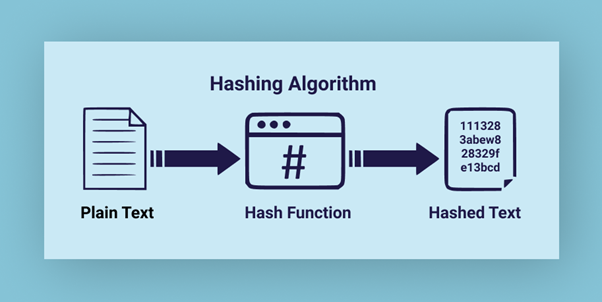
Yuk Berkenalan dengan Cryptography School of Information Systems
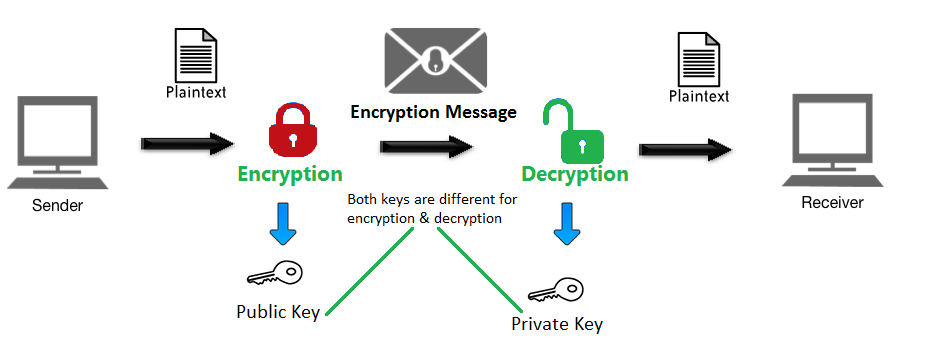
Public key retrieval is not allowed Telegraph
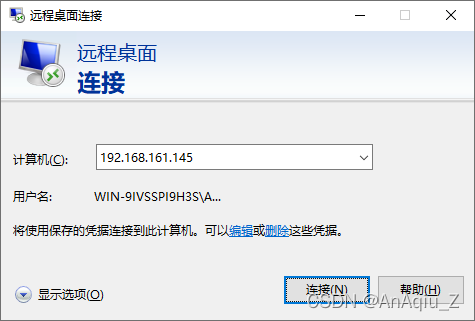
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客

【漏洞复现】CVE 2004 2761 使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【精选】SSL Certificate Signed Using Weak Hashing Algorithm 使用弱哈希算法签名的 SSL