Privileged Access Management Policy Template
Here are some of the images for Privileged Access Management Policy Template that we found in our website database.

Identity and Access Management Policy PDF Information Security

Privileged Access Management Policy Template Edge Linking

Privileged Access Management Policy Template Download Free PDF

Privileged Access Management Policy Template TEC
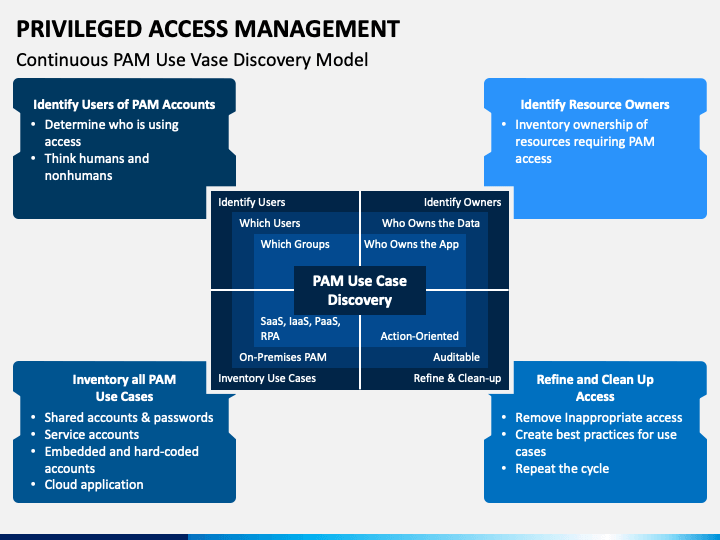
Privileged Access Management Policy Template
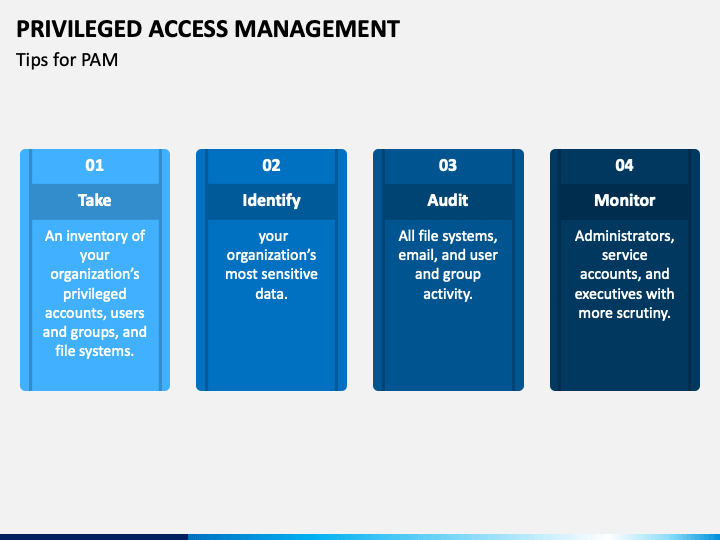
Privileged Access Management Policy Template

Privileged Access Management Policy Template

Privileged Access Management Policy Template DataBreachToday

Privileged Access Management Policy Template BankInfoSecurity

IT Identity Access Management Policy Manual Template in PDF Word

IT Identity Access Management Policy Manual Template in PDF Word

Privileged User Accounts Management Procedure IT Procedure Template
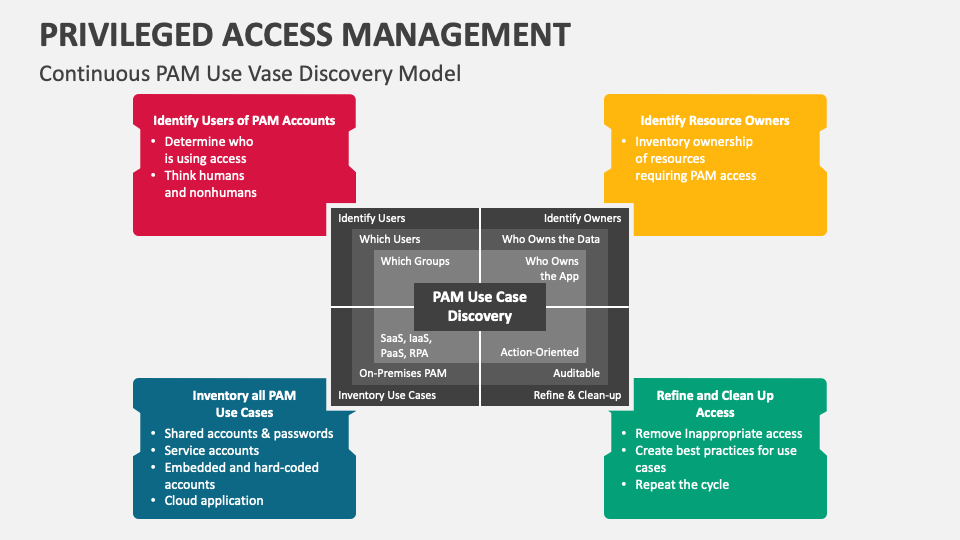
Privileged Access Management PowerPoint and Google Slides Template
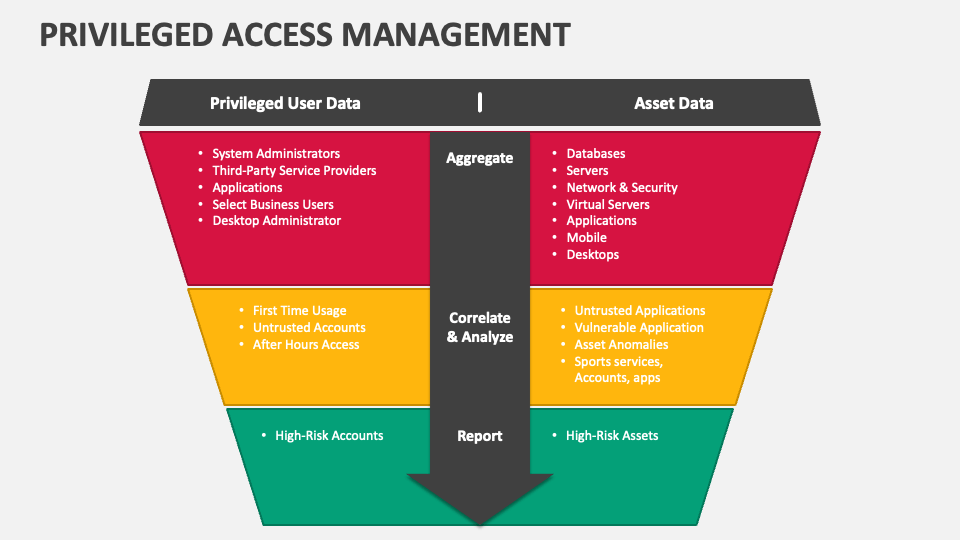
Privileged Access Management PowerPoint and Google Slides Template
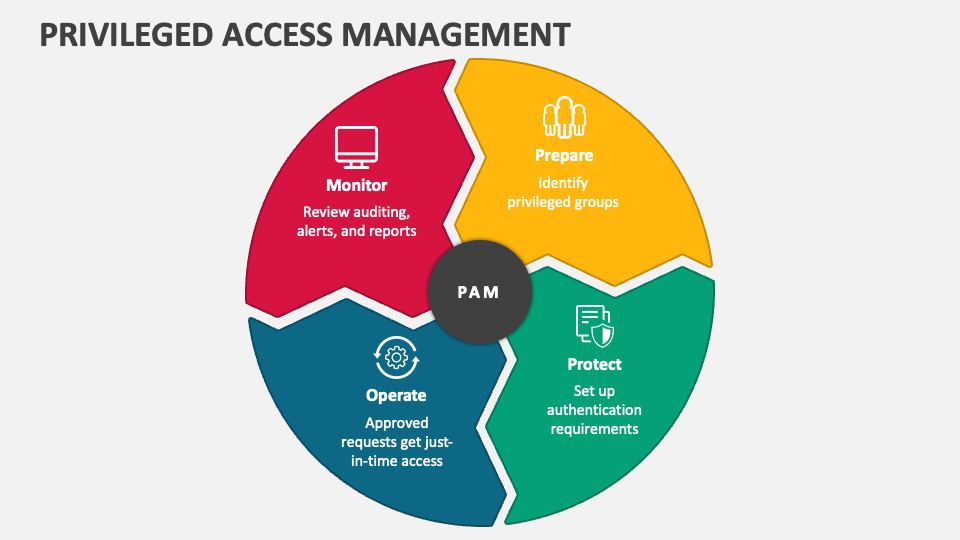
Privileged Access Management PowerPoint and Google Slides Template
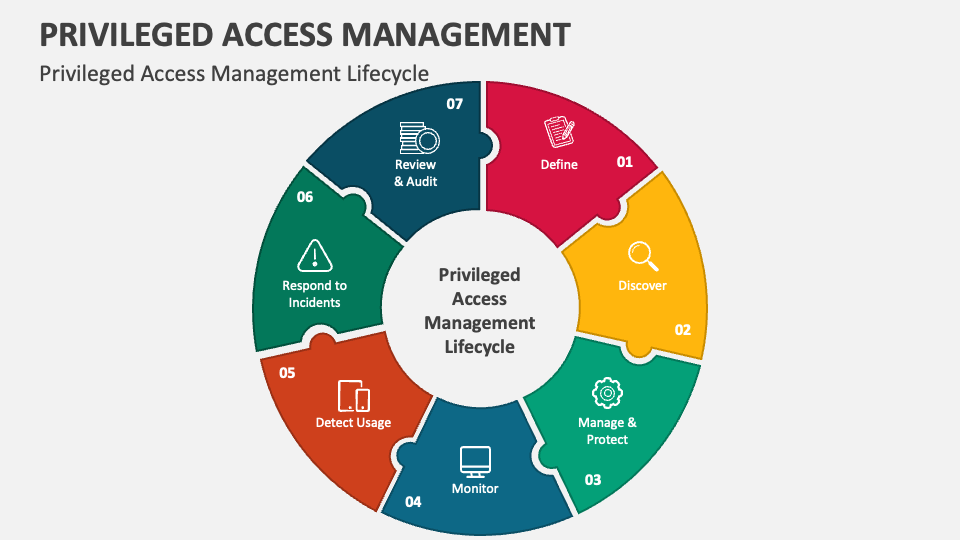
Privileged Access Management PowerPoint and Google Slides Template
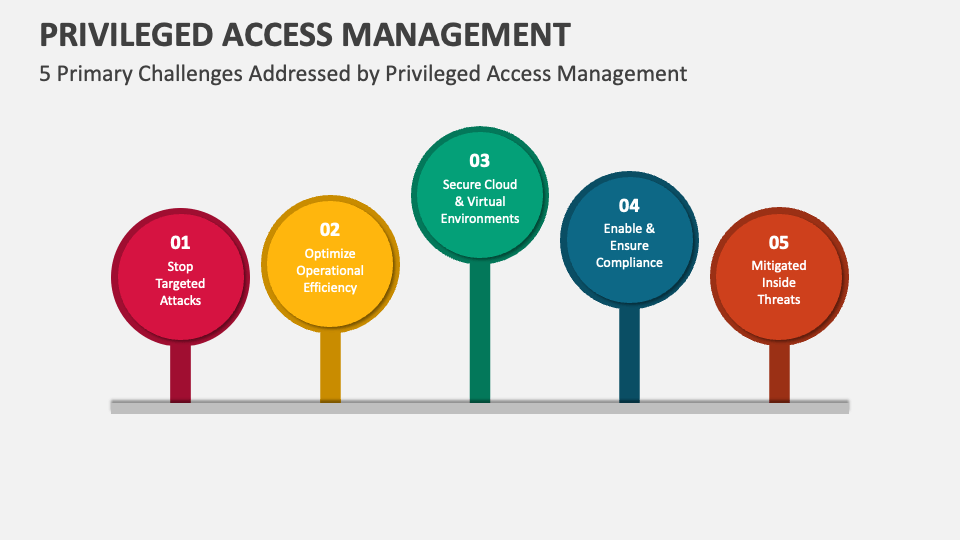
Privileged Access Management PowerPoint and Google Slides Template

Access Management Policy Template Printable Word Searches
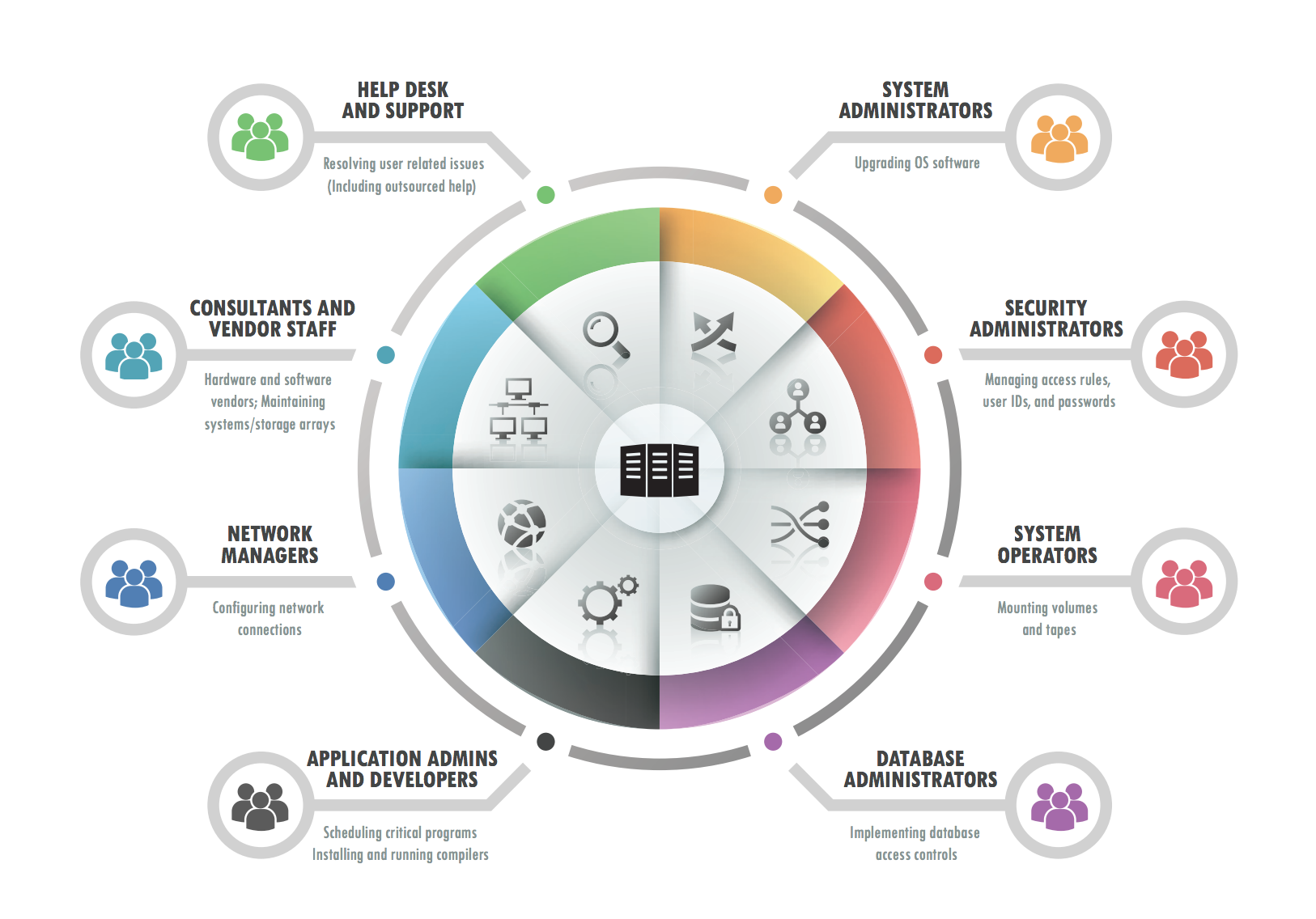
What is Privileged Access Management? Core Security
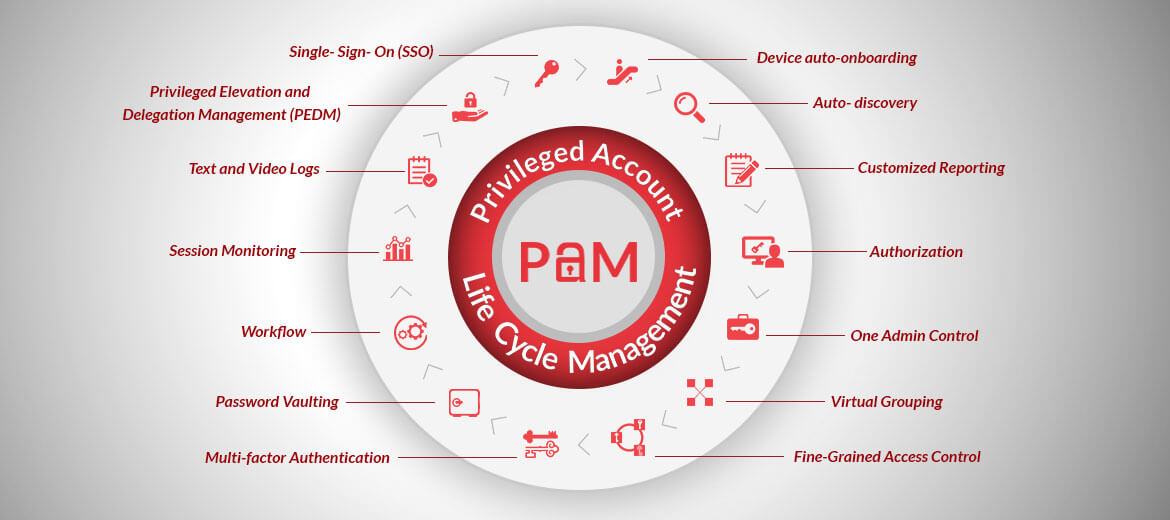
Privileged Access Management wearedots com

Privileged access management the network gatekeeper

PAM solution Enterprise privileged access management (PAM) tool

What Is Privileged Access Management? Internxt Blog

PAM for Educational Institutions Control Access to your Data
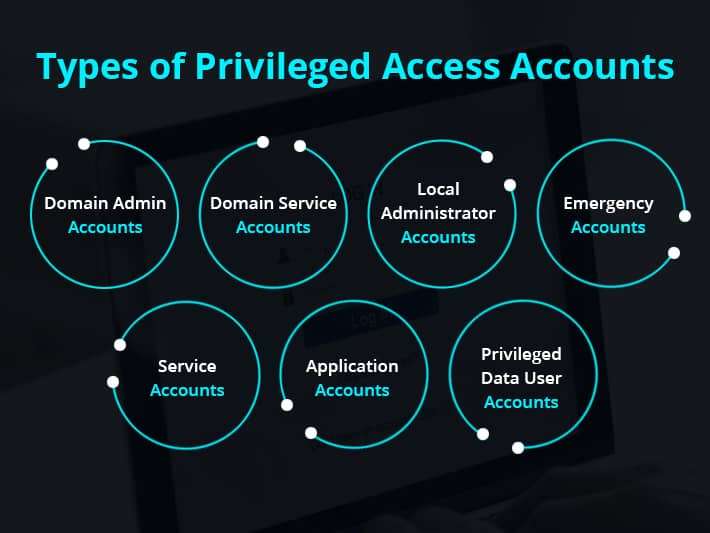
What is Privileged Access Management?
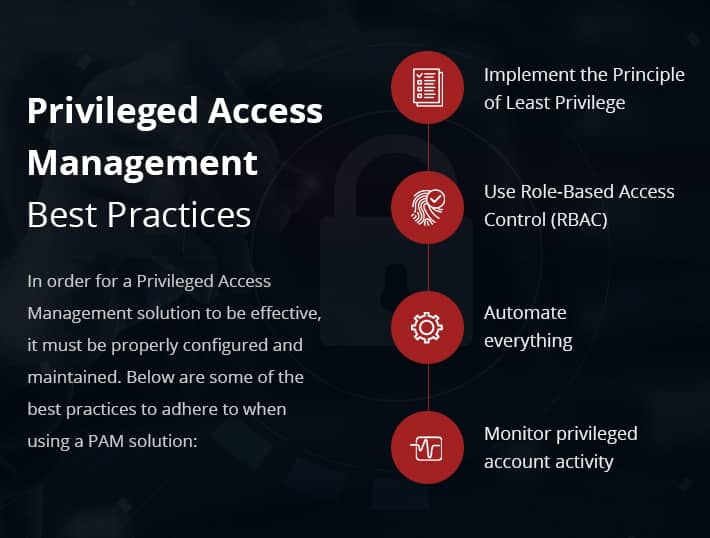
What is Privileged Access Management?

Identity And Access Management Policy Template prntbl

Identity And Access Management Policy Template prntbl

Privileged Access Management in Microsoft 365
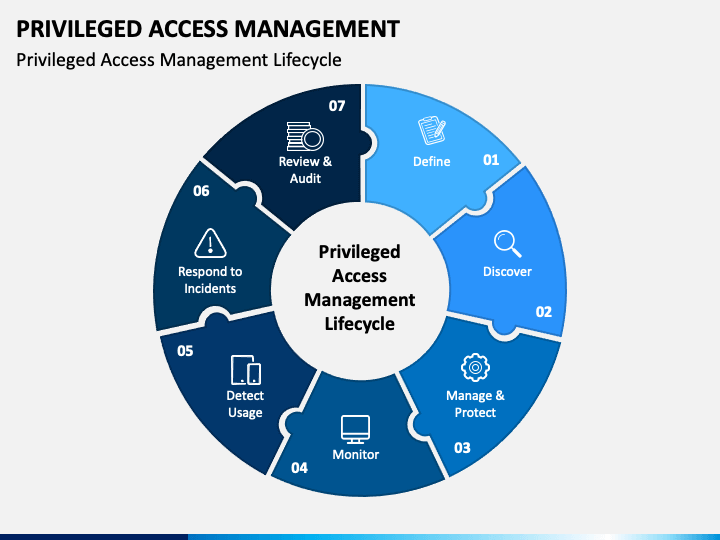
Privileged Access Management PowerPoint and Google Slides Template

What Is a Privileged Access Management Policy? Guidelines and Benefits

What Is a Privileged Access Management Policy? Guidelines and Benefits
User Access Management Policy Template Banking and Fintech Policies
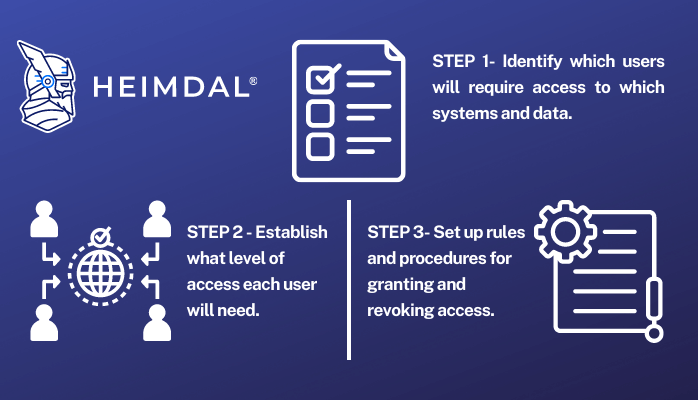
What Is a Privileged Access Management (PAM) Policy?
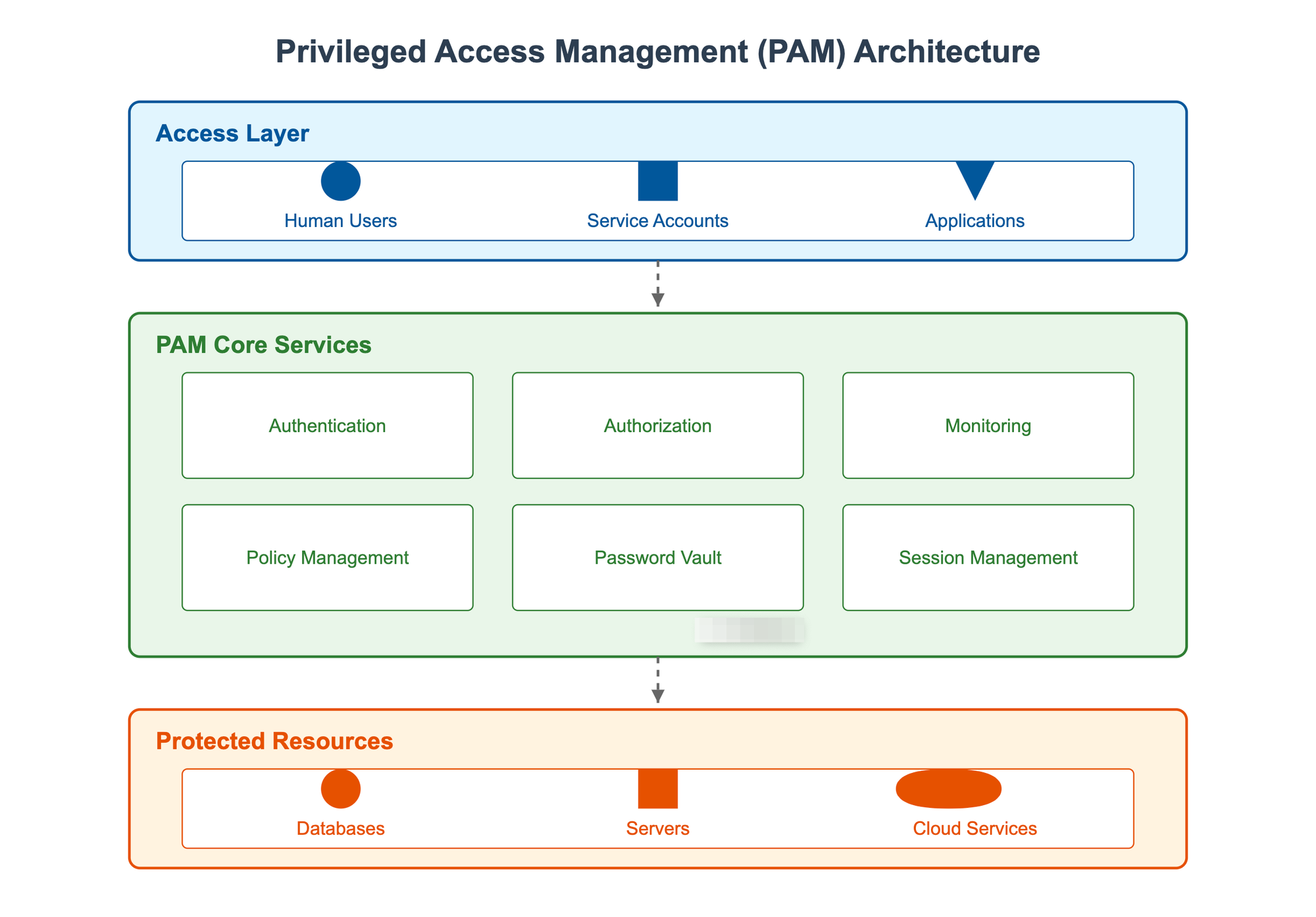
Privileged Access Management (PAM) Guide GuptaDeepak
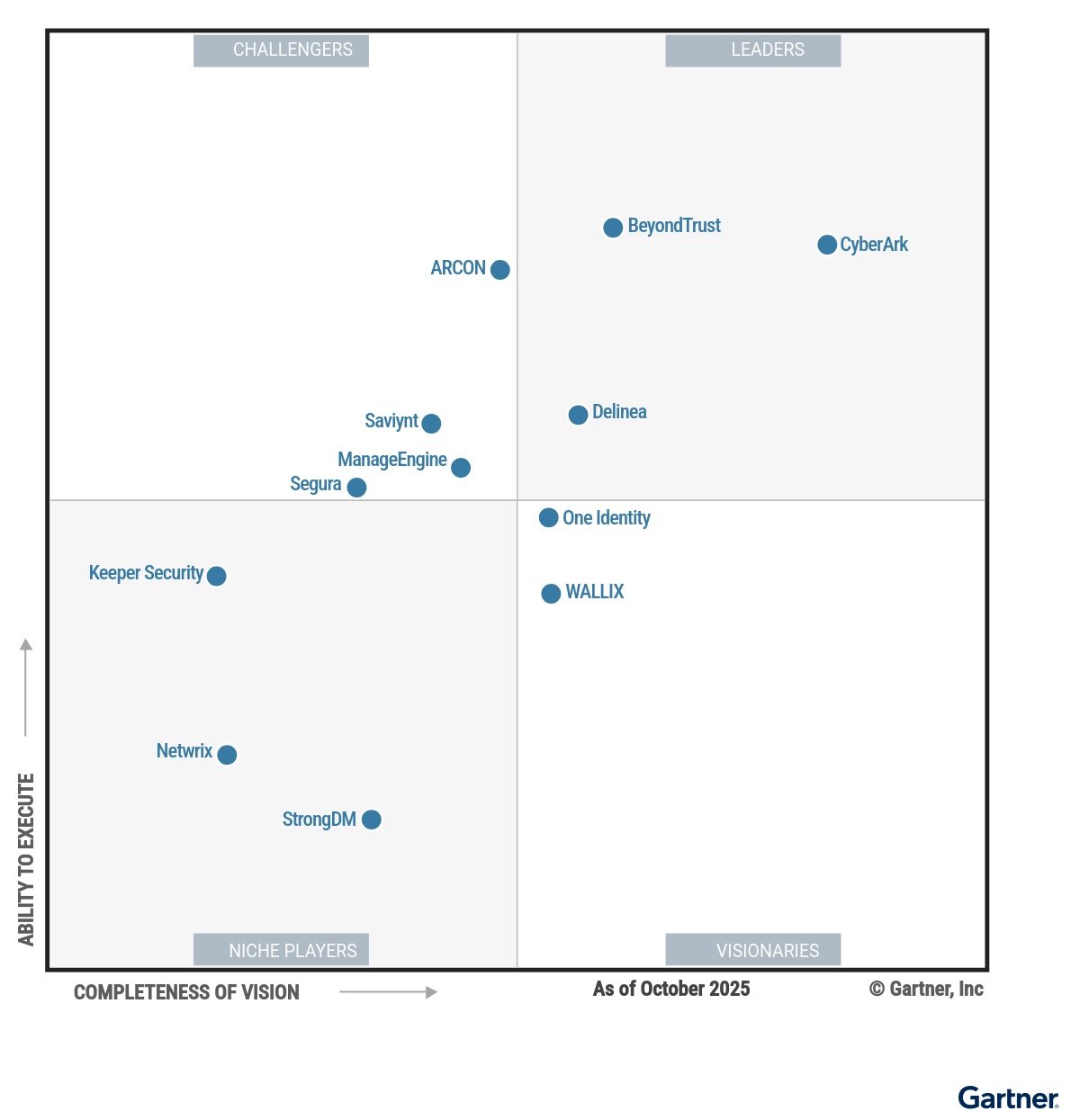
ManageEngine named a Challenger in the 2025 Gartner® Magic Quadrant

Privileged Access Management: Why and How to Prioritize It
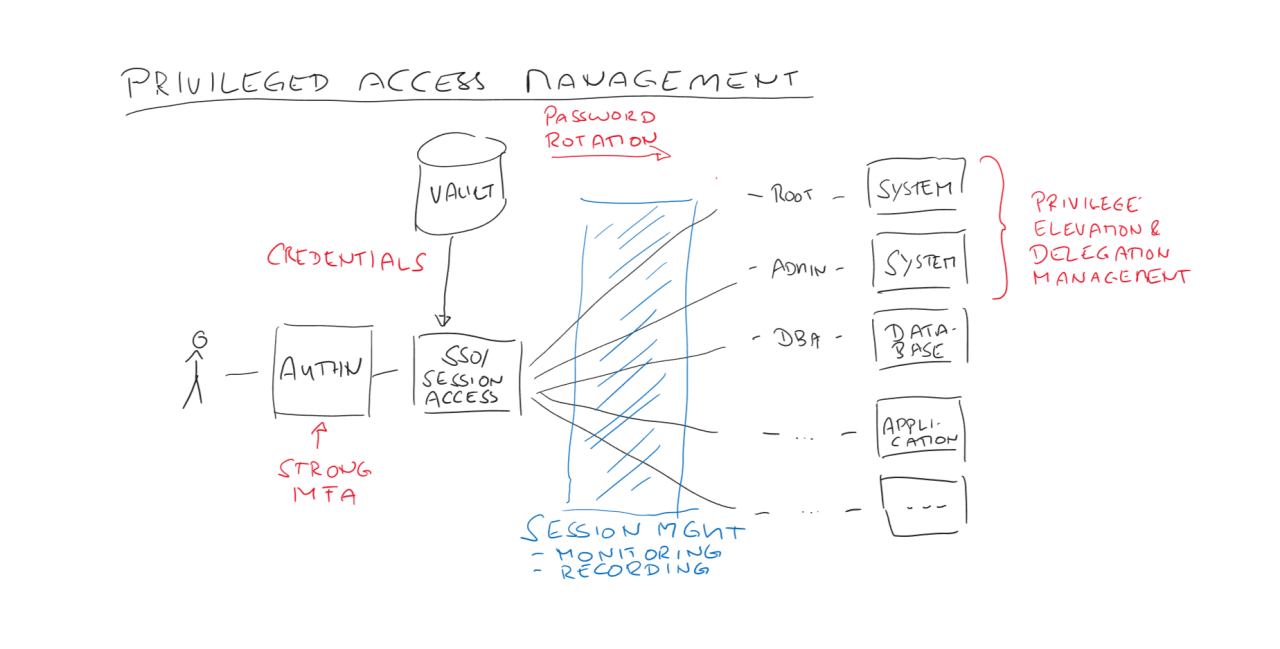
IAM Explained: PAM Privileged Access Management
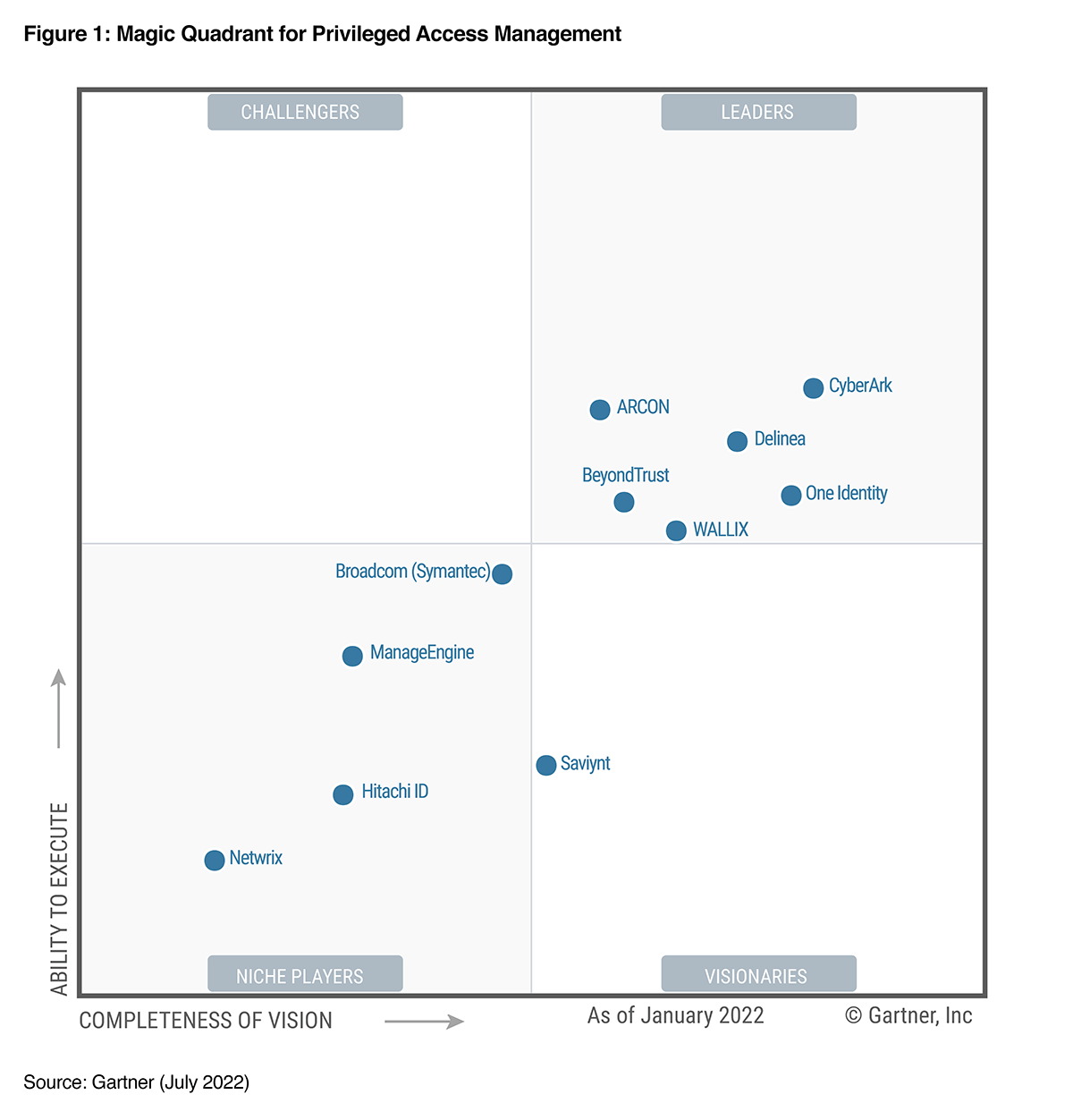
Gartner 2022 Magic Quadrant for Privileged Access Management(PAM

A Complete Guide to Privileged Access Management (PAM) Cloud Data
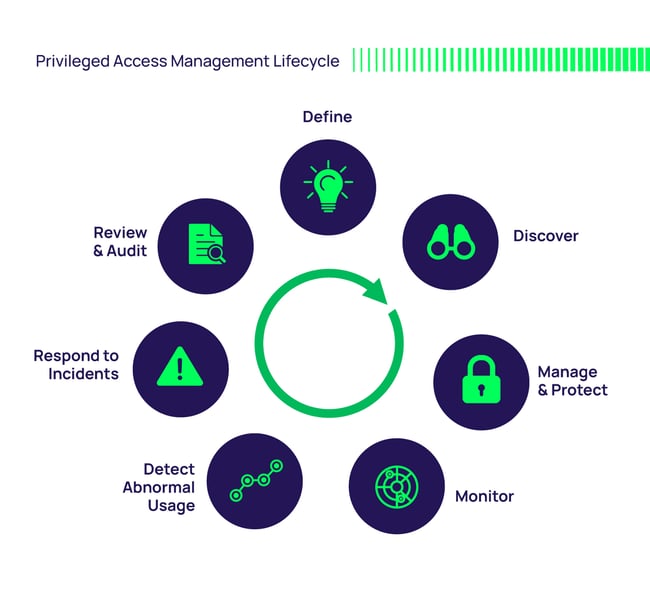
What is Privileged Account Management? Delinea

Privileged Access Management Policy: Enhancing Security and Control PPT

Learn Privileged Access Management best practices

Privileged Access Management Solutions Market Report 2025

Policy Identity and Access Management template en Identity and Access
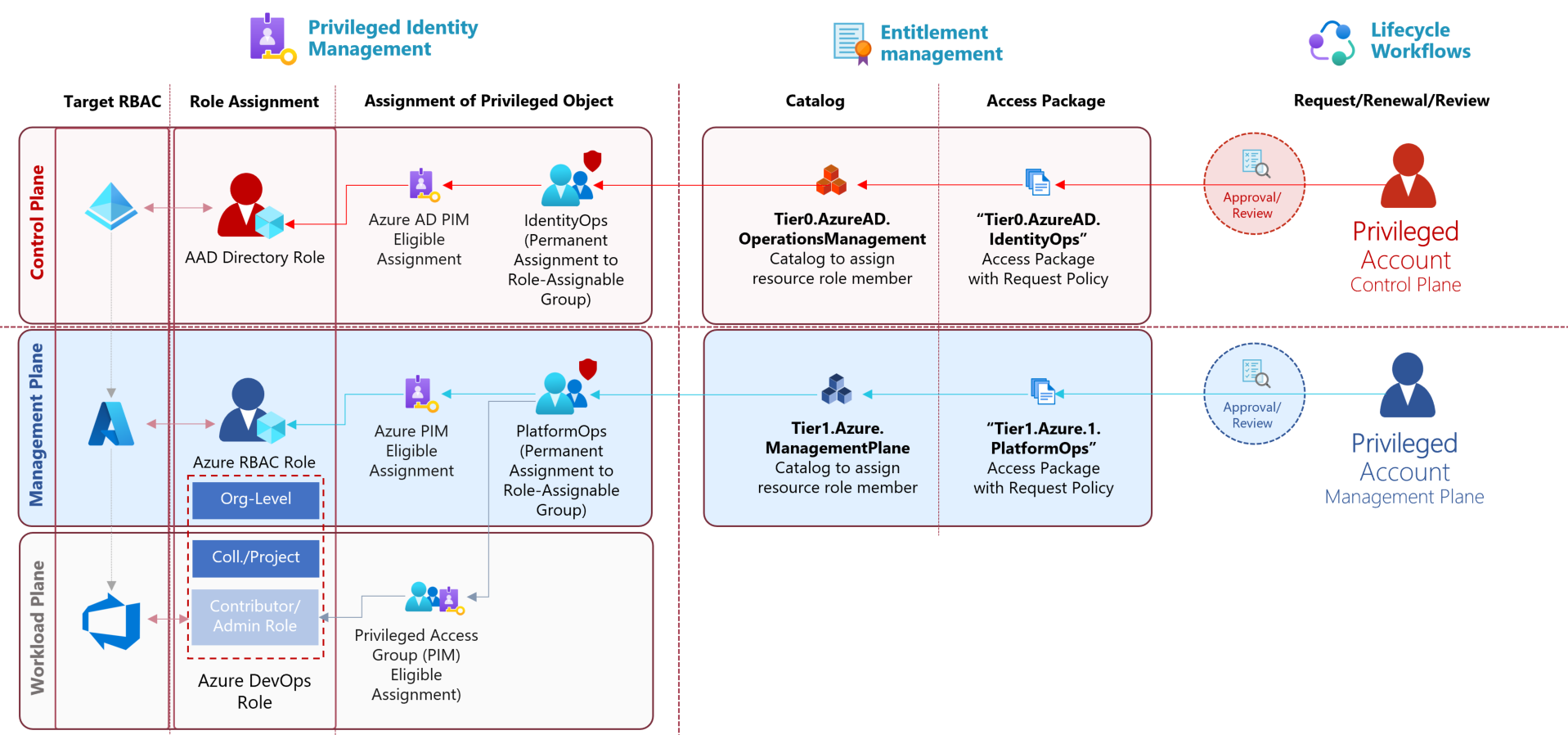
Securing privileged user access with Azure AD Conditional Access and

Access Management: A Comprehensive Guide Zluri

Identity and Access Management Policy Information Security at
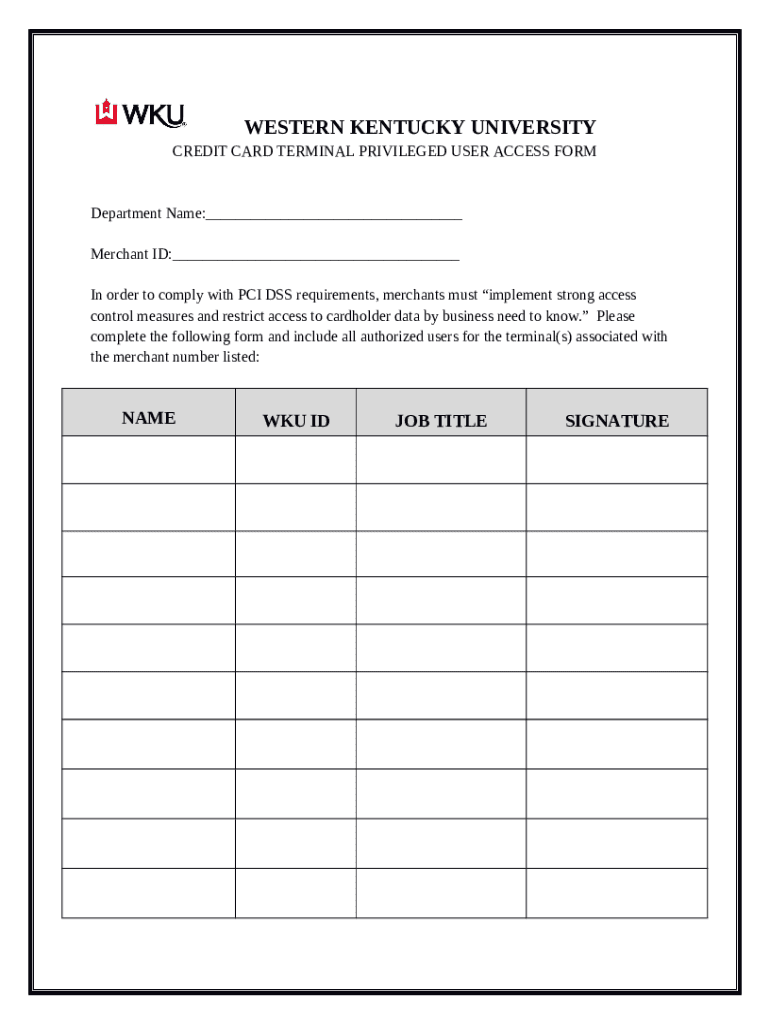
Privileged User Access Doc Template pdfFiller

Third Party Access Management: All You Need To Know Zluri
Soluzione di gestione delle sessioni privilegiate (PSM) miniOrange
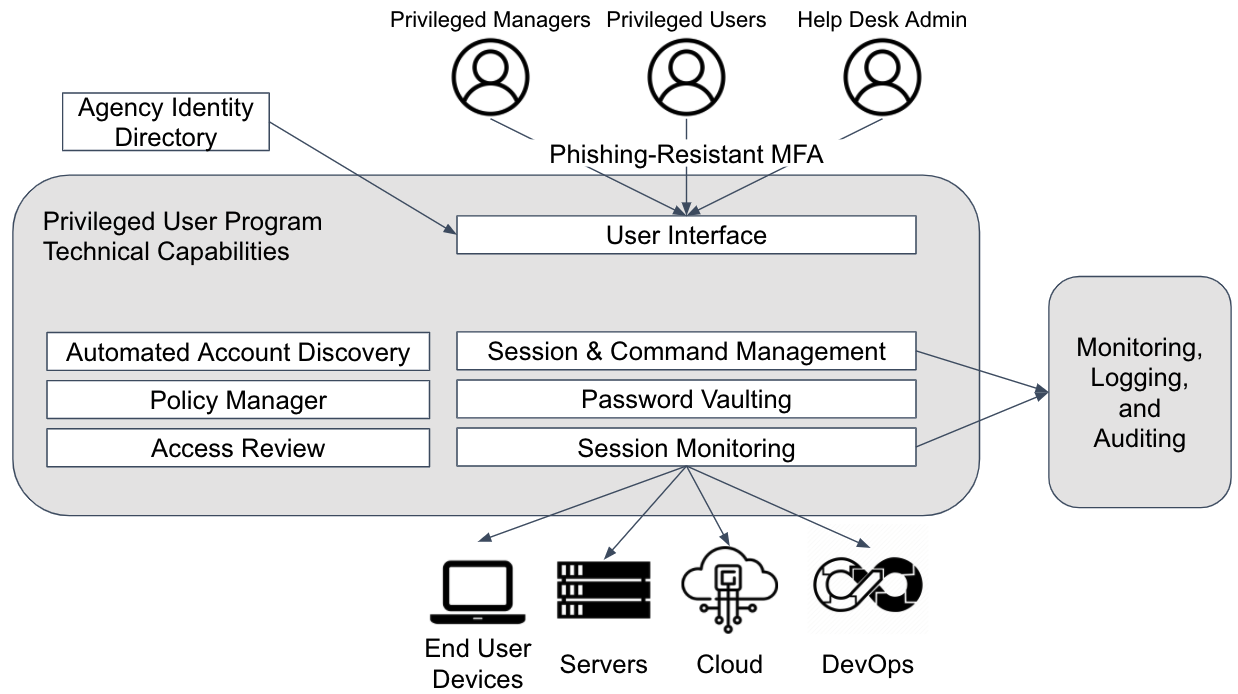
Privileged Identity Playbook

ISO 27001 Access Control Policy: A Complete Guide Template
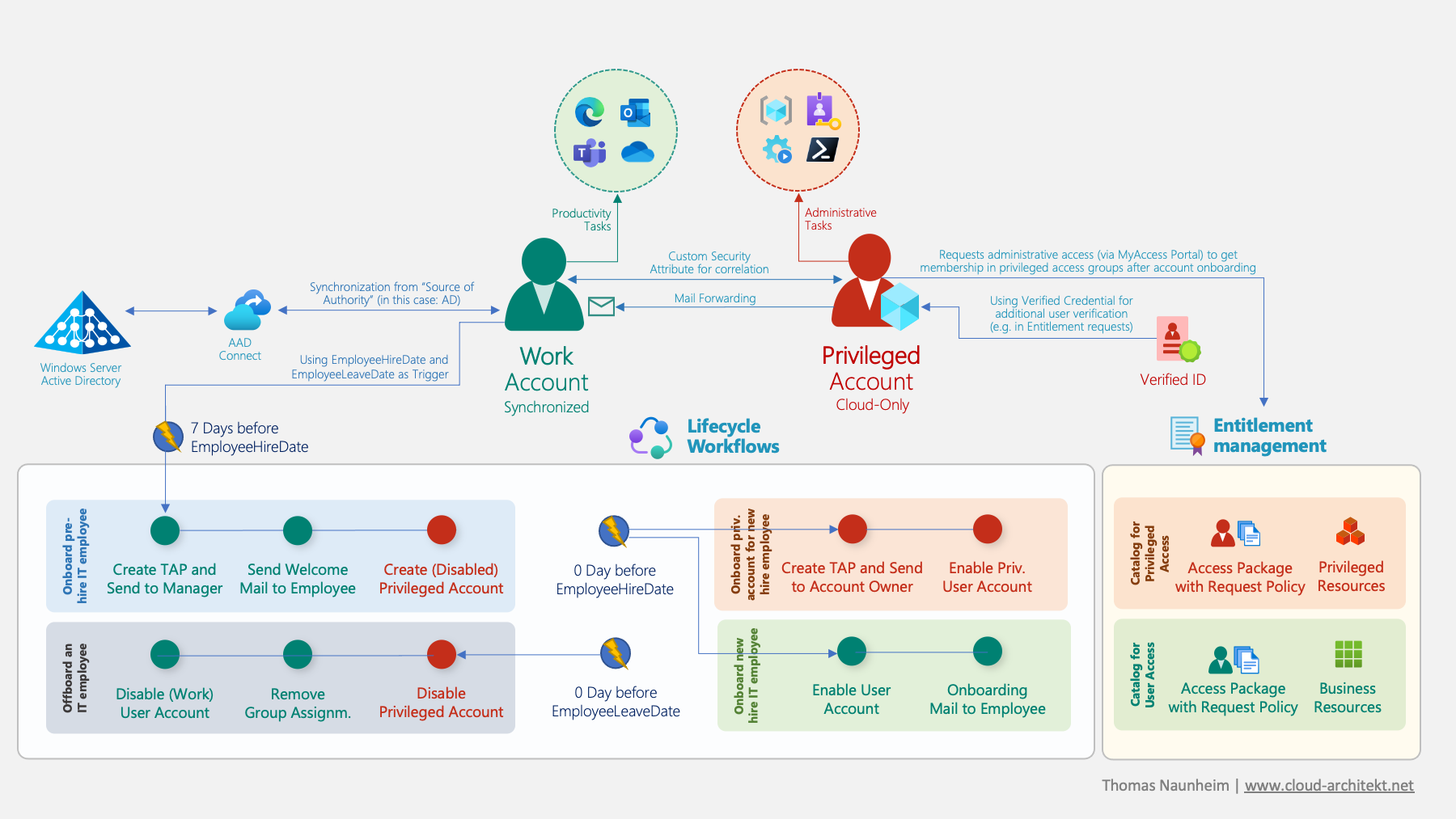
Automated Lifecycle Workflows for Privileged Identities with Azure AD

IAM SSO

ISO 27001 Control 8 2: Privileged Access Rights Guide

ISO 27001 Control 8 2: Privileged Access Rights Guide
PAM Implementation Guide for Better Cyber Security

Understanding the CyberArk Privilege Cloud Shared Responsibility Model