Phishing Email Templates Github
Here are some of the images for Phishing Email Templates Github that we found in our website database.

GitHub dsktop/Phishing Templates: Banks Chat

GitHub LinkSec/phishing templates: Over 50 of The Most Deceptive

GitHub LinkSec/phishing templates: Over 50 of The Most Deceptive

GitHub Void Cipher/Phishing Email Generator: 📧 This tool generates
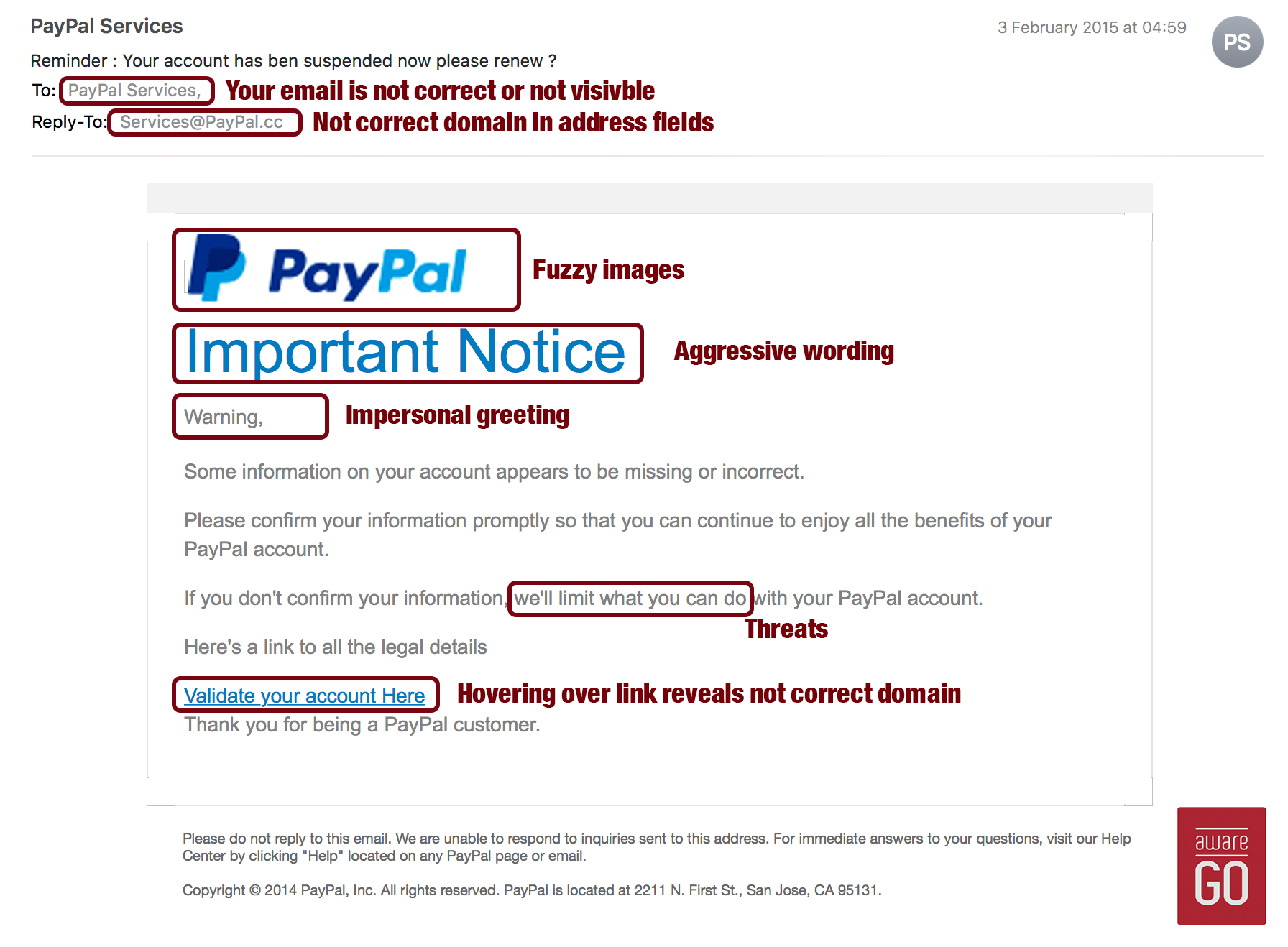
Phishing Email Templates Github
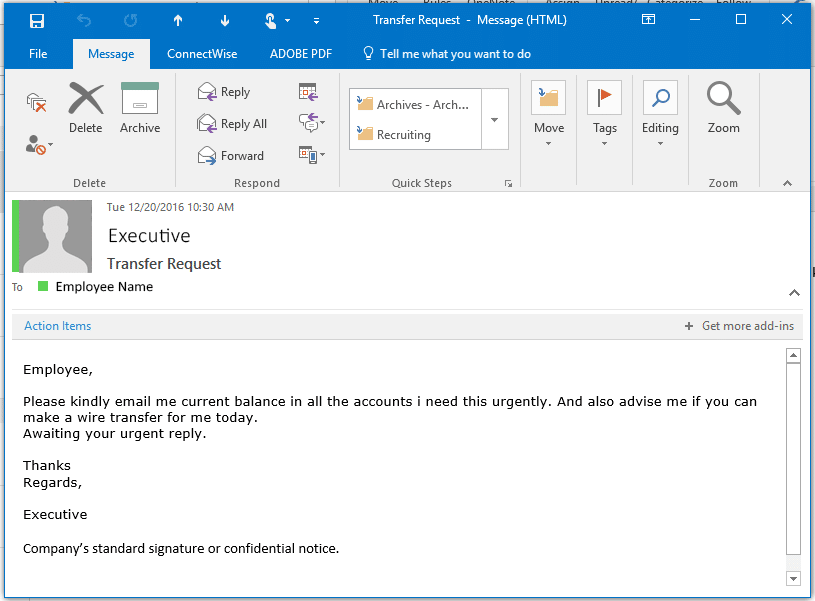
Phishing Email Templates Github

python phishing url detection/templates/index html at master · sannjayy

Phishing Email Templates Github
.jpg)
Phishing Email Templates Github

GitHub sathvikareddy11/Phishing Email Detector
GitHub Aarya1808/Phishing Attack Simulation: This repository contains
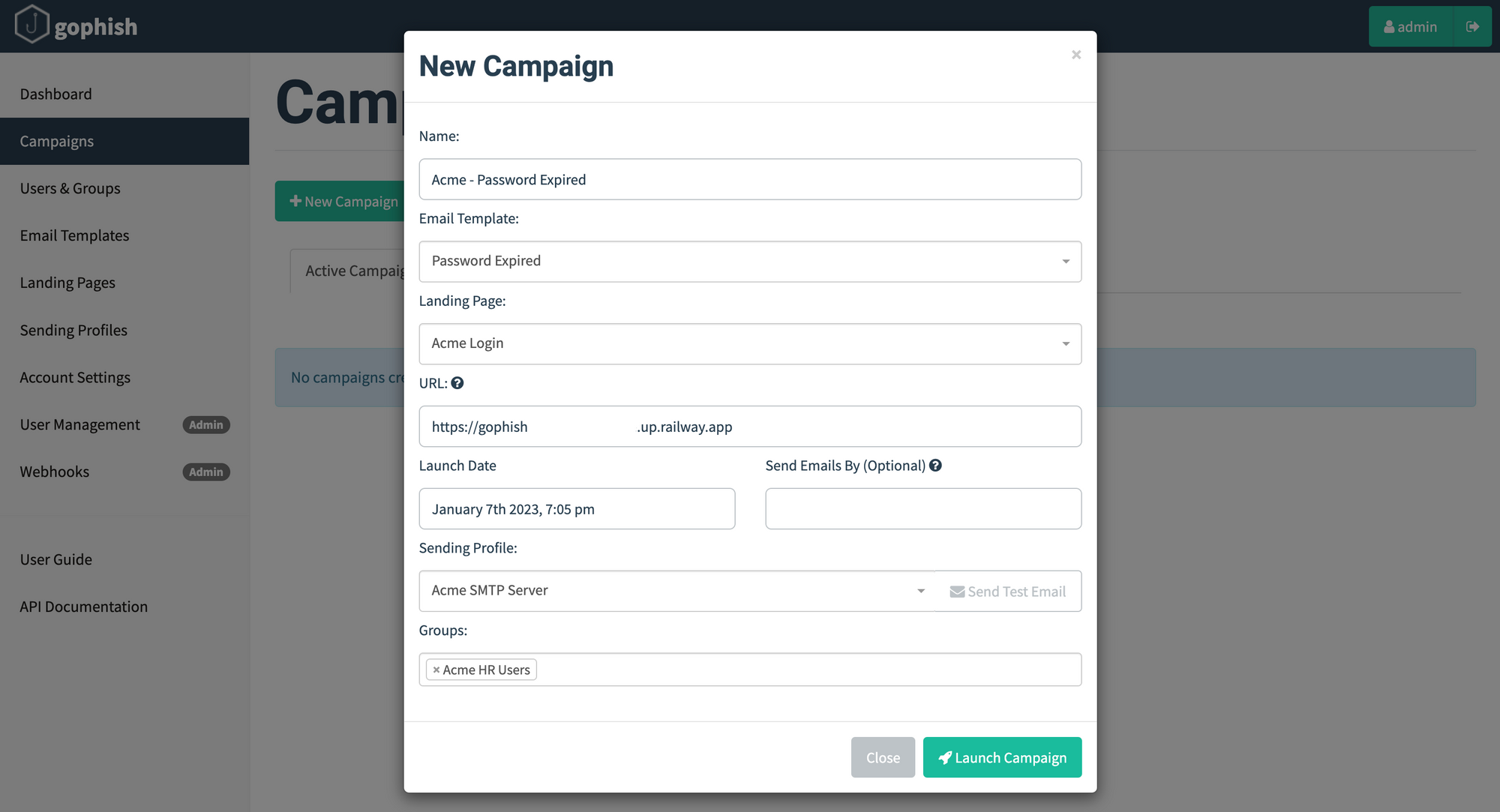
GitHub Aarya1808/Phishing Attack Simulation: This repository contains

Github Phishing Email Example Hook Security

Github Phishing Email Example Hook Security

Phishing Email Templates Phishing Awareness Email Template Use Phishing

Phishing on GitHub: A Sophisticated Attack Leveraging Brand Trust

Phishing on GitHub: A Sophisticated Attack Leveraging Brand Trust
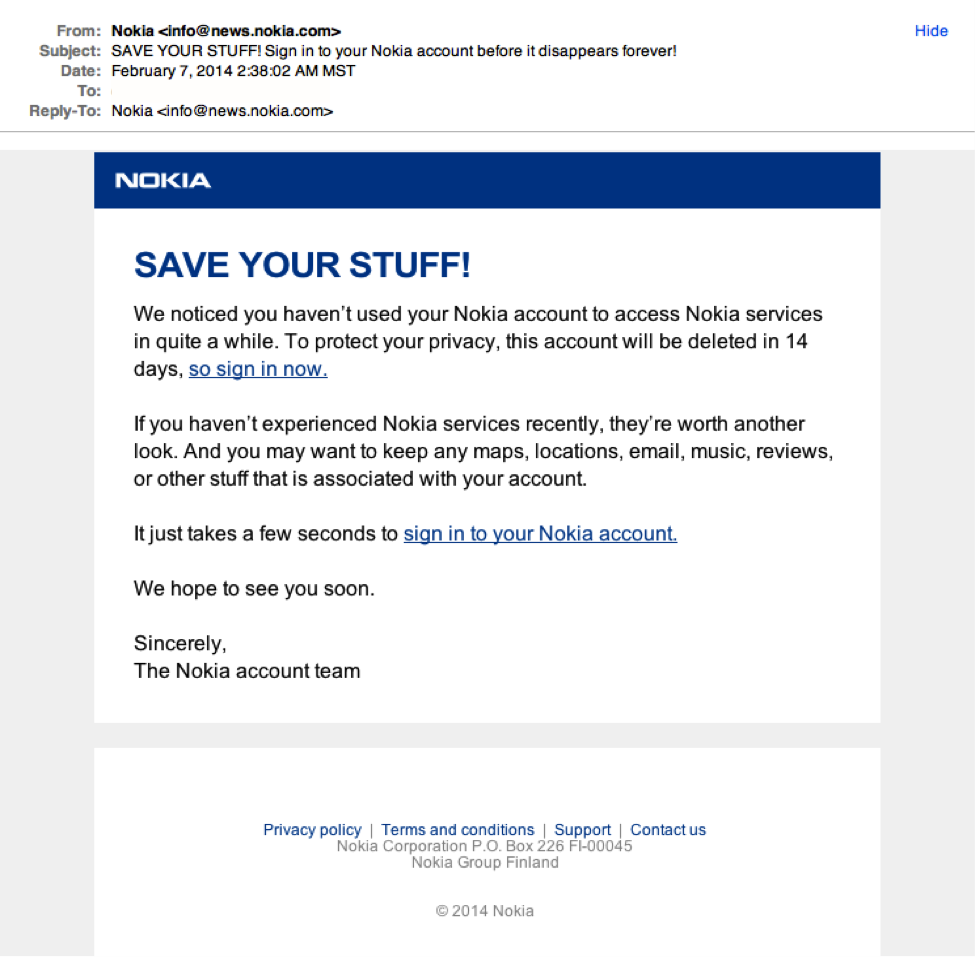
Sample Phishing Email Templates

Phishing Email Templates Printable Word Searches
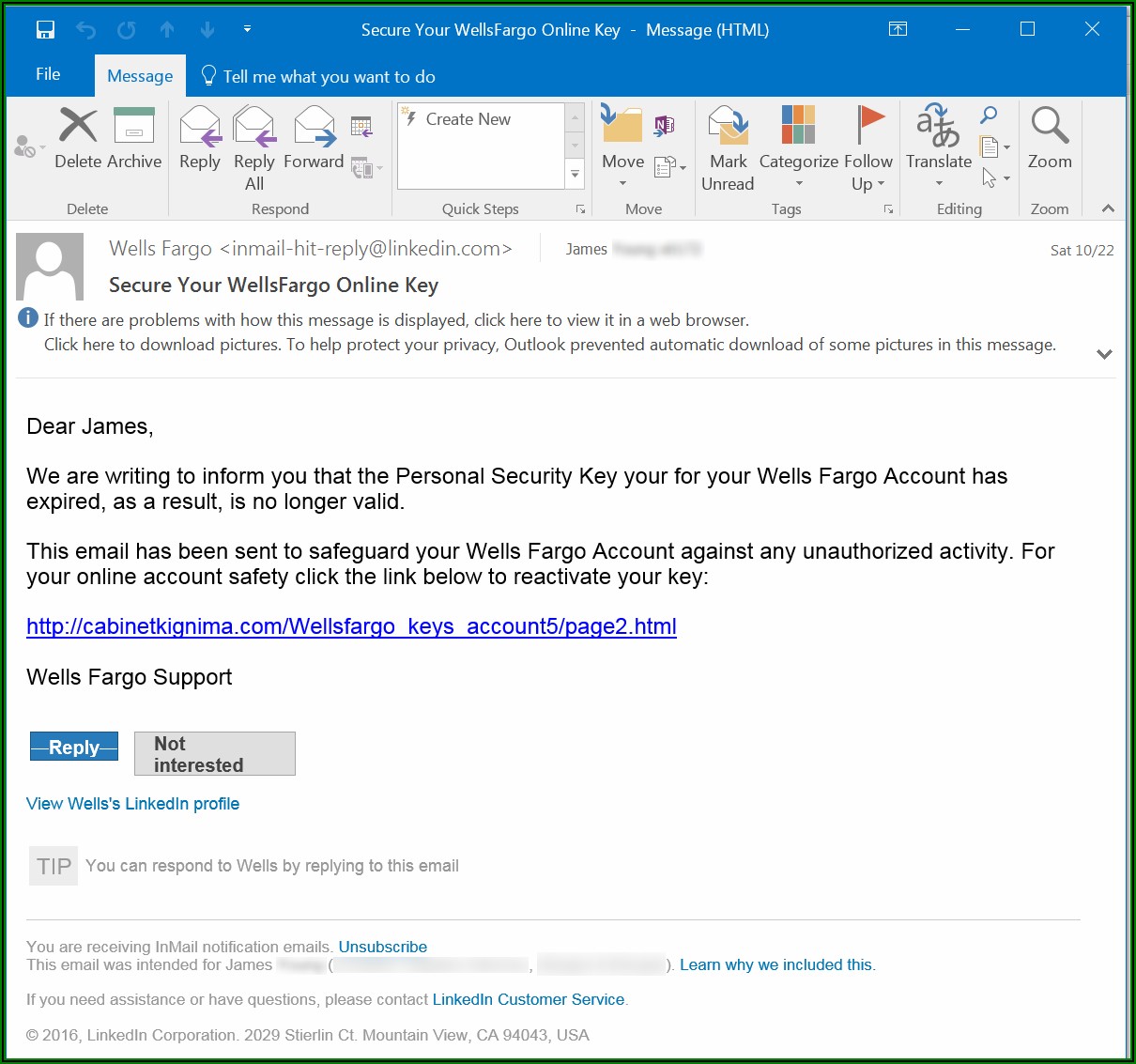
Phishing Test Email Templates Template 2 : Resume Examples #Bw9jQKz327
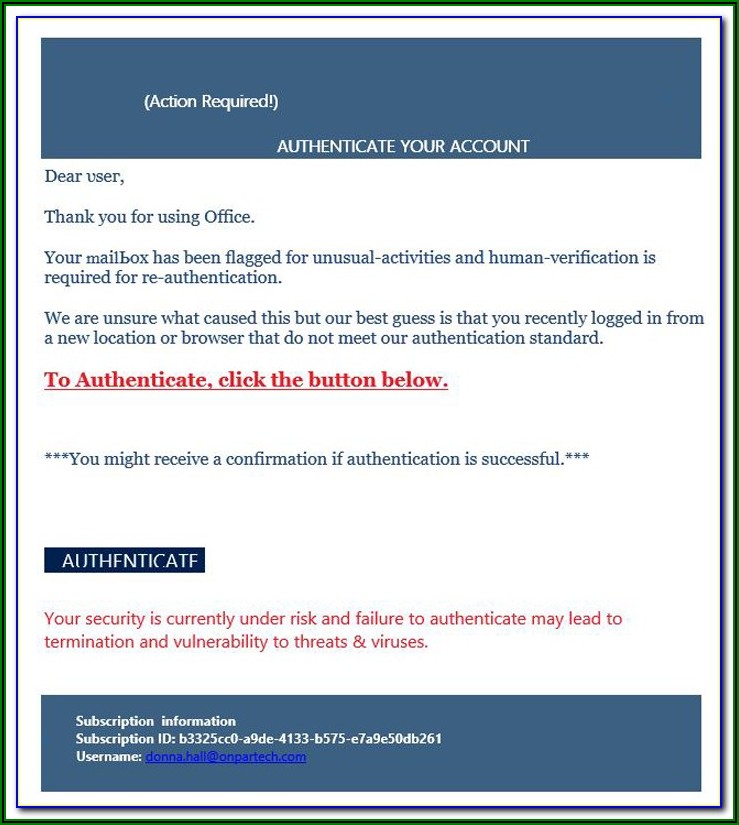
Phishing Test Email Templates Template 2 : Resume Examples #Bw9jQKz327
.png)
The Trickiest Phishing Email Templates How to Spot Them

GitHub developer compromise sought by novel GoIssue phishing tool SC

Phishing Email Templates

Phishing Email Templates prntbl concejomunicipaldechinu gov co
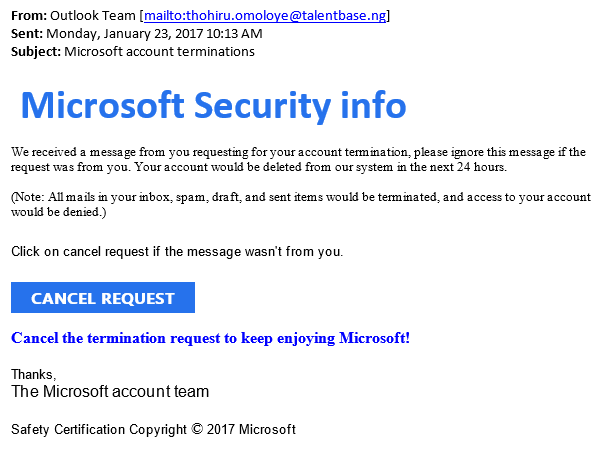
Phishing Email Templates Download prntbl concejomunicipaldechinu gov co

Phishing Email Templates Download prntbl concejomunicipaldechinu gov co
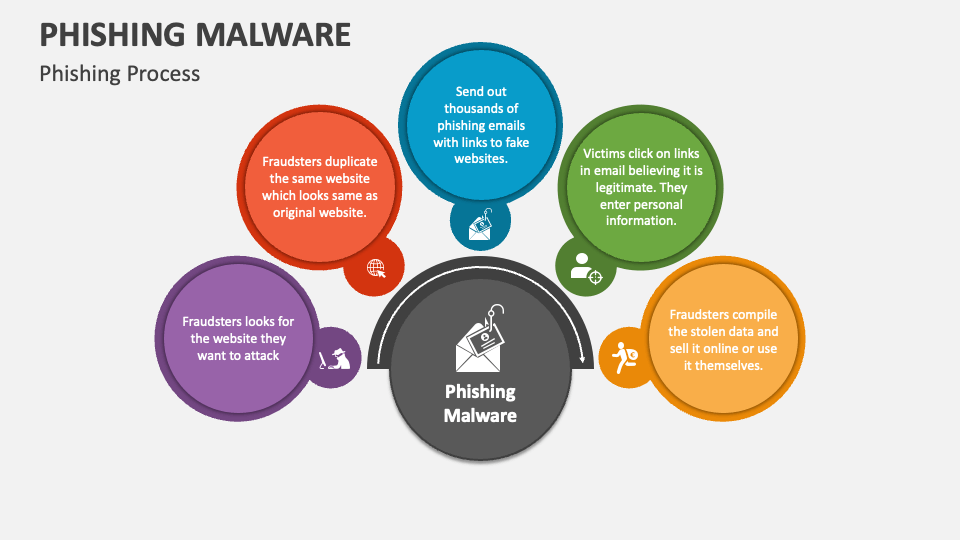
Phishing Email Templates Download prntbl concejomunicipaldechinu gov co
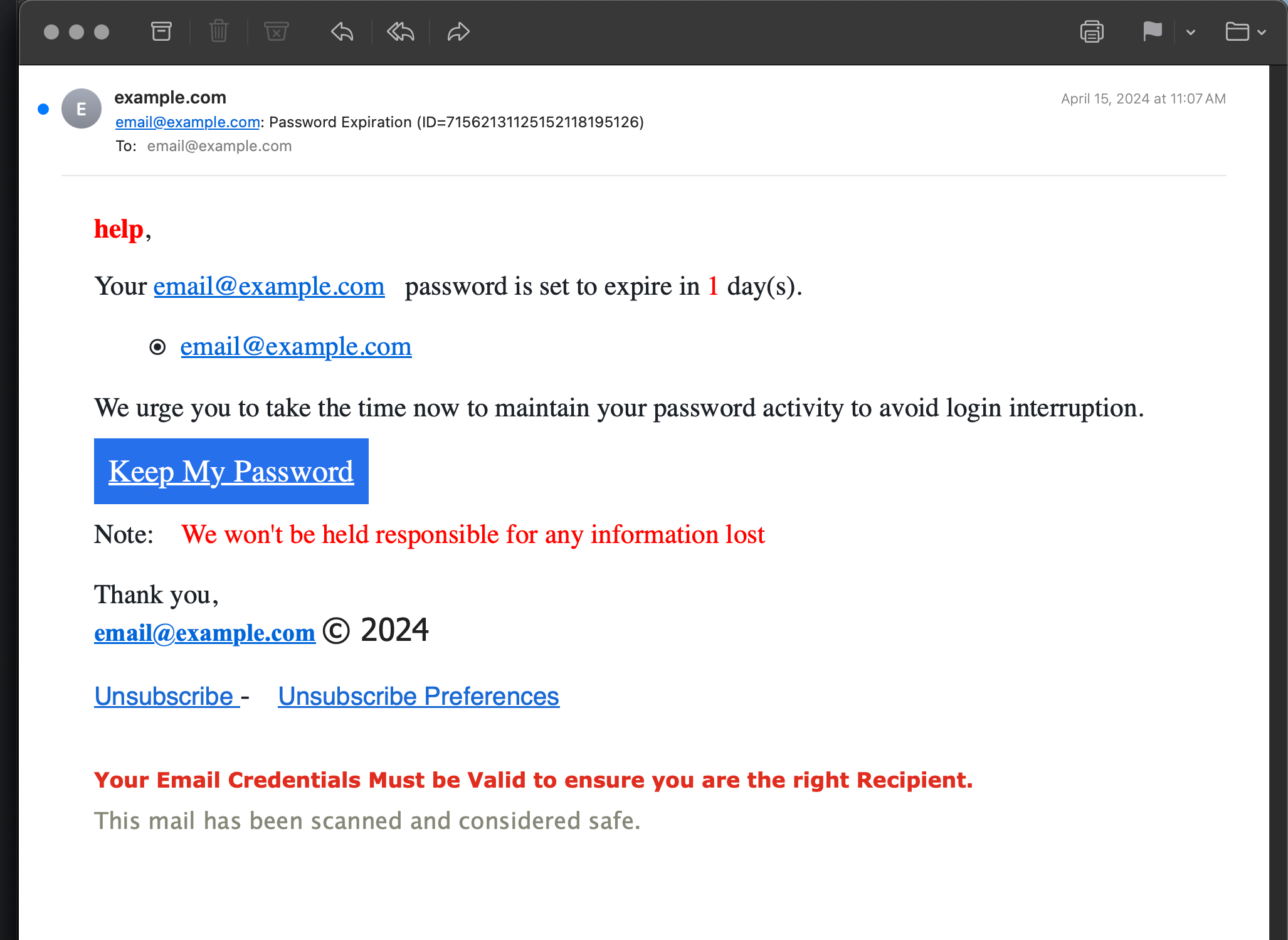
Examples of Email Phishing in 2024 Perishable Press

Free Phishing Templates One Possible Reason Could Be That The Email

Phishing Campaign Templates
Free Phishing Templates

Free Phishing Templates

Free Phishing Templates
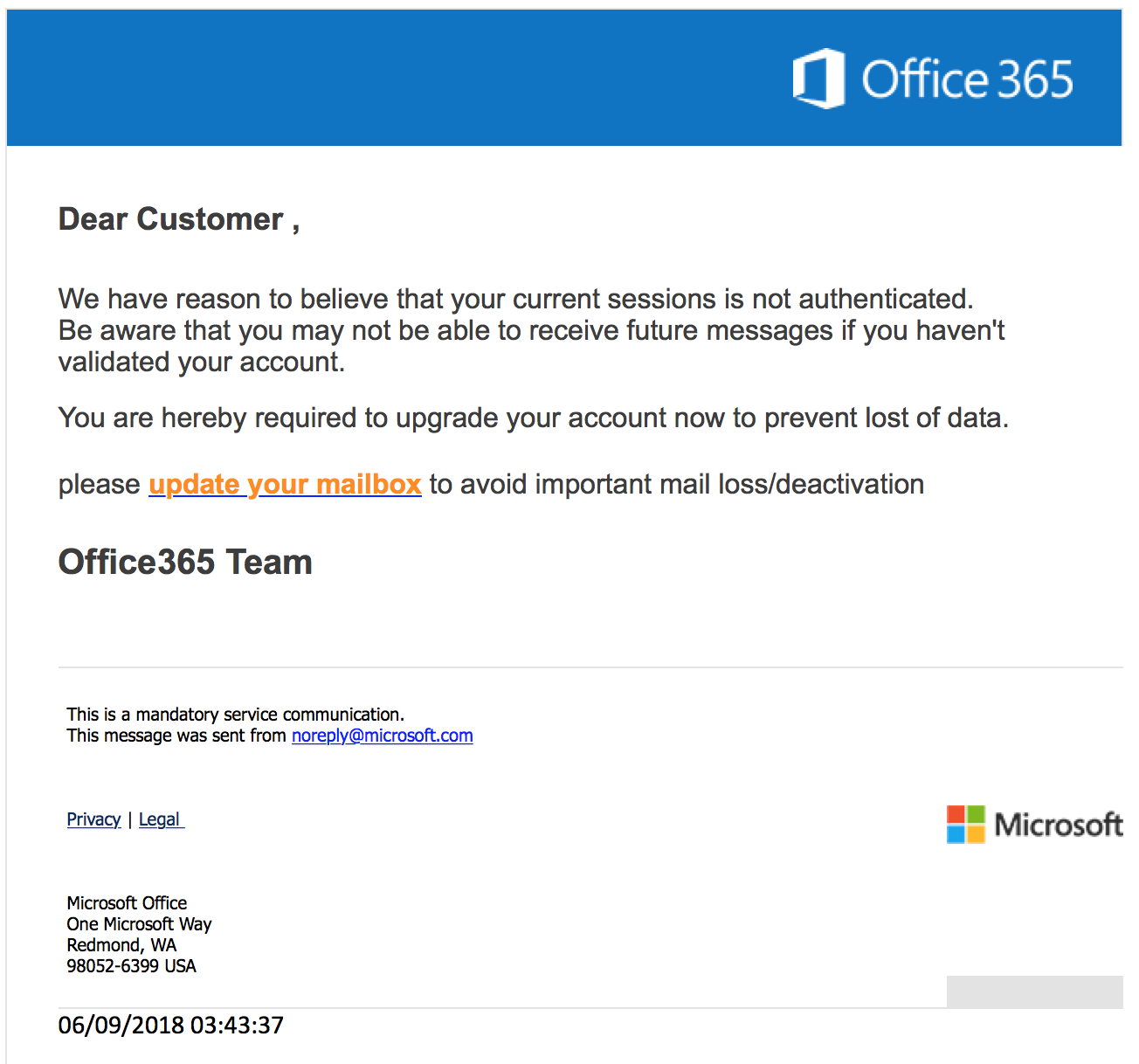
Phishing Email Examples

Phishing Email Template Content Calendar Template
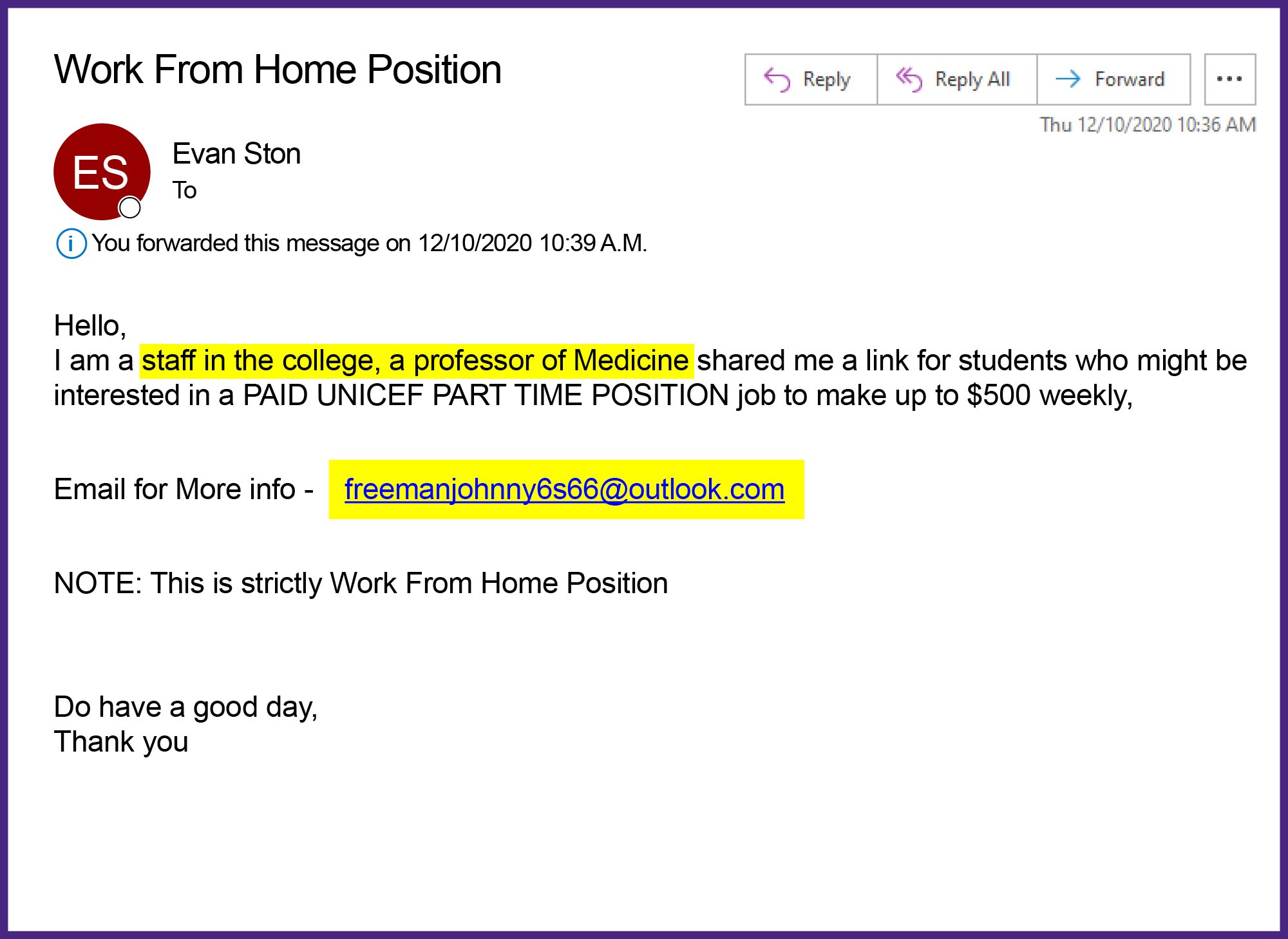
Phishing

Chase Phishing Email Example Hook Security

10 Of The Best Phishing Templates For Calculating Employee Risk UAHX

Top 5 Must Know Phishing Simulation Templates April 2024

How To Create A Phishing Email In 7 Steps

Google Drive Phishing Email Example Hook Security

Top 5 Must Know phishing simulation templates February Edition
Top 5 Must Know Phishing Simulation Templates March 2024 Edition
.png)
Top 5 Must Know Phishing Simulation Templates May 2024
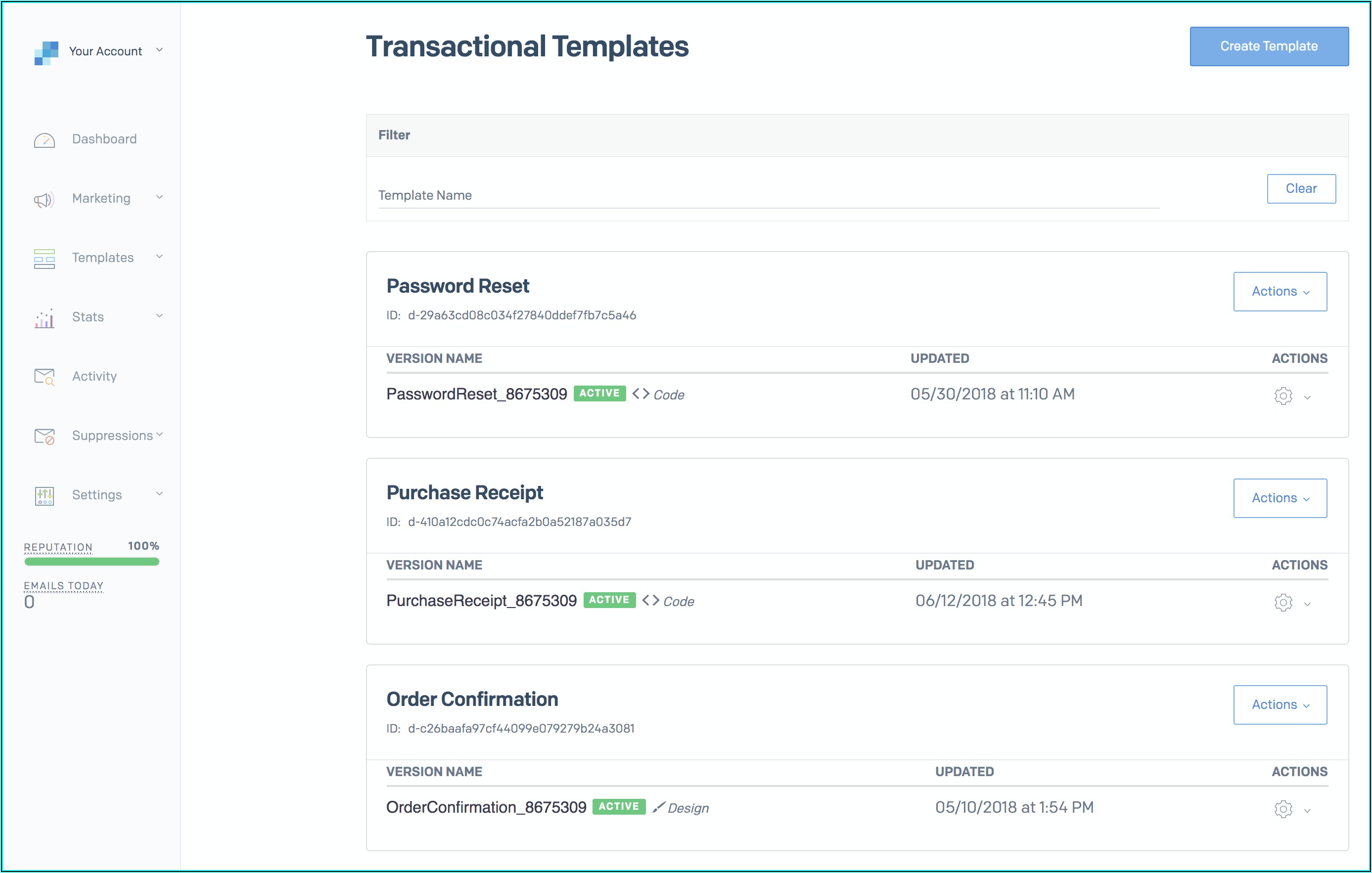
Sendgrid Email Templates Template 1 : Resume Examples #MeVRxEa9Do
Transactional Email Templates Template 1 : Resume Examples #MeVRxQ69Do
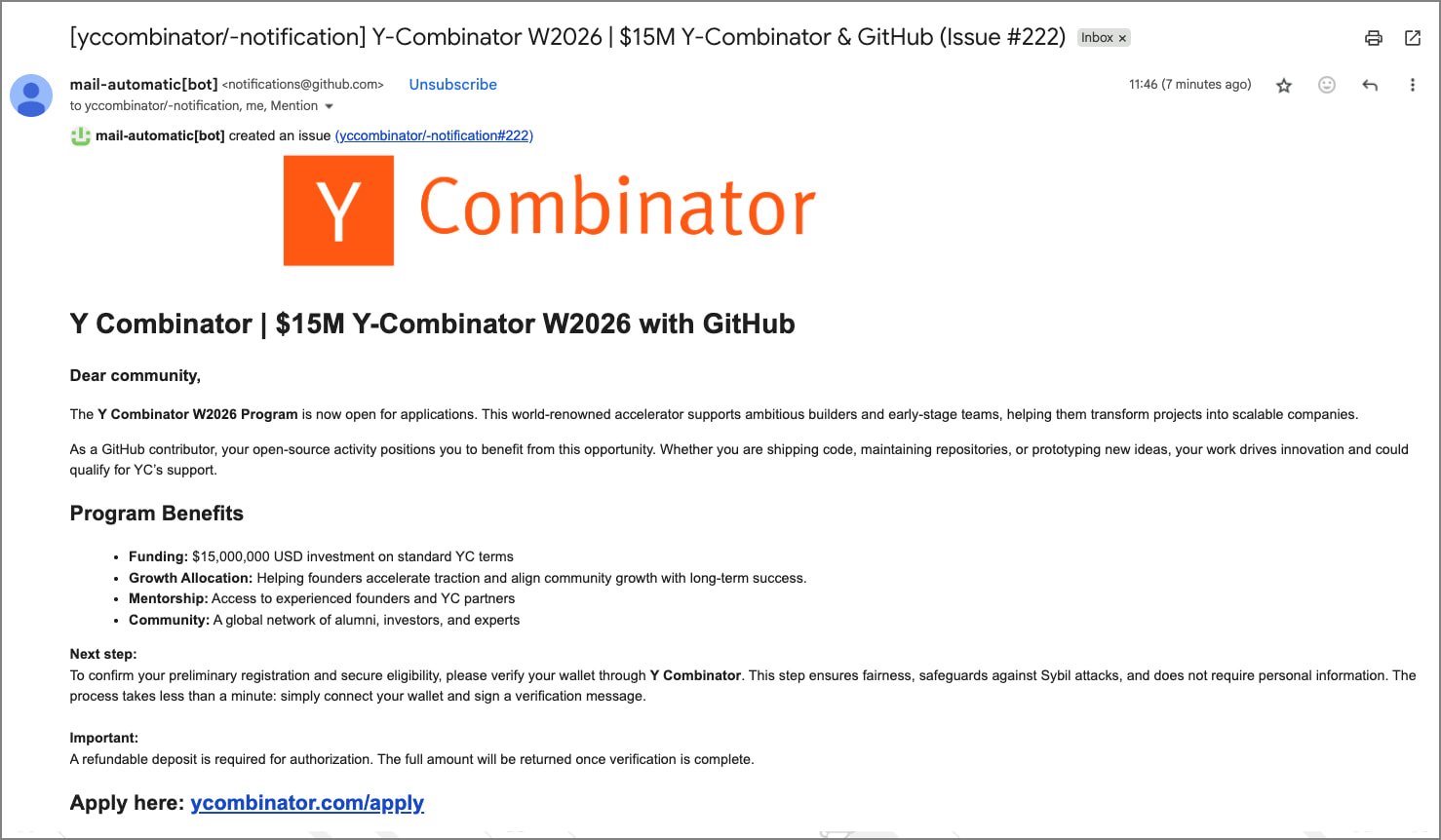
GitHub notifications abused to impersonate Y Combinator for crypto theft

10 Top Tips to Prevent Phishing Attacks Rublon
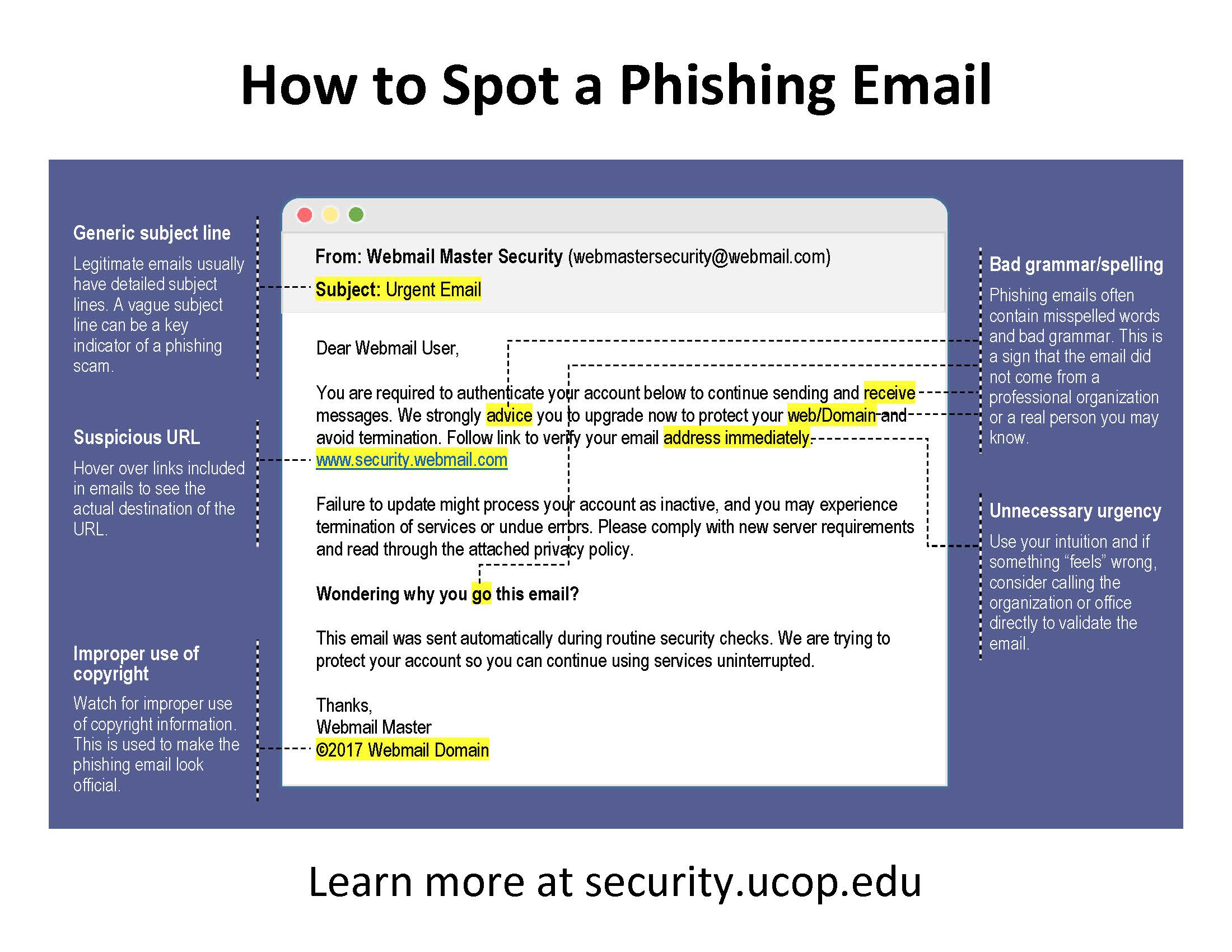
Cybersecurity Awareness Email Templates

攻撃者がフィッシング詐欺に AI や最新のツールを使用、巧妙になるその手口とは Cisco Japan Blog
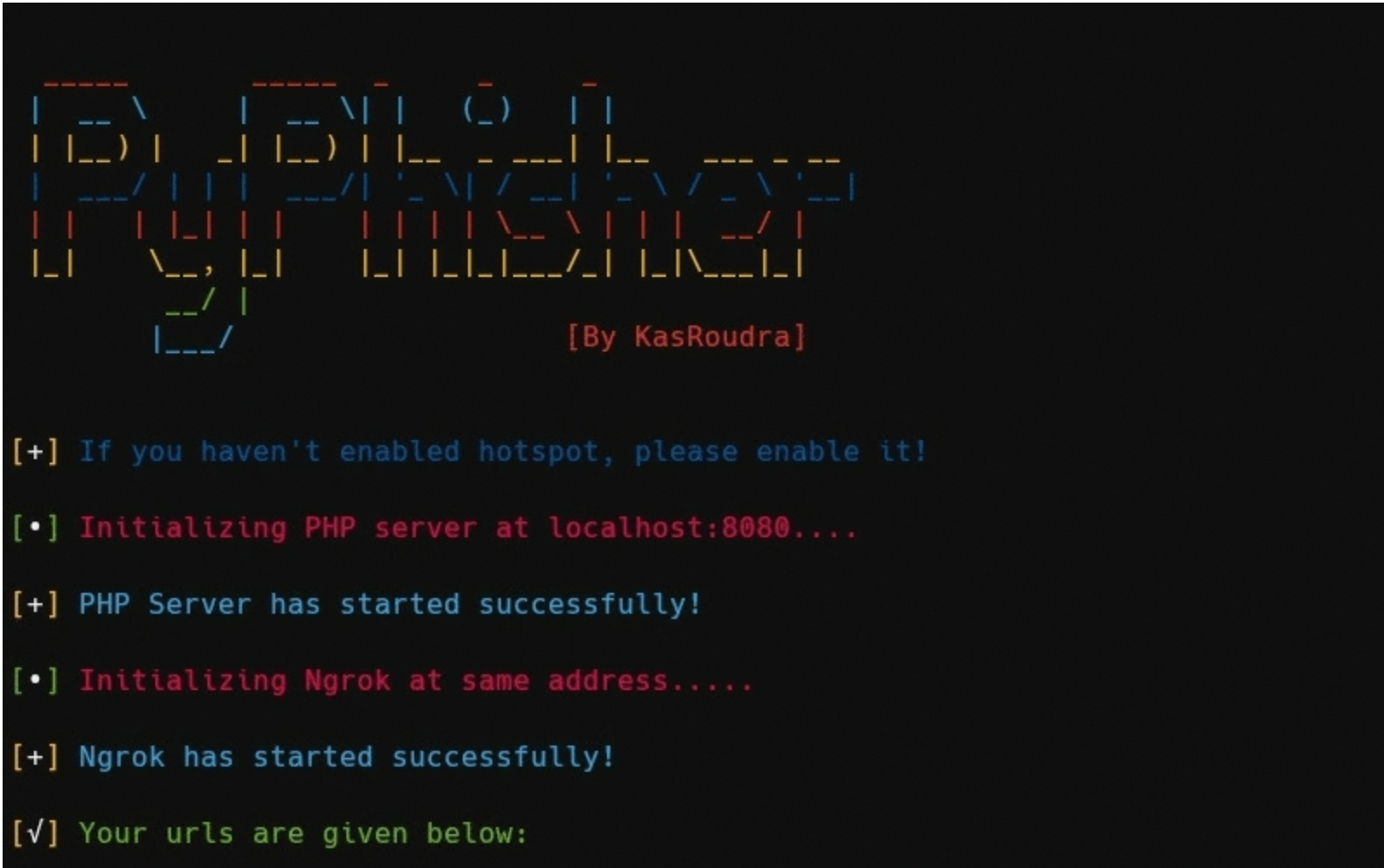
PyPhisher Easy to use phishing tool with 65 website templates

Change Learner Sophistication Levels Phriendly Phishing