Cybersecurity Workforce Certification Training
Here are some of the images for Cybersecurity Workforce Certification Training that we found in our website database.

teiss Insider Threat Internal threats: the importance of culture to

What Does the Cybersecurity Landscape Look Like in 2023? BusinessWest

Top 5 Cyber Security Trends for 2025

2024 #39 s Top Cybersecurity Trends: Insights by advansappz

What Is Cybersecurity? Forage

Demystifying the Role of AI in Cybersecurity
.jpg#keepProtocol)
What is Cybersecurity? Everything You Need to Know

Cybersecurity: The Forever Problem

How To Get Started In Cyber Security With No Experience

Breaking Down the Intersection of AI and Cybersecurity

What is Cybersecurity? Blue Light LLC

The Top Five Cybersecurity Trends In 2023

What is Cybersecurity? Key Topics Strategies and Insights

20 000 Free Network Security Cyber Security Images Pixabay

2960x1848 Resolution Cybersecurity Core 2960x1848 Resolution Wallpaper

The Importance Of Cybersecurity CTI

The reality of cybersecurity threats in manufacturing Manufacturing

지금 바로 사이버 보안 태세를 강화하는 7가지 방법
Why Cybersecurity Should Be Part Of Any Business Strategy

10 Cybersecurity and Data Privacy Predictions for the 21st Century

10 000 Free Cybersecurity Logo Cybersecurity Images Pixabay

Cybersecurity Courses: Requirements Career Prospects aecc

India 2023 Top 5 Trends to Watch in Cybersecurity

Cyber Security and Segregation of Duties SafePaaS

Bolstering cybersecurity readiness in the cloud Information Age

November 2020 Cybersecurity Influencers React to Space Policy

8 steps to starting a cybersecurity virtuous cycle World Economic Forum

Cybersecurity Concerns With Ai

Boosting Cybersecurity: The Role of Automated Document Conversion

Cybersecurity Act of 2015 2025

Cybersecurity for Electronic Assemblies Manufacturing Cybersecurity

Cybersecurity Comprehensive cybersecurity protection

Tackling the Challenges of Managed Service Providers Huzzed

Unmasking The Digital Shadows: Cyber Attacks On Iran #39 s Nuclear Ambitions

The Role of Forensics in Cyber Security

Three Simple And Effective Cybersecurity Basics For Off The Grid Living

AI in cybersecurity: Yesterday s promise today s reality MIT

Cyber Security Risks With Ai

India becoming target of increased cybersecurity attack says report by
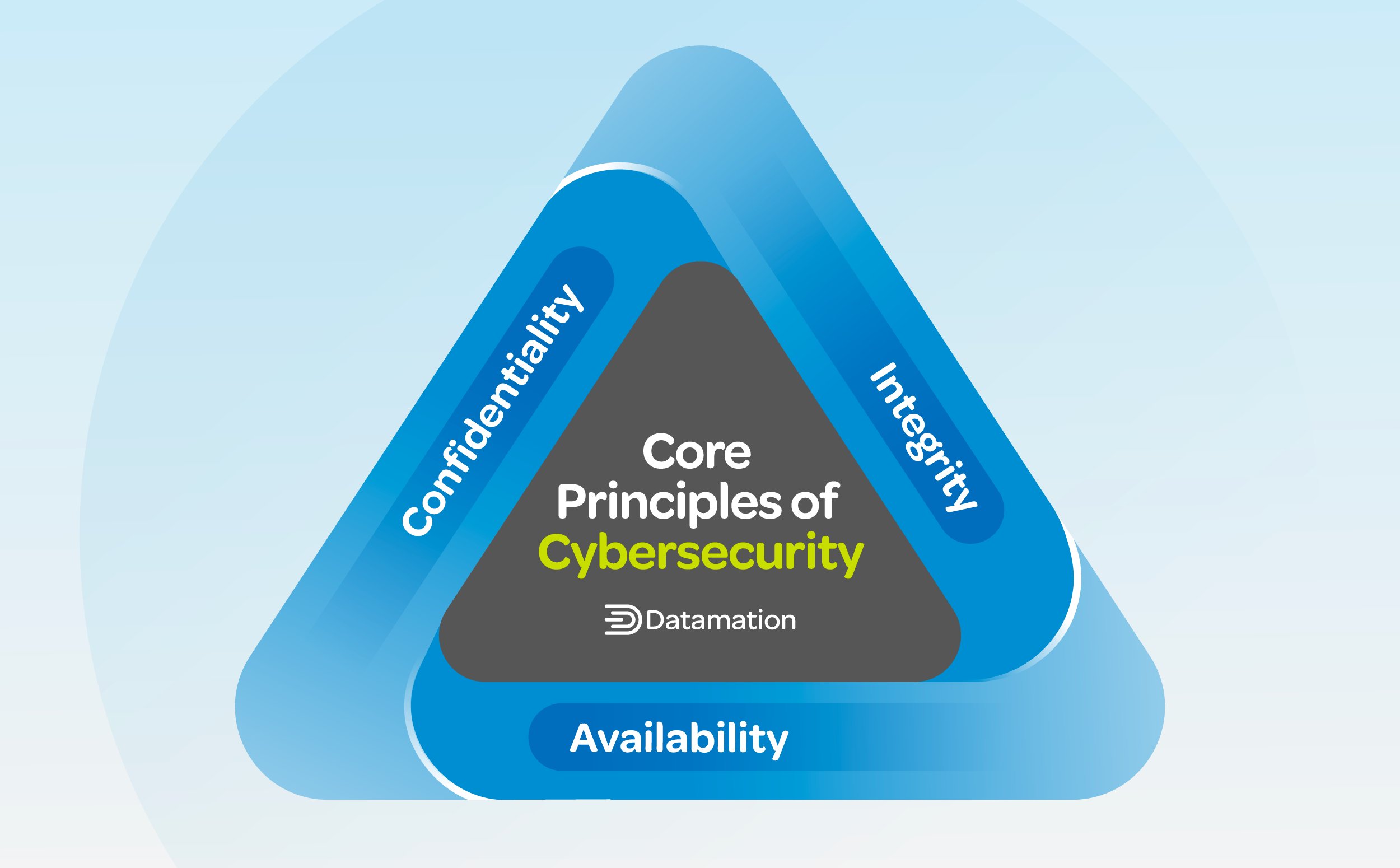
What Is Cybersecurity? Definitions Practices Threats

What is Cybersecurity and How Does it Work?

What is GLBA Compliance? Key Requirements and Concepts BD Emerson

How much cybersecurity expertise does a board need? The McCormick Group
Five Steps to Cyber Security in Virginia CoVaBiz Magazine

CYBER SECURITY

What is Cybersecurity? Everything You Need to Know

Cybersecurity Roadmap yashinfosec com

Between Blockchain Security vs Traditional Cybersecurity

What is a Cybersecurity Audit and Why is it Important? EasyDMARC
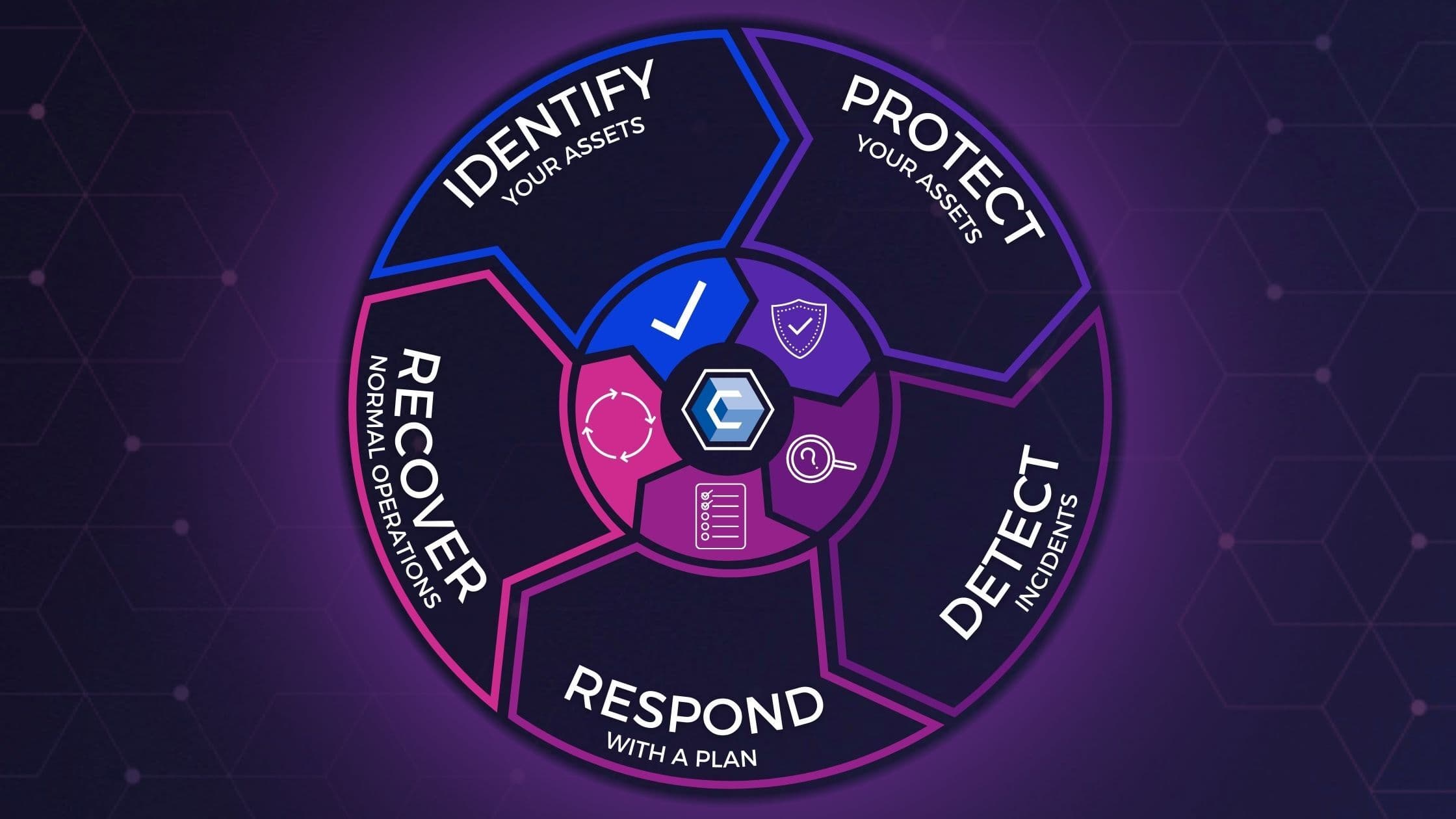
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

The role of Artificial Intelligence in Cyber Security CIO News

Security Measure: Định Nghĩa Ví Dụ và Cách Sử Dụng

Financial Analyst vs Data Analyst: A Comprehensive Guide to Their Roles
Industrial Control System Cybersecurity Resilience Industrial

Importance of Cyber Security in Business AeoLogic Blog

Understanding Malware: How to Categorize and Identify Types Without the
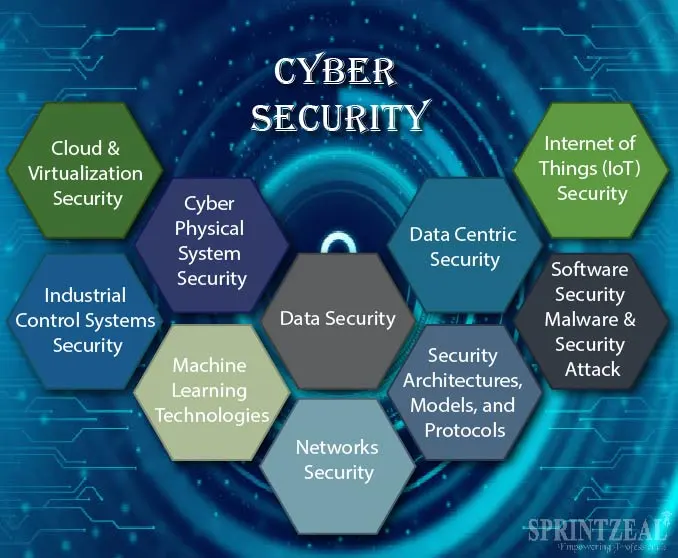
Emerging Technologies in Cybersecurity

Free Intro To Cybersecurity With Ai Course
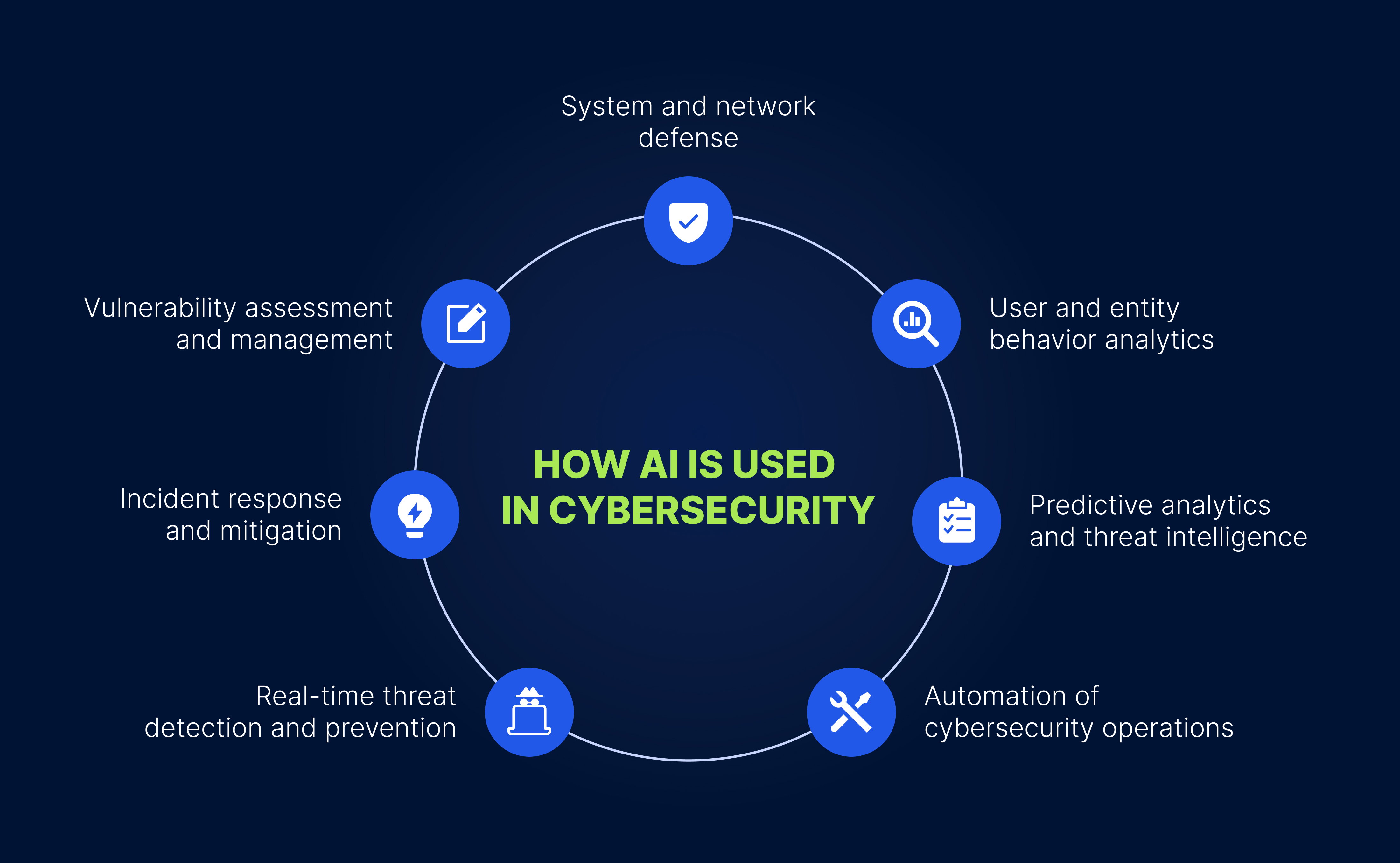
AI in Cybersecurity: What #39 s Next? EffectiveSoft
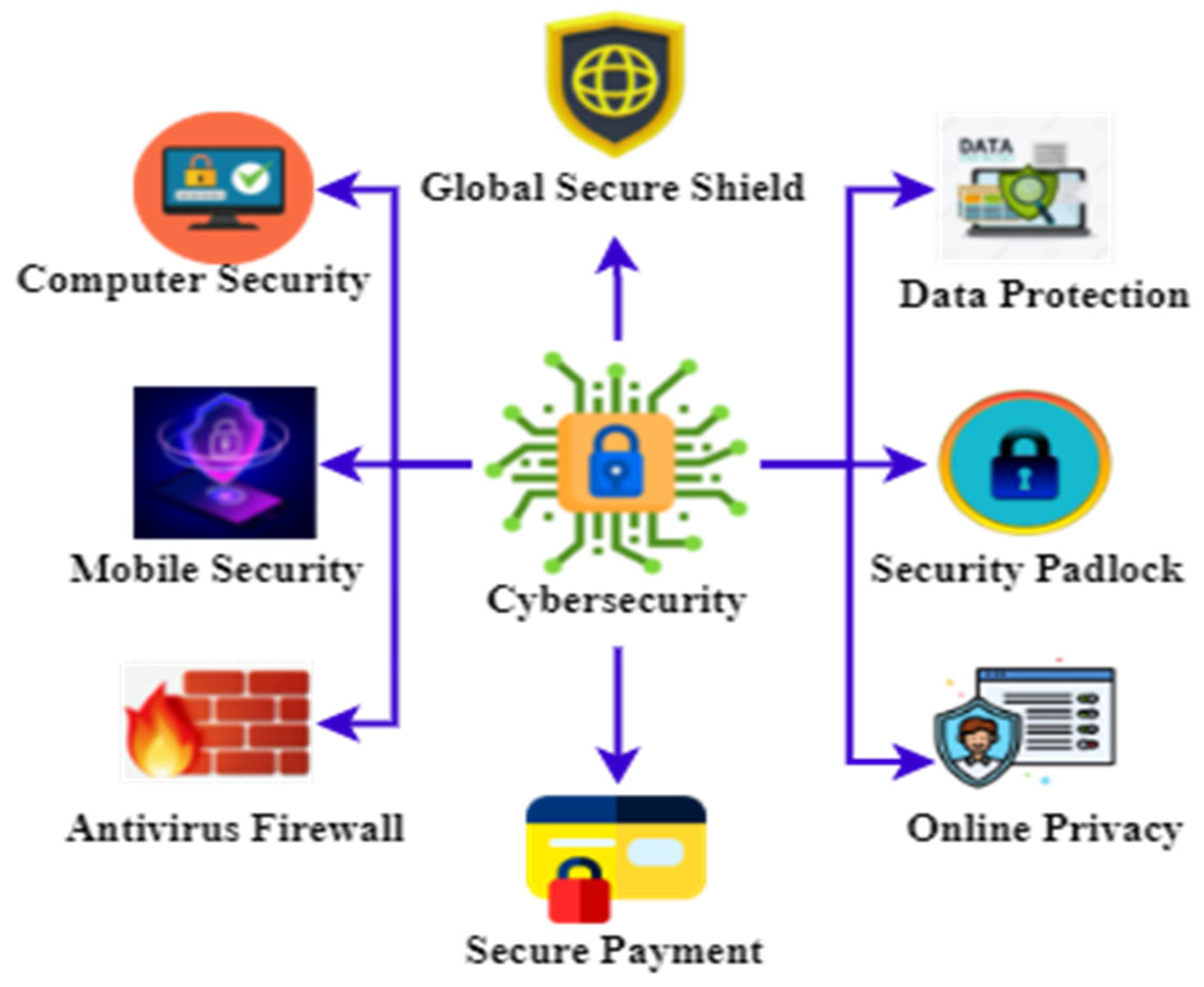
Applied Sciences Free Full Text Exploring the Impact of AI Based