Security Officer Resume Template
Here are some of the images for Security Officer Resume Template that we found in our website database.

Here s Why CEOs Should Consider Private Security

20 000 Free 安全管控 Security Images Pixabay

Security guard ALLIED CPR

Duties and demand of Security guard services in Los Angeles CITIGUARD

Off Duty Officers #1 Security Guard Company Security Guards

Shopping Mall Security in Houston TX Ranger Security Agency

Security Guard Service Idaho Falls ID Trident Security

What is manned guarding in the security industry

6 Large Venue Security Tips and Technologies The District Weekly

4080x1020 Resolution Cybersecurity Core 4080x1020 Resolution Wallpaper

Security Guard Service Sydney Hire Security Guard Sydney

What Is Cybersecurity? Forage

Safety Protocols for Armed Security Guards

750 Security Pictures HD Download Free Images on Unsplash
.jpg#keepProtocol)
Cyber security: how can your School protect itself from the latest threats?

Security Services Rodgers Security Solutions Inc
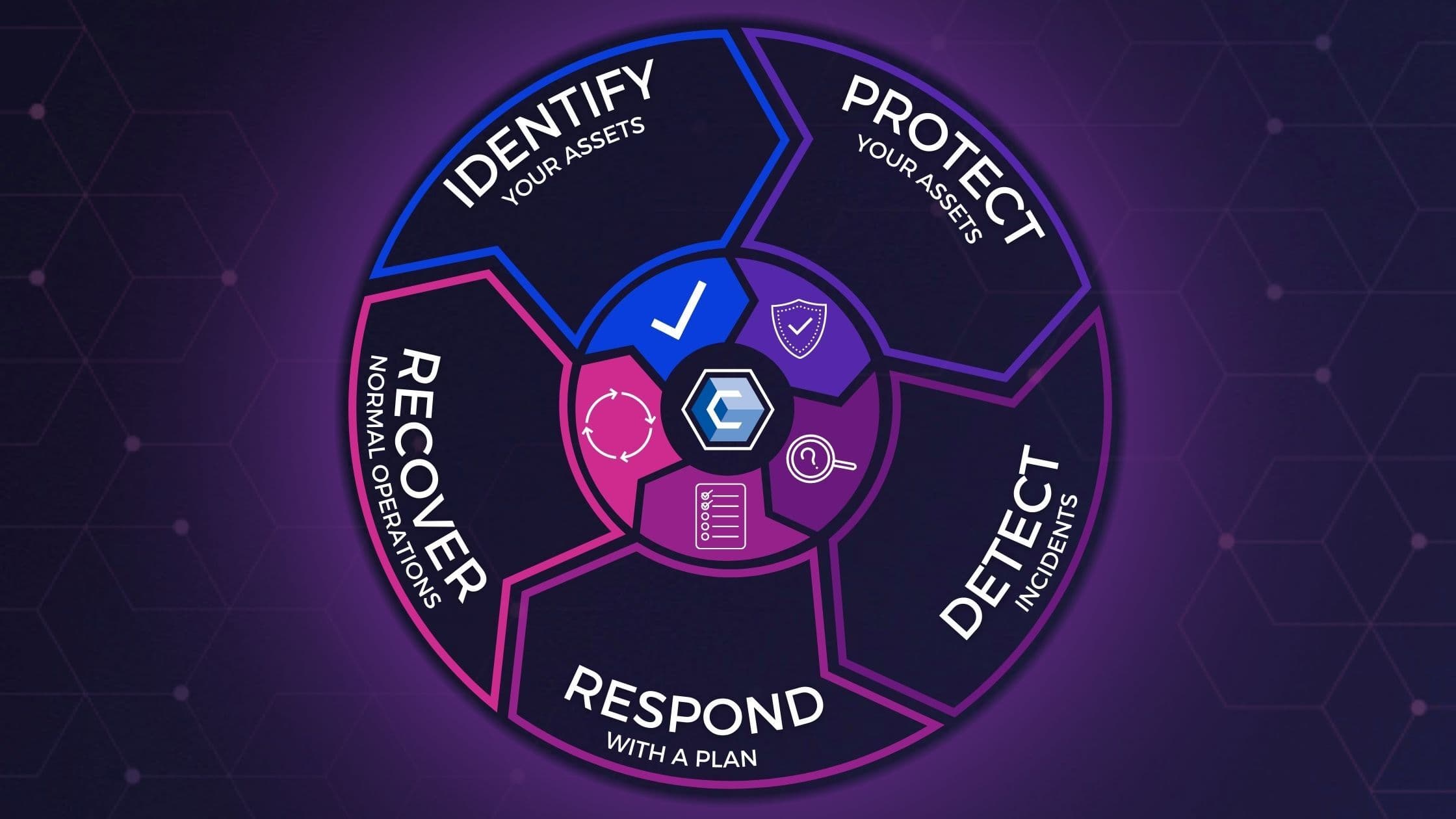
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

How we handle security needs ongoing security improvements Part 1

aimssoft com

National Retail #39 s Timely Collaboration with Ignite Systems Amidst Cyber

Cybersecurity Plan: 3 Keys for CISOs Trend Micro (US)

Protecting Your Building from Physical Security Breaches Radius Systems

Head of Security and criminal law enforcement Gauteng South Africa

Securing the Future: Exploring the Benefits of Security Services

What does Security mean to you? Timber Composite Doors Blog

Seattle Security Company Security Solutions Seattle Private

The war for cybersecurity talent hits the Hill Computerworld

Considerations for security officer training in healthcare facilities

Innovations and Breakthroughs from Nigerian Security Scholars

North London Event Security Services Mike Golf Security

CloudBric: The Future of Cloud Computing and Cyber Security by Carl

Security and Care RRVA

Bolstering cybersecurity readiness in the cloud Information Age
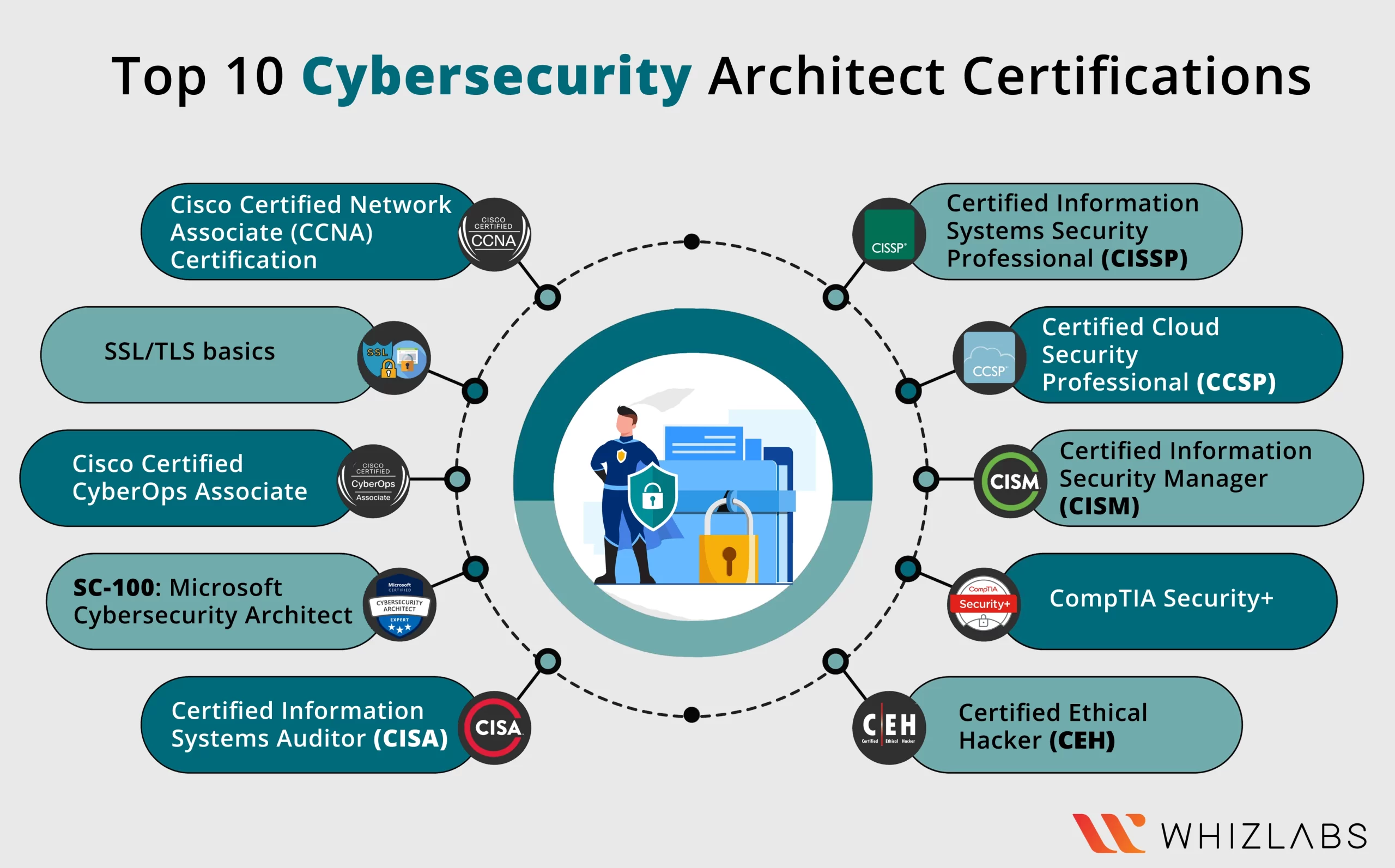
10 Best CyberSecurity Architect Certifications in 2024

Cyber security in software development: 12 outsourcing tips