Security Business Proposal Template Free
Here are some of the images for Security Business Proposal Template Free that we found in our website database.
Free Template For Business Proposal Letter Infoupdate org

Business Proposal Template in Word PDF Google Docs Pages Download

Sample Free Sample Security Proposal Security Guards Companies Cyber

Proposal Cover Template in Google Docs PDF Word InDesign Download

Security Business Proposal Template Free
Security Business Proposal Template Free

Security Business Proposal Template Free

Security Business Proposal Template Free

Security Templates in PDF FREE Download Template net

Security Business Proposal Template Free
Business Proposal Template InDesign Free

Security Services Proposal Template startasecuritycompany com

Free Sample Business Proposal Template to Edit Online

Business Plan Proposal Template Free

Free Handyman Business Proposal Template to Edit Online

Simple Business Proposal Template

Free Sample Service Business Proposal Template to Edit Online

Security Proposal Template Free

Free Simple Sales Business Proposal Template to Edit Online

Free Spa Business Proposal Template to Edit Online

Free Event Management Business Proposal Template to Edit Online

Free Tech Startup Business Proposal Template to Edit Online

Free Business Proposal Template Ms Word Sampletemplate my id

Free Food Truck Business Proposal Template to Edit Online
Writing A Business Proposal Template Free 11 Useful Business Proposal

Free Fee Proposal Template to Edit Online

Free Law Firm Business Proposal Template to Edit Online

Free B2B Business Proposal Template to Edit Online

Free Printable Business Proposal Template Doc

Free Church Proposal Template to Edit Online

Free Church Proposal Template to Edit Online

Free Church Proposal Template to Edit Online

Free Church Proposal Template to Edit Online

Free Business Proposal Template Proposal Templates Docs Templates

Free Situation Target Proposal Template to Edit Online

Free Agricultural Farming Proposal Template to Edit Online

Security Guard Services Proposal Template

Premium Vector Business proposal design or project proposal template

Creative Business Proposal Cover Design Template AI Free Download

Free Hotel Insurance Proposal Template to Edit Online

Free Church Project Proposal Format Template to Edit Online

Free Church Project Proposal Format Template to Edit Online

Free Church Project Proposal Format Template to Edit Online

Free Church Project Proposal Format Template to Edit Online

Free Church Project Proposal Format Template to Edit Online

Free Church Project Proposal Format Template to Edit Online

Proposal Cover Page Template

Free Printable Business Proposal Templates Word PDF Investors
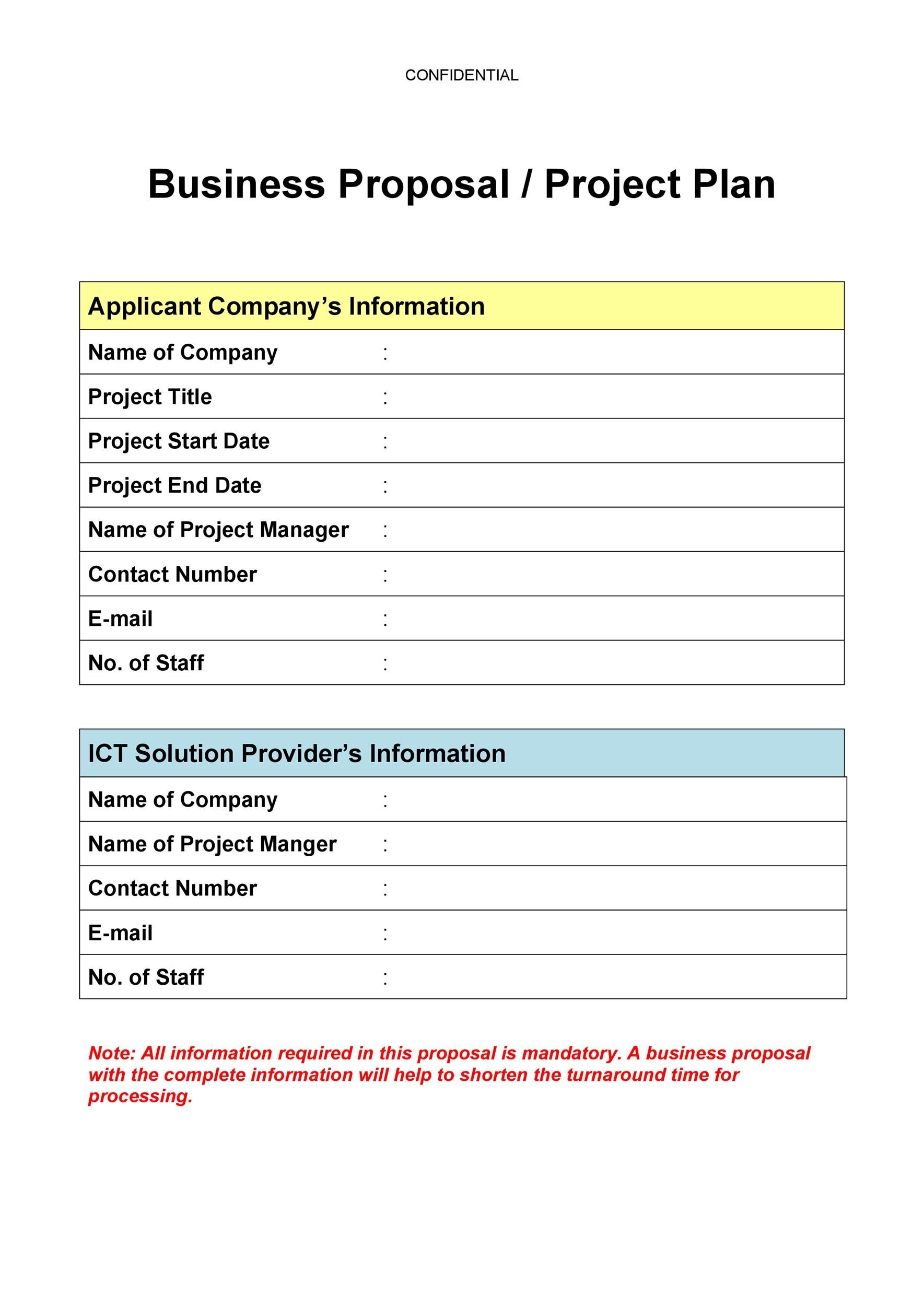
Partnership Proposal Template Word

Partnership Proposal Template Word

Google Docs Business Proposal Template at netnatashablog Blog

Free Business Letter with Subject Line Template to Edit Online

Page 7 FREE Proposal Templates Examples Edit Online Download

Editable Blank Proposal Templates in Word to Download

Sample Business Proposal Examples

Business Proposal Template

Page 3 Sales Proposal Templates in Google Docs FREE Download

Service Contract Proposal Template

Executive Summary Template For Proposal
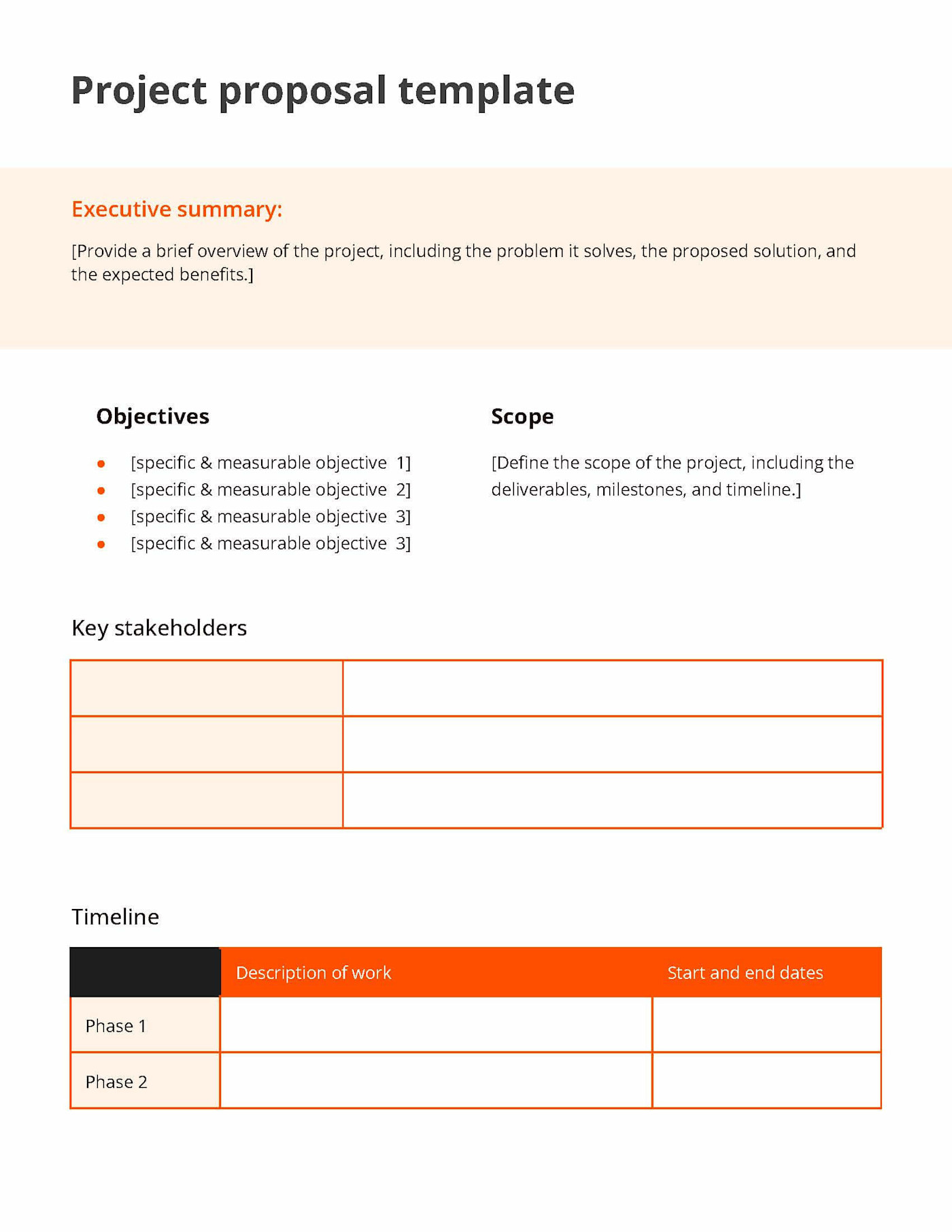
Basic Rfp Template prntbl concejomunicipaldechinu gov co