Select The Eap Protocol That Uses Digital Certificates For Authentication
Here are some of the images for Select The Eap Protocol That Uses Digital Certificates For Authentication that we found in our website database.
Extensible Authentication Protocol (EAP) Explained Frontegg

Select the Eap Protocol That Uses Digital Certificates for
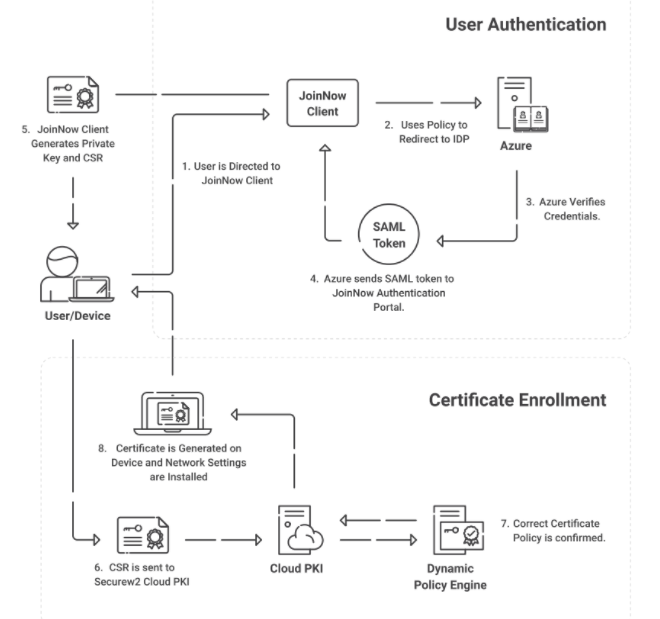
Select the Eap Protocol That Uses Digital Certificates for
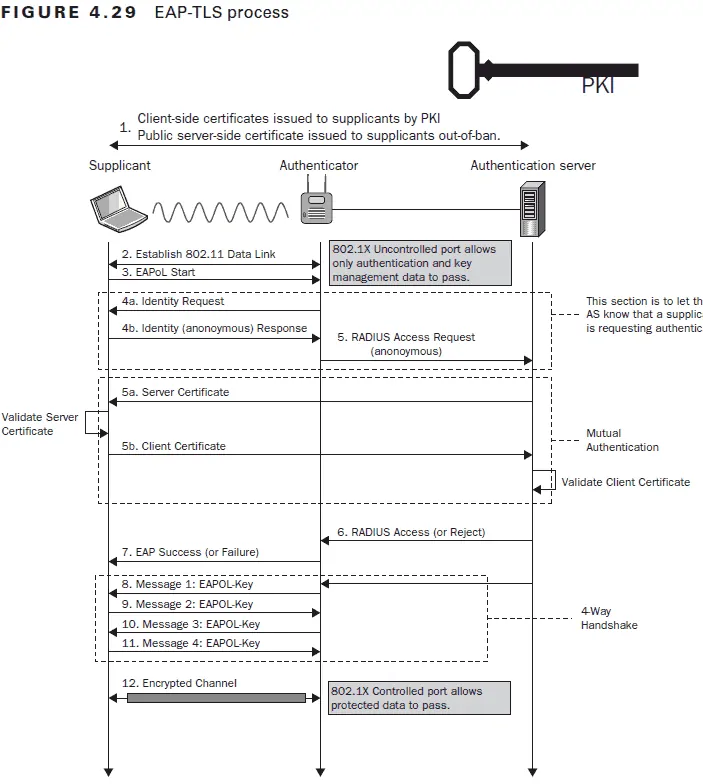
Select the Eap Protocol That Uses Digital Certificates for
.jpg)
What is Extensible Authentication Protocol (EAP)? EAP Types and Priorities

Decoding EAP Protocol: A Guide to Extensible Authentication NETWORK

EAP protocol stack Download Scientific Diagram

What is Extensible Authentication Protocol (EAP) and how does it work

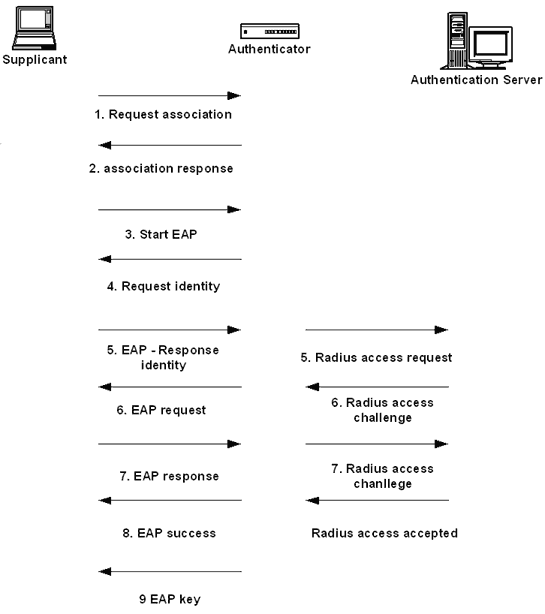
EAP based authentication procedure flow * EAP MD5: EAP MD5 is the base

From the Extensible Authentication Protocol (EAP) methods given below pdf
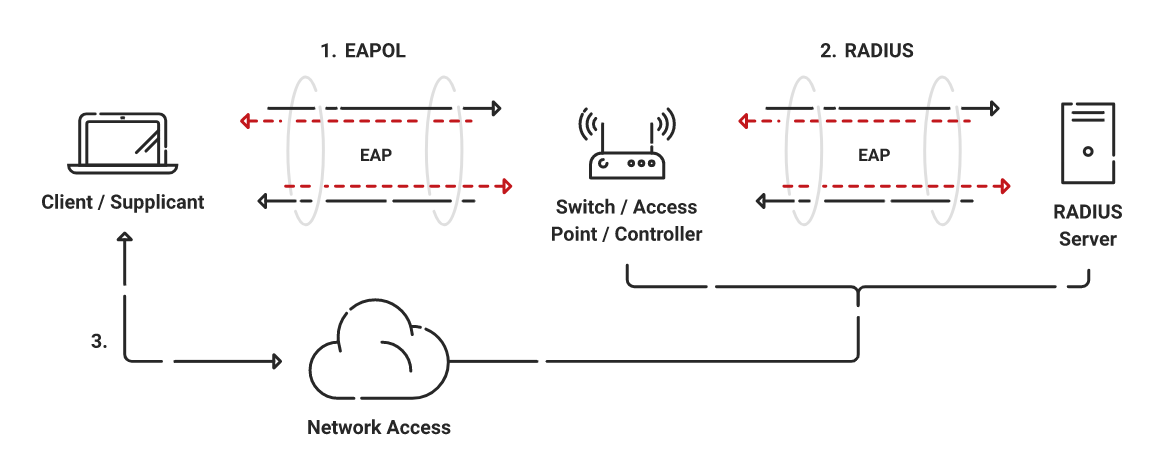
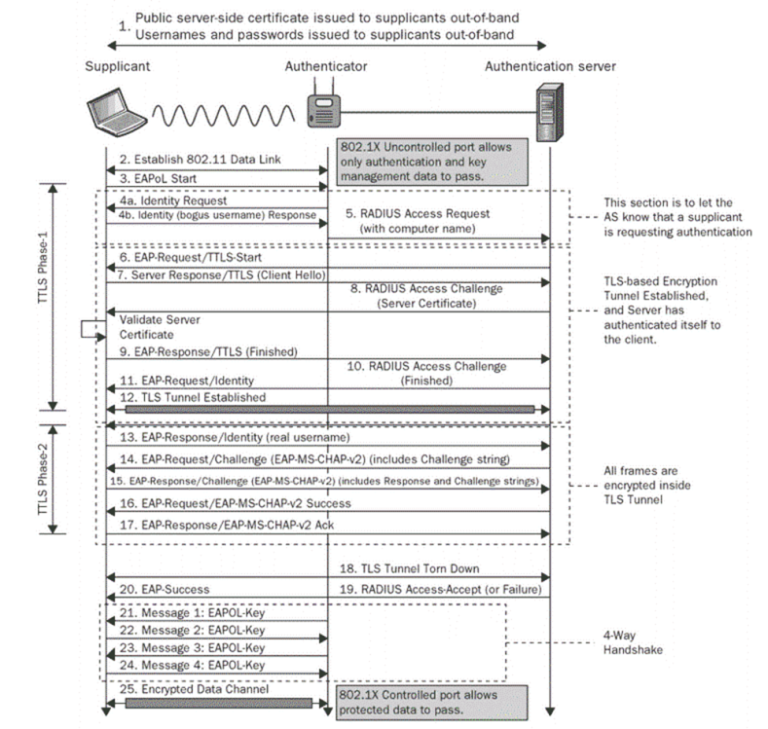
Configure EAP TLS Authentication Cloud RADIUS

Authentication Protocols (802 1X EAP/PEAP EAP FAST/TLS/TTLS and

Authentication Protocols (802 1X EAP/PEAP EAP FAST/TLS/TTLS and

Types of Authentication #authentication Dr Erdal Ozkaya
A Comprehensive Guide to the EAP Protocol in Networking
A Comprehensive Guide to the EAP Protocol in Networking
A Comprehensive Guide to the EAP Protocol in Networking

A Comprehensive Guide to the EAP Protocol in Networking
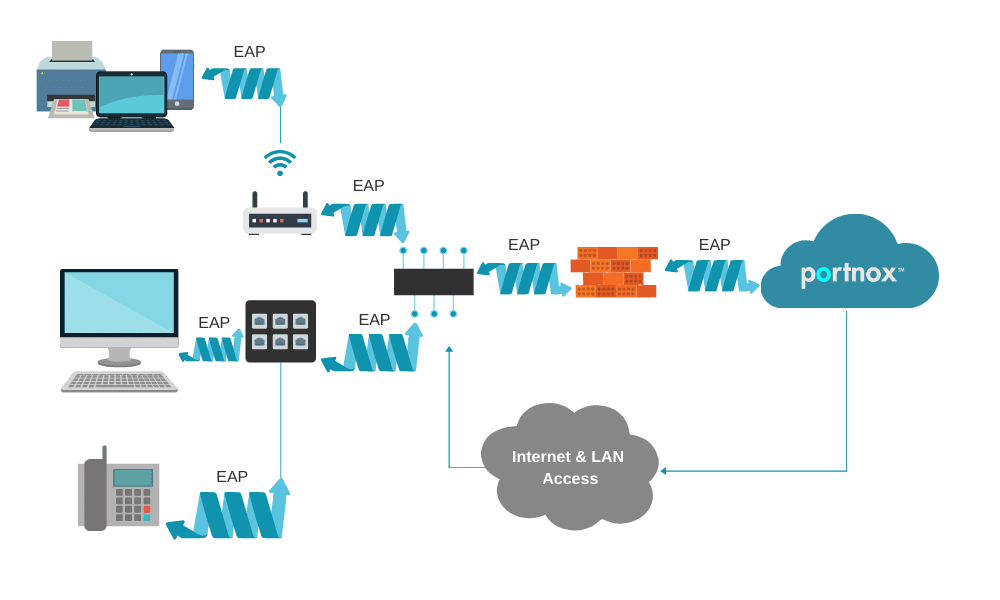
EAP TLS Authentication with Certificates Portnox

EAP TLS Authentication with Certificates Portnox
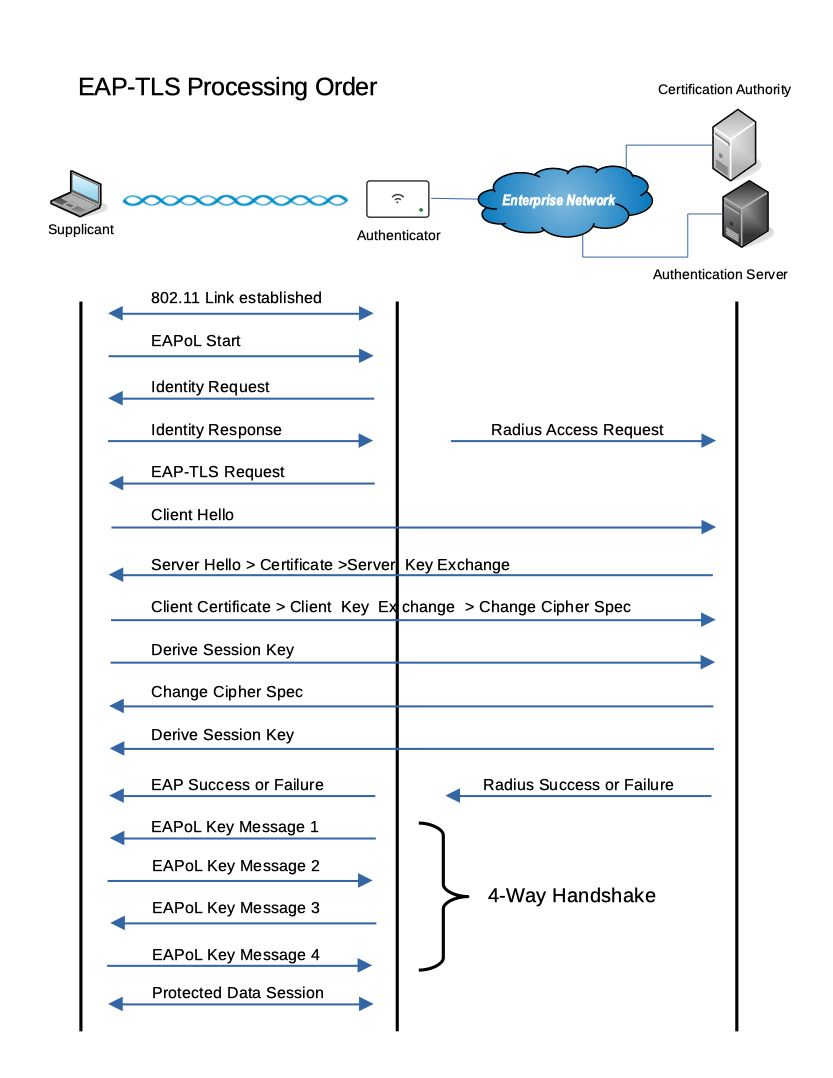
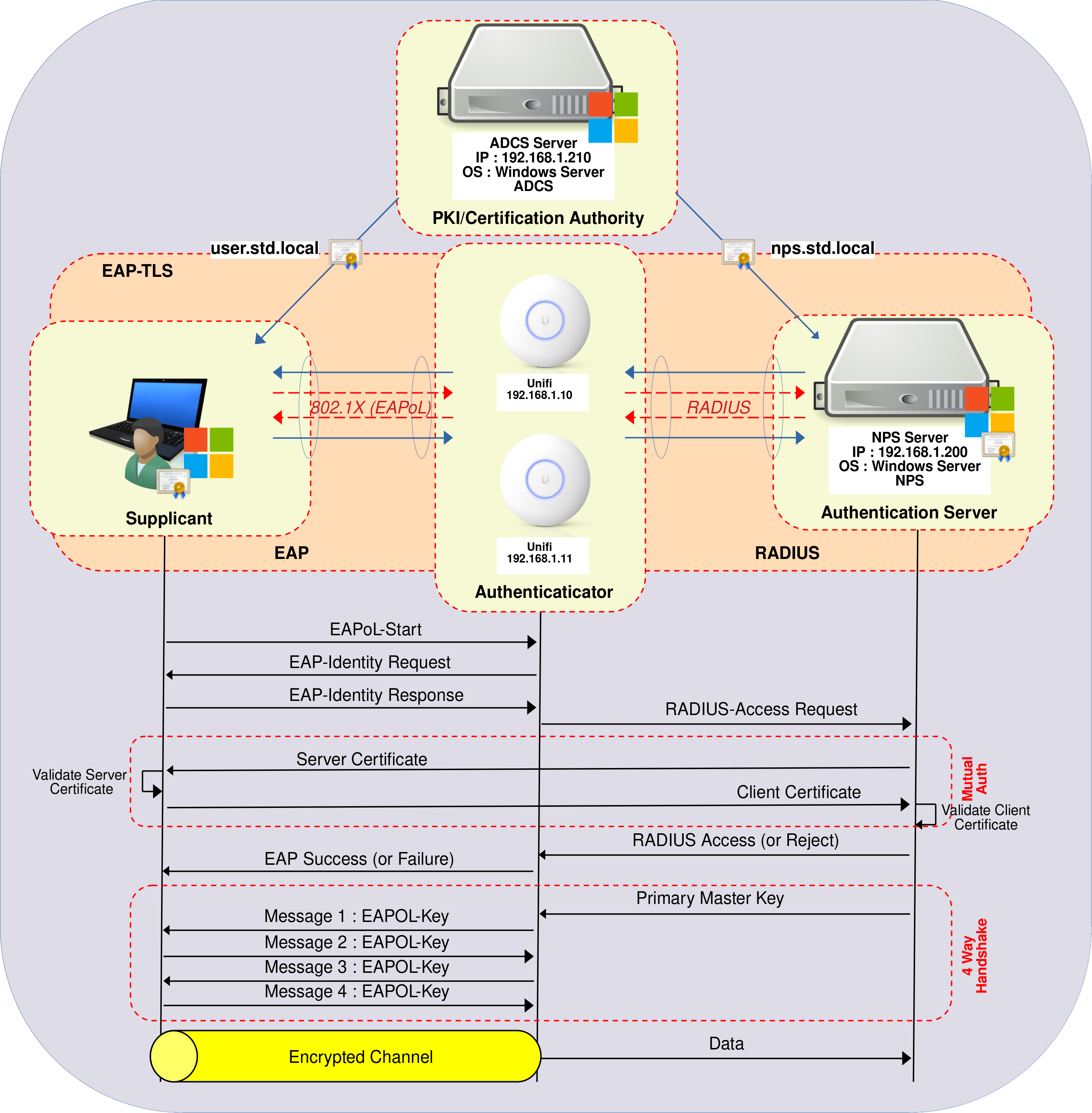
Darwin Castro Wireless Authentication using EAP TLS Protocol
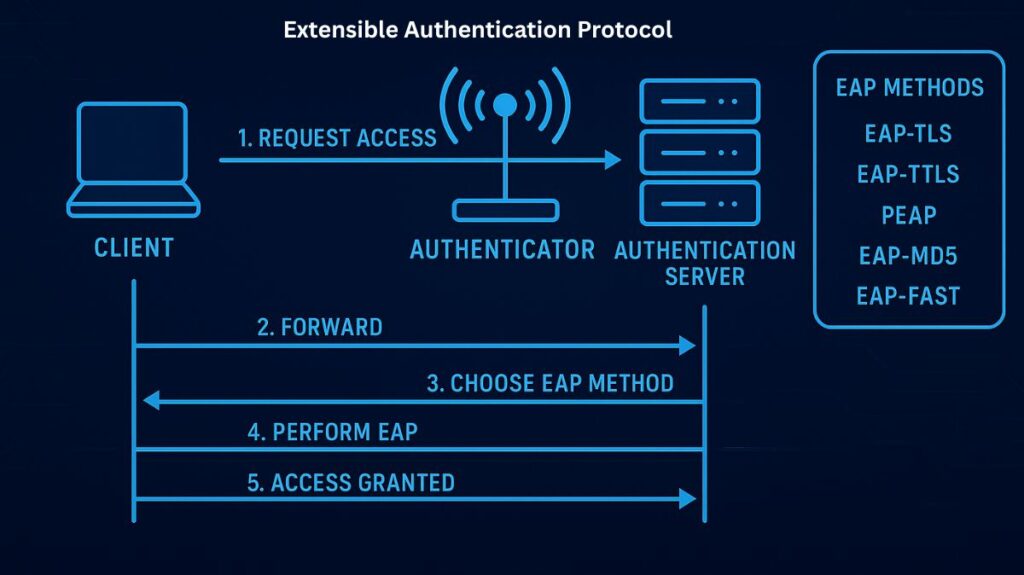
EAP and How Does Extensible Authentication Protocol Work?

How to do Wi Fi Certificate Based Authentication (CBA) Using EAP TLS
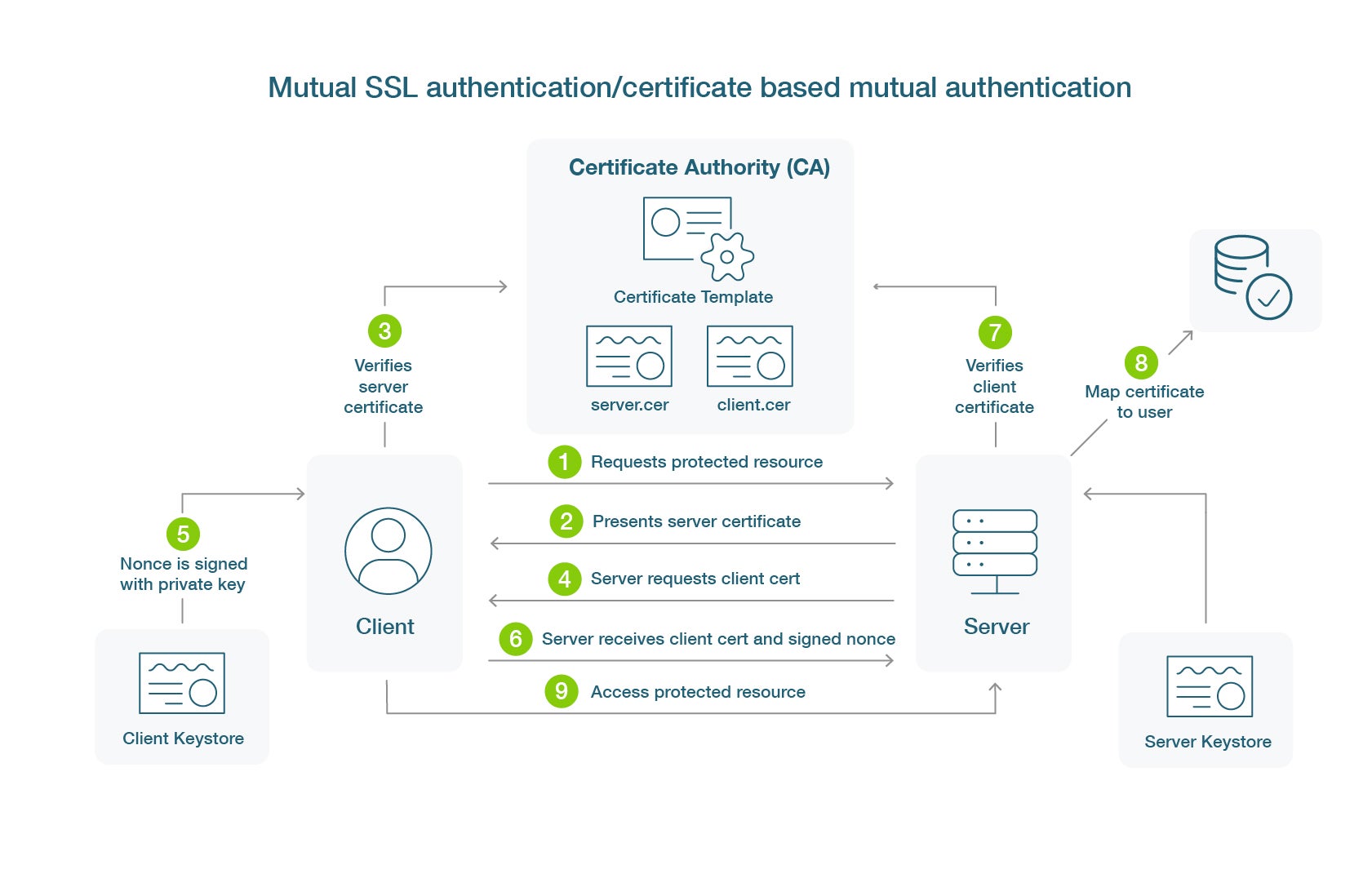
Certificates authentication

OVERVIEW OF PKM AUTHENTICATION MECHANISM IN WiMAX SECURITY PROTOCOL

IKEv2 with EAP AKA (second authentication step) Moreover an

Extensible Authentication Protocol (EAP): Definition Types Uses

How to Setup Wi Fi Authentication with X509 Certificates Keytos

Extensible Authentication Protocol (EAP): Definition Types Uses
Was ist das Extensible Authentication Protocol (EAP)? Dutch Bullion
Eap tls Flow Diagram Eap Peap Aruba Authentication Tls Clear
Ubiquiti Implementing WPA Enterprise EAP TLS
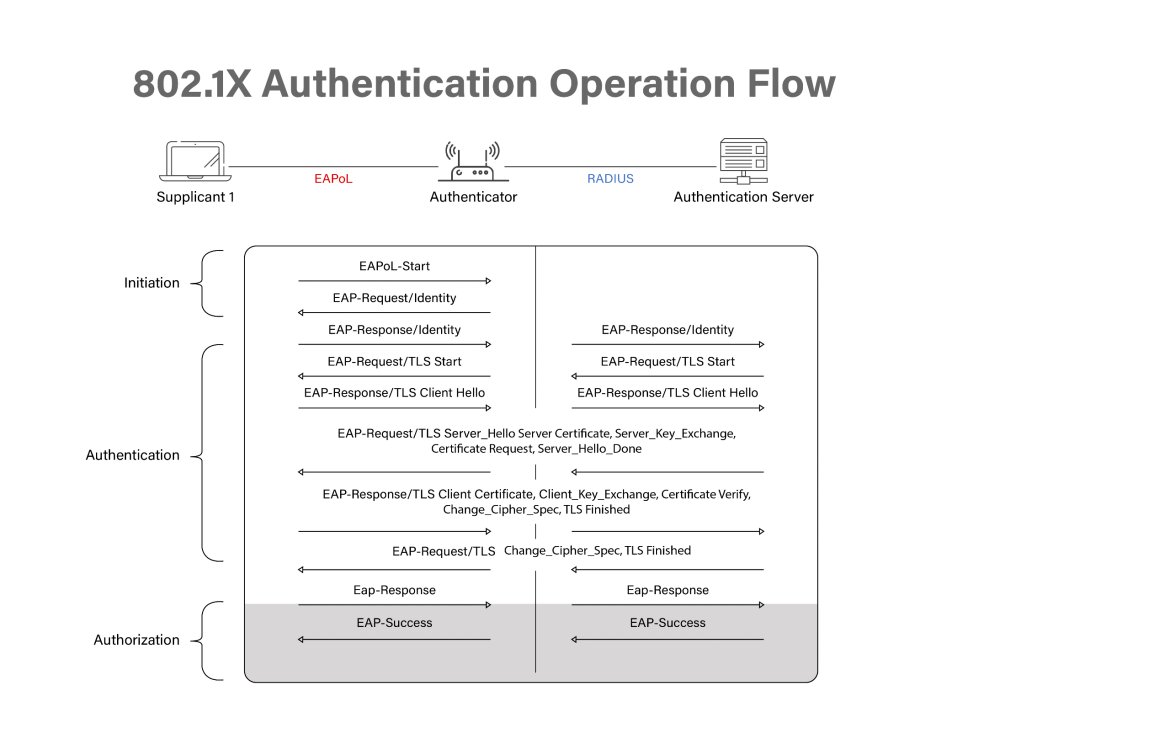
802 1X Protocol for Network Authentication Portnox
What is 802 1x security authentication? NETGEAR Support

Implementing 802 1x Authentication PPT

802 1X Network Authentication: In Depth Guide Cloud RADIUS
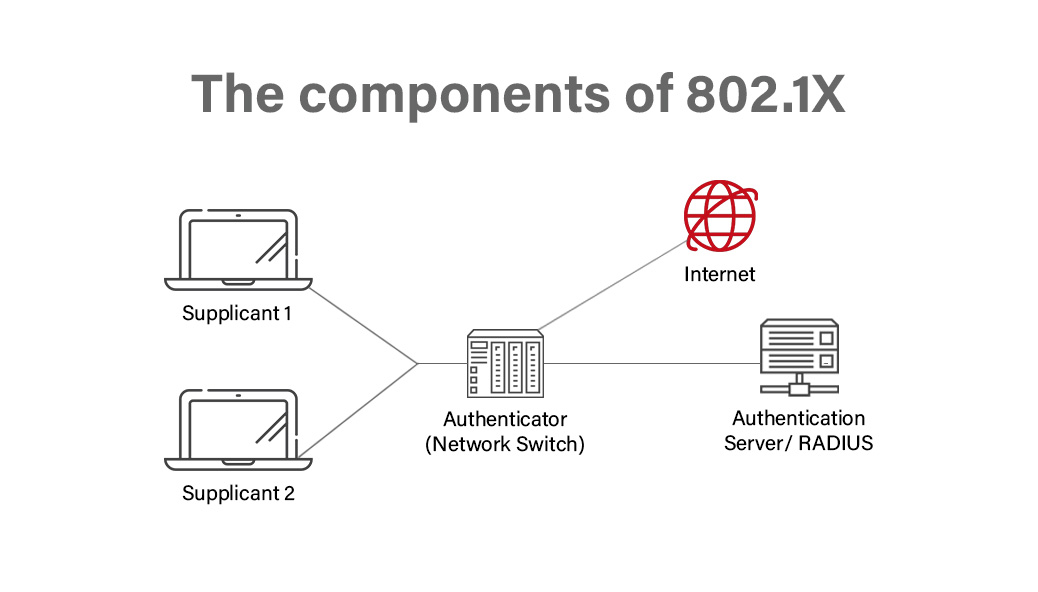
Freeradius Certificate Authentication prntbl concejomunicipaldechinu

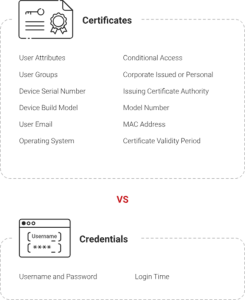
Passwords vs Certificates for 802 1X Mist
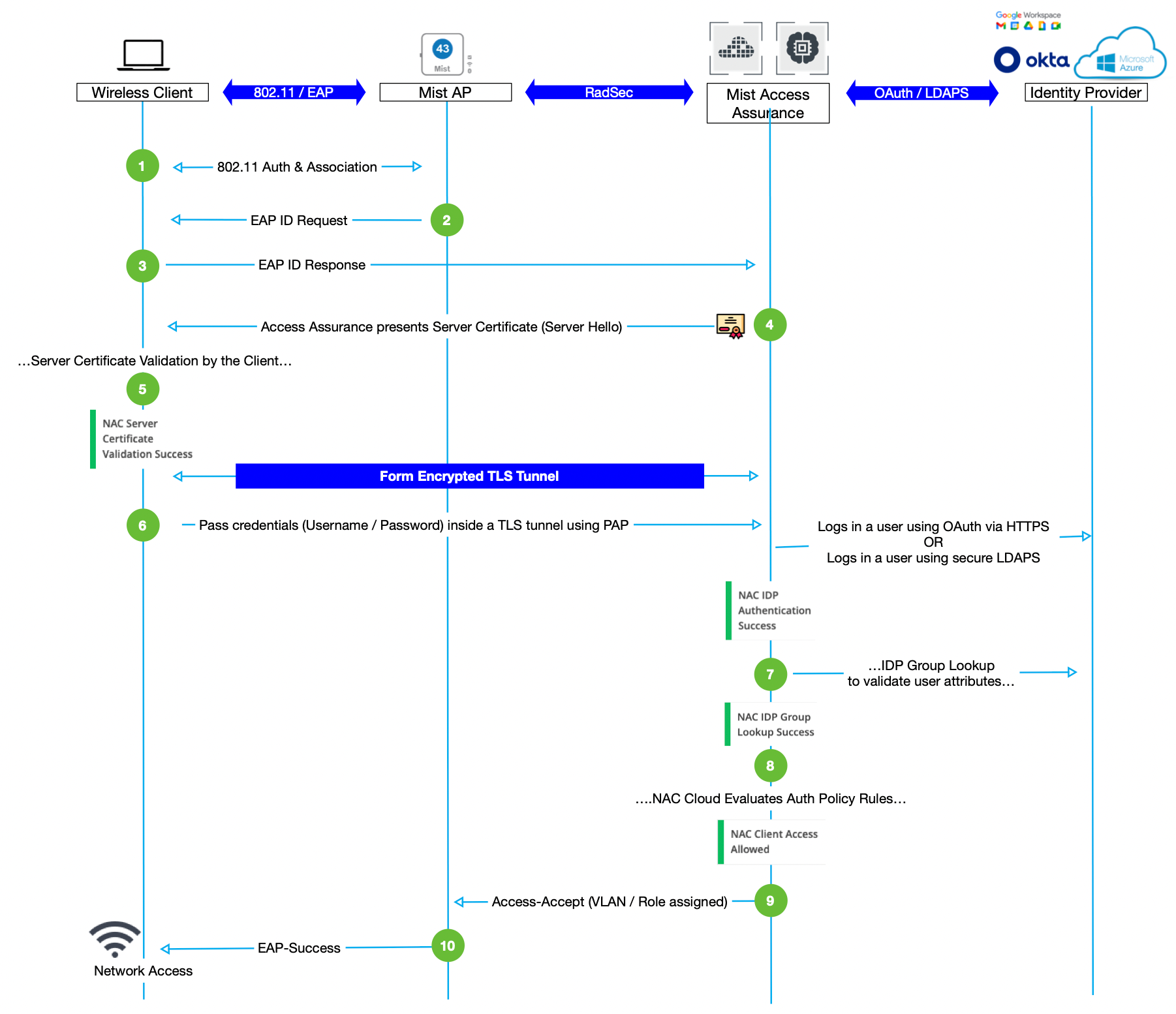
Passwords vs Certificates for 802 1X Mist

Eaptls Certificates For Wireless On Android

𝐂𝐇𝐀𝐏 𝐕𝐒 𝐏𝐀𝐏 𝐕𝐒 𝐄𝐀𝐏 EAP is the most secure authentication method
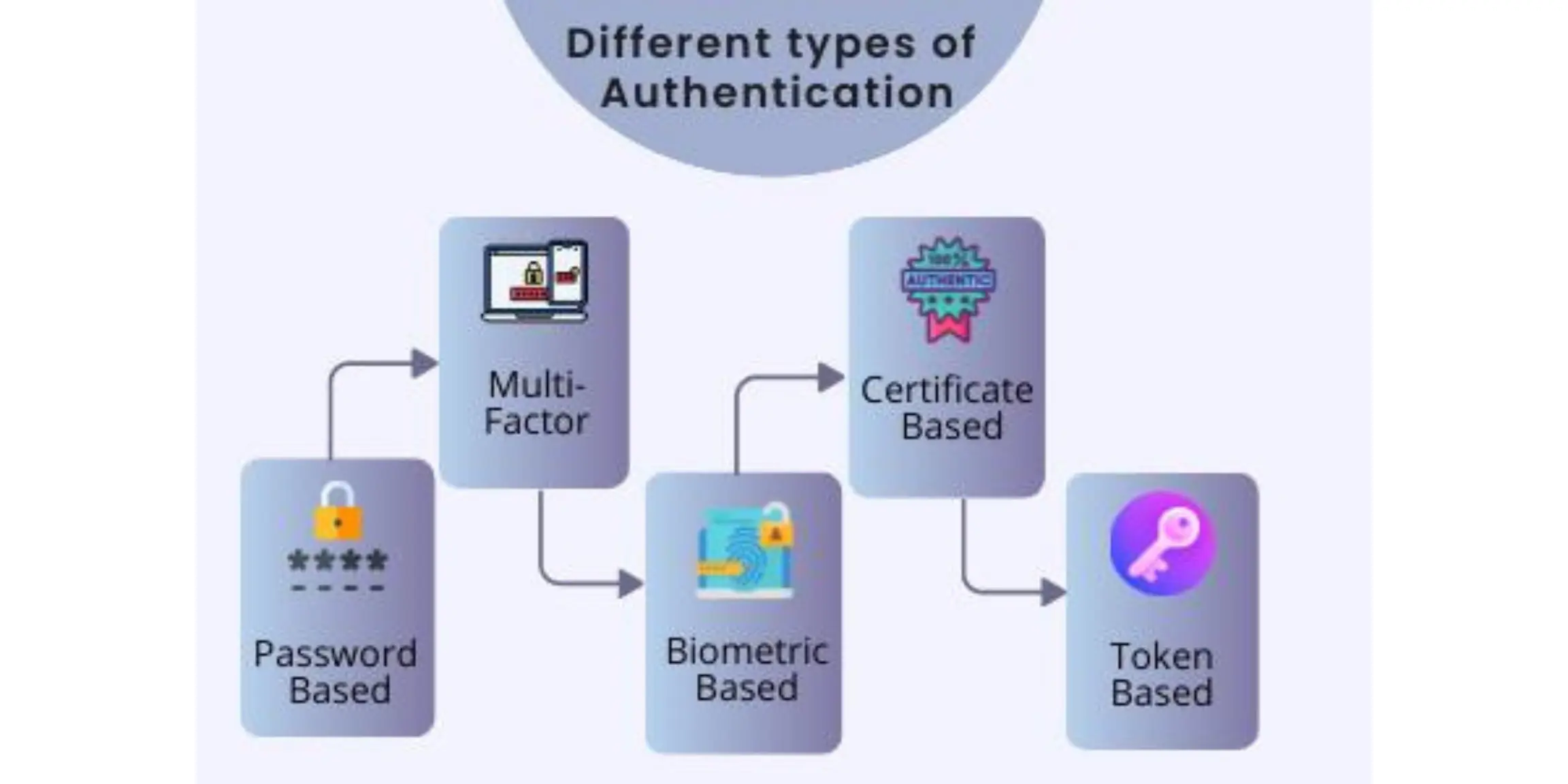
Quelle est la différence entre l authentification et l autorisation

Upload 802 1x certificates to Grandstream Video Phone GXV se

EAP Extensible Authentication Protocol YouTube

Module 6 Flashcards Quizlet
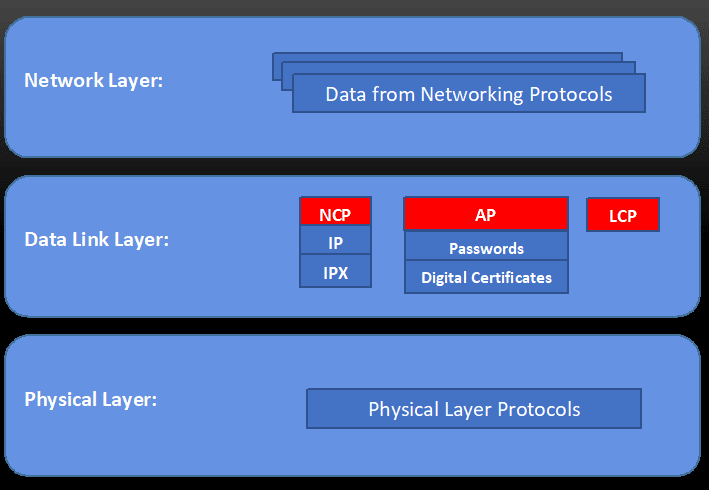
Point to Point Protocol (PPP) Baeldung on Computer Science

Security Acronyms 701 Flashcards Quizlet

Module 6 Flashcards Quizlet

Networking updates: CHECO ppt download

Wi fi security PPTX
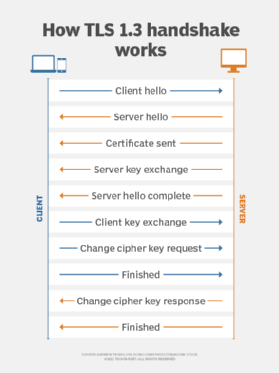
What is Transport Layer Security (TLS)?

Chapter 8 roadmap 8 1 What is network security? ppt download
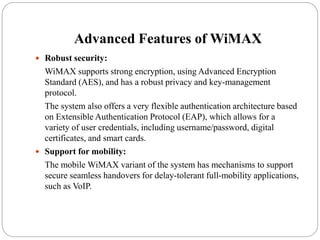
WiMAX ppt

Kela v2cs final PDF Internet Computing
+was+developed+by+Microsoft.+Requires+certificates+for+clients+and+servers..jpg)
ITEC 275 Computer Networks Switching Routing and WANs ppt download
.jpg)
ITEC 275 Computer Networks Switching Routing and WANs ppt download
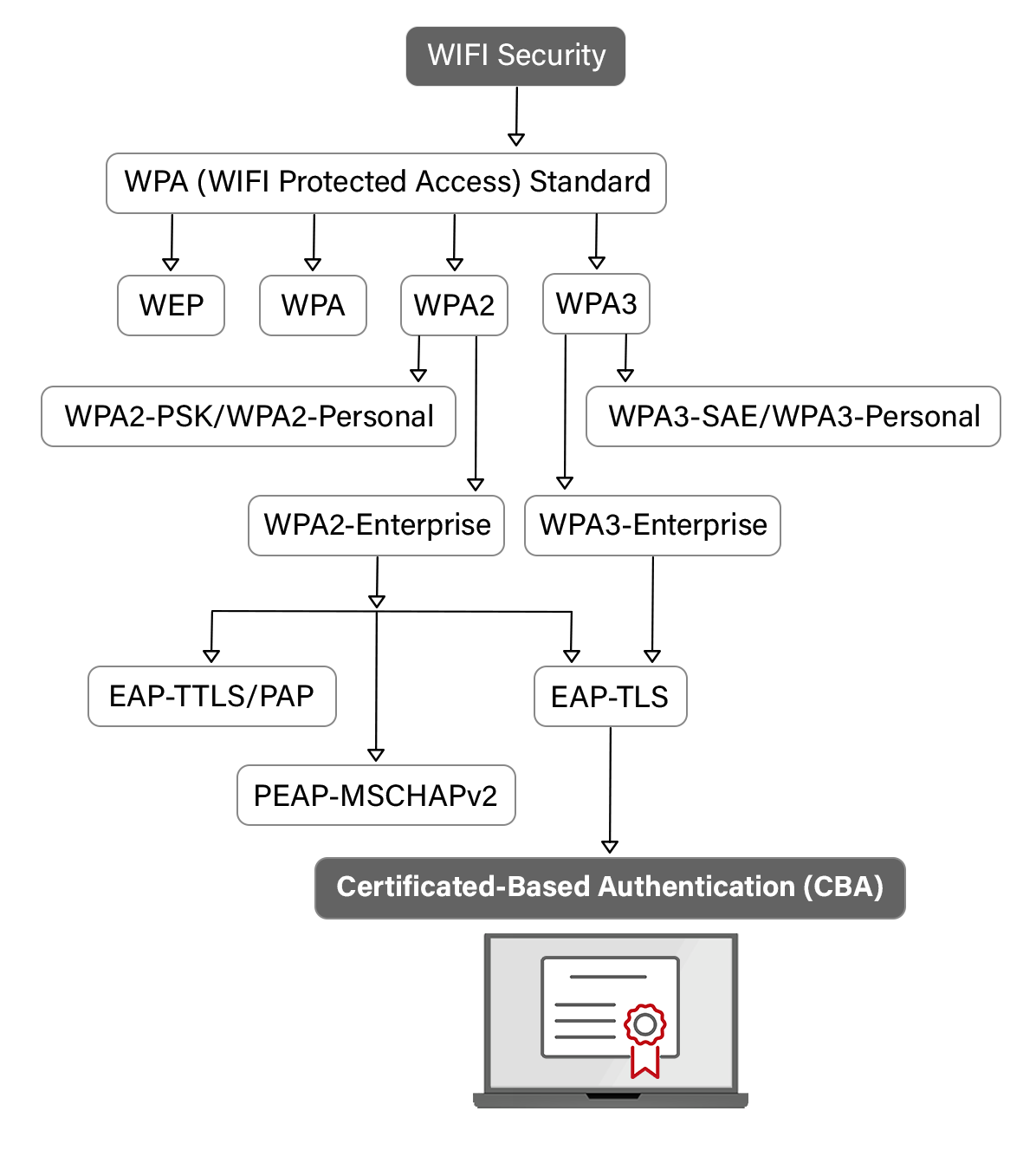
What is the Difference Between WPA2 and 802 1X?

WAPI Position Paper Sept 2005 Sept 2005 IEEE WG ppt download

Attacking and Securing WPA Enterprise Networks PDF Information and