Encryption For Private Messages Crossword
Here are some of the images for Encryption For Private Messages Crossword that we found in our website database.
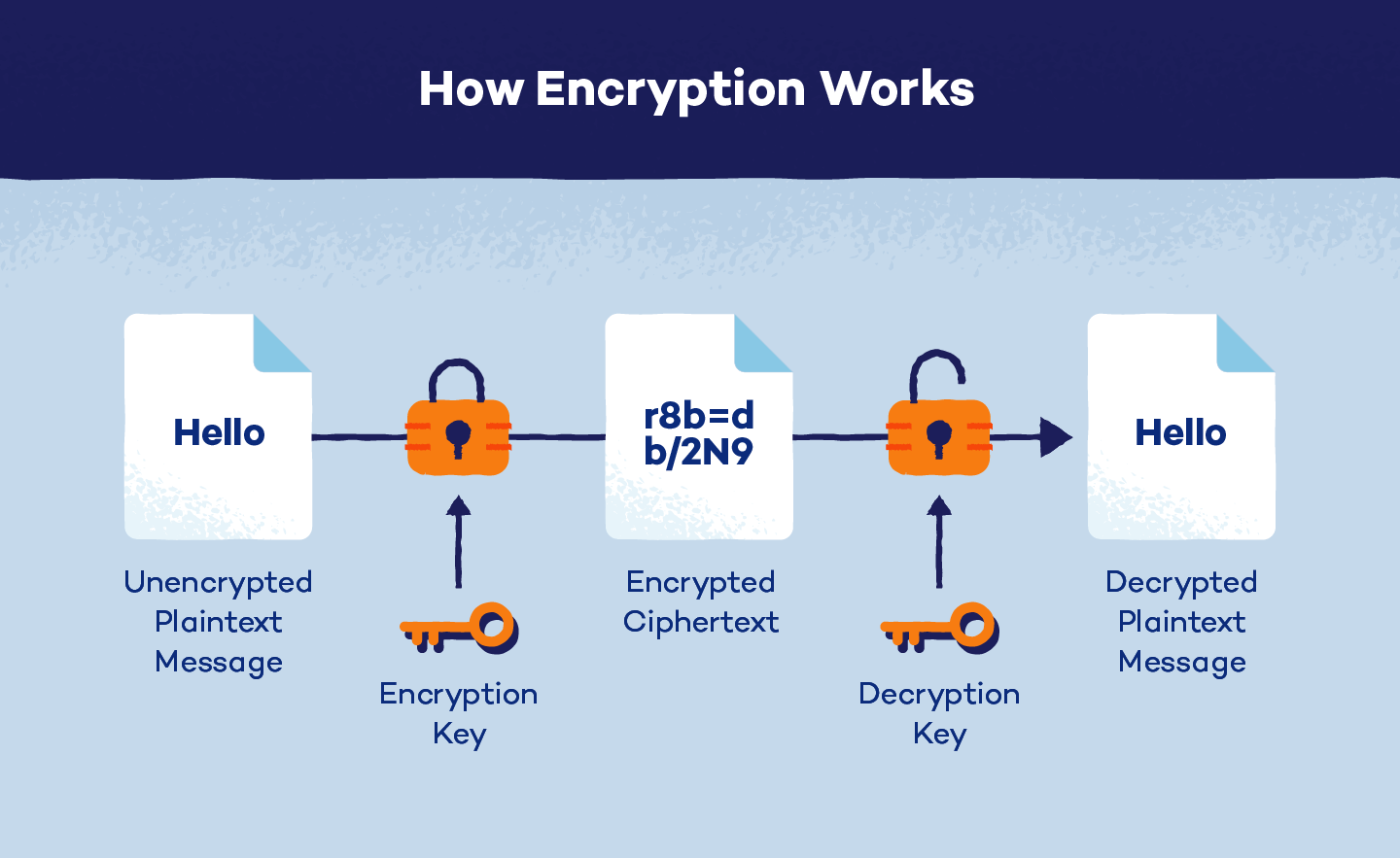
What Is Encryption and How Does It Work? Panda Security

Encryption choices: rsa vs aes explained Prey
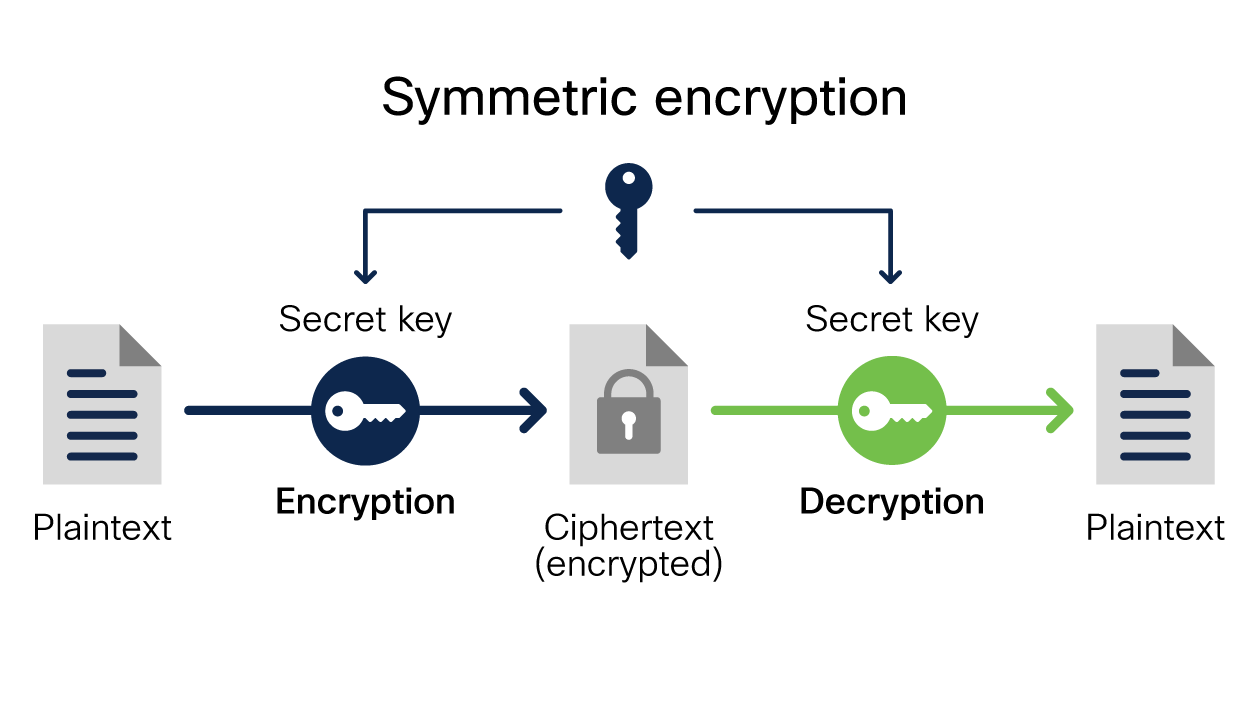
What Is Encryption? Explanation and Types Cisco

What Is Asymmetric Encryption How Does It Work? InfoSec Insights

Symmetric Encryption Algorithms: Live Long Encrypt Hashed Out by

What Is Encryption? Definition Types More Proofpoint US
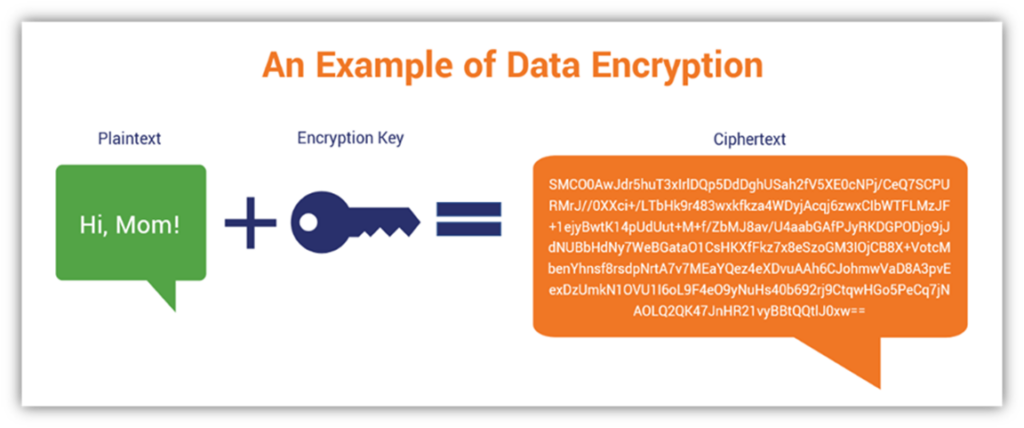
Encrypting Data
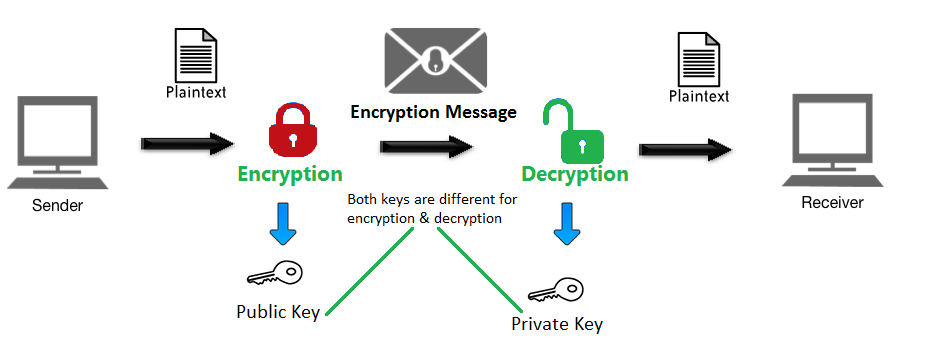
What is Encryption? Why it s Important? A Brief Overview
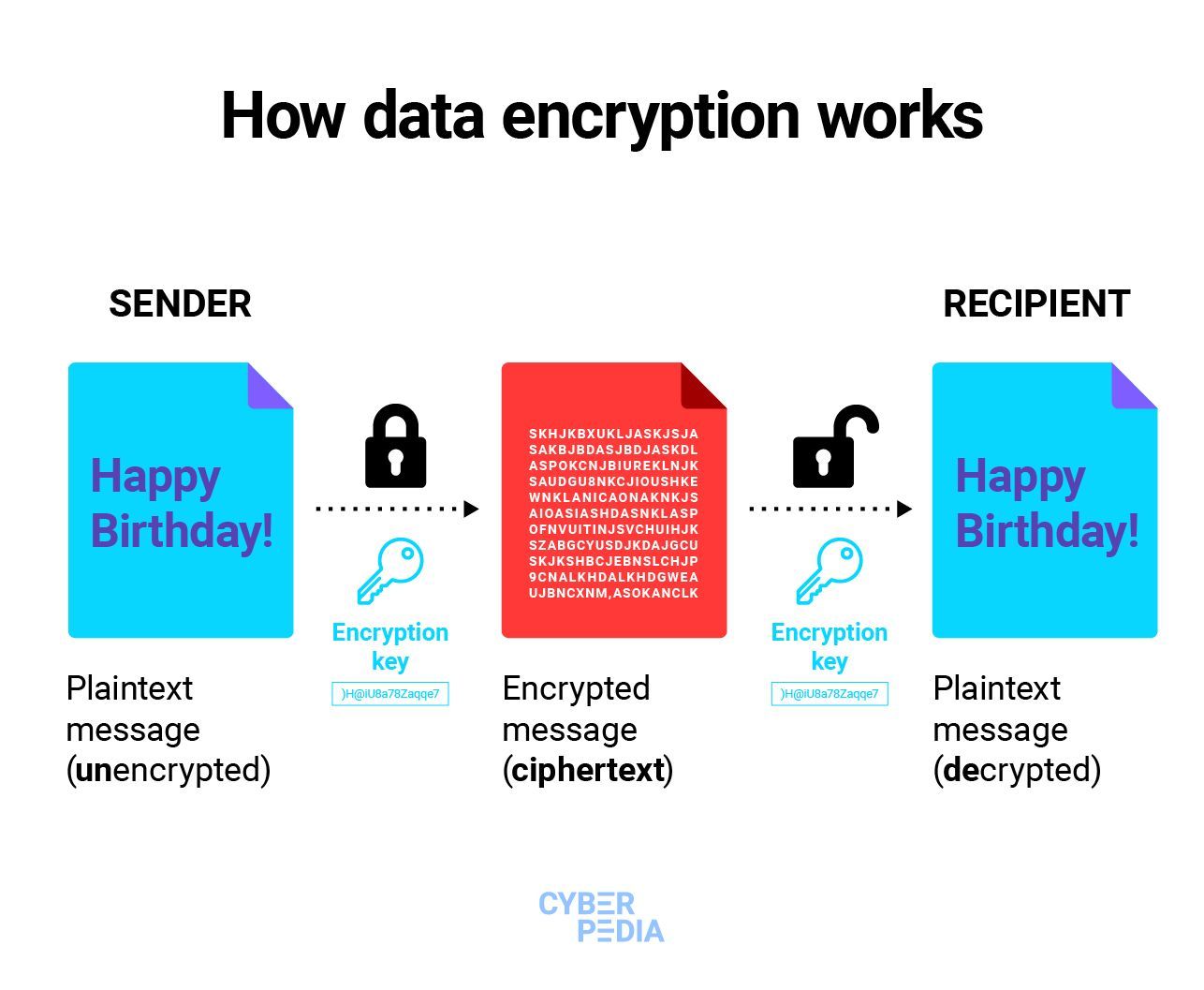
What is Data Encryption? Bitdefender Cyberpedia

Cryptography Tutorial GeeksforGeeks

Asymmetric Encryption How Asymmetric Encryption Works

What Is Encryption? How Does Encryption Work? Ciphertex Data Security

Difference Between Hashing vs Encryption

The Role of Encryption in Information Security: How Encryption Protects
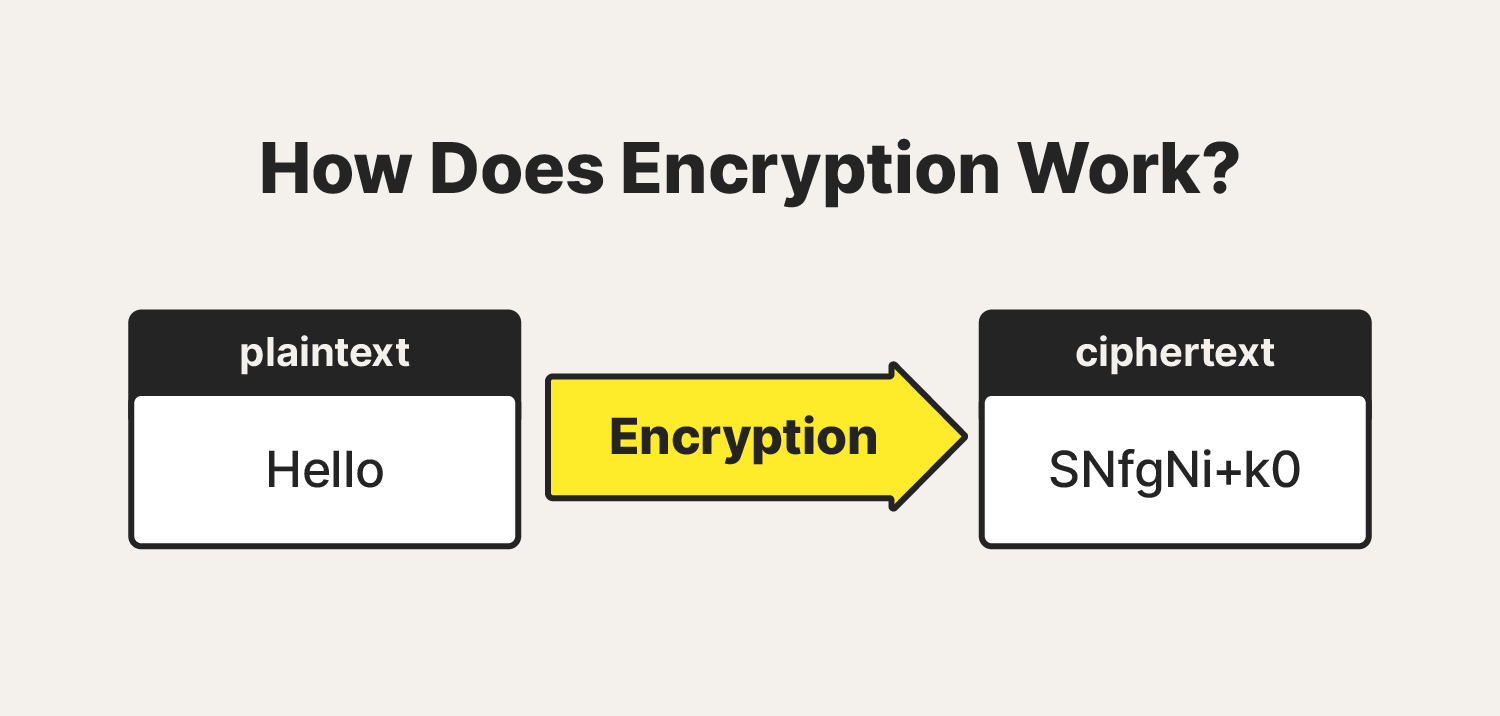
Wireless Encryption Types at Dennis Penn blog

What is Data Encryption?
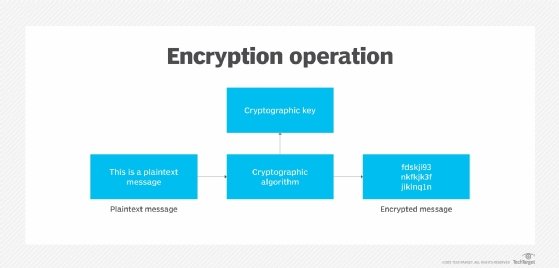
What is Encryption and How Does it Work?

Encryption safety system explanation with encrypt and decrypt outline

What is encryption? How it works types of encryption Norton
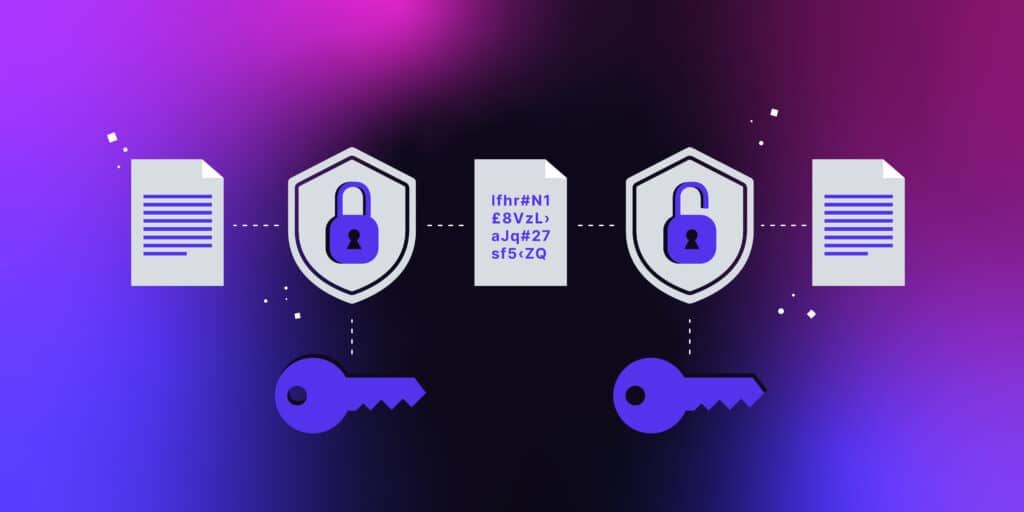
Lesson 11 FINAL PROJECT

Encryption TRICKSTER
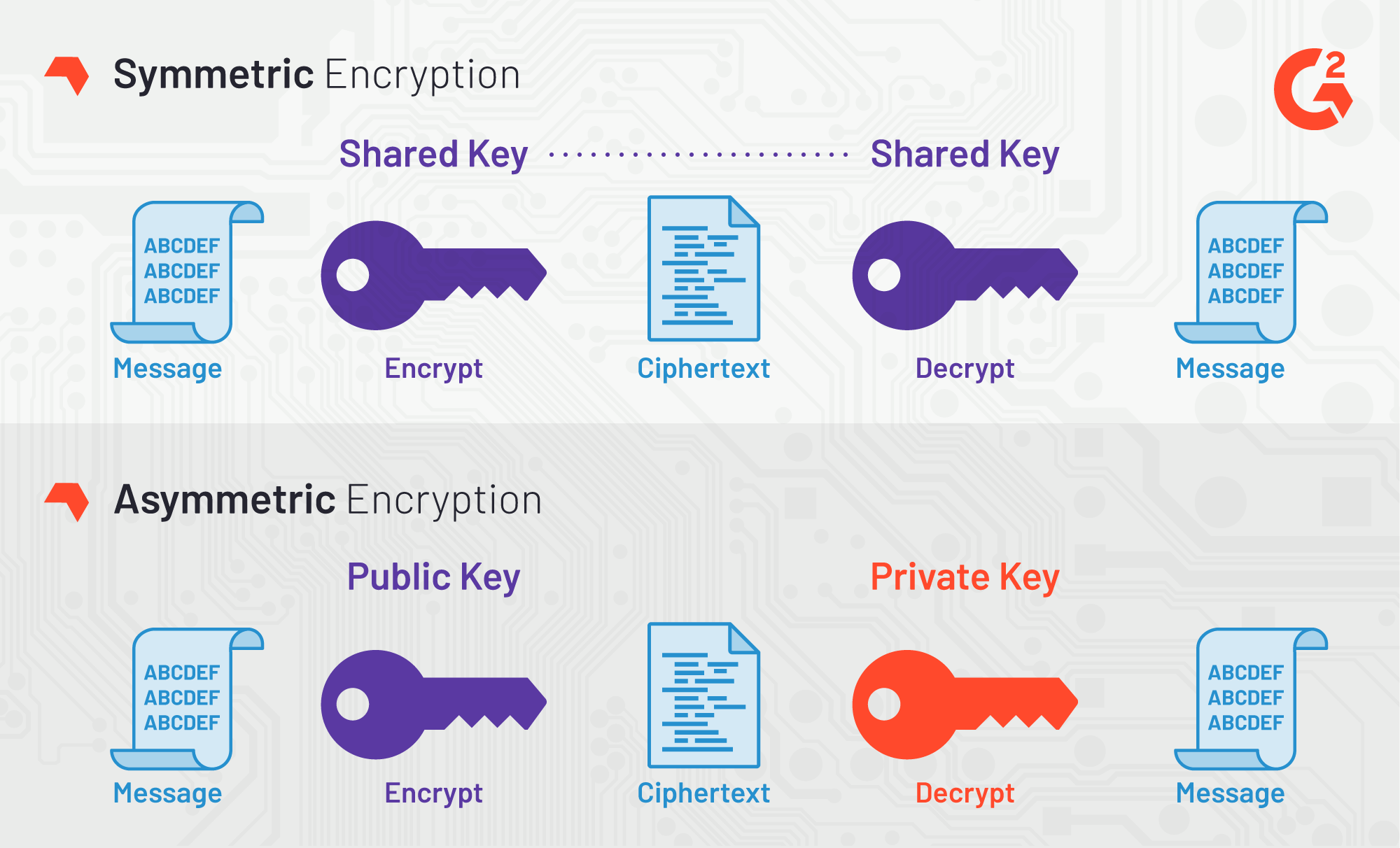
ploraplus Blog
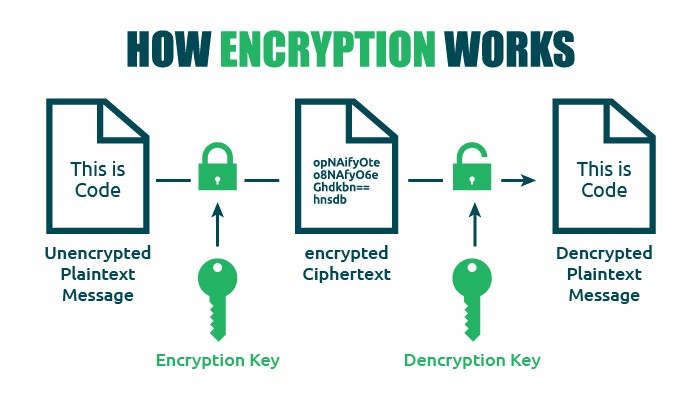
How Encryption Works
SSL Encryption PureSourceCode

Concept of Cryptography in Blockchain Analytics Vidhya

What is Asymmetric Encryption? Babypips com
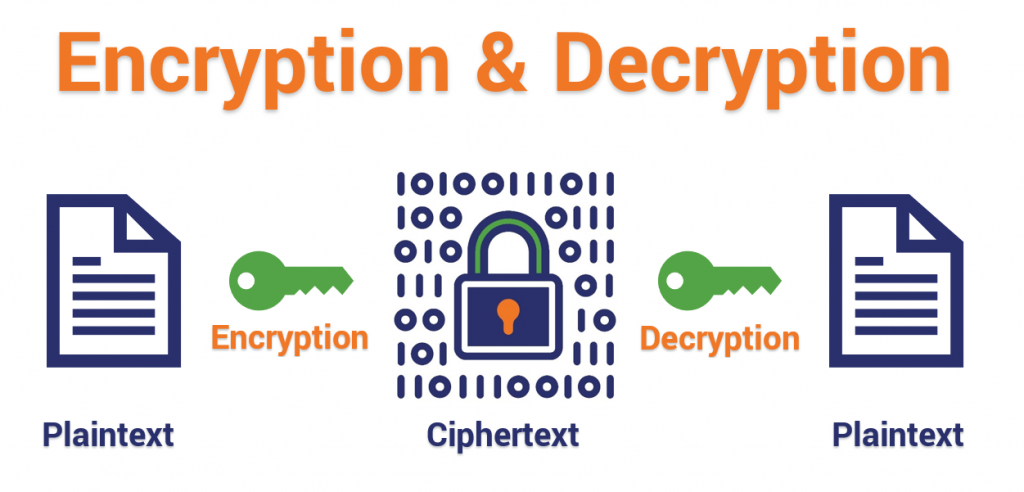
How Does HTTPS Work? Hashed Out by The SSL Store™

Encryption: what is it and how does encryption software work? WIRED UK

Data Encryption PowerPoint and Google Slides Template PPT Slides
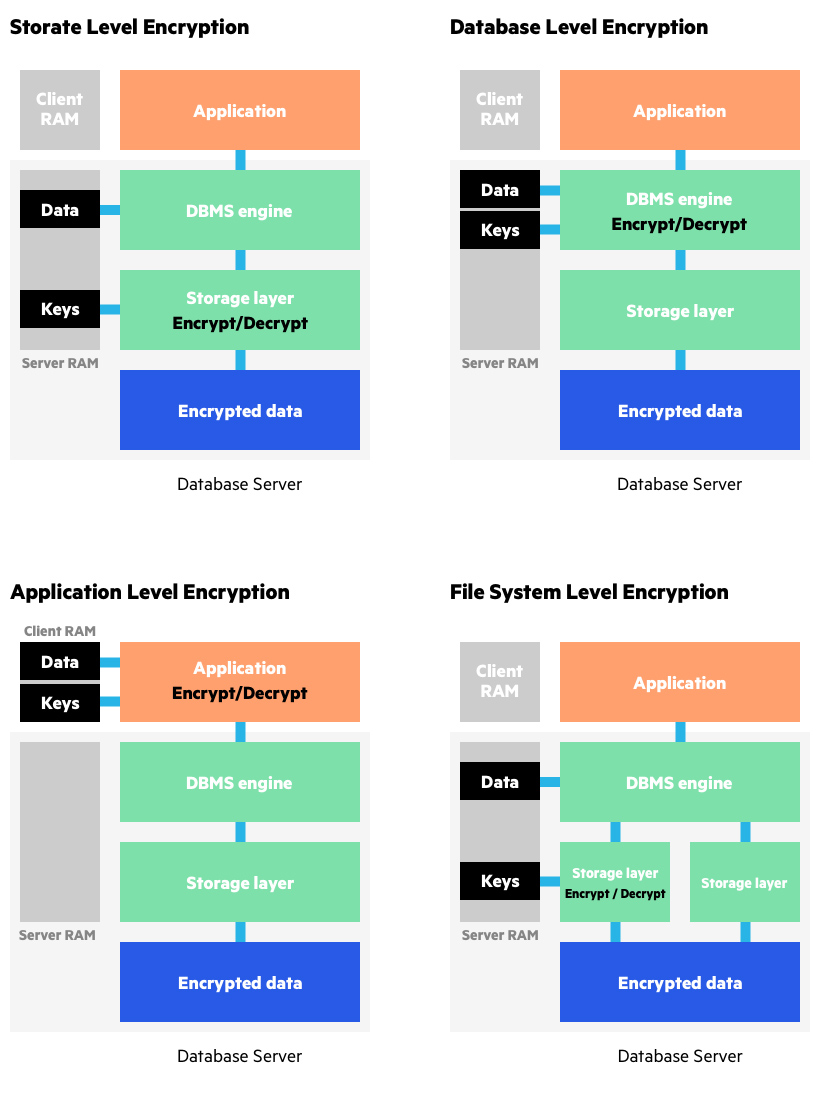
data encryption
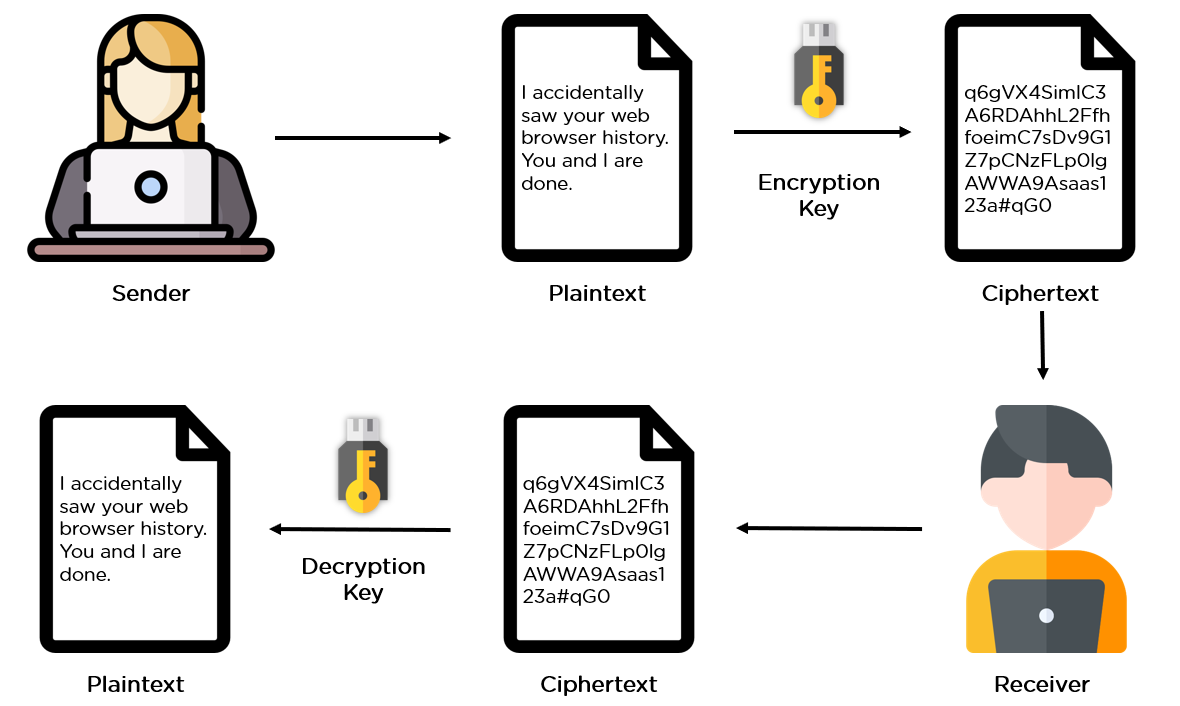
What Is Data Encryption: Algorithms Methods and Techniques

What is Data Encryption Encryption Algorithms

5 Common Encryption Algorithms and the Unbreakables of the Future
How To Encrypt Data Client Side JavaScript? Newsoftwares net Blog
What is Data Encryption? Benefits of Using Encryption Technology