Cyber Security Template Ppt
Here are some of the images for Cyber Security Template Ppt that we found in our website database.

Cyber Security PPT Presentation Template EaTemp

Cyber Security PPT Presentation and Template

Ai Cyber Security Powerpoint Ppt Template Images/cyber Security
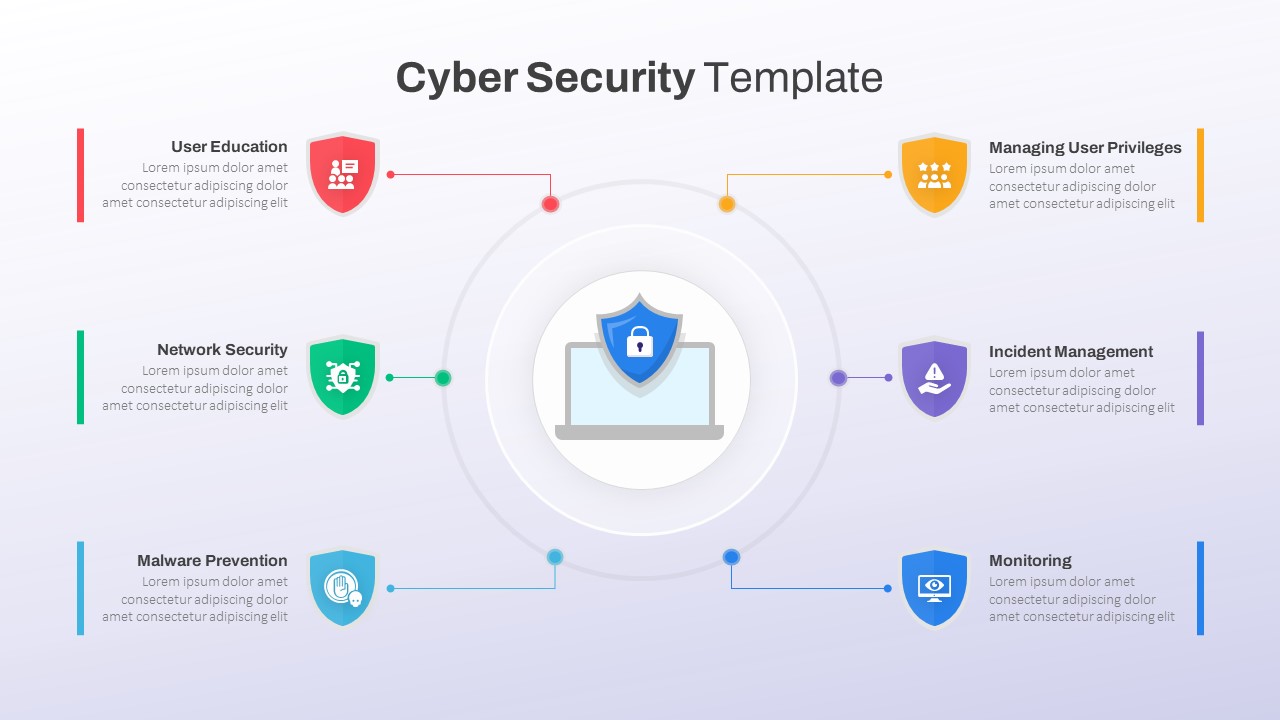
Cybersecurity Roadmap PPT Template and Google Slides SlideKit
Free Cyber Security Templates to Edit Online
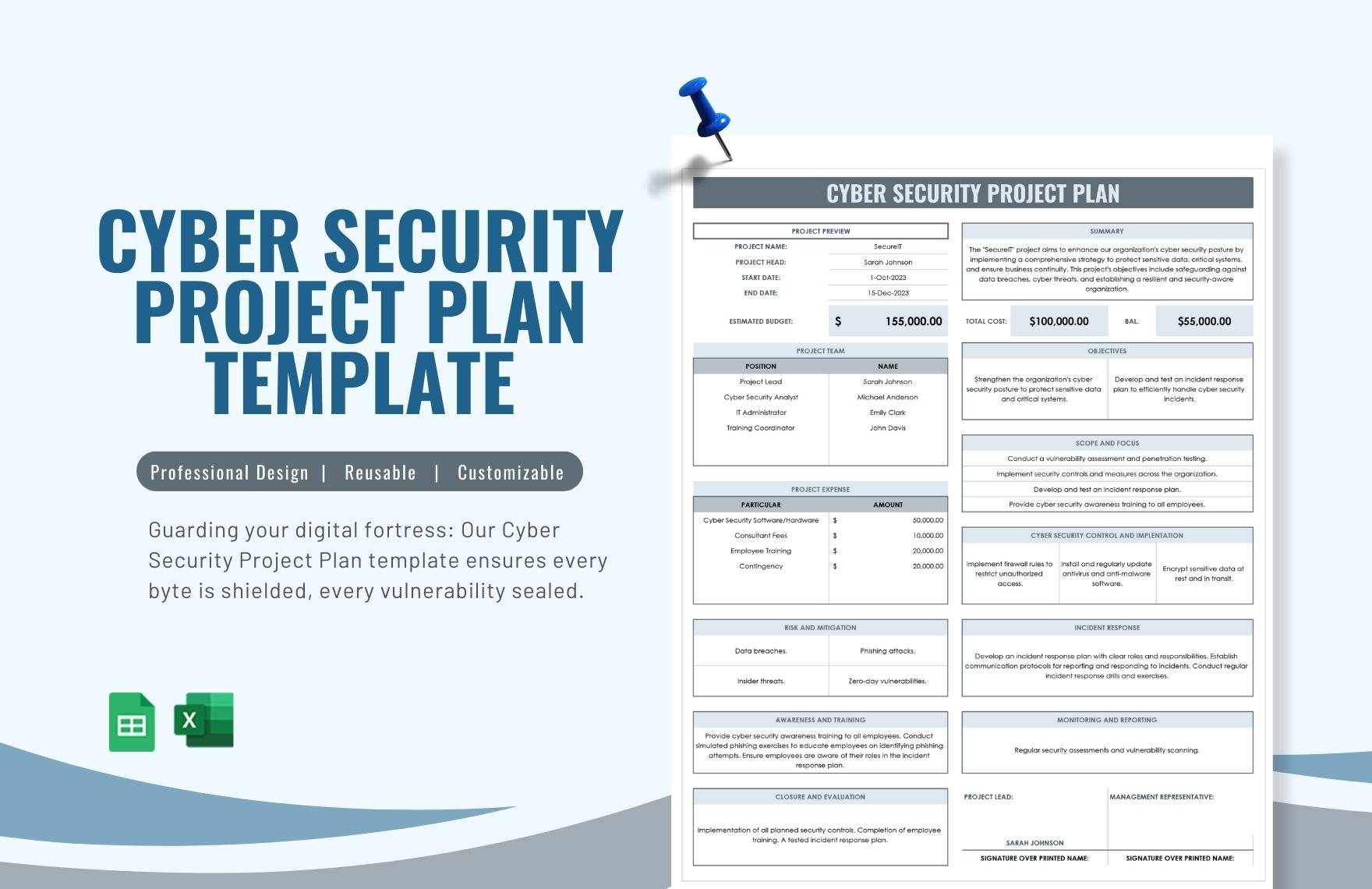
FREE Cyber Security Templates Download in Word Google Docs Excel

Cyber Security Ppt Template

Cyber Security Incident Response Powerpoint Ppt Template Bundles PPT Slide

Cyber Security Ppt Template prntbl concejomunicipaldechinu gov co

Cyber Security Ppt Template prntbl concejomunicipaldechinu gov co

Cyber Security Ppt Template prntbl concejomunicipaldechinu gov co

Cyber Security Ppt Template prntbl concejomunicipaldechinu gov co

Cyber Security Ppt Template prntbl concejomunicipaldechinu gov co

Cyber Security Ppt Template prntbl concejomunicipaldechinu gov co

Cyber Security PPT Theme SlideBazaar

Cyber Security Presentation Template for PowerPoint SlideModel
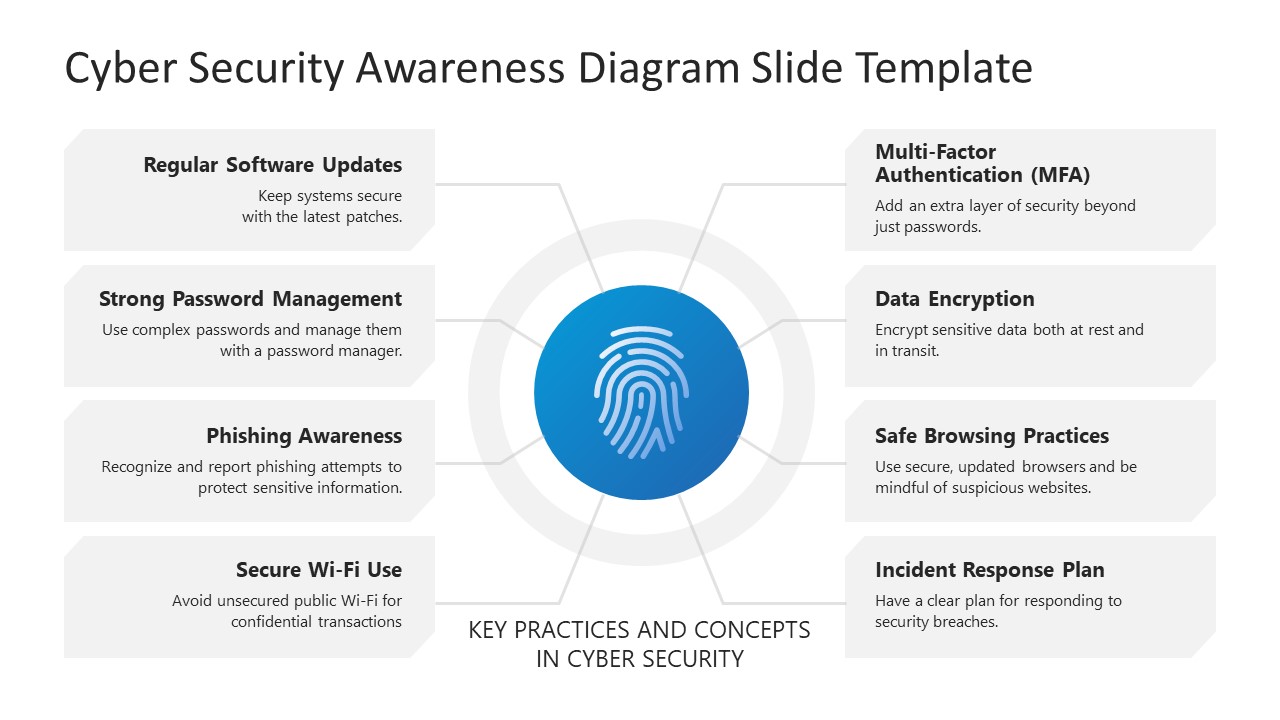
Cyber Security Awareness PowerPoint Template

Cyber Security Template For PowerPoint SlideBazaar

Cyber Security Template For PowerPoint SlideBazaar
Cyber Security Presentation Template

Cyber Security Presentation Template
Cyber Security Powerpoint Template Free

Cyber Security Presentation Template Just Free Slide

Cyber Security Template Powerpoint prntbl concejomunicipaldechinu gov co

Cyber Security Powerpoint Template
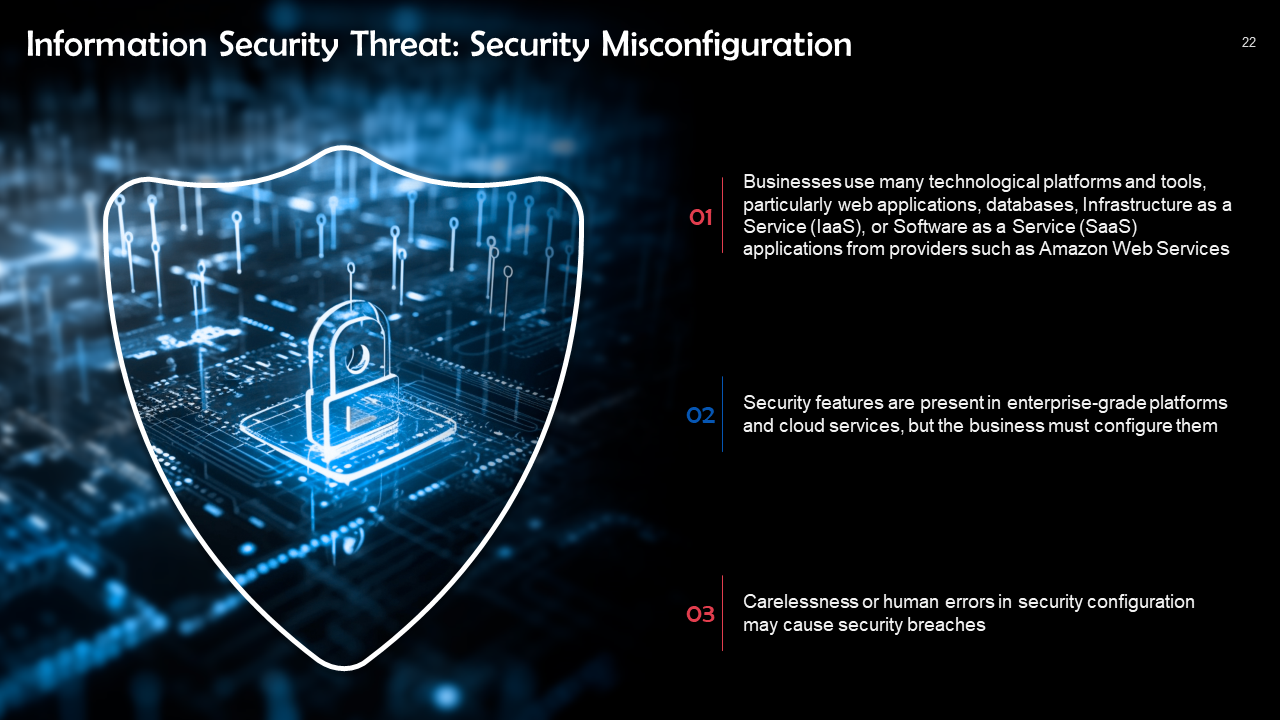
Cyber Security Ppt 2025 : Cybersecurity Threats 2025 Presentation XLYIJJ

Cyber Security Ppt 2025 : Cybersecurity Threats 2025 Presentation XLYIJJ
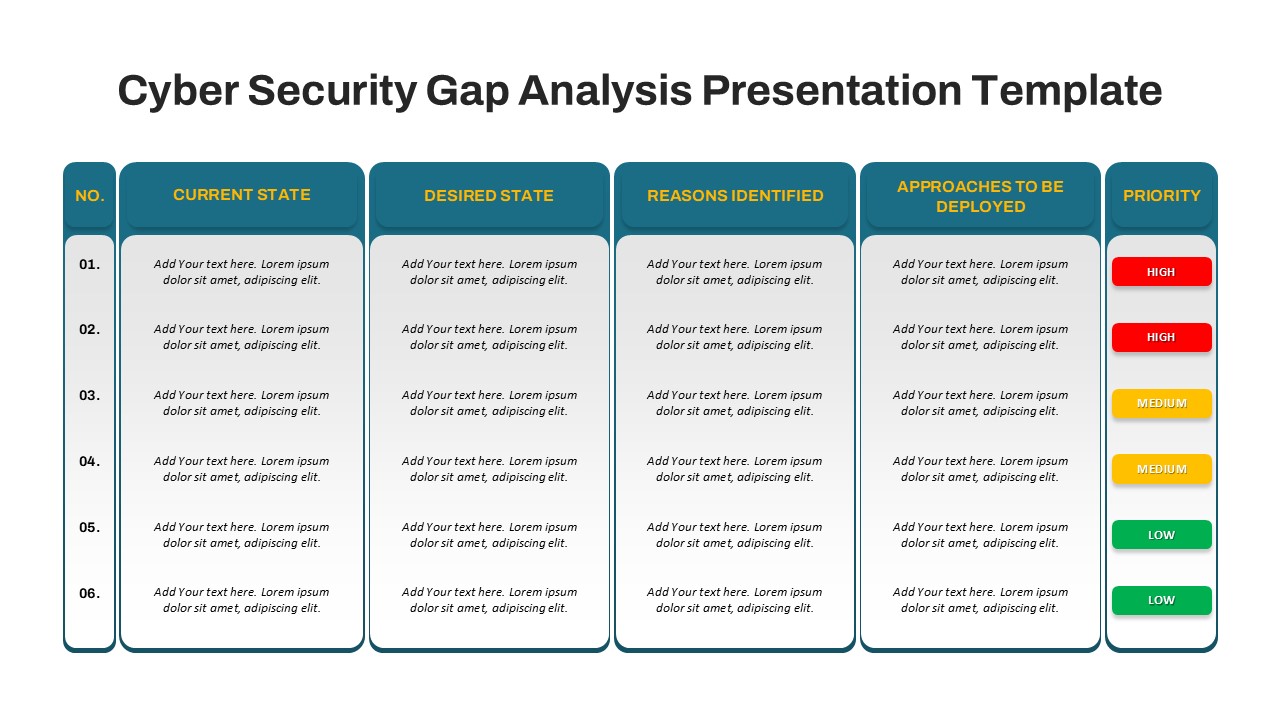
Design Thinking Process Template for PowerPoint and Google Slides

Unique Selling Proposition (USP) PowerPoint Template SlideKit