Secure To A Dock Crossword
Here are some of the images for Secure To A Dock Crossword that we found in our website database.

Where ships dock Crossword Clue Daily Commuter

Secure Storage Crossword Clue

Leaving the Dock Crossword American Sailing
)
Space where dock set up (4) Crossword Clue Answers Crossword Solver

Secure as a Ship #39 s Line: Meaning and Context Explained

Secure as a Ship #39 s Line: Meaning and Context Explained

What to Know About Keeping the Yacht Secure on the Dock
lake dock crossword by cubic dice letters 3D illustration Stock Photo

3d Secure Search Crossword Cross Crossword Puzzle Photo Background And
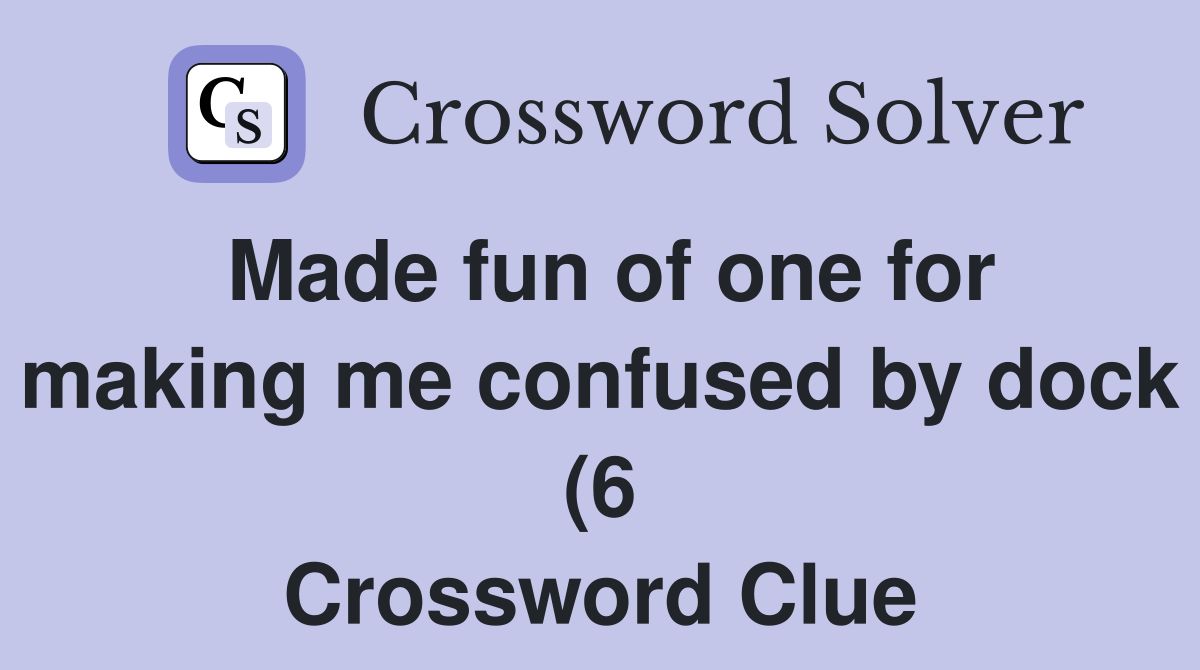)
Made fun of one for making me confused by dock (6) Crossword Clue

3d Secure Guard Crossword Stock Photo Download Image Now Antivirus

Knowing how to secure a boat properly to a dock is a skill that every
)
Arab beginning to modify secure method of restraint (7) Crossword

3D Free Secure Crossword on white background Stock Photo Alamy

Floating Dock Anchoring Hardware Maynardville TriStar Renovations

Loading Dock Door Raxdoor

Small Orchard Crossword Clue Answers TechWiser

NYT Mini Crossword: 8 Strategies To Solve It Fast

Dock Lines: 1/2 quot x 20 #39 Double Braided Nylon Boat Dock Lines Premium

Near the Loading Dock a Detailed Diagram Illustrates How To Properly

Social Media Crossword Stock Photo Download Image Now Connection

How to Use a Dock Plate Beginner #39 s Guide

The Dangers of the Loading Dock How To Avoid Them

Guardian Prize crossword No 29 775 by Paul Fifteensquared

Guardian Prize crossword No 29 775 by Paul Fifteensquared

Guardian Prize crossword No 29 751 by Brockwell Fifteensquared

USB C Hub for Microsoft Surface Pro 8 pro 9 10 11 2024 Dock Pro X

Premium Photo White boat rope attached to a wooden dock with dark

Premium Photo White boat rope attached to a wooden dock with dark

Premium Photo White boat rope attached to a wooden dock with dark

KeyBudz Secure Dock for AirTag 2 pack Billig

Lexington Volleyball Secure Spot in Final Lexington Progress

Secure Docks completed to comply with current HMCTS Courts Tribunals

KEYBUDZ เคสซิลิโคนใส่ AirTag พร้อมพวงกุญแจ AirTag Secure Dock Silicone

Crossword Labs: Сөзжұмбақ құрастыру quot Bilimpaz quot

Never crash into a dock again Safe secure accessible One person

Dashboard American Sailing

NAYELI LIMA INSURANCE BROKER ( nzinsurancecorp) • Instagram photos

Stow It Safe Dock Locker Company Inc A reminder that our vertical

Devices Pocket lint

The Steamship Authority

KickPlate (ToeBoard) Ideal Safety for Elevated Work Surfaces

Costa Rica You Tours costaricayoutours gmail com Facebook

AdU SHS Commission on Elections Manila

Funkytown Chaat DFW Chaat Mini Pancakes ( funkytownchaat

Pritunl Icon Stock Photos Free Royalty Free Stock Photos from

Shop Aluminum Anchoring Arm for Secure Dock Stability by Candock

Misfit Strength Studio ( misfitstrengthstudio) • Instagram photos and
Color wheel art lasopajd

Colour Japanese crossword Spatter Dock

Italian composer Gioachino Crossword Clue Answers

FloDragRacing 📣 ATTENTION IN THE PITS: 📣 Due to Facebook

Hickory Dickory Dock Activities Crafts and Worksheets for Kids

iPad docking station adds 8 essential ports Cult of Mac

How To Keep Ants Out of the Boat BeatPests

Eastwind Development on LinkedIn: Framing is well underway at The Aston

Transform Justice CourtWatch London

Just wrapped up our first webinar in a while on Bail Remand and the

Countrywide Paving Concrete on LinkedIn: May your day be as lucky as