Ssh Certificate Authentication
Here are some of the images for Ssh Certificate Authentication that we found in our website database.

What is the Secure Shell (SSH) Protocol? How Does it Work?
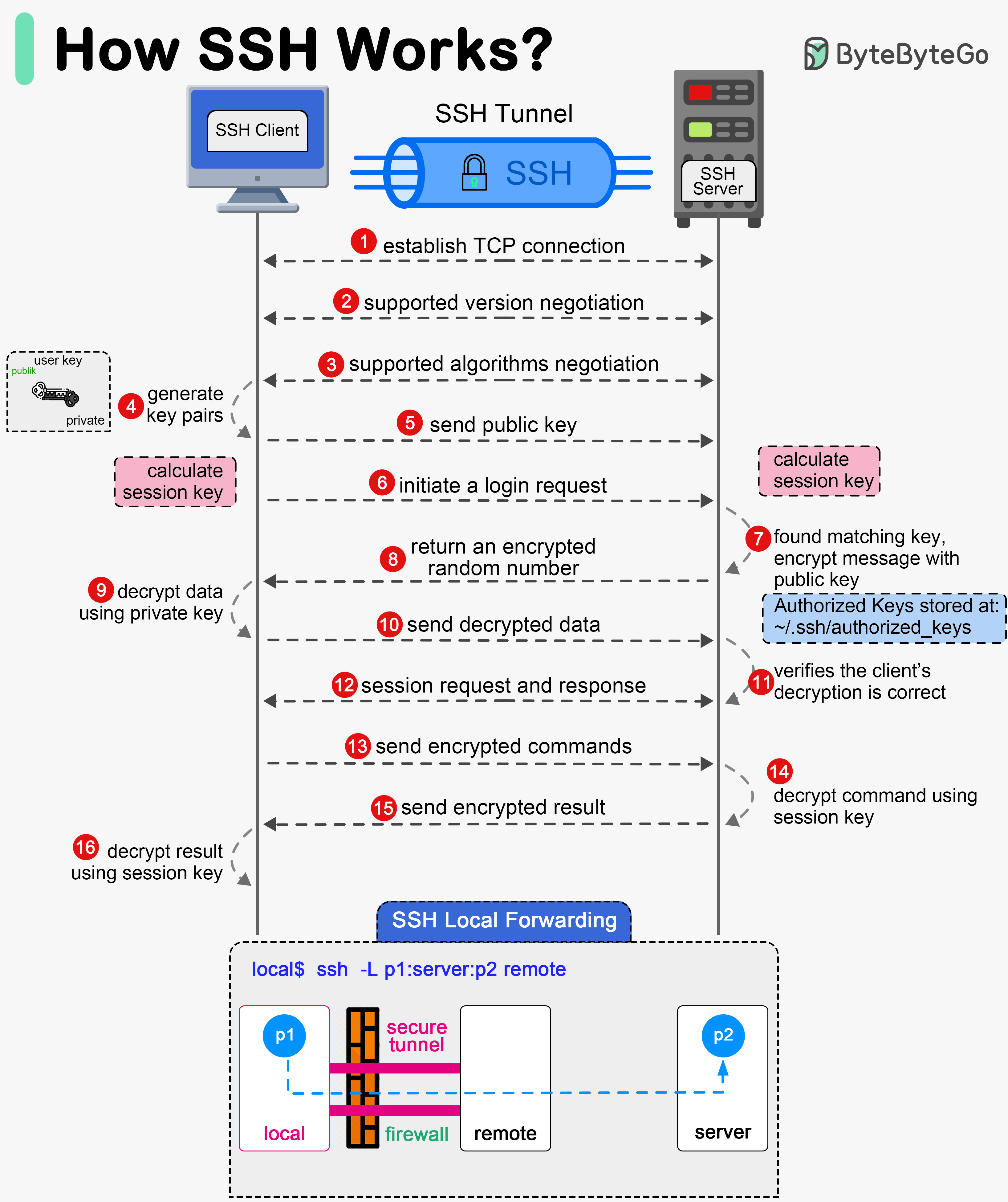
ByteByteGo How does SSH work?

Solar PuTTY: El Cliente SSH para entornos Windows

Todo lo que necesitas saber sobre el Protocolo Secure Shell (SSH

SSH vs FTP: What #39 s the Difference? UltaHost Blog

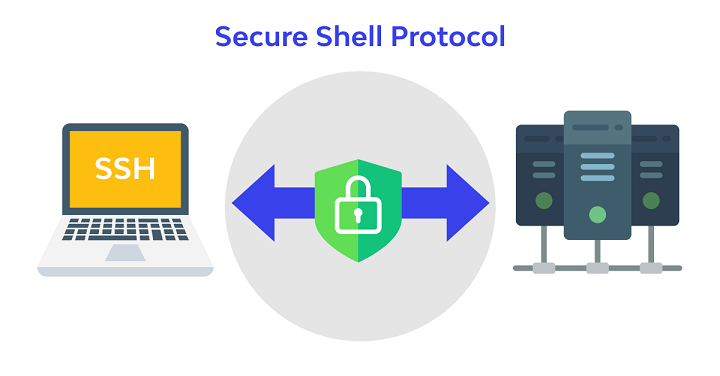
Secure Shell (SSH)

How to Secure SSH on Linux servers Ubuntu/CentOS/Fedora Tutorial

Introduction to SSH (Secure Shell) by Aqeel Abbas Medium
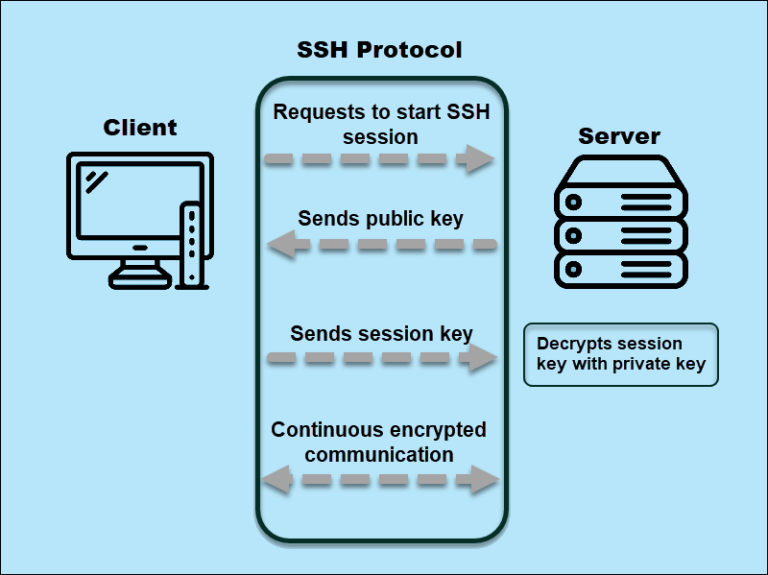
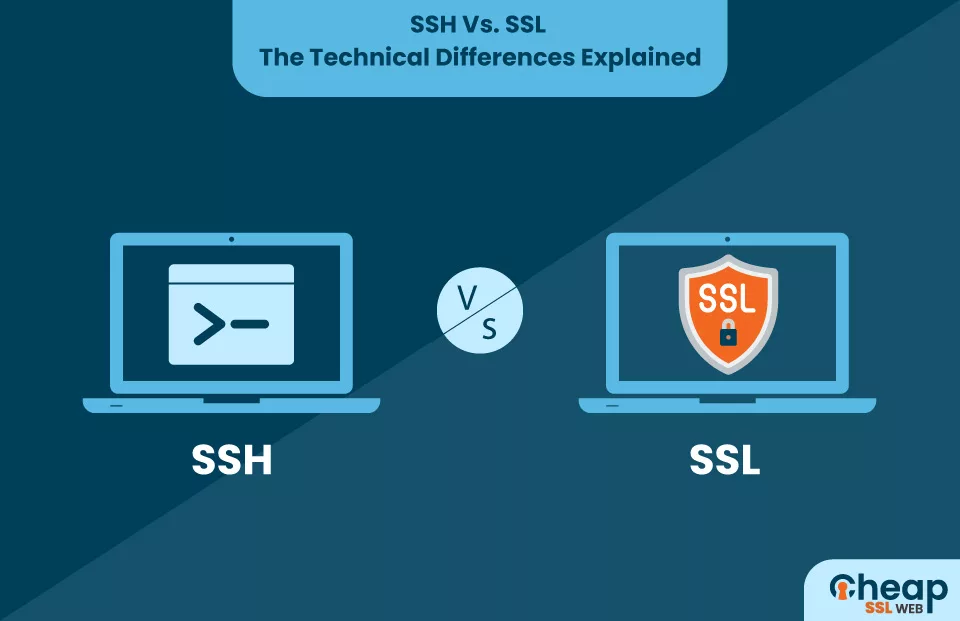
SSH vs SSL: What Are the Differences?
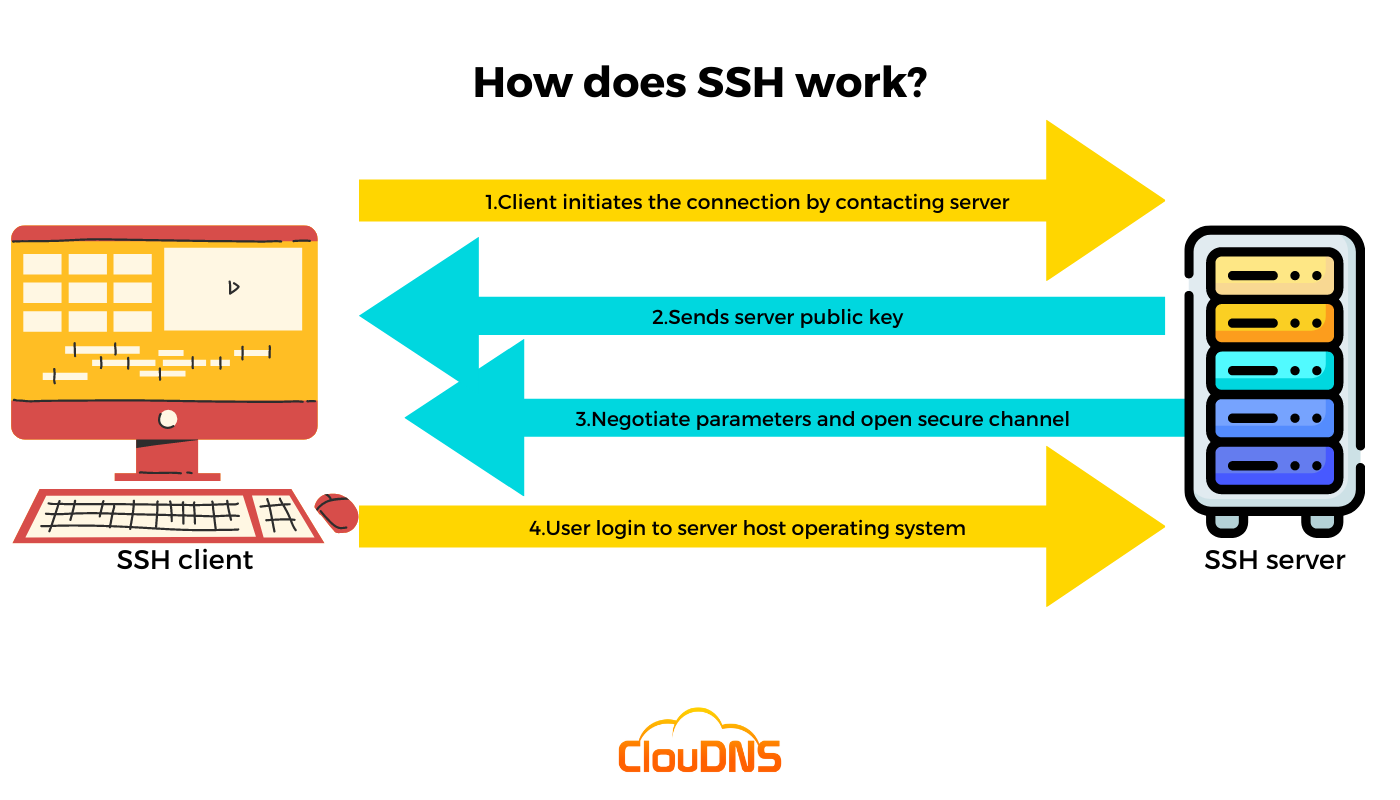
SSH Là Gì? Tìm Hiểu Về Giao Thức Bảo Mật Và ứng Dụng Quản Lý Máy Chủ
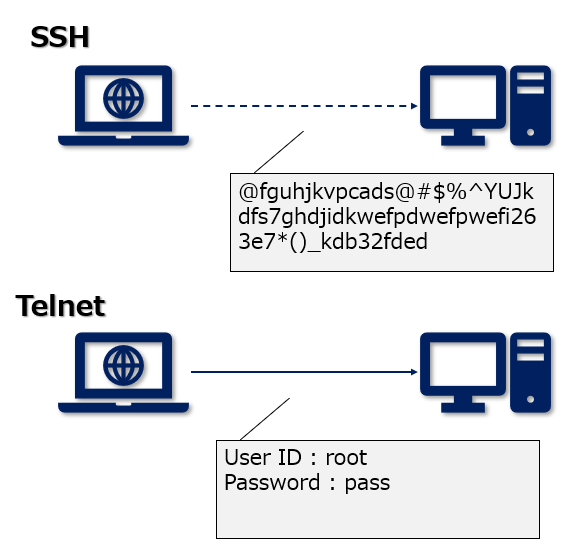
SSH(Secure Shell)とは?初心者向けにわかりやすく3分で解説 ビズドットオンライン
.png)
What Is SSH? Key to Improving Remote Access Security

Comment installer SSH sur Ubuntu
SSH vs SSL/TLS: Difference Similarities and Working
SSH là gì? Tìm hiểu tất cả kiến thức về giao thức SSH chi tiết

SSH vs Telnet : l #39 option la plus sûre pour l #39 accès à distance 2023

Comment changer le port SSH dans Ubuntu

SSH Todo lo que Necesitas Saber y cómo Utilizarlo

What is SSH? Beginner #39 s Guide to Remote Access SiteGround KB

Jak korzystać z protokołu SSH w systemie Windows

Konfigurasi SSH Server Pada Debian 11 ditempel
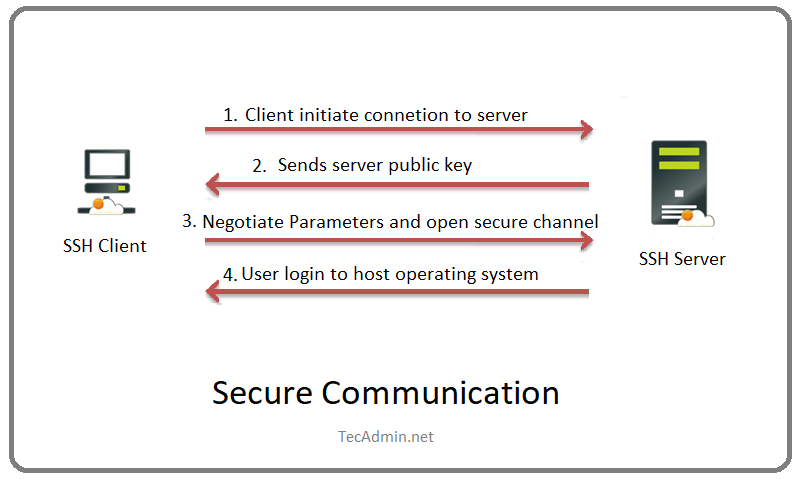
What is Secure Shell (SSH)? TecAdmin

什么叫SSH?原理详解,看这一篇就够了! CSDN博客
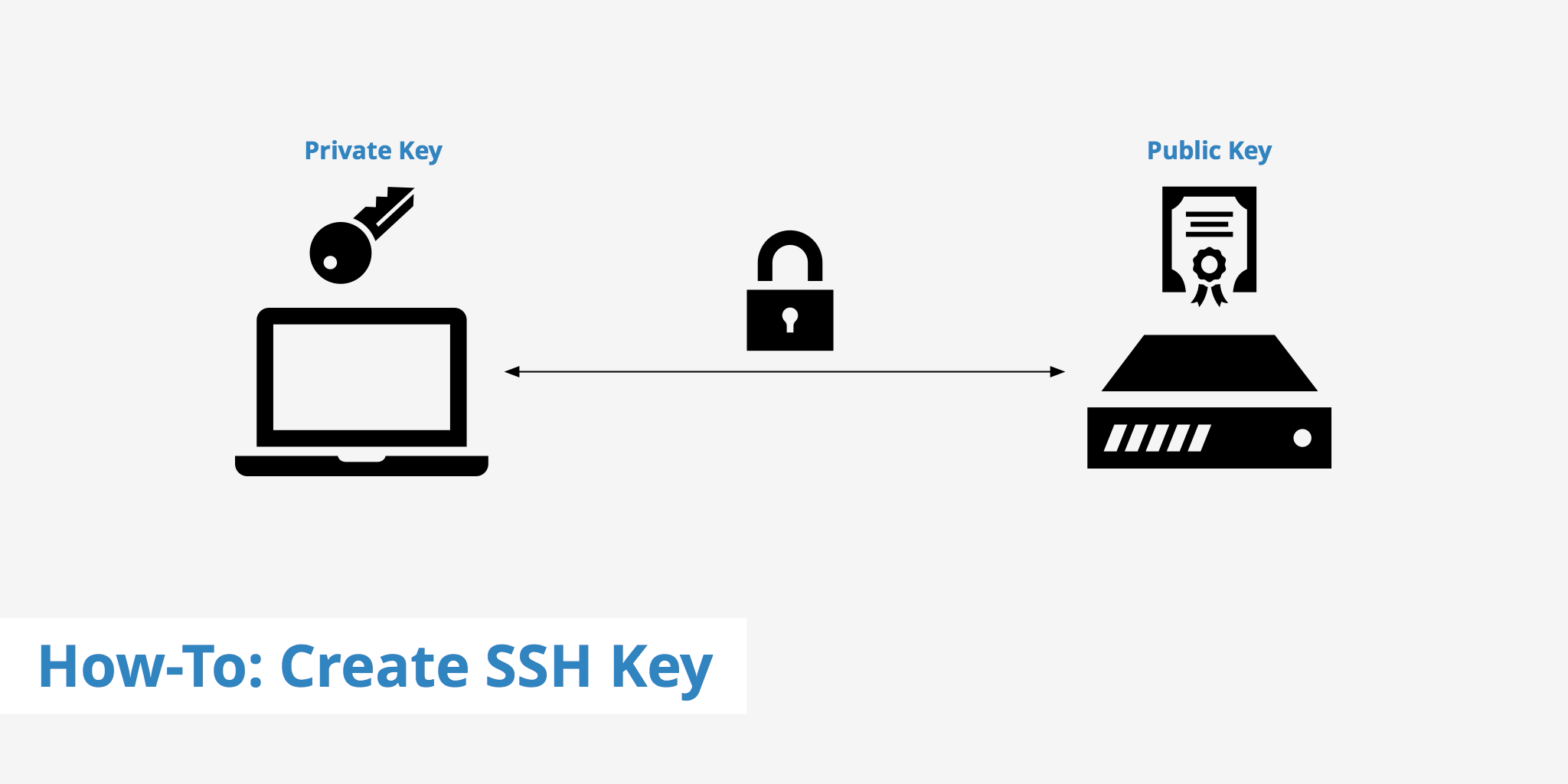
How to Create an SSH Key KeyCDN Support

Free SSH CloudFront Server Germany NeoSSH

A Visual Guide to SSH Tunnels : r/programming
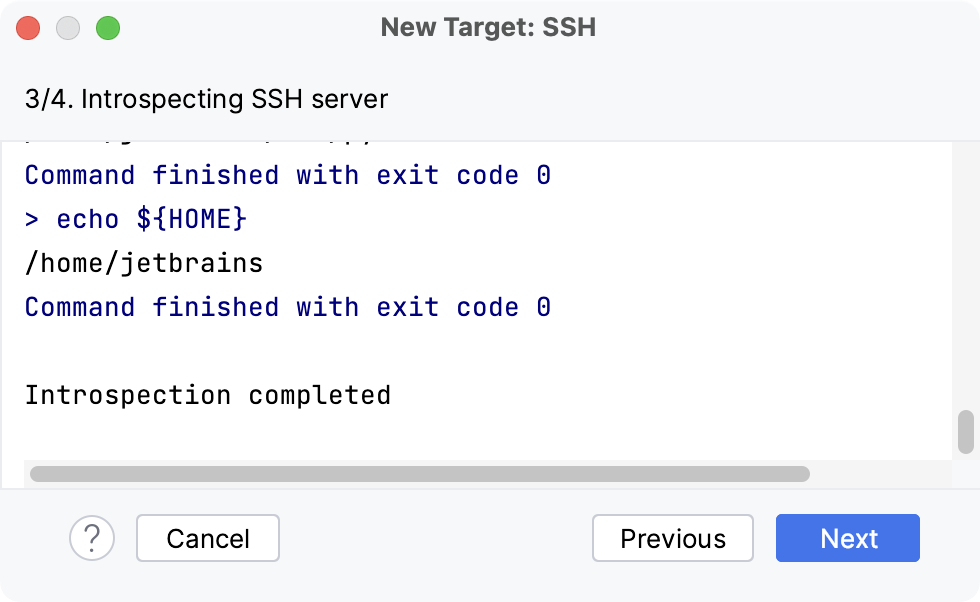
Configure an interpreter using SSH DataSpell Documentation

Windows Terminal and SSH the most beautiful SSH client? Nicola Suter

SSH Key là gì? Hướng dẫn sử dụng SSH Key hiệu quả BKHOST
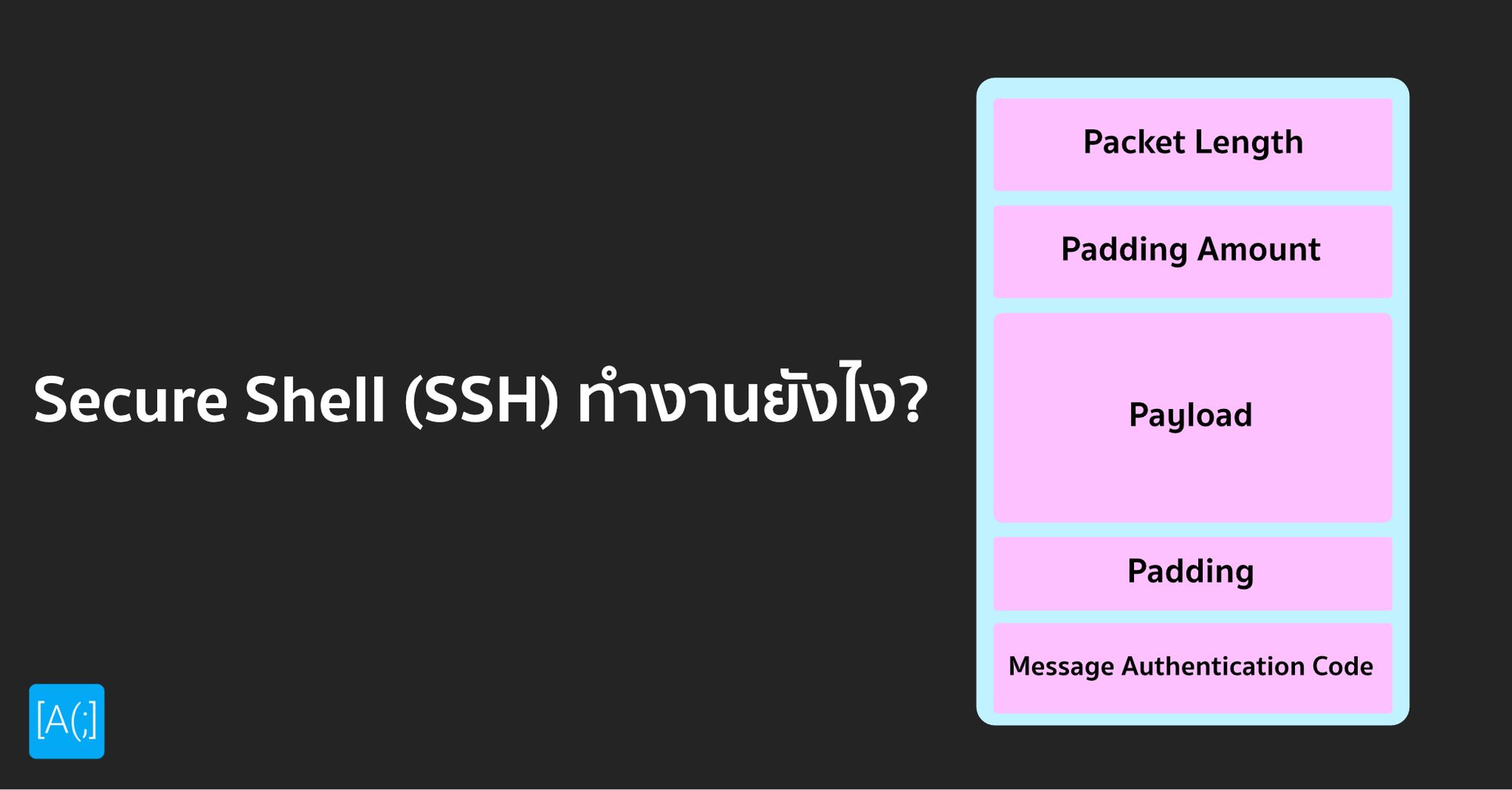
Secure Shell (SSH) ทำงานยังไง Arnondora

The SSH Commands Cheat Sheet You ll Regret Missing Out On

Linux SSH Server (sshd) Configuration and Security Options With

How to add php repositories to debian kali linux for php files? by

Was ist Caching und wie wird eine Website gecached? Gcore

statidentity Blog