Security Strategy Template
Here are some of the images for Security Strategy Template that we found in our website database.

Cyber Security Strategy Template Content Calendar Template
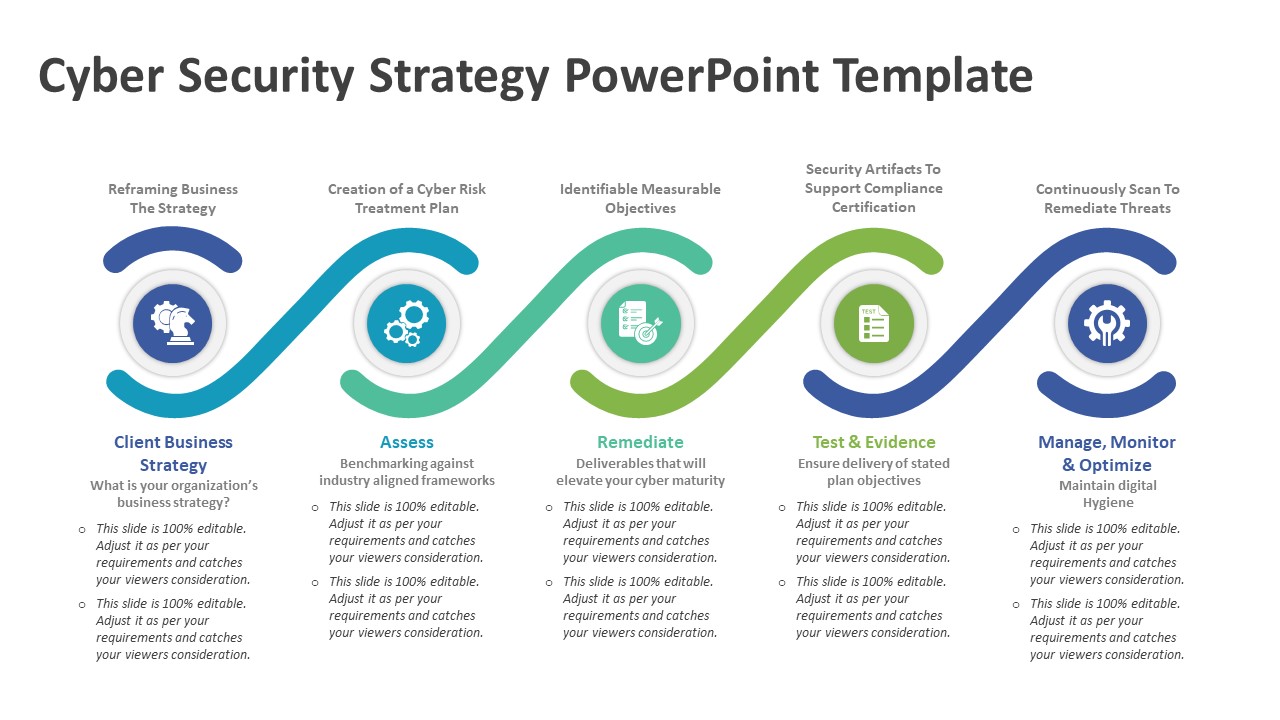
Cyber Security Strategy PowerPoint Template
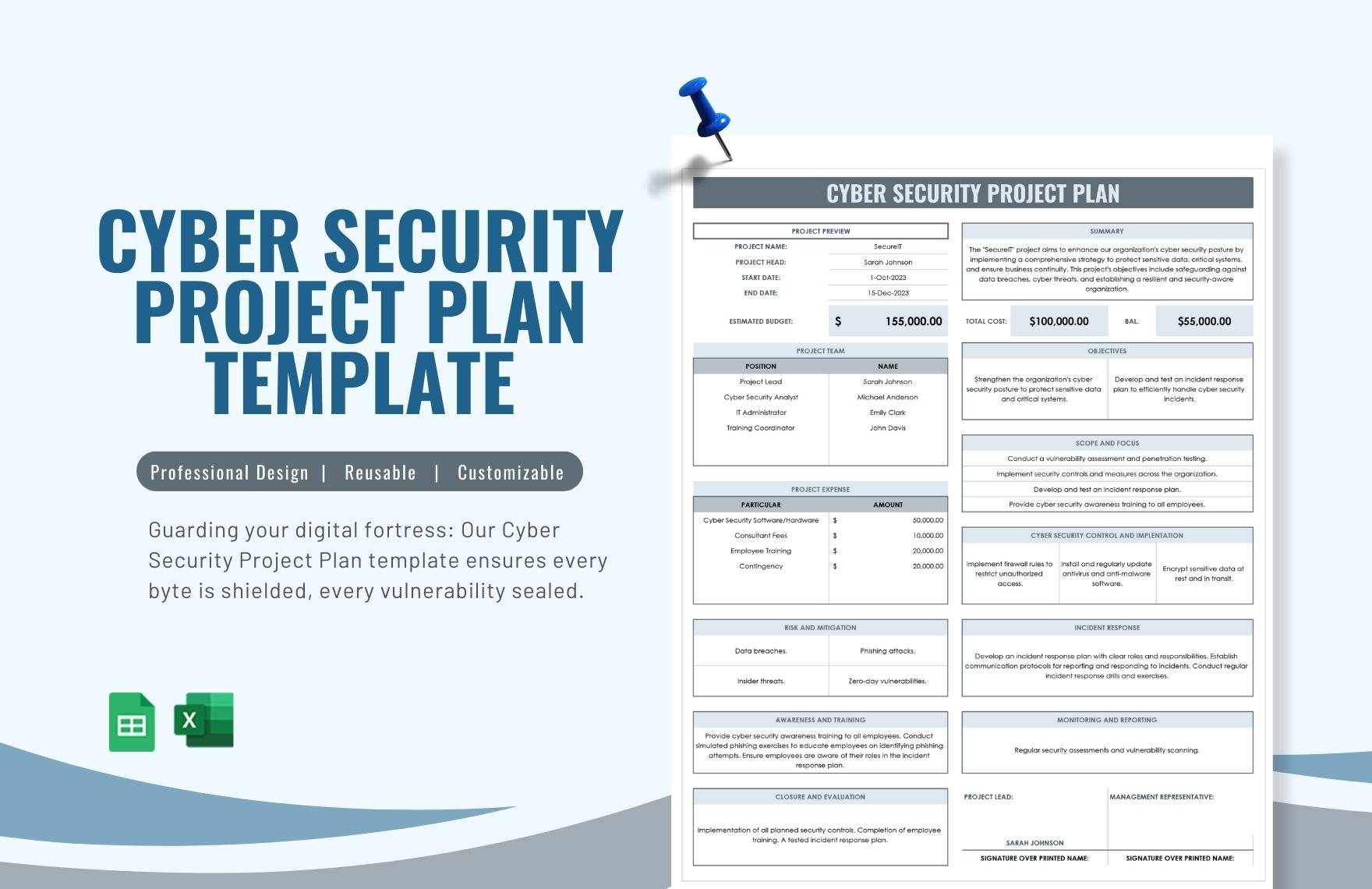
Free Cyber Security Templates to Edit Online
Information Security Strategy Template
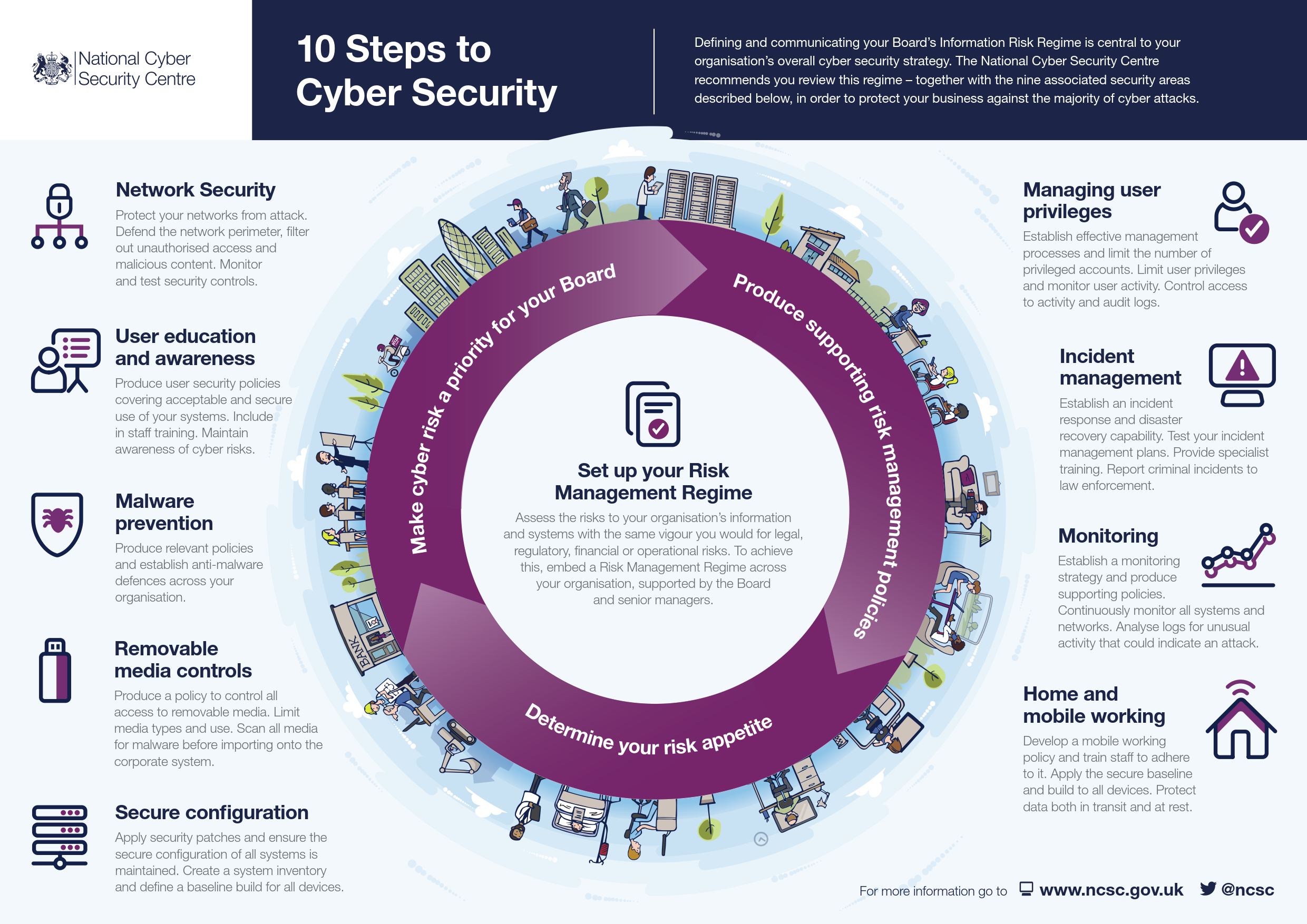
Cybersecurity Strategy Template

Cybersecurity Strategy Template
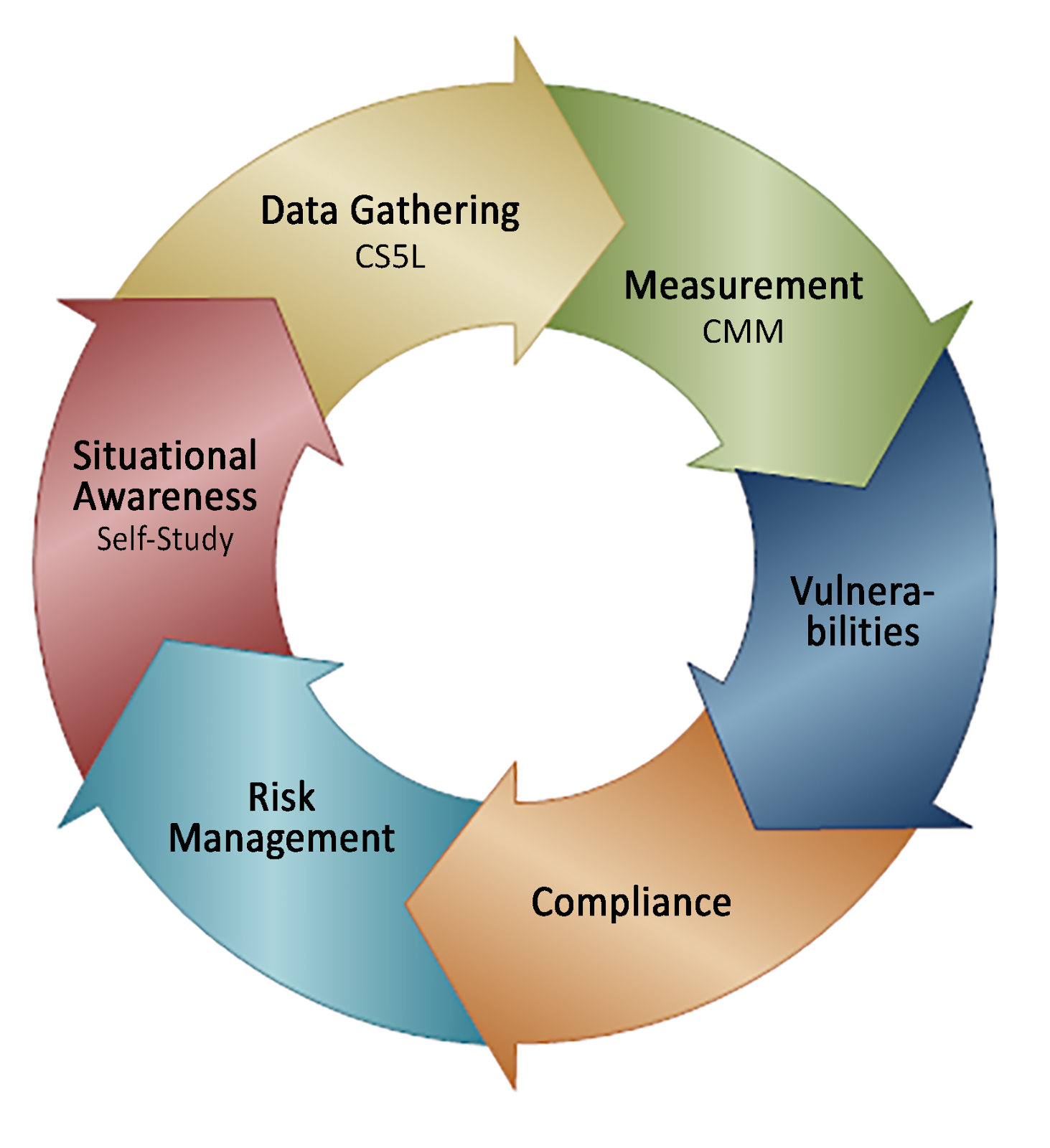
Cybersecurity Strategy Template

Information Security Strategy Template Printable Word Searches

Cybersecurity Strategy Template

Cybersecurity Strategy Template
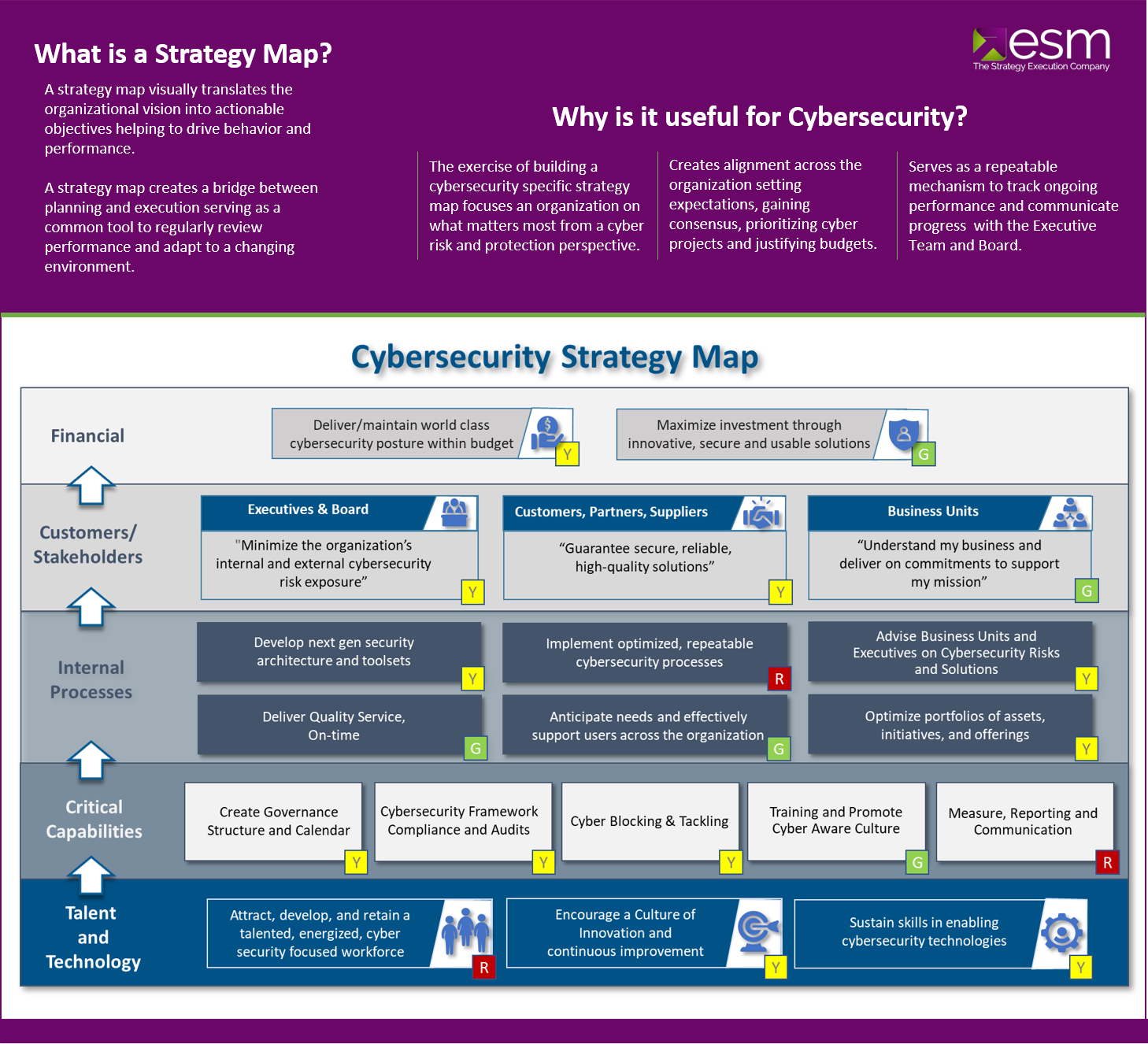
Cybersecurity Strategy Template

Cybersecurity Strategy Template

Free School Safety and Security Strategy Template to Edit Online

Cyber Security Strategy Template
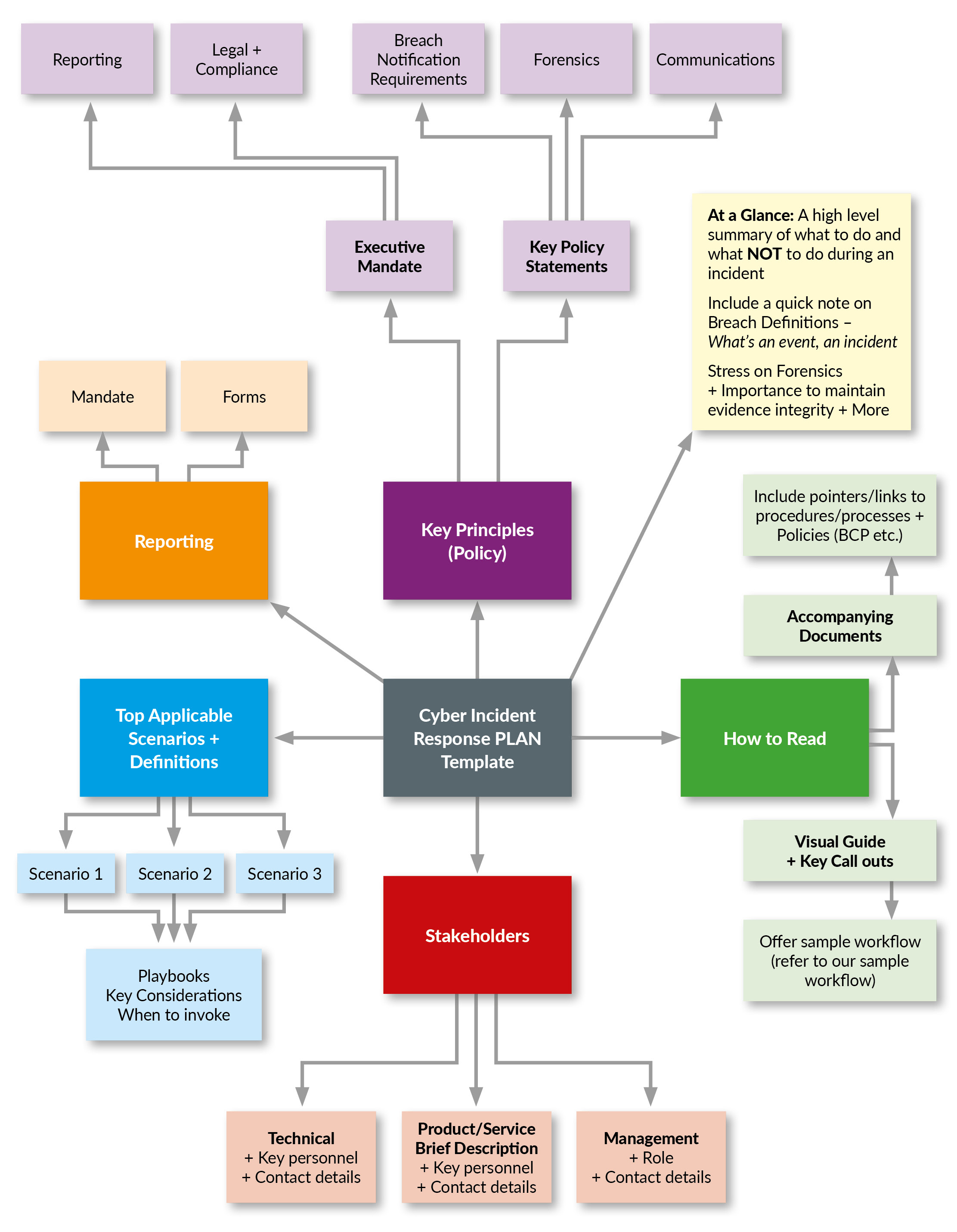
Cybersecurity Strategy Template

Information Security Strategy Template

Information Security Strategy Template
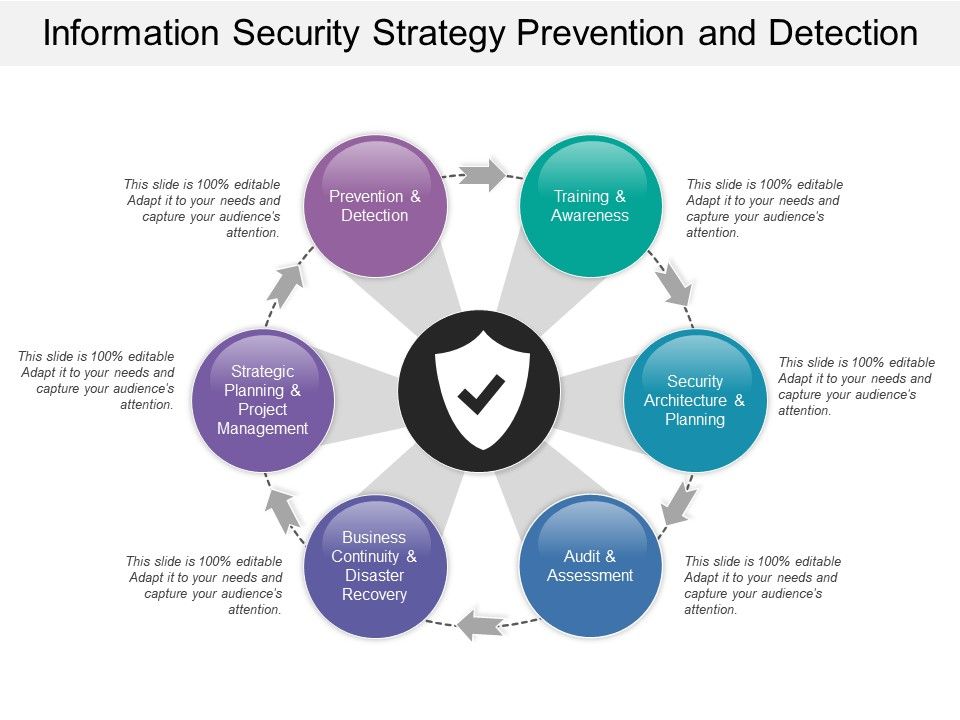
Information Security Strategy Template

Nist Cyber Security Strategy Template

Information Security Strategy Template
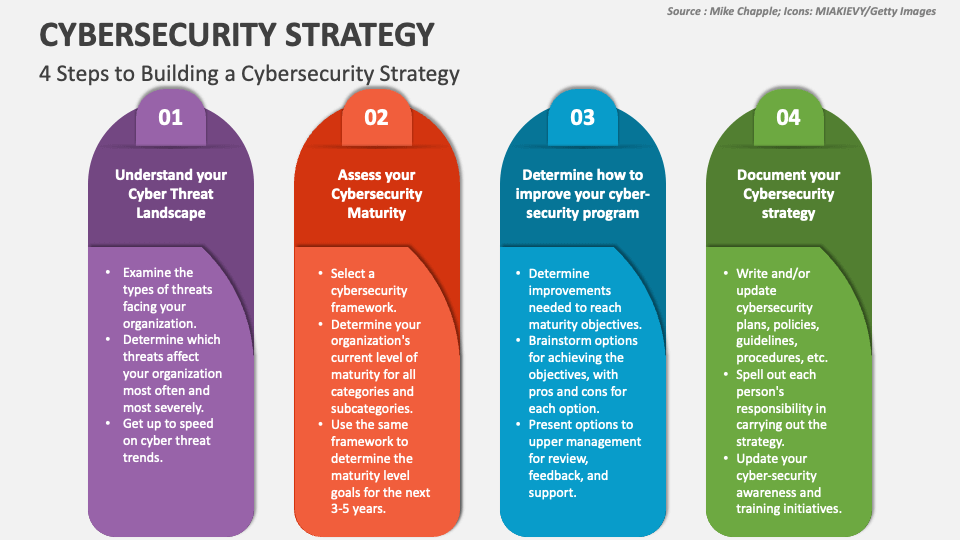
Cybersecurity Strategy Template prntbl concejomunicipaldechinu gov co
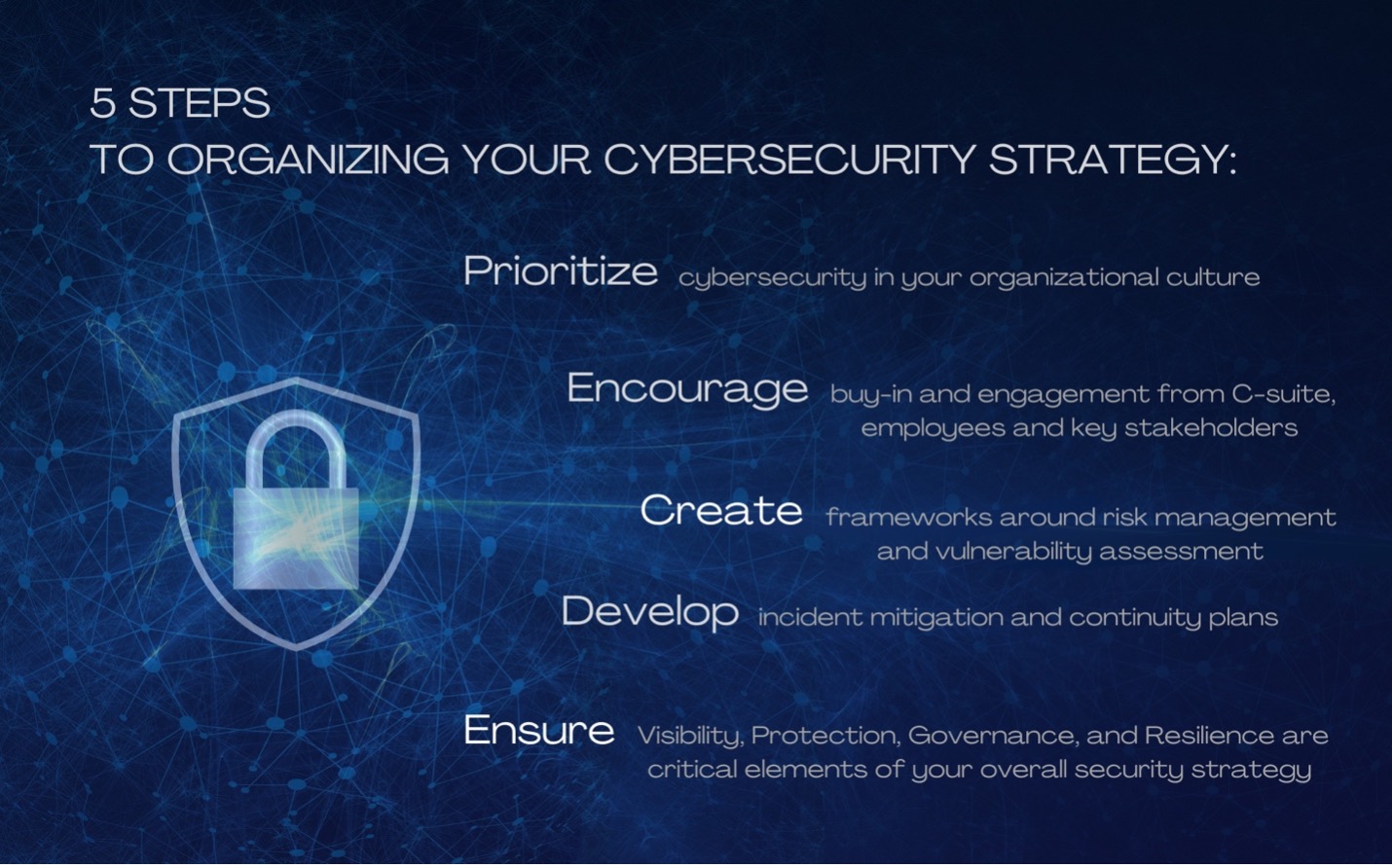
Cybersecurity Strategy Template prntbl concejomunicipaldechinu gov co
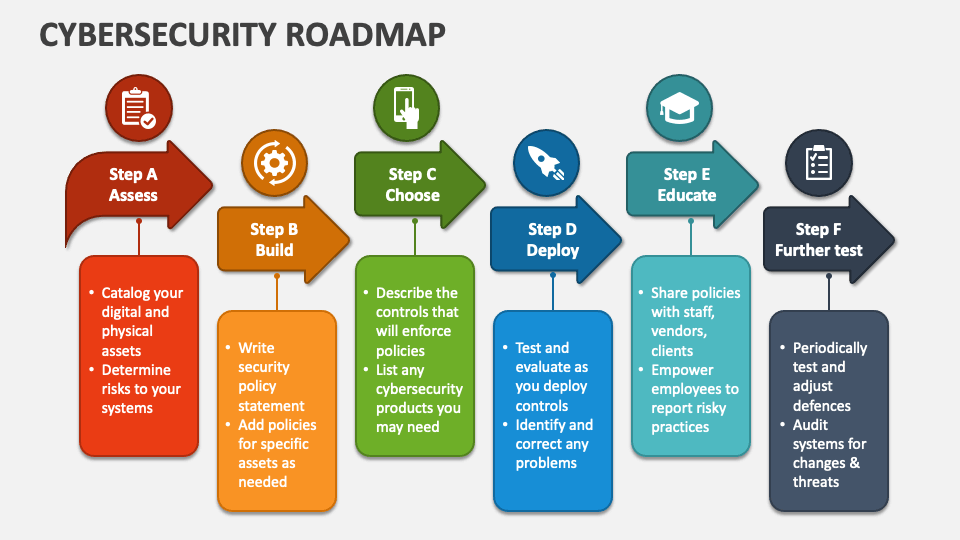
Cybersecurity Strategy Template prntbl concejomunicipaldechinu gov co
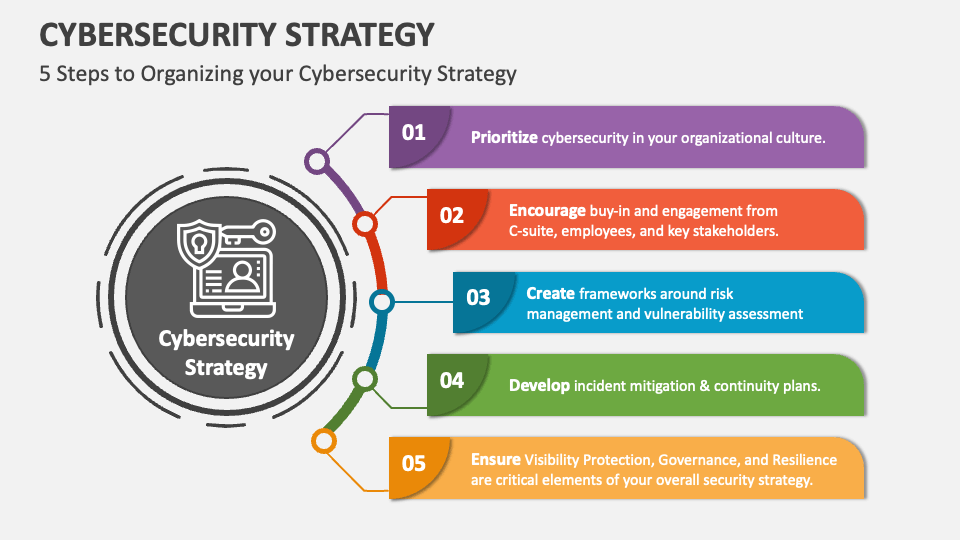
Cybersecurity Strategy Template prntbl concejomunicipaldechinu gov co

Free Security Plan Template to Edit Online
Cyber Security Policy Template

Information Security Strategy Template Ppt PowerPoint Presentation Outline

Cyber Security Strategy Template

Information Security Strategy Template Ppt PowerPoint Presentation

Strategy House Template for PowerPoint Google Slides
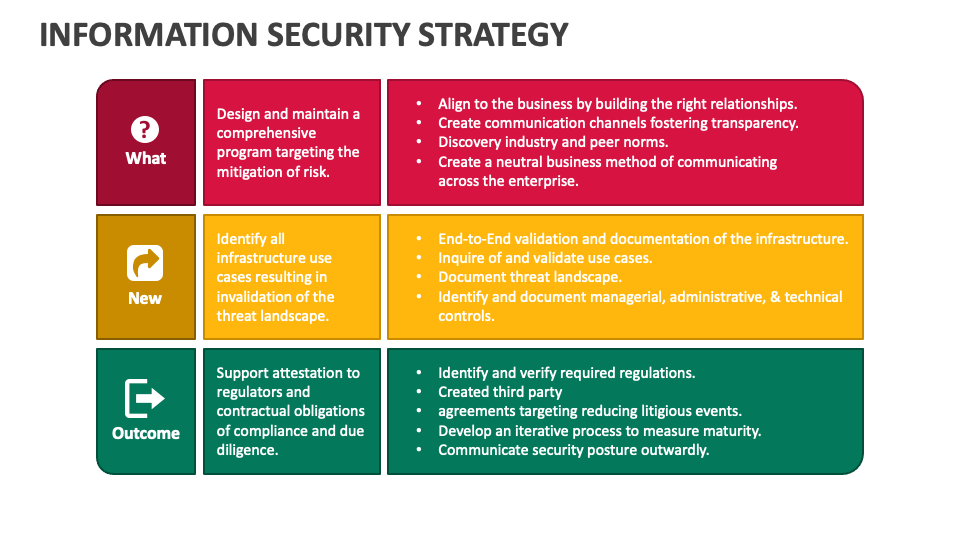
Information Security Strategy PowerPoint Presentation Slides PPT Template
Information Security Strategy PowerPoint Presentation Slides PPT Template

Cloud Security Strategy: Building a Robust Policy

How to Craft an Effective Cyber Security Strategy?

Resume Template For Cyber Security

Nist Cybersecurity Plan Template prntbl concejomunicipaldechinu gov co

Strategic Plan Timeline To Develop Effective Cyber Security Strategy

Top 10 Cybersecurity Strategy Templates with Examples and Samples

Cmmc Policy Templates

2023 DOD Cyber Strategy Industrial Cyber

Construction Security Plan Sample Construction Company Business Plan

Top 10 Cloud Strategy Templates With Samples And Examples Cloud
Roadmap Infographic Template

New 2023 DOD Cyber Strategy outlines approach to cyberspace enhances

TryHackMe on LinkedIn: NEW ROOM: Explore auditing logging and