Least Privilege Policy Template
Here are some of the images for Least Privilege Policy Template that we found in our website database.
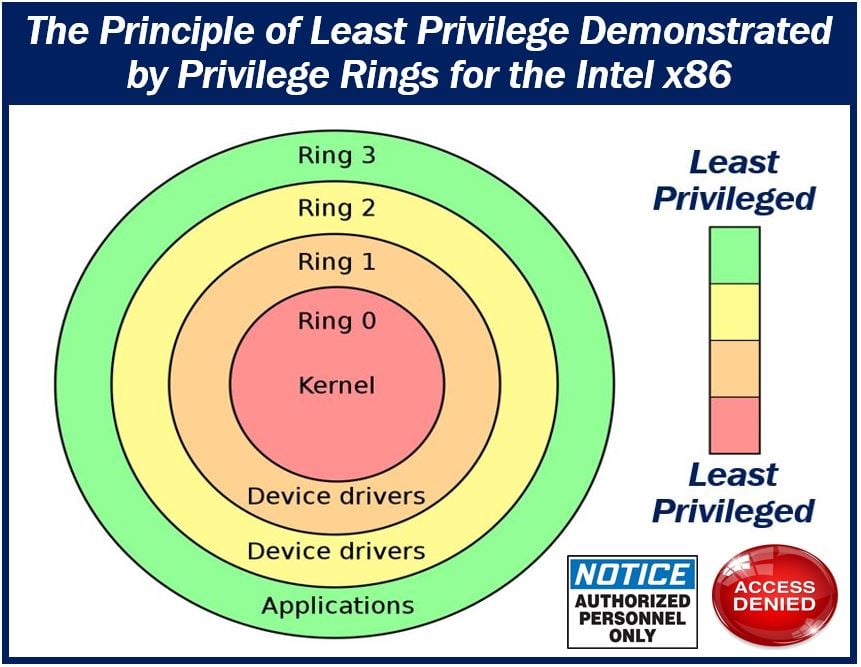
Least Privilege Policy Template

Least Privilege Policy Template

Least Privilege Policy Template
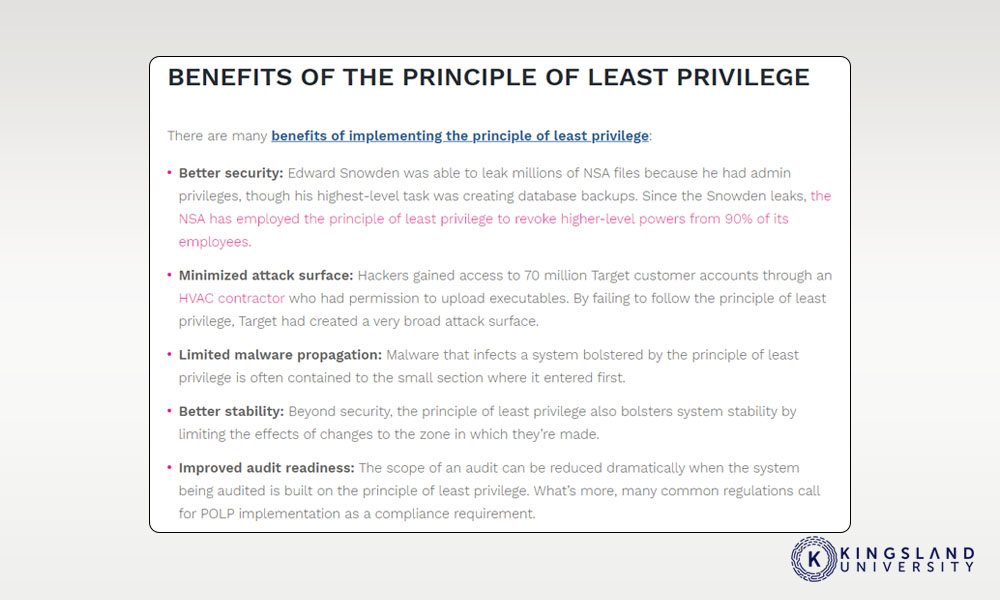
Least Privilege Policy Template

Least Privilege Policy Template

Least Privilege Policy Template prntbl concejomunicipaldechinu gov co

Least Privilege Policy Template prntbl concejomunicipaldechinu gov co

Least Privilege Policy Template prntbl concejomunicipaldechinu gov co
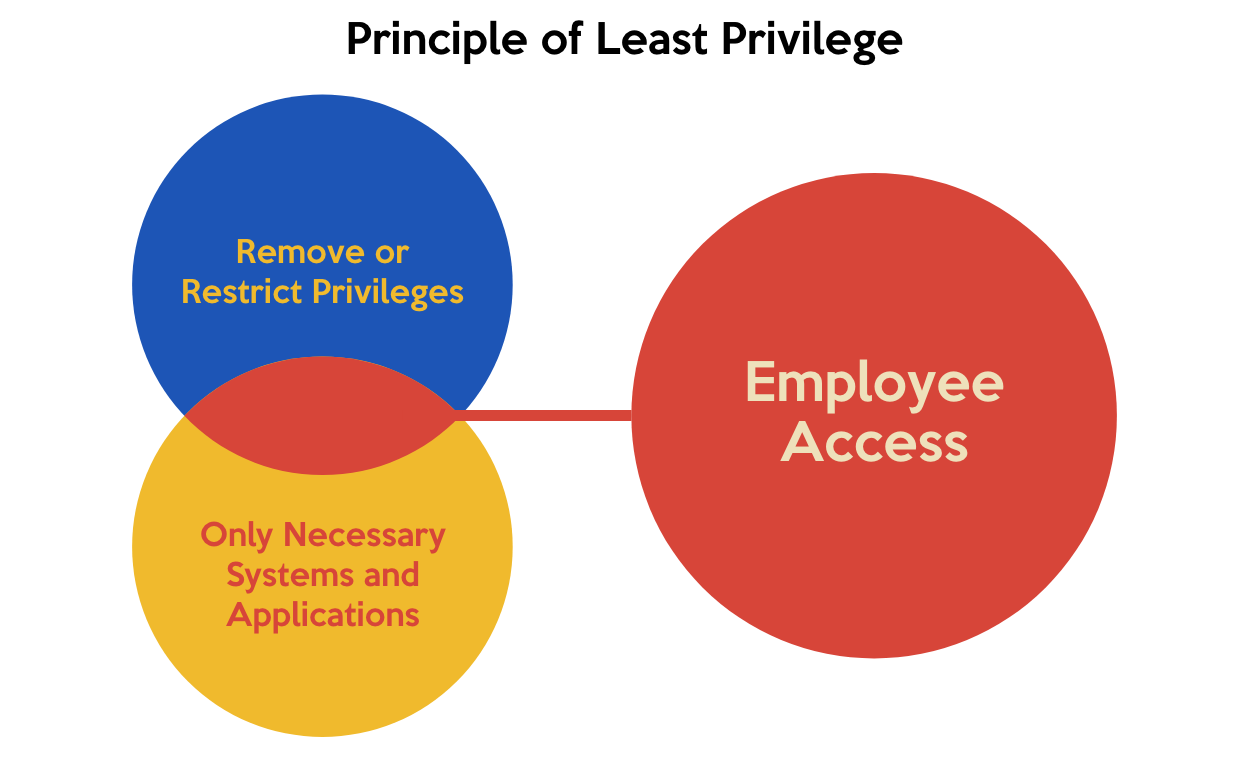
Identity Access Management (IAM) for Dummies

Least Privilege CyberHoot Cyber Library

Policy Sentry IAM Least Privilege Policy Generator QAInsights

Create a least privilege S3 bucket policy Cheat Sheet Cybr

The least privilege principle in practice: 7 1 steps to avoid privilege

ConlinEthan LeastPrivilegePolicy Week2 docx Template Policy V 1 0

Principle of Least Privilege and Privilege Bracketing Xown Solutions

Least Privilege Access The Least Privilege Policy Explained

Least Privilege Access The Least Privilege Policy Explained

Least Privilege Access The Least Privilege Policy Explained

Least Privilege Access The Least Privilege Policy Explained

Principle of Least Privilege examples Least privilege model

How to Align Your Least Privilege Policy with Your Culture
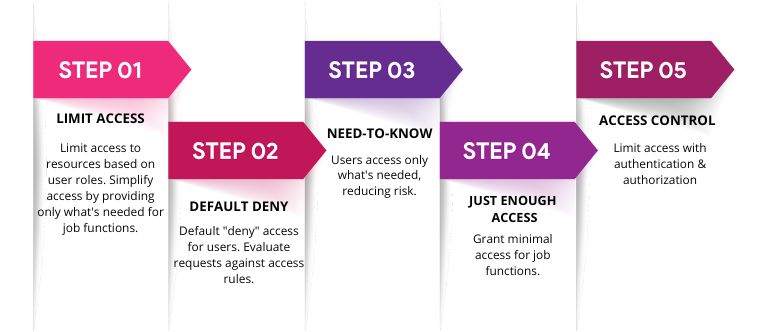
The Principle of Least Privilege Access: Maximizing Data Security BigID

Rowan Udell on LinkedIn: AWS IAM Least Privilege Policy Masterclass

How do you enforce the principle of least privilege in your information

Implementing least privilege administrative model PowerPoint templates

Principle of Least Privilege Explained (How to Implement It)

Least Privilege policy Gøran Tømte
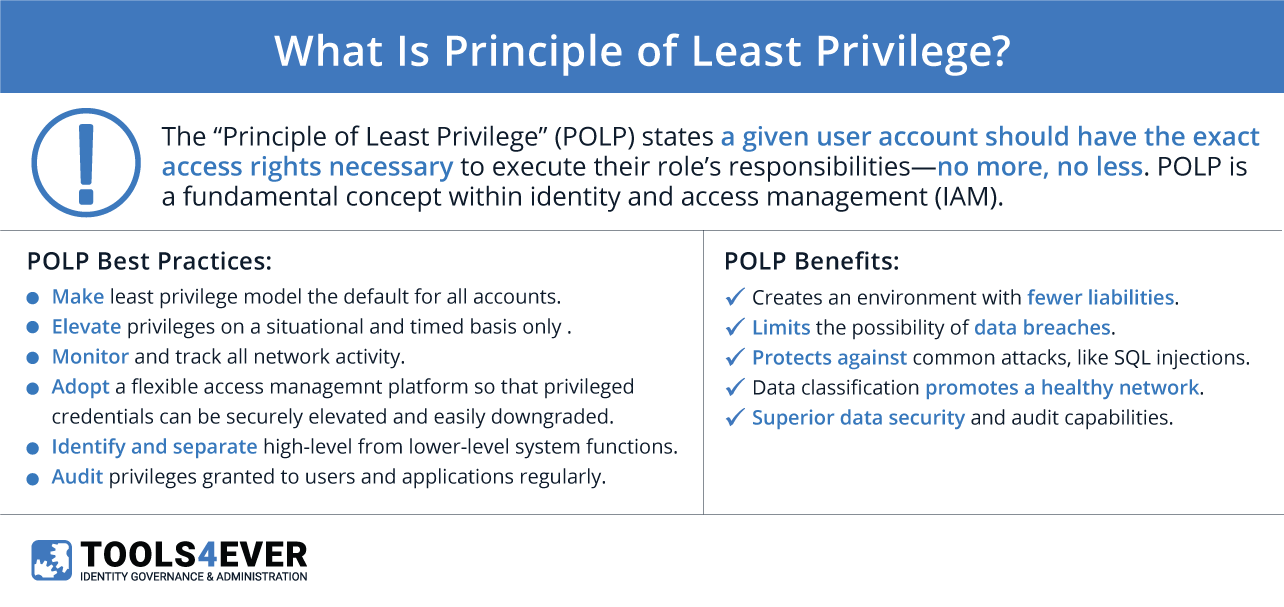
What is Principle of Least Privilege? Tools4ever
Access Control Policy Powerpoint PPT Template Bundles PPT Sample

There s a New Way To Do Least Privilege

Six Ways To Apply The Principle Of Least Privilege To vrogue co

How to Minimize Unintended Access and Achieve Least Privilege with

How to Minimize Unintended Access and Achieve Least Privilege with

How to Minimize Unintended Access and Achieve Least Privilege with

How to Minimize Unintended Access and Achieve Least Privilege with

How to implement the principle of least privilege with CloudFormation
Solution Template Documentation

What is Principle of Least Privilege (POLP)? zenarmor com
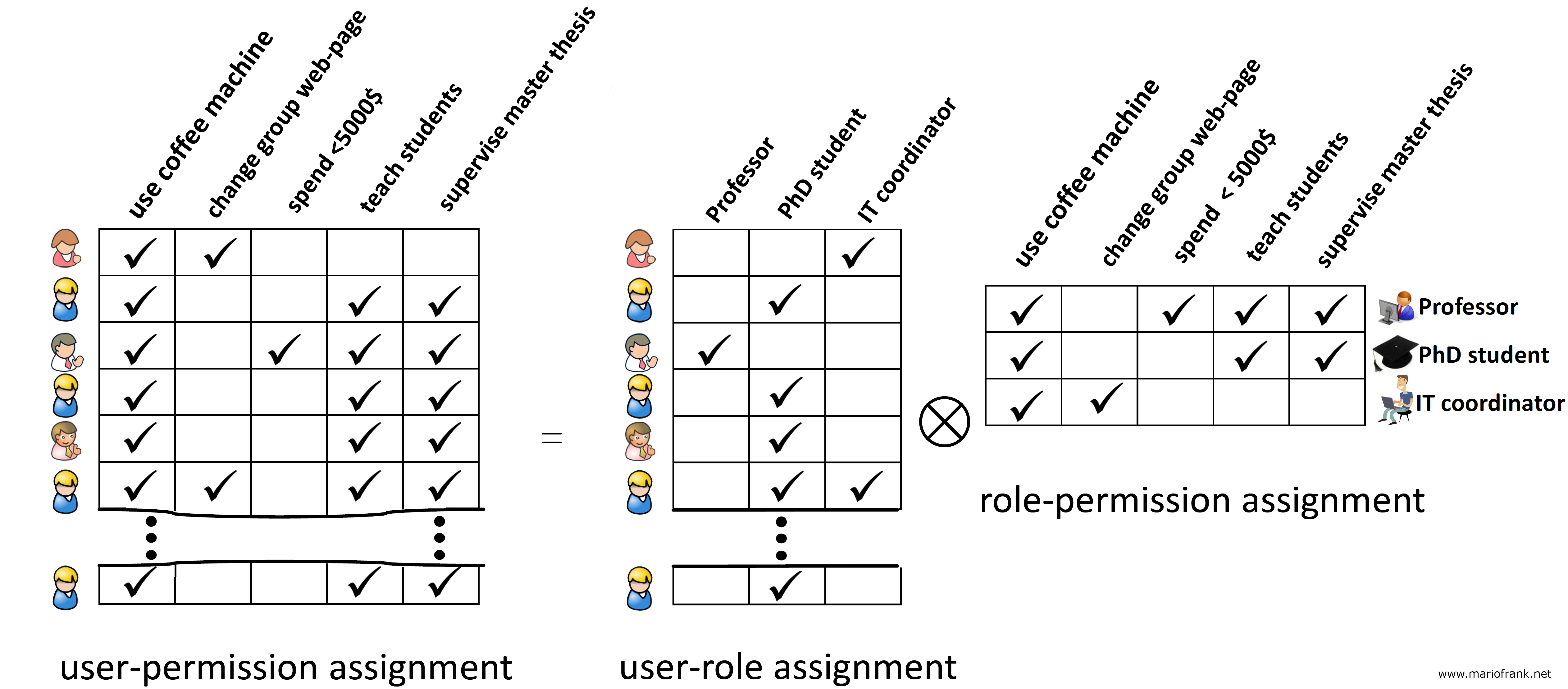
Rbac Matrix Template

Cyber Security News ® on LinkedIn: Types of privilege Accounts Cyber
Page pour en savoir plus Qu est ce que le moindre privilège

Check Your Privilege Chart

Use IAM Access Analyzer policy generation to grant fine grained

Rowan Udell

Rowan Udell
Rowan Udell

Certified in CyberSecurity (CC) Access Control Least Privilege

Risk remediation and least privilege policy enforcement ManageEngine

Education Gumroad

lerytan Blog

The Right Approach to Zero Trust for Medical IoT Devices

Slauth io CTO

Slauth io CTO

Creatio on LinkedIn: No Code Playbook get your PDF copy for free
Top 10 PAM Solutions Techyv com
Ppt Authentication Access Control And Authorization 1 Of 2 Hot

Overcoming the Visibility Challenge and Enhancing Cloud Security
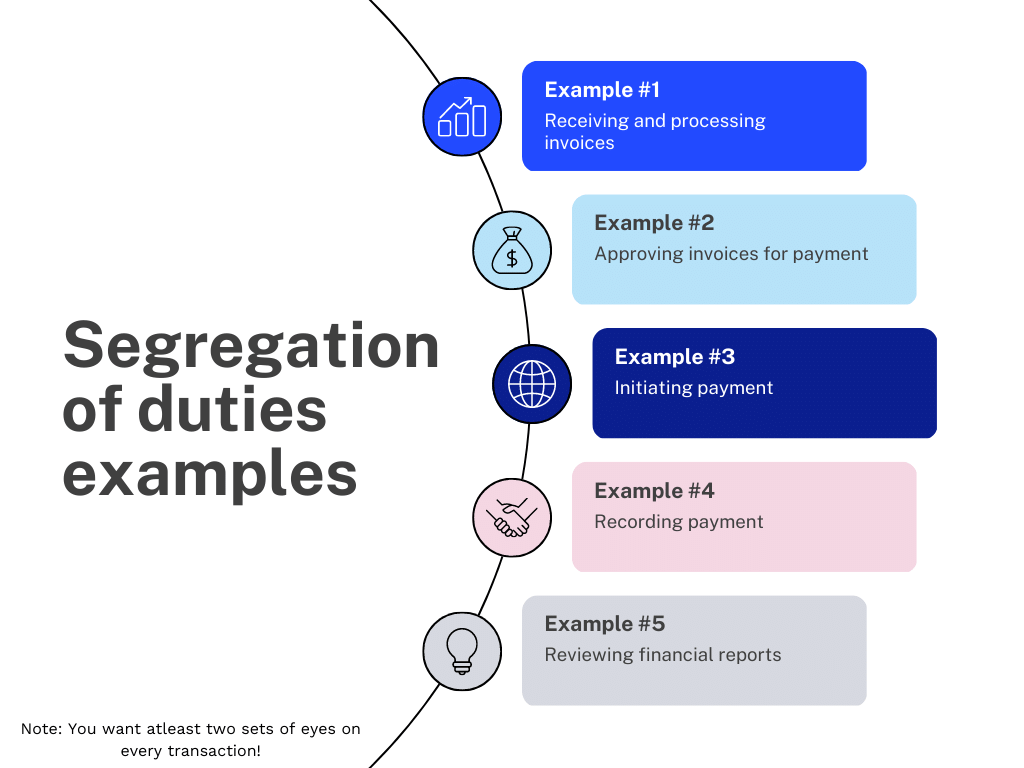
Segregation Of Duties Control Example at Kevin Morel blog

Rowan Udell on LinkedIn: And that #39 s a wrap I had good fun presenting

Best Practices IAM Audit Checkpoints for Optimal Security on AWS TO