Security Policies And Procedures Template
Here are some of the images for Security Policies And Procedures Template that we found in our website database.

HIPAA Security Policies and Procedures Template

IT Security Policies and Procedures Template

Cyber Security Policies and Procedures Template

General University Policies Procedures Template in Word Google Docs

Information Security Policies And Procedures Template Template 1

Information Security Policies And Procedures Template Template 1

Information Security Policies And Procedures Template Template 1

Security Policies And Procedures Template

Free Company Policies and Procedures Template Of Hr Policy Procedure

Free Company Policies and Procedures Template Of 10 It Security Policy
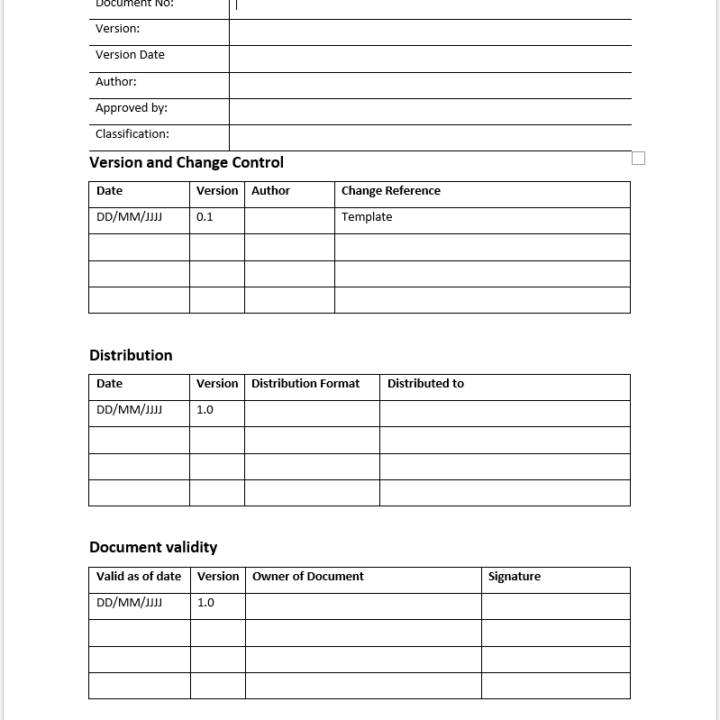
Security Operating Procedures Template Control 5 37 Ready

Human Resources Policies and Procedures Template

Policies And Procedures Template For Small Business Professional

Editable Security Policy Templates in Word to Download
Editable Security Policy Templates in Word to Download

Free Legal Corporate Compliance Policies Procedures Portfolio

Security Operating Procedures Template

Hipaa Privacy Policies And Procedures Template Template 1 : Resume

Hipaa Privacy Policies And Procedures Template Template 1 : Resume

Hipaa Privacy Policies And Procedures Template Template 1 : Resume

Policies And Procedures Template For Nonprofits

Nonprofit Policies And Procedures Manual Template
_LRG.jpg)
Business Policies And Procedures Template prntbl

Medical Office Policies And Procedures Manual Template Printable Word

Financial Policies And Procedures Template For Nonprofits

Cyber Security Policy Template

42 Information Security Policy Templates Cyber Security ᐅ TemplateLab
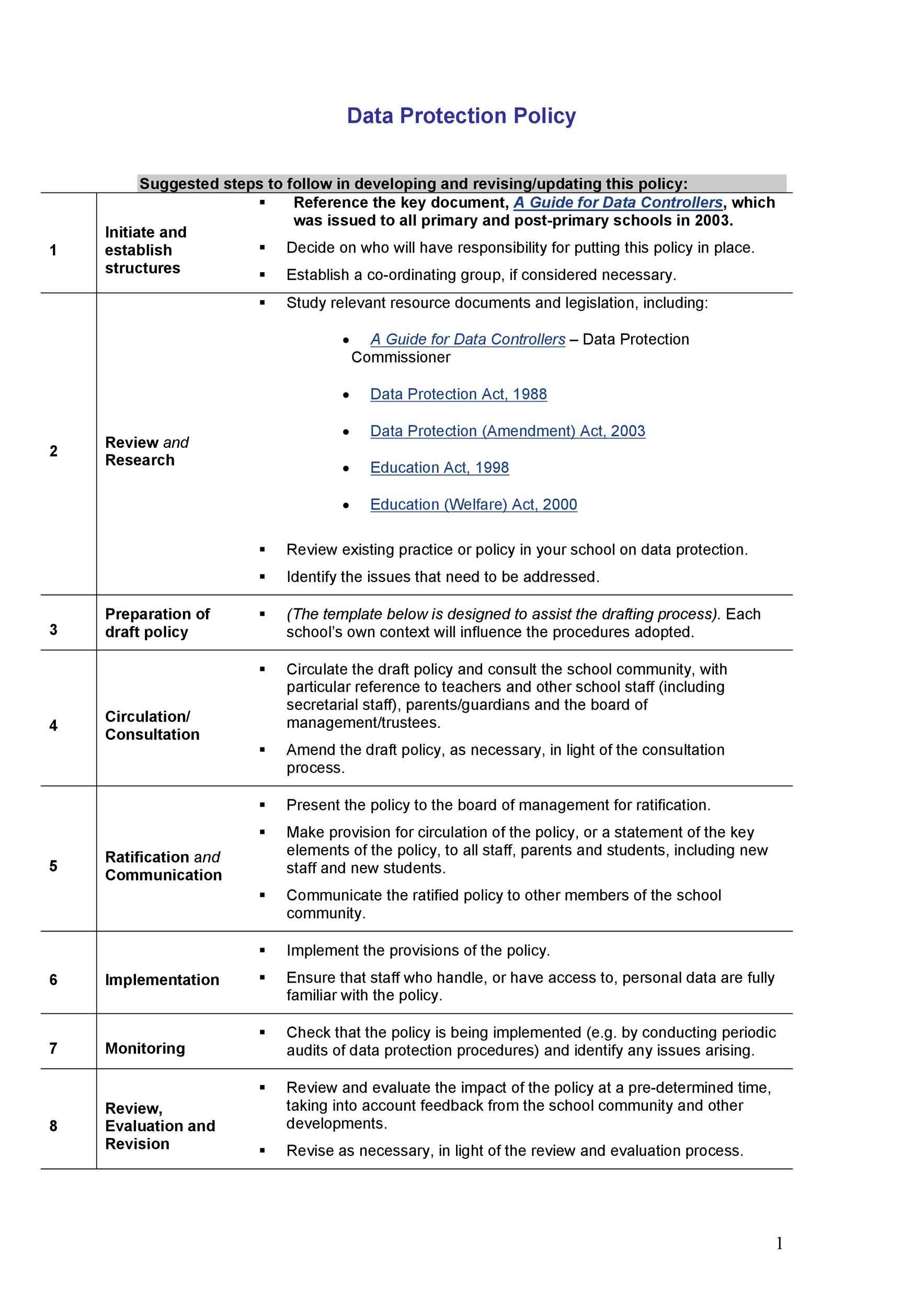
42 Information Security Policy Templates Cyber Security ᐅ TemplateLab

42 Information Security Policy Templates Cyber Security ᐅ TemplateLab

Maintenance policy and procedures template in Word and Pdf formats

29 Free Policies and Procedures Templates

Editable Procedure Manual Templates in Word to Download

Editable Procedure Manual Templates in Word to Download
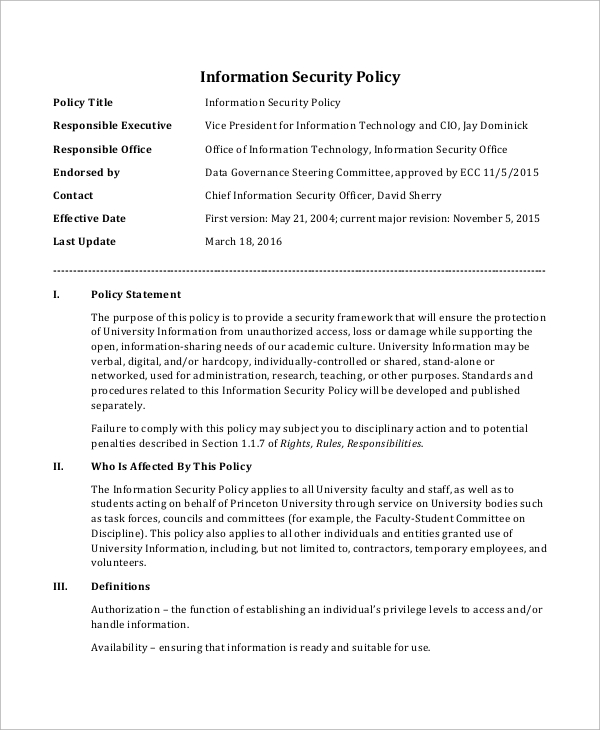
Information Security Program Template
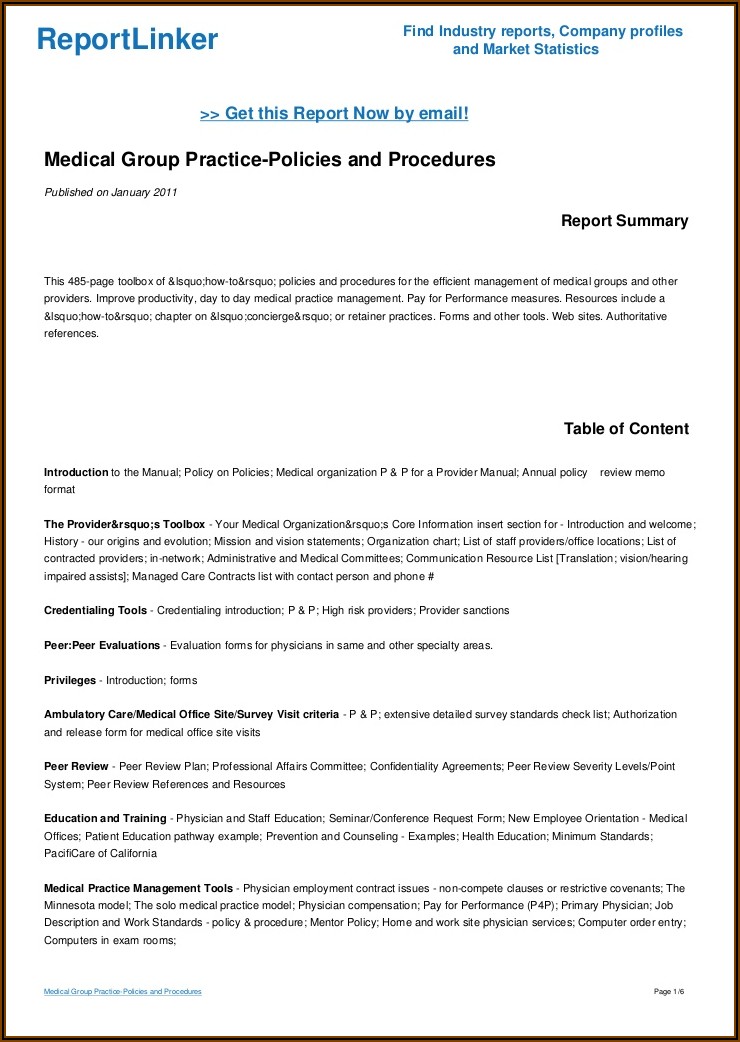
Hipaa Hitech Policies And Procedures Templates Template 1 : Resume

Hipaa Hitech Policies And Procedures Templates Template 1 : Resume

Small Business Policy And Procedures Manual Template Ccalcalanorte com

FREE 9 Sample IT Security Policy Templates in MS Word PDF

Security risk assessment template in Word and Pdf formats page 4 of 5
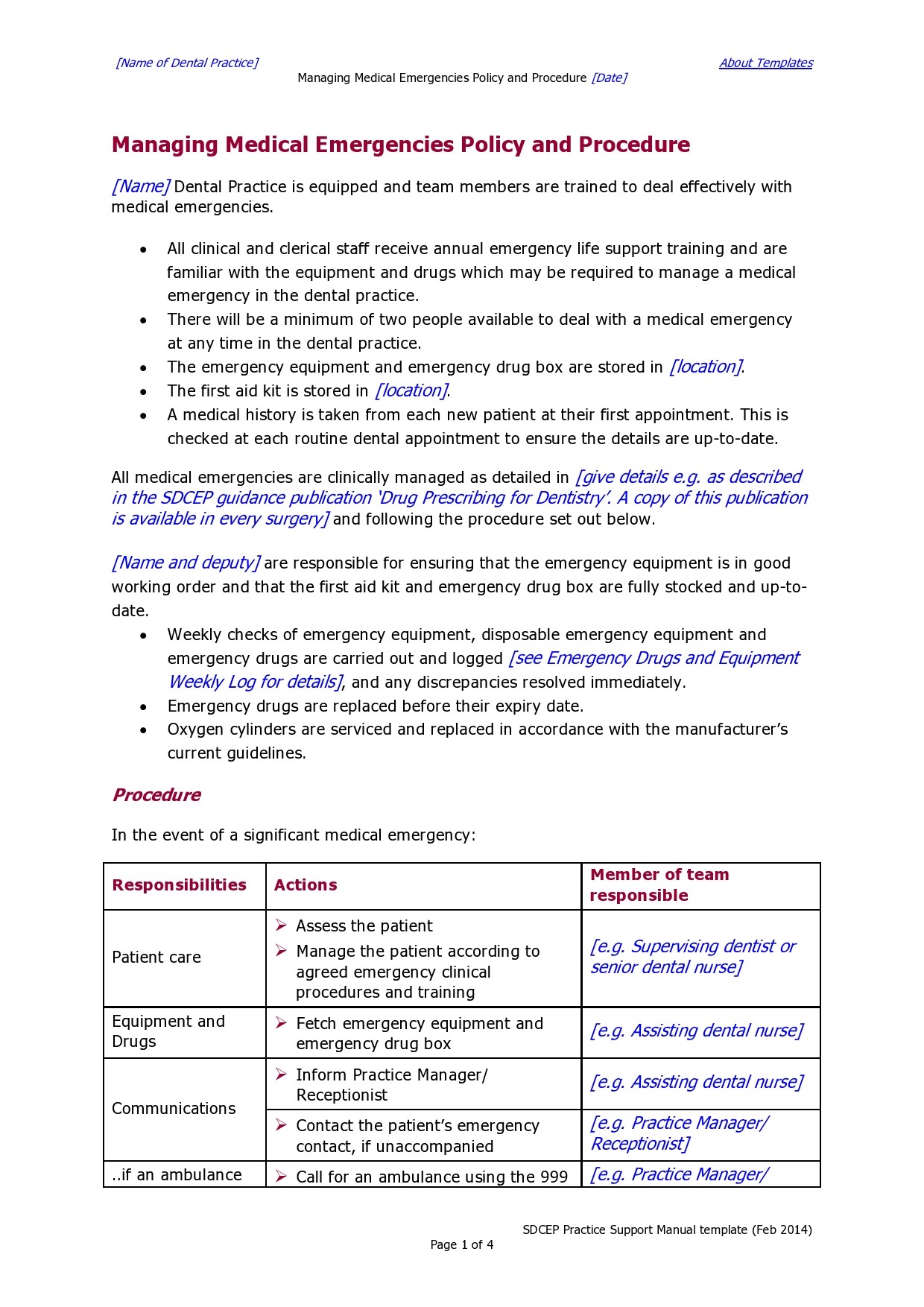
Policies And Procedures Template

Free Emergency Procedure Template to Edit Online

Physical Security Policy Template (Word PDF) Free Trial

Cyber Security Plan Template For Small Business prntbl

Procedures

Procedures

HIPAA Security Policies Procedures Templates
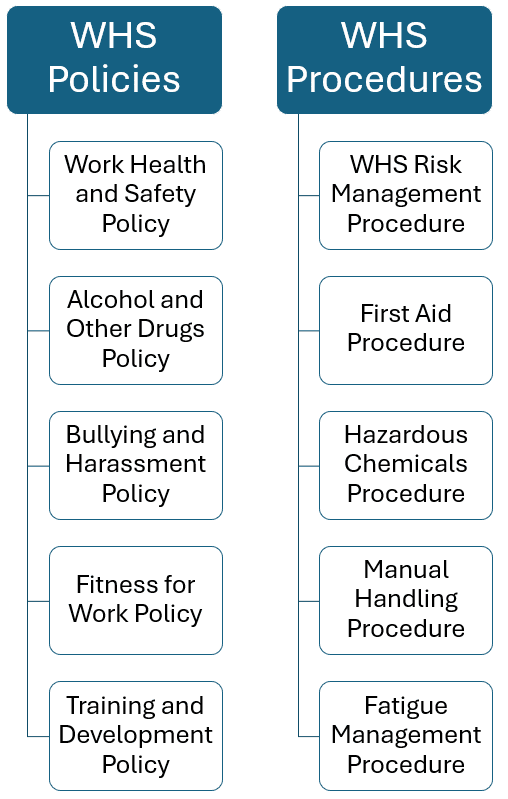
The Complete Guide to WHS Policies and Procedures in Australia Spire

Policy Manual Templates 16 Free Printable Word PDF Formats
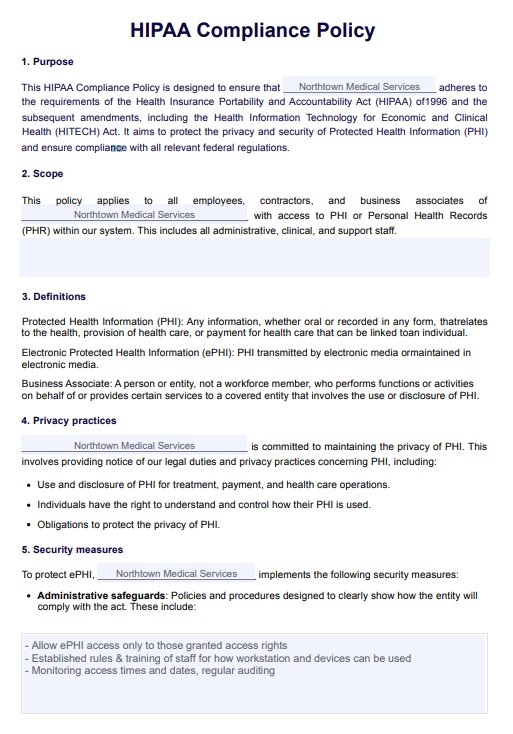
HIPAA Policy Template Example Free PDF Download

It Security Policy Template Free Free Templates 2024

Interview Questions for Ability to Follow Company Policies and

Interview Questions for Ability to Follow Company Policies and
Interview Questions for Ability to Follow Company Policies and

Product Showcase: Security Management System

Company Policy Template

Cyber Security Advice from Ex Hackers Vanguard Risk
Gruppenrichtlinienobjekt: Best Practices für Windows GPOs tenfold

Policies And Procedures Manuals Templates Bizmanualz Word template