Insider Threat Plan Template
Here are some of the images for Insider Threat Plan Template that we found in our website database.

Insider Threat Management PDF Security Computer Security
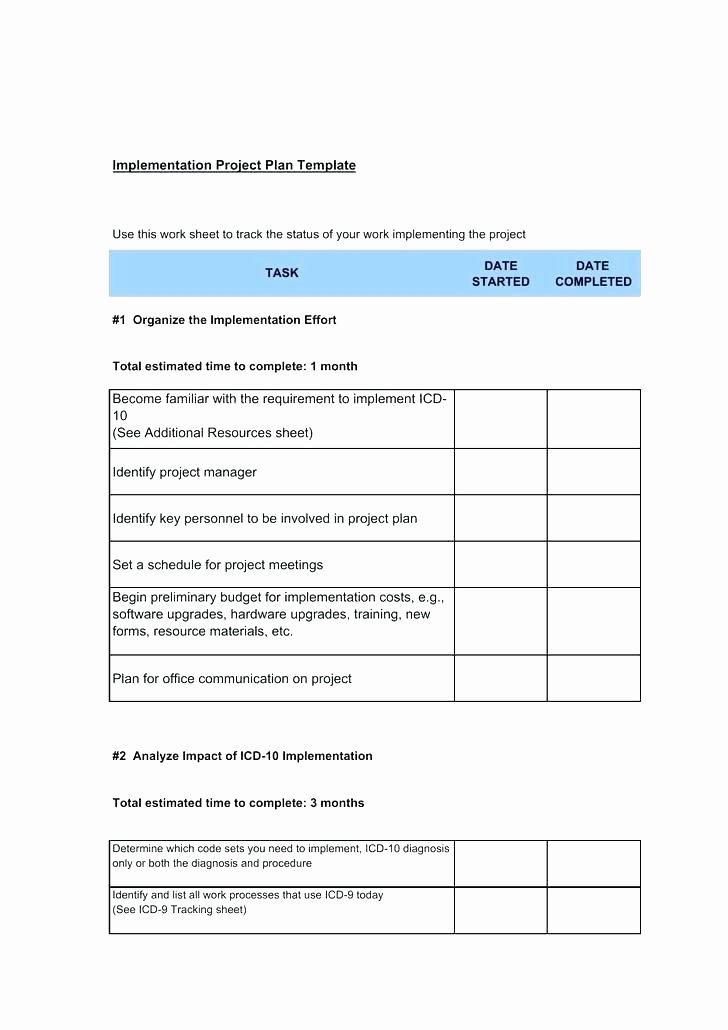
Software Implementation Project Plan Template Lovely Insider Threat
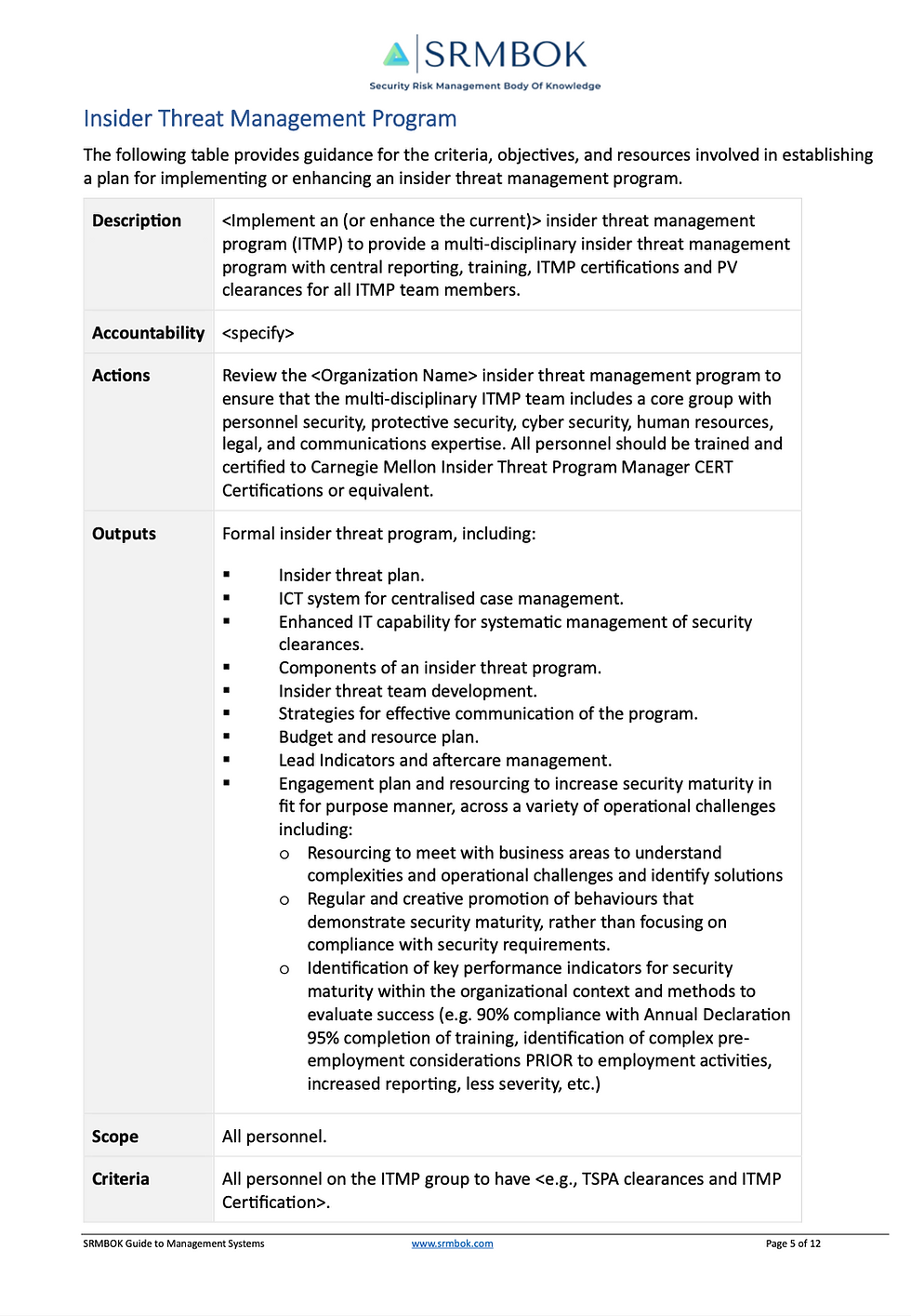
Insider Threat Program Plan Template

Insider Threat Plan Template
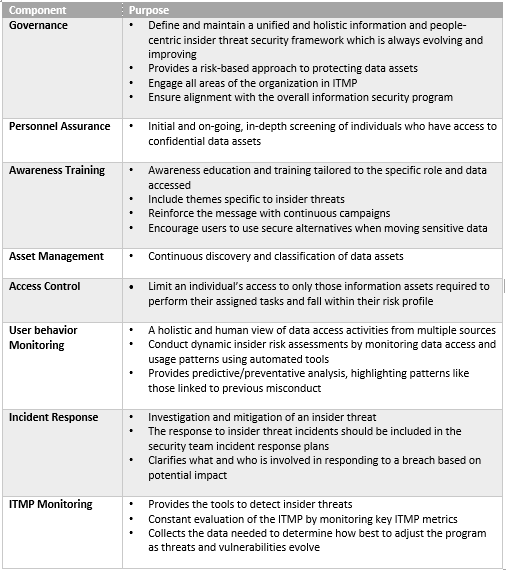
Insider Threat Plan Template

Insider Threat Plan Template
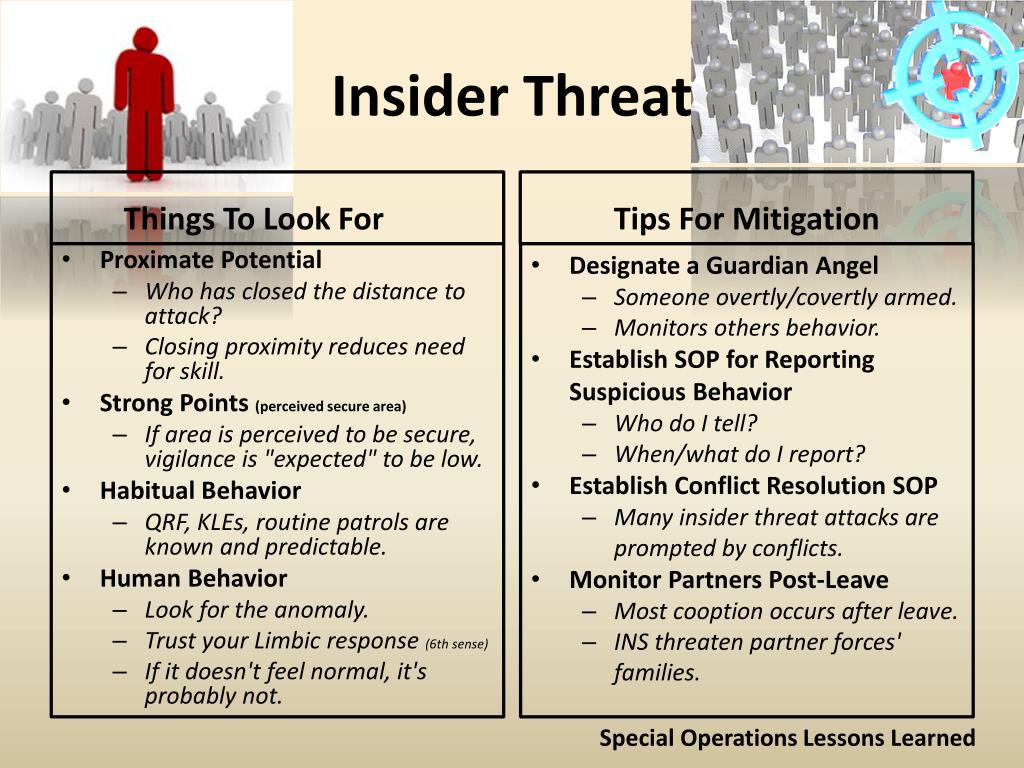
Insider Threat Plan Template

Insider Threat Plan Template

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint
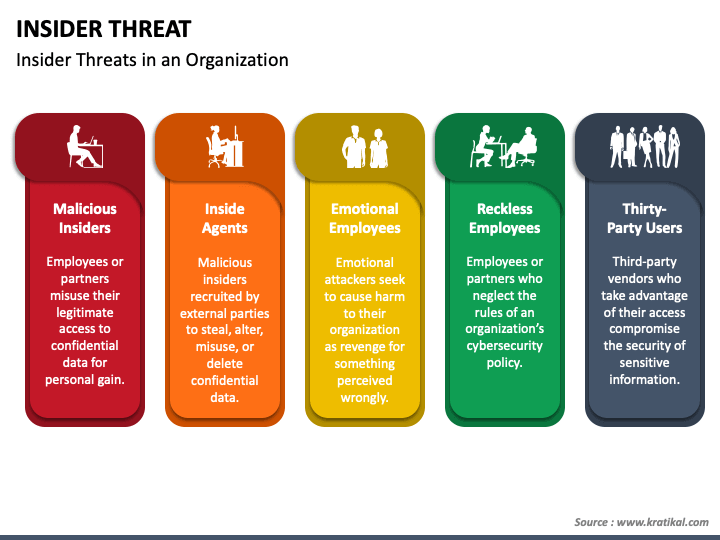
Insider Threat Policy Template

Insider Threat PowerPoint Presentation Slides PPT Template

What Is Insider Threat Indicators Types Of Insider Threats

Insider Threat Assessment Template

How To Create an Insider Threat Incident Response Plan
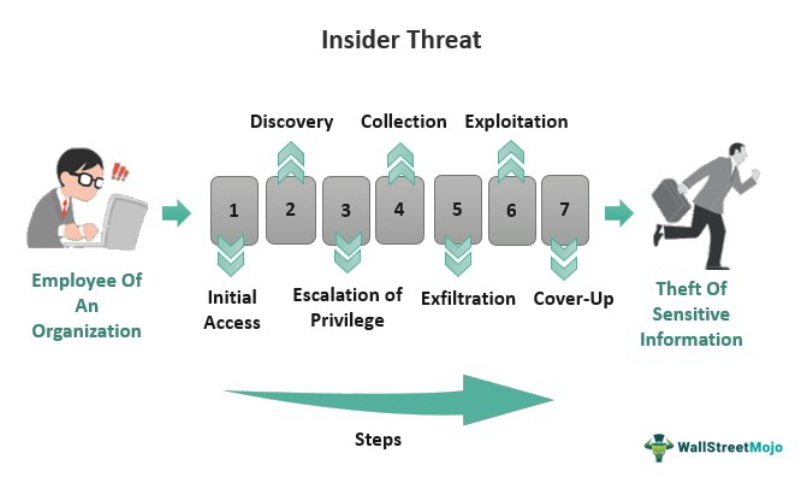
Insider Threat What Is It Indicators Examples Types Prevention

Cybersecurity Threat Intelligence Report Template in Word PDF Google
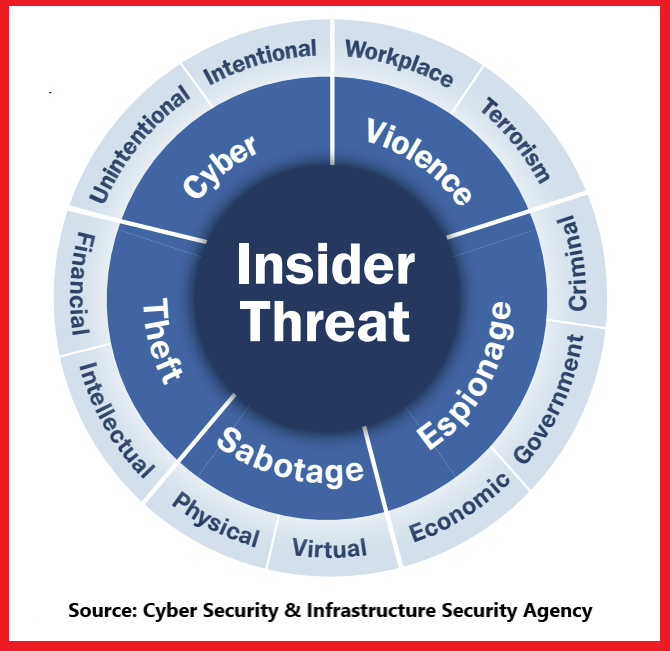
NATIONAL INSIDER THREAT SPECIAL INTEREST GROUP INSIDER THREAT
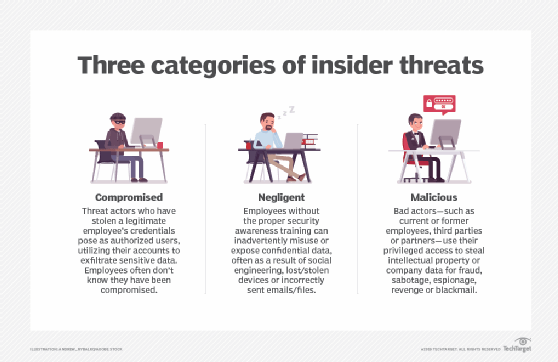
What is an Insider Threat?

NATIONAL INSIDER THREAT SPECIAL INTEREST GROUP INSIDER THREAT
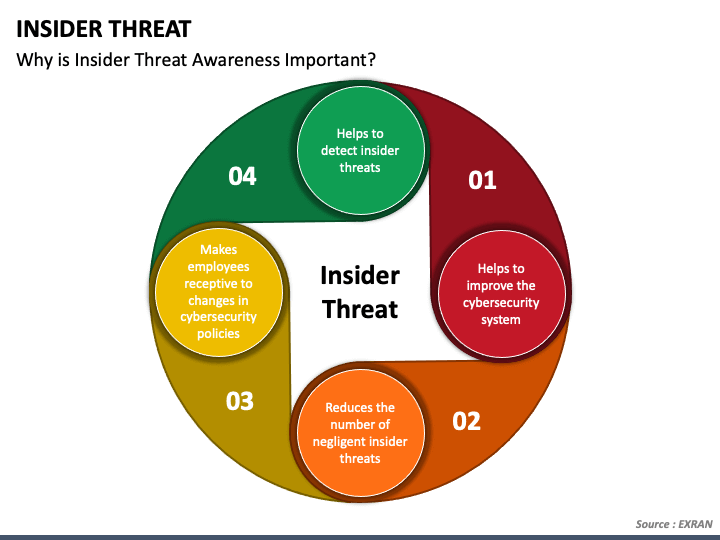
Insider Threat PowerPoint and Google Slides Template PPT Slides

What does your 2020 insider threat plan look like? Cyber Defense Magazine

What Is an Insider Threat Program Definition Goals Syteca

The Insider Threat Response Plan You Should Follow

How to Implement an Insider Threat Program

The Early Indicators Of An Insider Threat Digital Guardian

The Early Indicators Of An Insider Threat Digital Guardian
The Early Indicators Of An Insider Threat Digital Guardian
The Early Indicators Of An Insider Threat Digital Guardian

Threat Analysis And Risk Assessment Template prntbl

Threat Analysis And Risk Assessment Template prntbl

The importance of having an #39 Insider Threat Program #39 VIDEO gt Wright

Insider Program

Insider Program

Insider Program
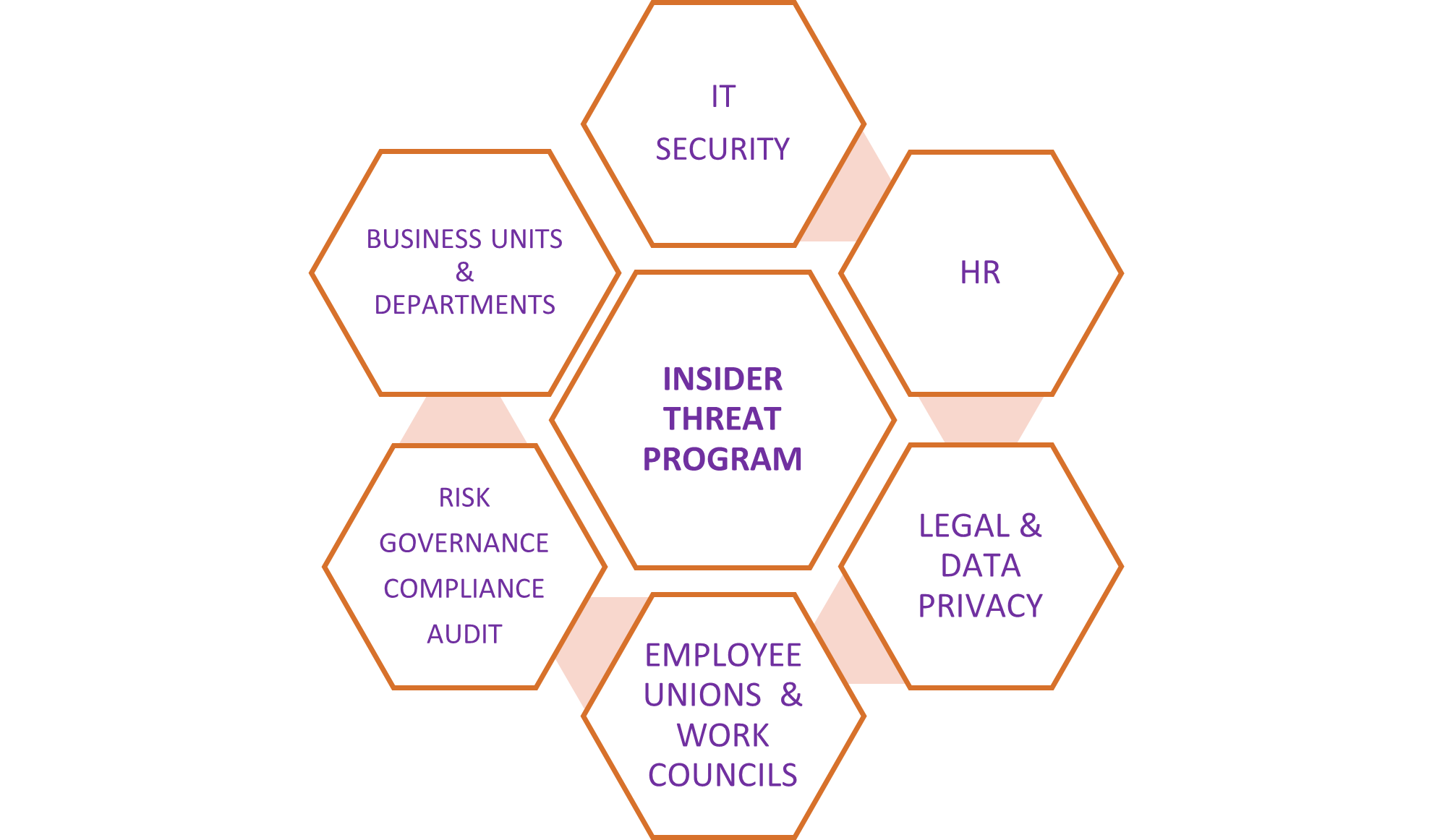
4 Steps to Maintain Employee Trust When Setting Up Your Insider Threat

Jamey S on LinkedIn: #bsidestampa #insiderthreat #incidentresponse #

Cyber Incident Response Plan Template Venngage
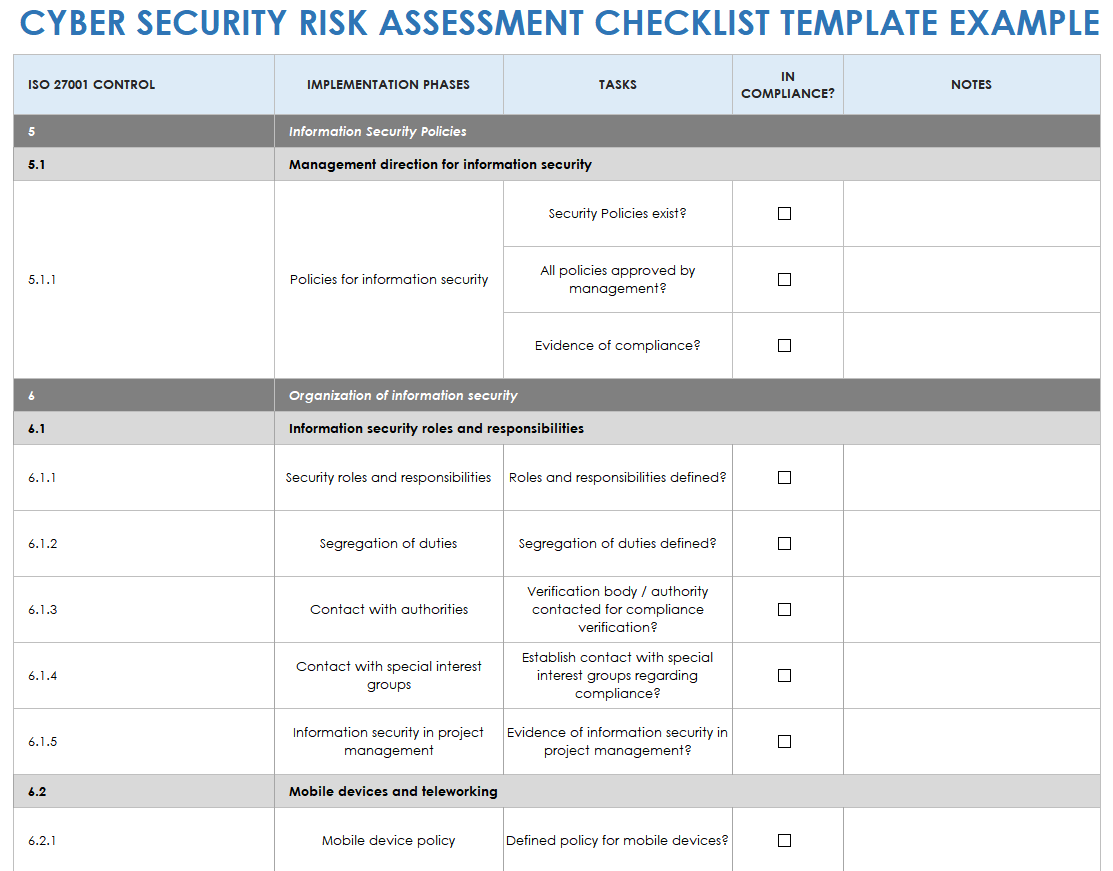
Security Audit Template Free Free Printables Hub
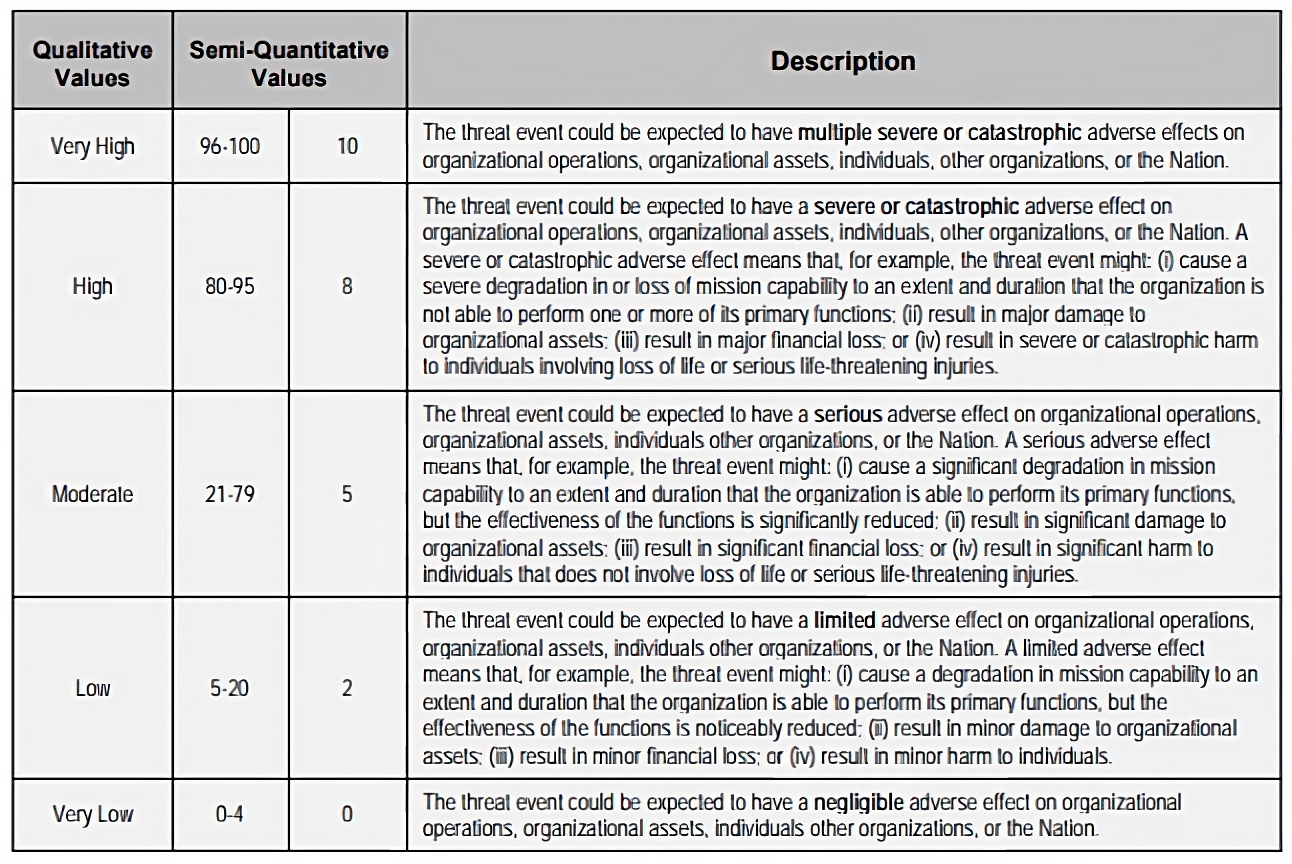
Nist Risk Assessment Template prntbl concejomunicipaldechinu gov co

Cyber Security Incident Response Process Flow Chart Download PDF
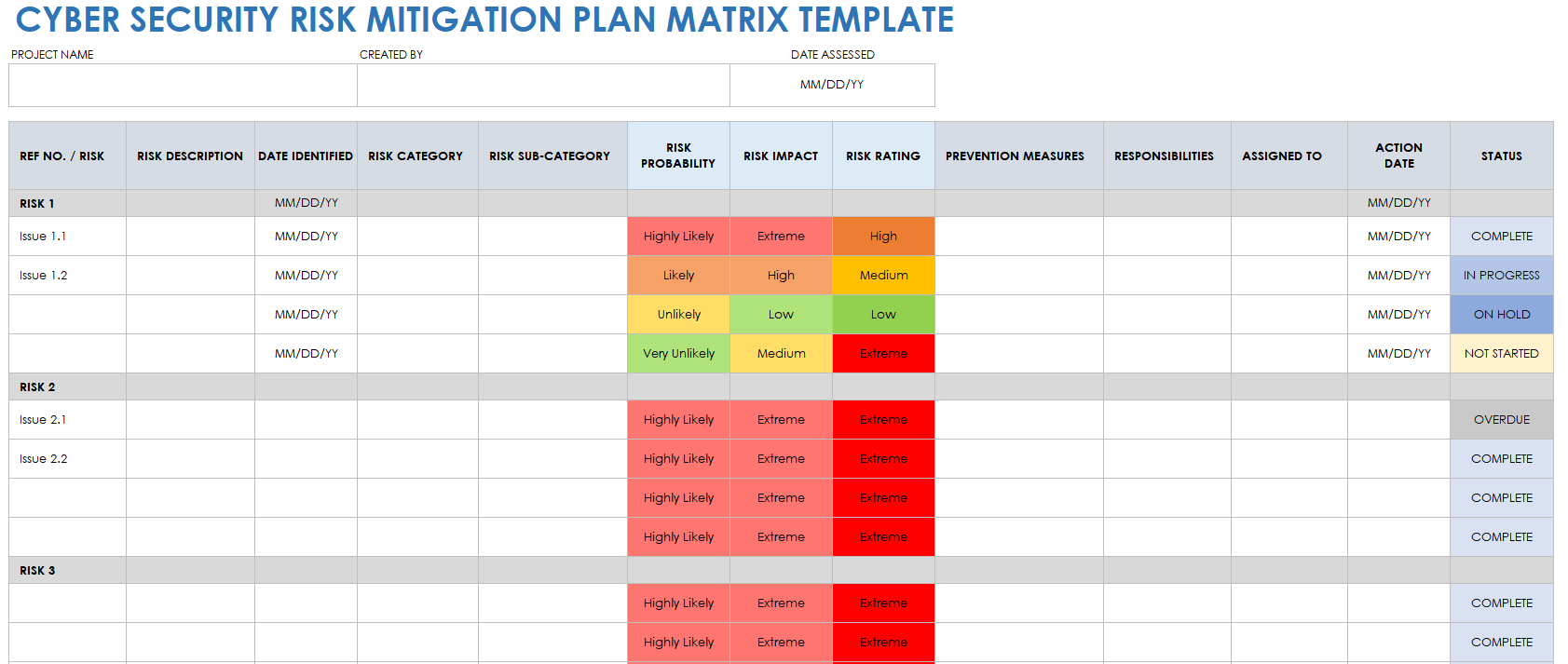
Army Risk Matrix Template Excel
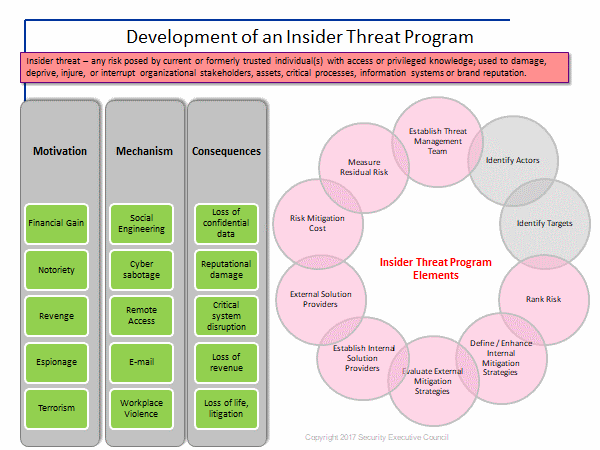
Development of an Insider Threat Program
Butterfly Coloring Sheet Free Printable prntbl
Butterfly Coloring Sheet Free Printable prntbl
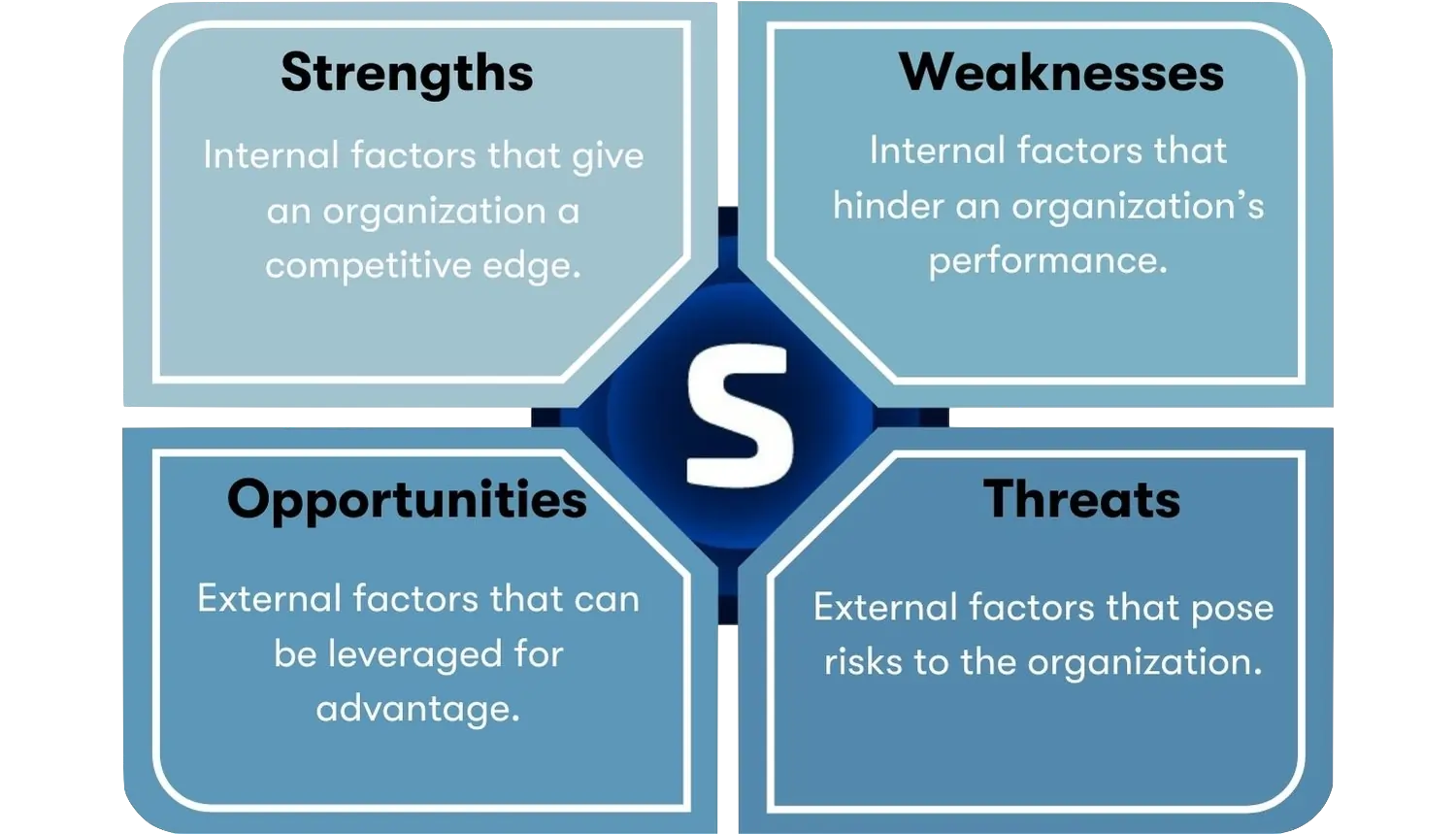
SWOT Analysis: Understanding Strengths Weaknesses Opportunities and

Related Links

2017 Insider Threat Guide

Fillable Online eCFR :: 32 CFR Part 117 National Industrial Security
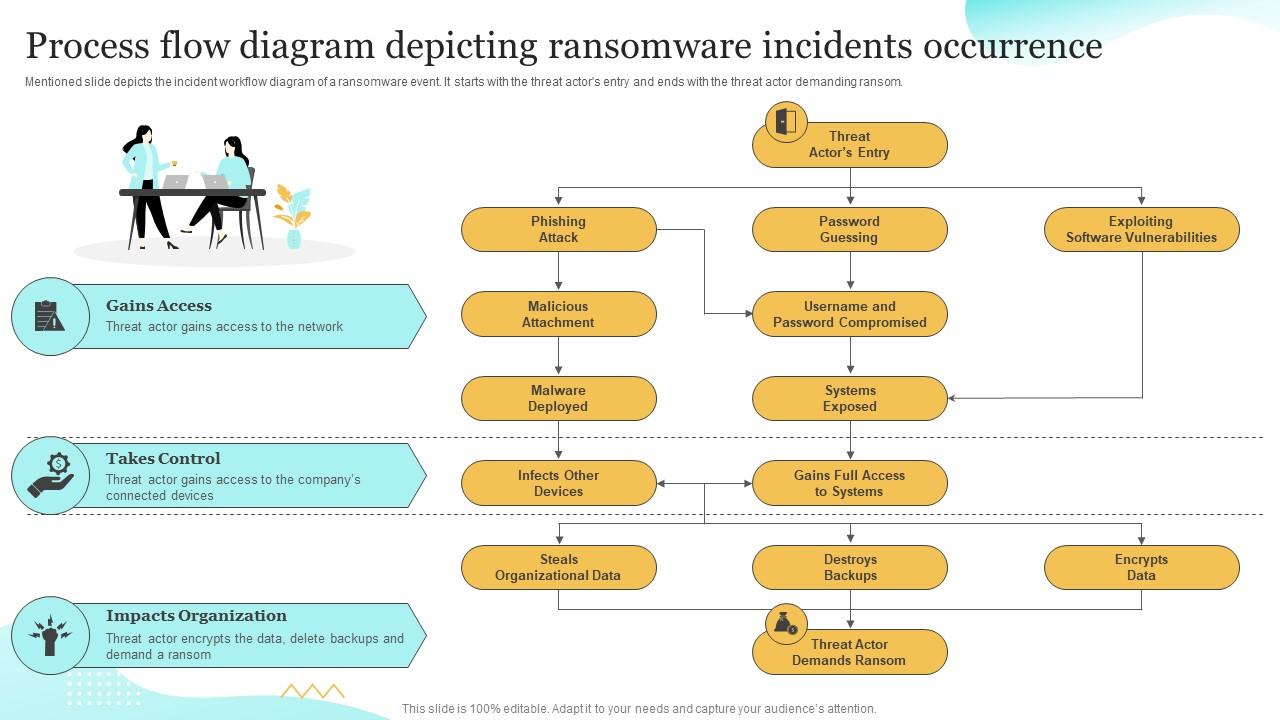
Process Flow Diagram Depicting Ransomware Upgrading Cybersecurity With