Ransomware Policy Template
Here are some of the images for Ransomware Policy Template that we found in our website database.

Ransomware Incident Response Plan Template PDF Computer Security

Ransomware Policy Template
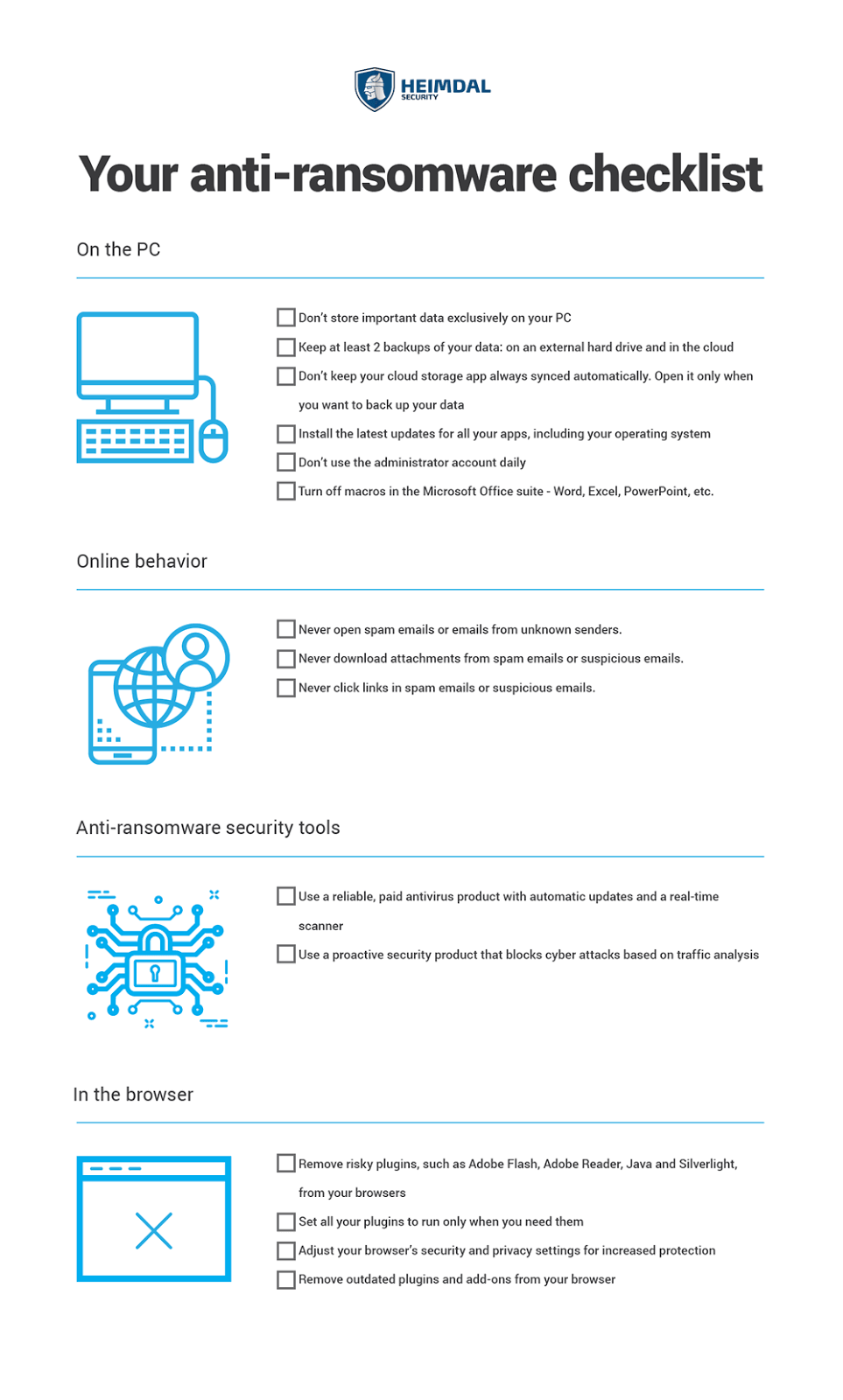
Ransomware Policy Template

Ransomware Policy Template

Ransomware Policy Template

Ransomware Response Playbook Policy Template Banking and Fintech

Ransomware Policy Template

Ransomware Incident Response Plan Template
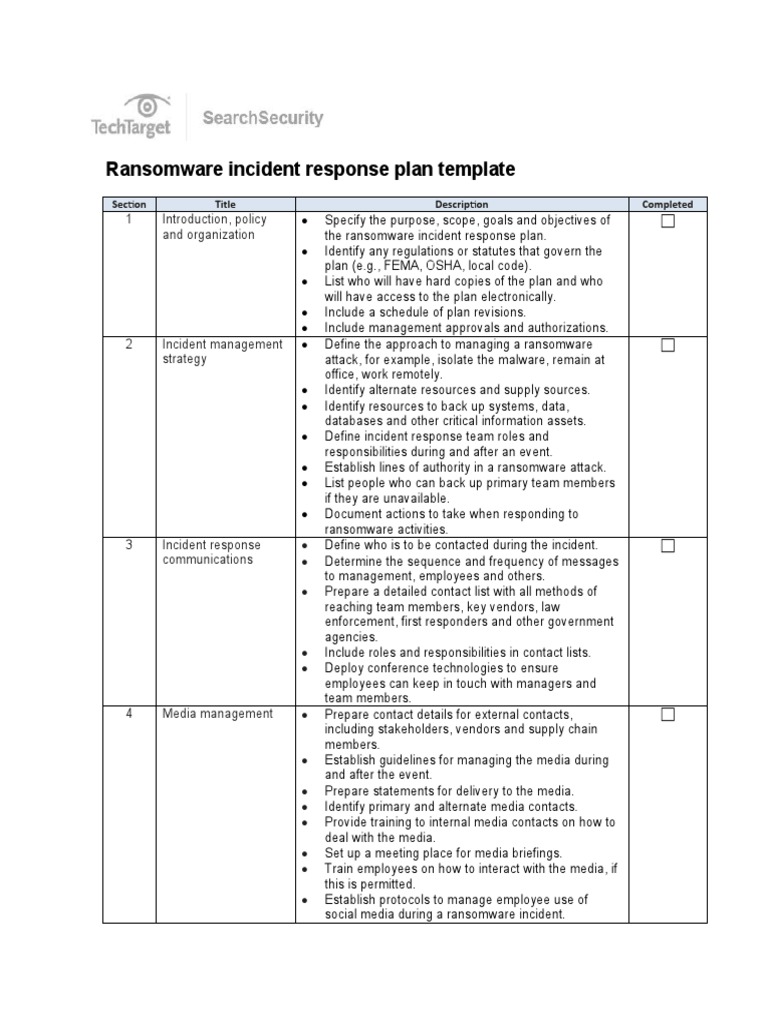
Ransomware Incident Response Plan Template
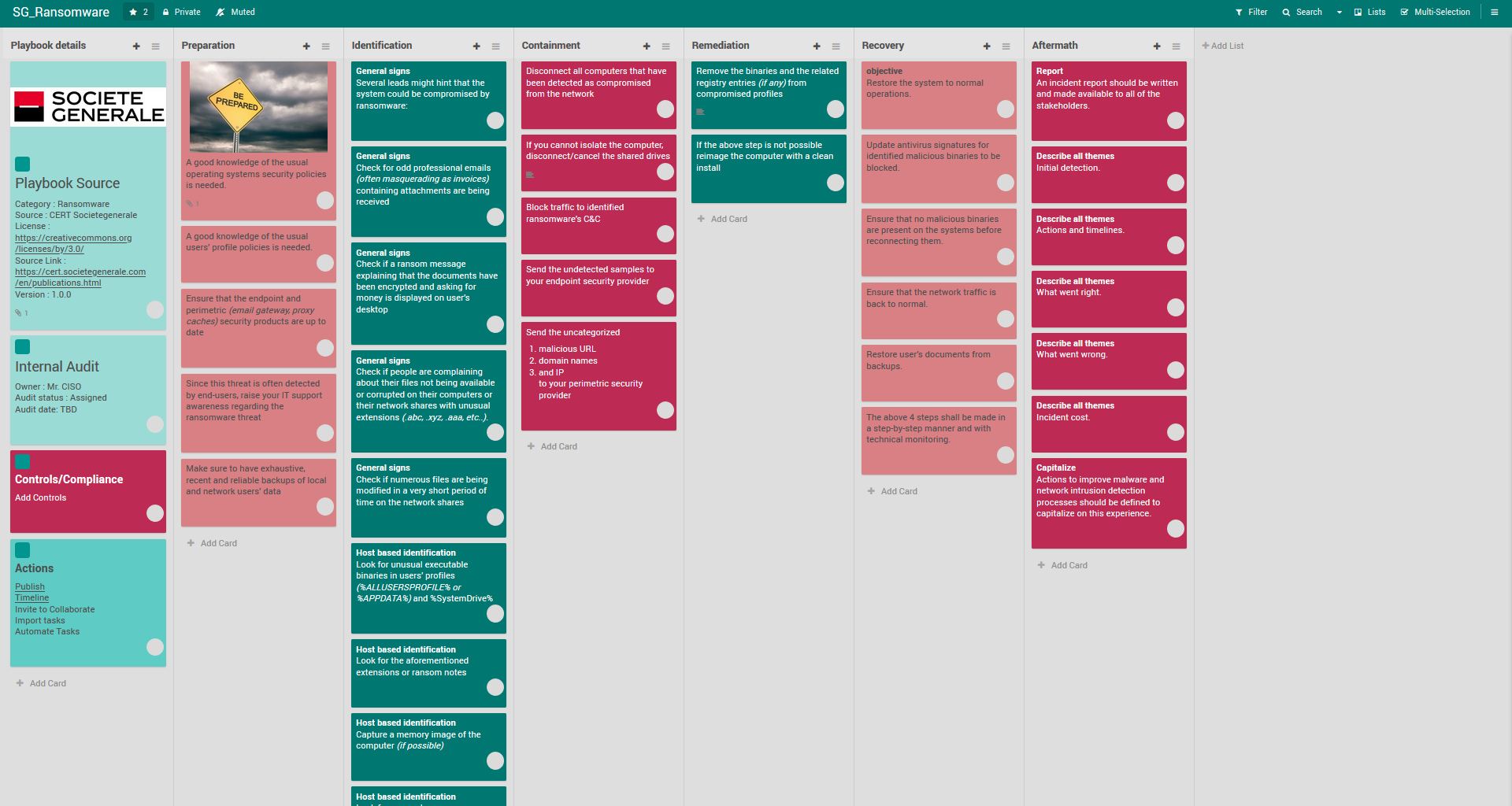
Ransomware Playbook Template
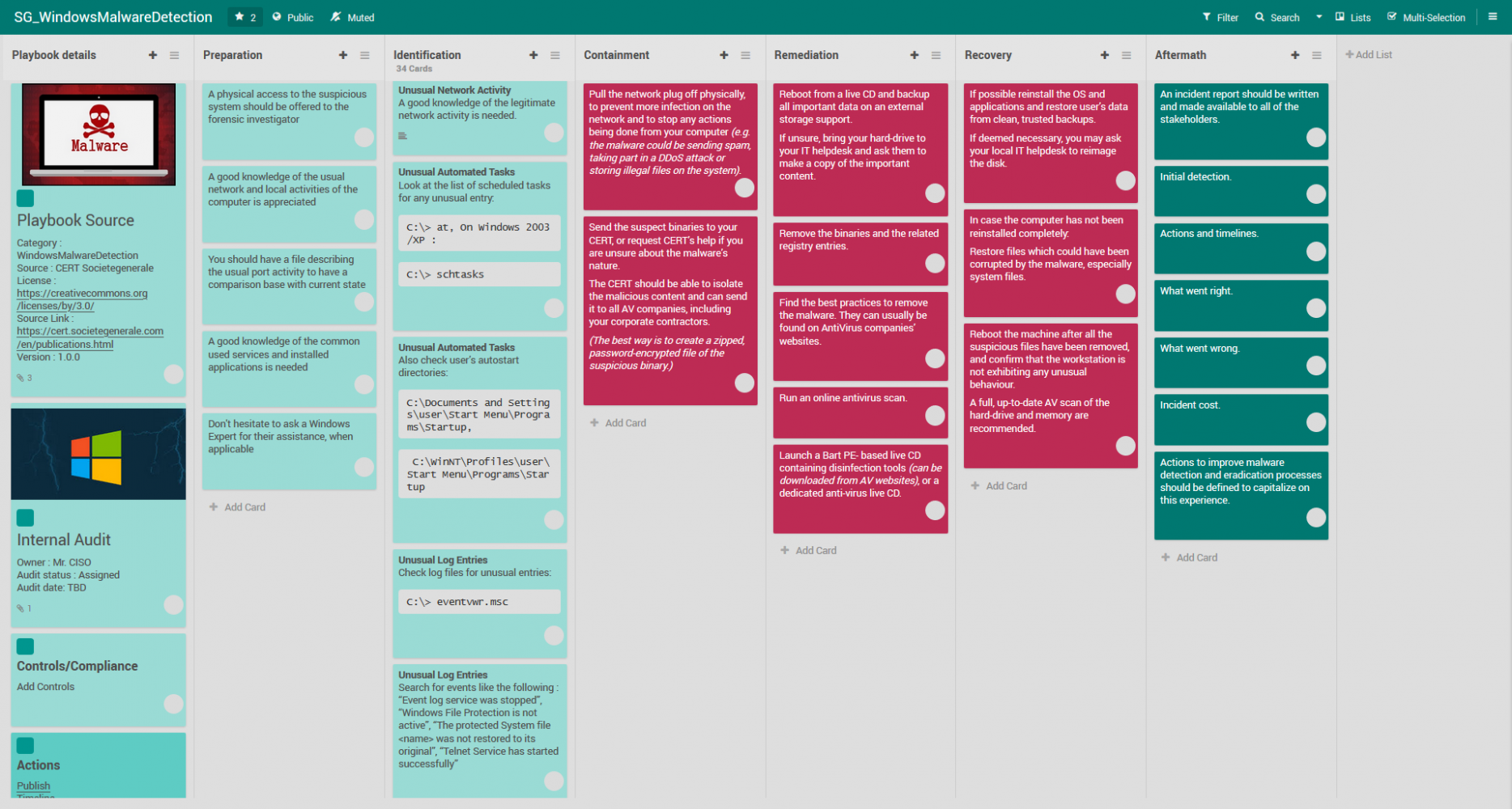
Ransomware Playbook Template
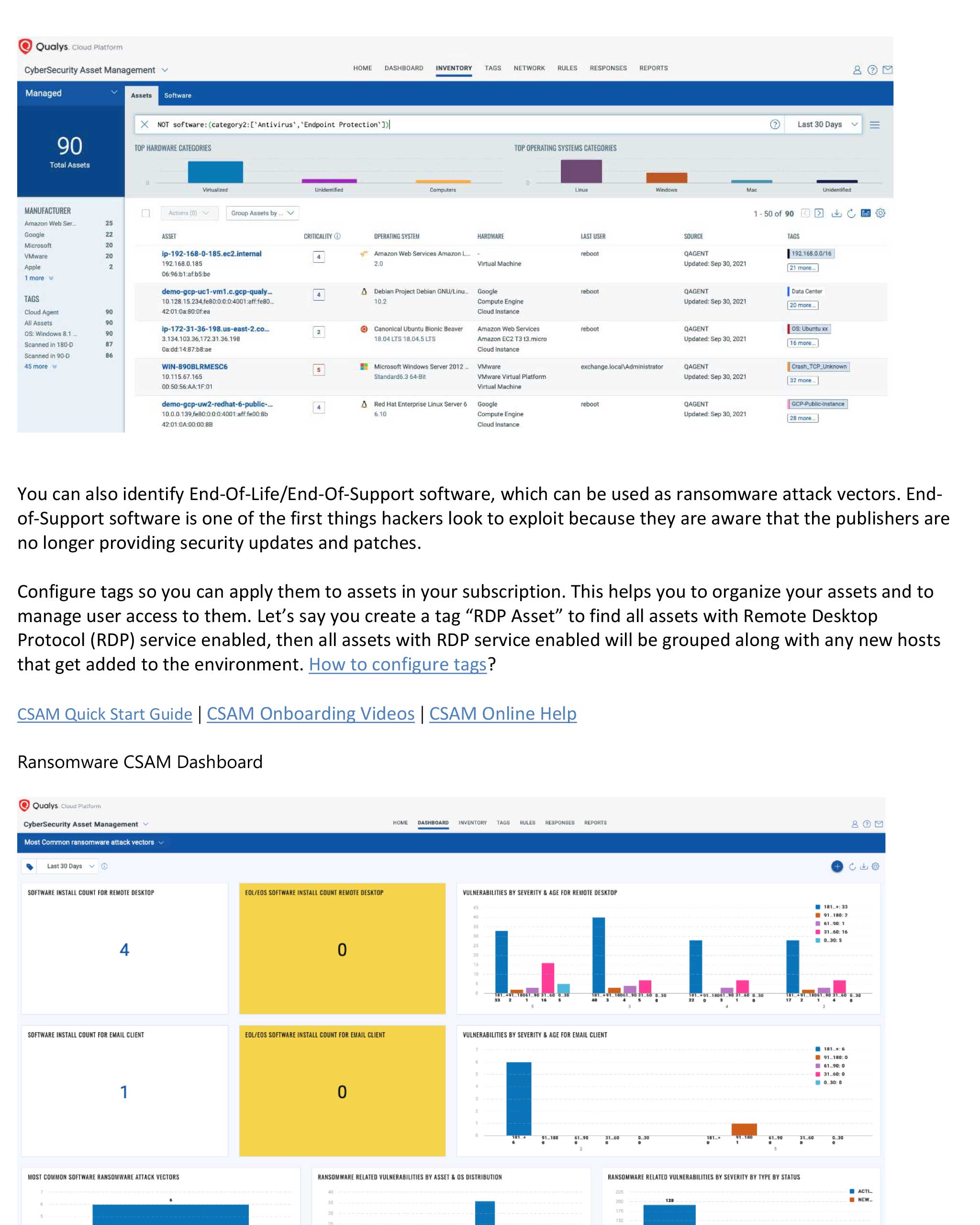
Ransomware Playbook Template Nist
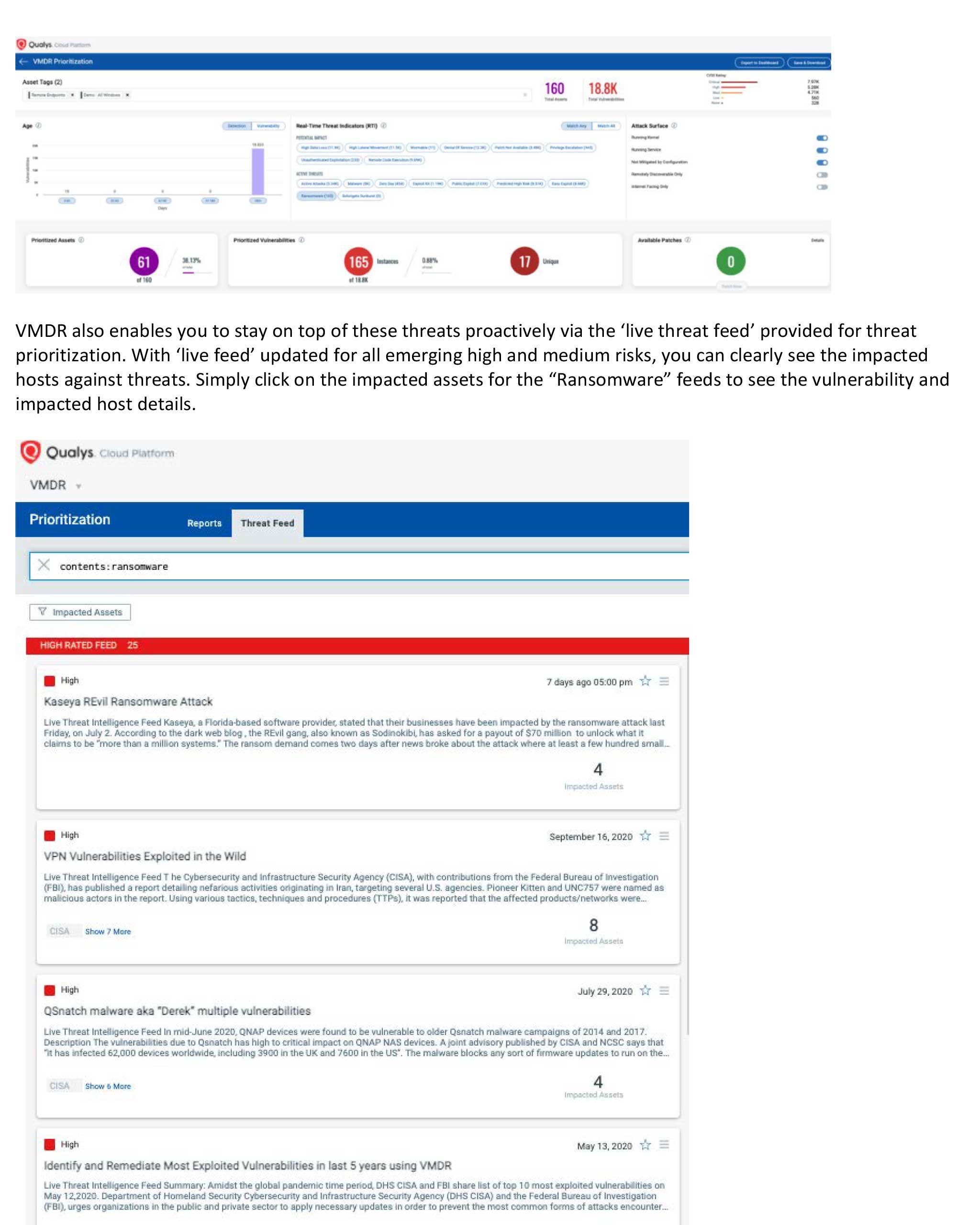
Ransomware Playbook Template Nist

Incident Response Playbook Template

Ransomware Playbook Template Nist

Ransomware Playbook Template English Version Felipe Machado

Ransomware Playbook Template
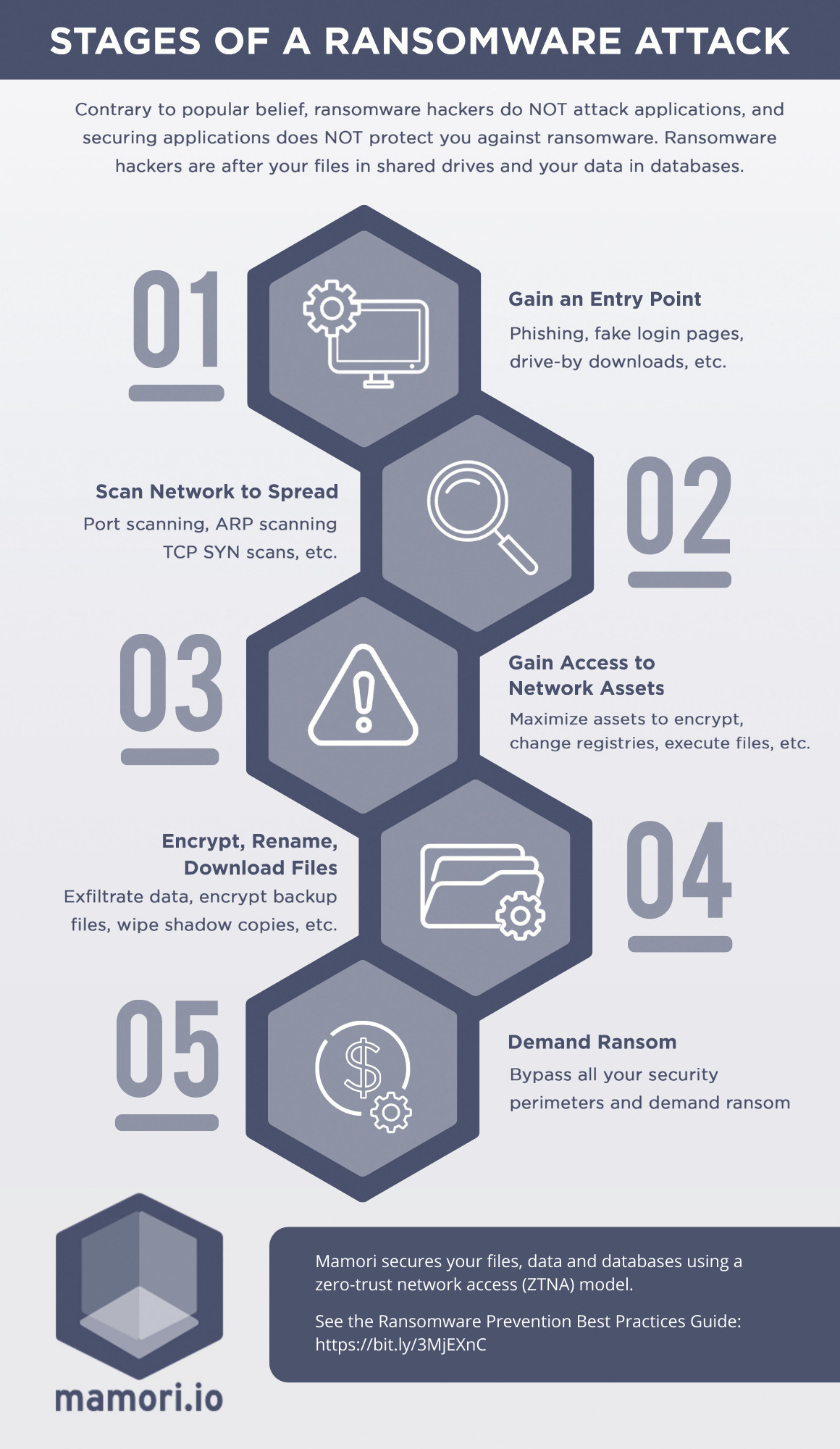
Ransomware Recovery Plan Template prntbl concejomunicipaldechinu gov co
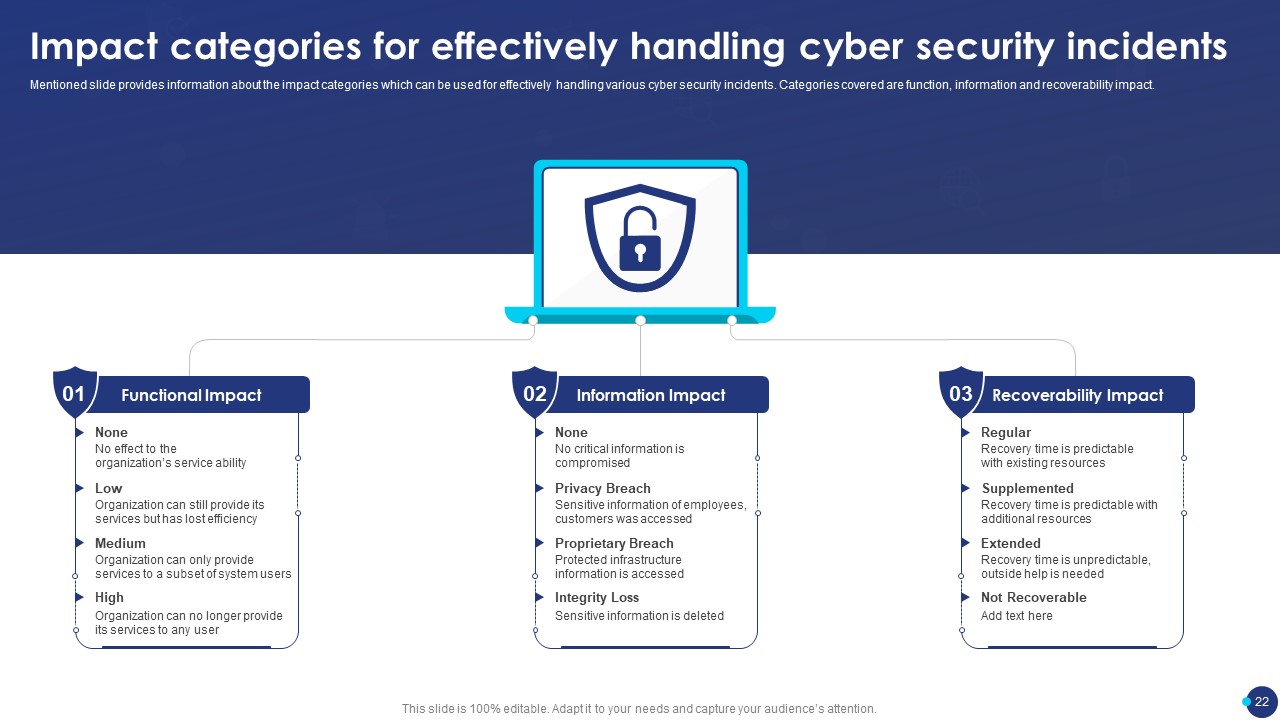
Incident Response Playbook Template

incident response plan template/playbook ransomware md at master

Ransomware Incident Response Playbook Template Ransomware incident

Ransomware Response Playbook PDF

PLAYBOOK RESPONSE RANSOMWARE PDF Ransomware Computer File

Incident Response Methodology Ransomware PDF Ransomware Malware

Ransomware Incident Response Plan Download Free PDF Malware

Ransomware Incident Response Playbook

Free Ransomware Incident Response Playbook: Protect Your Organization Now

Ransomware Playbook Slide Team