Security Camera In Use Sign Printable
Here are some of the images for Security Camera In Use Sign Printable that we found in our website database.

Duties and demand of Security guard services in Los Angeles CITIGUARD

300 000 Free Security Wallpaper Security Images Pixabay

Our Services Black Hawk Security

Security Officer Duties and Responsibilities

What Is Cybersecurity? Forage

Seeking Justice for Inadequate Property Security? Learn More

ISO/IEC 27032:2023 Cybersecurity Guidelines ANSI Blog

超过 50000 张关于 网络安全威胁图片 和 网络安全 的免费图片 Pixabay

750 Security Pictures HD Download Free Images on Unsplash

Security Guard Images

Cyber Security: 7 Steps to Developing a Cloud Security Plan BIIA com

5 Contoh Surat Lamaran Kerja Security/Satpam Lengkap dan Cara

What is Cybersecurity? Types Threats and Cyber Safety Tips

aimssoft com

Cybersecurity Plan: 3 Keys for CISOs Trend Micro (US)

Security Companies Johannesburg Complete List 2023

Head of Security and criminal law enforcement Gauteng South Africa

The war for cybersecurity talent hits the Hill Computerworld

Considerations for security officer training in healthcare facilities

What does Security mean to you? Timber Composite Doors Blog

Cybersecurity Emory Continuing Education

Understanding the 3 Phases of Cybersecurity Architecture Ardoq

GLBA Compliance Checklist: Key Requirements BD Emerson

How to Handle Conflict in a Security Role in Manchester

Securing the Future: Exploring the Benefits of Security Services

IS A SECURITY JOB RIGHT FOR YOU? Dailysun

Security Considerations for Deploying Notes Plugins

Threat Hunting: The Necessity of Proactive Cybersecurity ThreatHunter ai

Cybersecurity Medical Devices and IEC 81001 5 1 TÜV SÜD

How to maintain business security when you re not there? AtulHost
.jpg#keepProtocol)
What is Cybersecurity? Everything You Need to Know
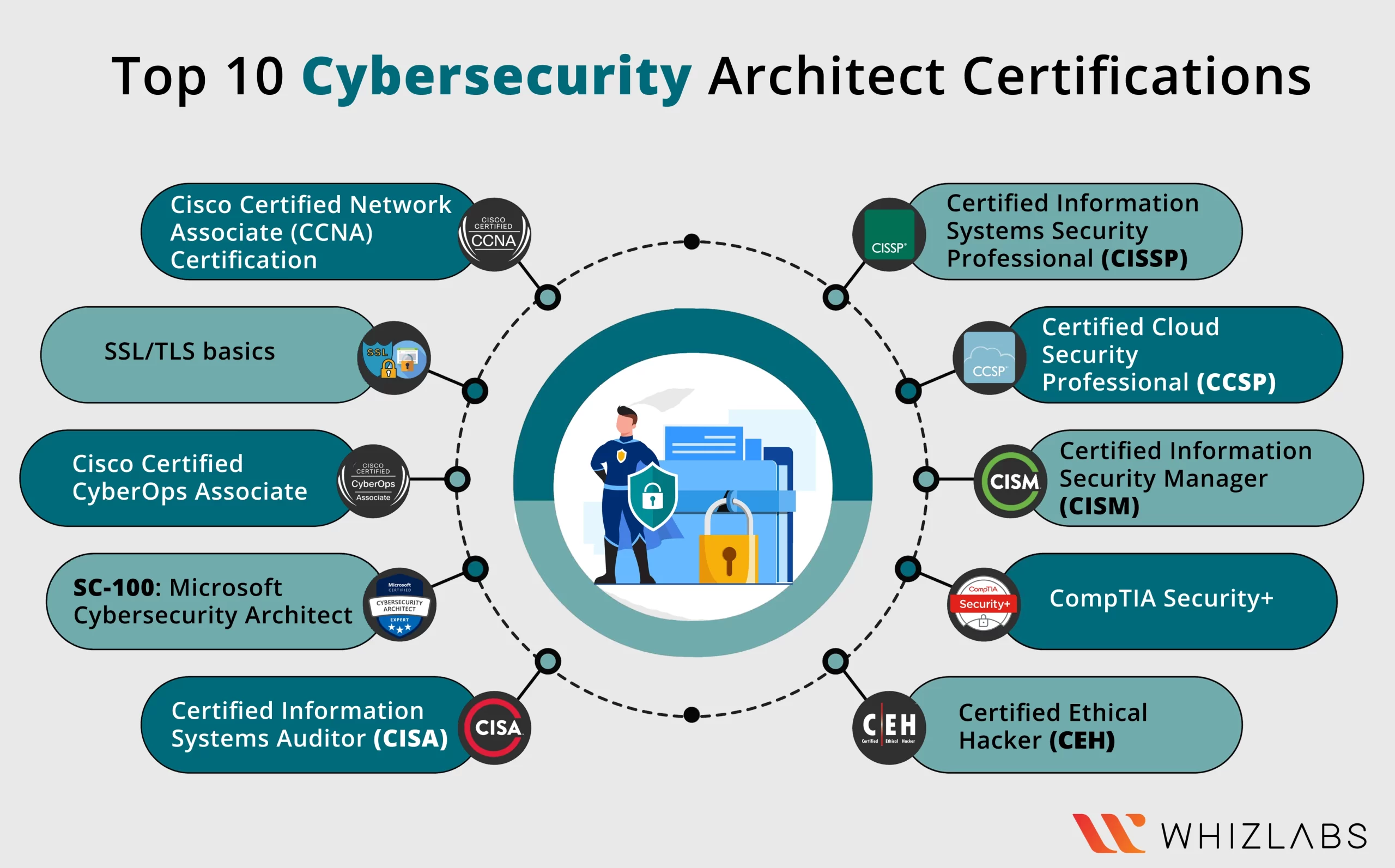
10 Best CyberSecurity Architect Certifications in 2024

Bolstering cybersecurity readiness in the cloud Information Age

Security TC Facilities Management

Efficient Tactics Of Cyber Security An Updated Examination Diamond Sr