Security Logo Design Template
Here are some of the images for Security Logo Design Template that we found in our website database.

Seeking Justice for Inadequate Property Security? Learn More

Duties and demand of Security guard services in Los Angeles CITIGUARD

CloudBric: The Future of Cloud Computing and Cyber Security by Carl

Agent de sécurité filtrage www securitsolutions fr
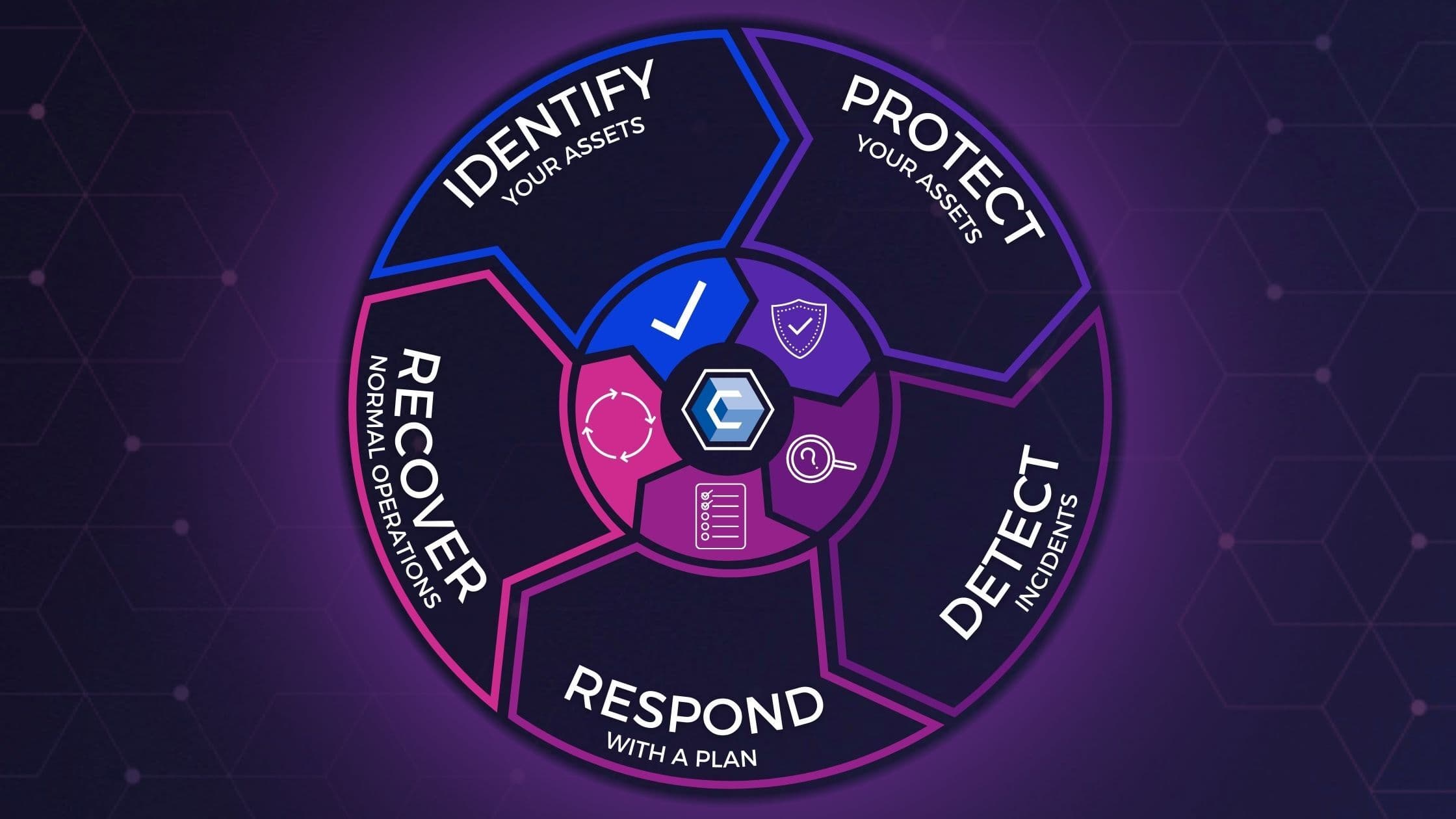
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

Our Services Black Hawk Security

Is New Hampshire ready to adopt a privacy and cybersecurity law? NH

Community Policy on Security Cameras CAM

What Is Cybersecurity? Forage

Armed Off Duty Security Services Law Enforcement Specialists Inc

5 Contoh Surat Lamaran Kerja Security/Satpam Lengkap dan Cara

Network security concept Cyber protection Anti virus software

What is manned guarding in the security industry

California #39 s Premier Security Company Diamond Security Service

Security Services Images

BBC investigation uncovers fraudulent security courses Counter Terror

Cyber Security Images

ISO/IEC 27032:2023 Cybersecurity Guidelines ANSI Blog

Security Companies Johannesburg Complete List 2023

What to Look for in Travel Security and Executive Protection Services

Cybersecurity Plan: 3 Keys for CISOs Trend Micro (US)

7 Best Practices of Data Security for Businesses in Tech Corporate

Managed Cybersecurity Services Solution RTCS

Understanding the 3 Phases of Cybersecurity Architecture Ardoq

Cyber Security for OT AutomaTech

How to maintain business security when you re not there? AtulHost

BroadBand Nation: Cybersecurity Career Pathway (INFOGRAPHIC)

Understanding the quot attacker mindset quot in security CBTS
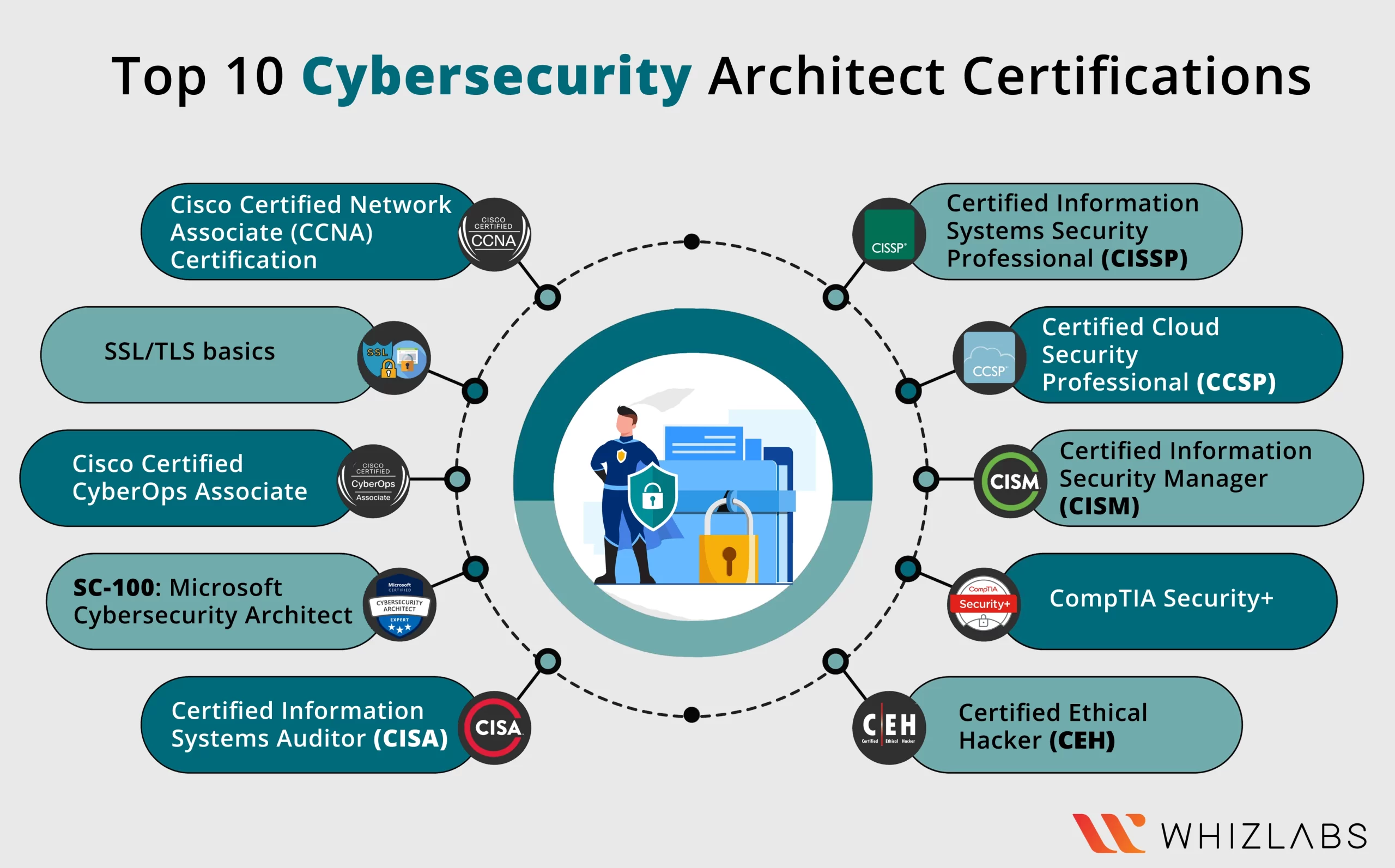
10 Best CyberSecurity Architect Certifications in 2024
.jpg#keepProtocol)
Cybersecurity Issues In Ai

Bolstering cybersecurity readiness in the cloud Information Age

Security and the Right to Security Gentil Kasongo

5 security measures that experts follow (and so should you ) Panda

Security Considerations for Deploying Notes Plugins

Importance of Cybersecurity in Business

Security Commitments Metafour com

WSQ Security Courses Singapore KnowledgeTree Training

The Benefits Of Corporate Security You Need To Know About Toronto

Security Industry For 17 Year Olds Skills Training College

Use an Air Gap for Security SlawTips

Greater business security flexibility with alarm system partitions EPS

Head of Security and criminal law enforcement Gauteng South Africa

aimssoft com

OhNo Trevor

5 Benefits of Using Security Officers From a Private Security Company

How is Edge Security Helping Secure Devices that Use Edge AI? Xailient

Ontario Security Group Your Trusted Security Partner

Security TC Facilities Management

Security Wallpapers (63 images)

Residential Security Services: Residential Security Guard Services

Cyber Security Consultancy Solutions Strategy Specialist OfficeLabs

What does Security mean to you? Timber Composite Doors Blog

Brace Yourself Cybersecurity Threats Are On The Rise

About us RIA Security

Combatting the New Security Normal PaymentsJournal

The Case for Incorporating Cultural Awareness into Executive Protection

Computer Network Security

The Role of Forensics in Cyber Security

Gartner #39 s 8 Cybersecurity Predictions for 2023 2025 Krontech