Security Daily Activity Report Template
Here are some of the images for Security Daily Activity Report Template that we found in our website database.

Security guard ALLIED CPR

Safety Protocols for Armed Security Guards

What Is Cybersecurity? Forage
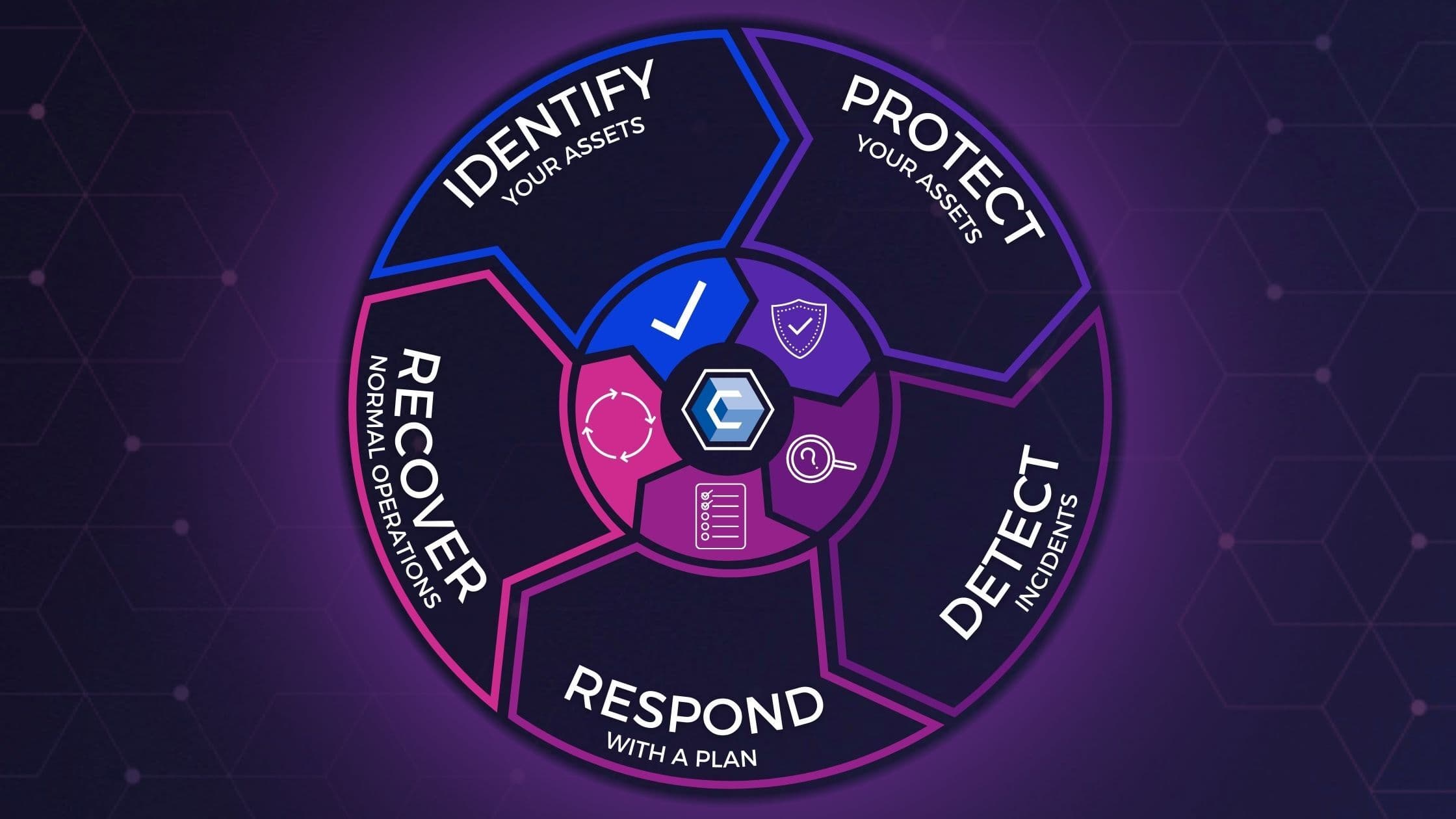
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

20 000 Free 安全管控 Security Images Pixabay

Here s Why CEOs Should Consider Private Security

A Guide to The Different Types of Security Service Corinthians Group

How Armed Security Guards Ensure Safety 24/7 The Power Of Dedication

Cybersecurity Plan: 3 Keys for CISOs Trend Micro (US)

The war for cybersecurity talent hits the Hill Computerworld

CloudBric: The Future of Cloud Computing and Cyber Security by Carl
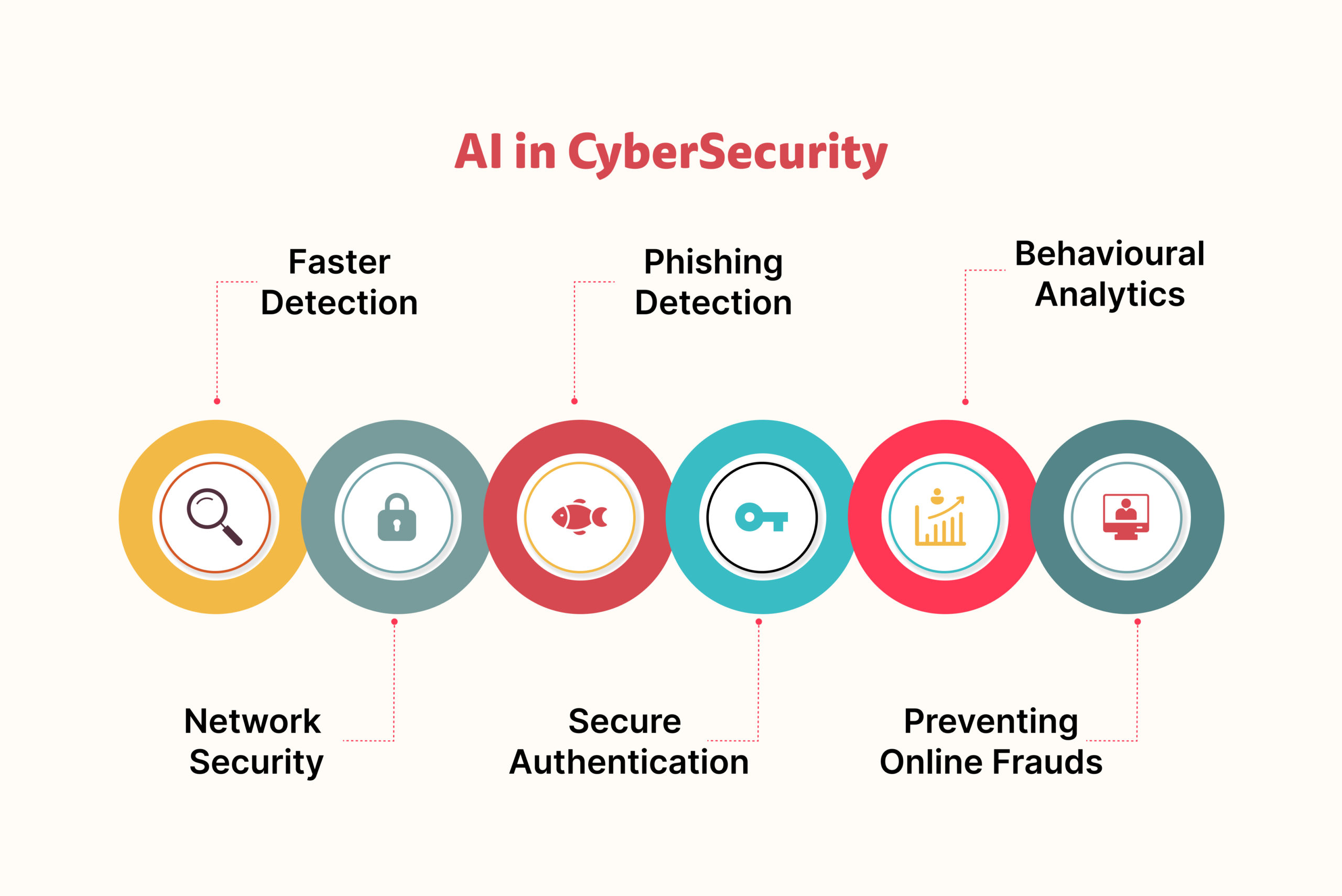
How AI in Cybersecurity Reimagines Cyberthreat

Cyber Security: 7 Steps to Developing a Cloud Security Plan BIIA com

Shopping Mall Security in Houston TX Ranger Security Agency

Security Services Rodgers Security Solutions Inc

Off Duty Officers #1 Security Guard Company Security Guards

6 Large Venue Security Tips and Technologies The District Weekly

4080x1020 Resolution Cybersecurity Core 4080x1020 Resolution Wallpaper

超过 50000 张关于 网络安全威胁图片 和 网络安全 的免费图片 Pixabay

Modern Devices Included in Most Wellington Security Services

Duties and demand of Security guard services in Los Angeles CITIGUARD

Greater business security flexibility with alarm system partitions EPS
.jpg#keepProtocol)
Cyber security: how can your School protect itself from the latest threats?

Why Most People Avail Services Of Security Guard Companies? AZ Web

aimssoft com

North London Event Security Services Mike Golf Security

What to Look for in Travel Security and Executive Protection Services

Health and Safety Resources

The Case for Incorporating Cultural Awareness into Executive Protection

6 common cybersecurity mistakes you can fix today

CyberSecurity: The goals are simple: safety and security Complete Chain

The Sony Pictures Hack and Learning Information Security Lessons the

Security and Care RRVA

750 Security Pictures HD Download Free Images on Unsplash

Innovations and Breakthroughs from Nigerian Security Scholars