Cyber Security Plan Template For Small Business
Here are some of the images for Cyber Security Plan Template For Small Business that we found in our website database.

Cyber Security Plan Template For Small Business PDF

Small Business Cyber Security Plan Template Odd Culture
small business cyber security plan template PowerPoint PPT Templates

Cyber Security Business Plan Template (Free Download)

Cyber Security Business Plan Template (Free Download)

Cyber Security Plan Template For Small Business Method

Cyber Security Plan Template For Small Business

Cyber Security Plan Template For Small Business
Free Cyber Security Templates to Edit Online

Cyber Security Plan Template For Small Business

Free Small Business Cybersecurity Plan Template Download Here FocusIMS

Cyber Security Plan Template For Small Business

Cyber Security Plan Template For Small Business

Up Your Game with This Small Business Cyber Security Plan Template
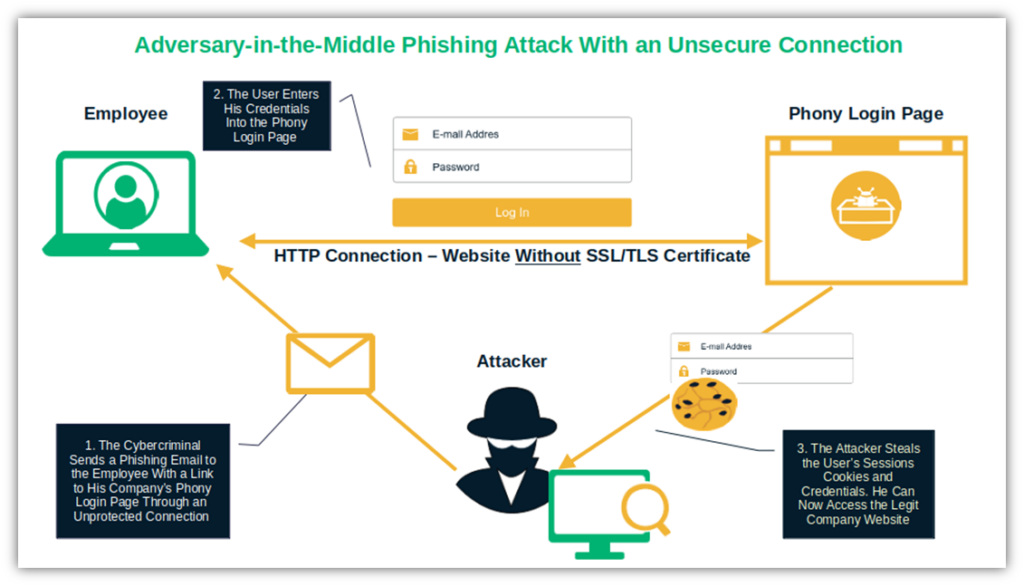
Up Your Game with This Small Business Cyber Security Plan Template
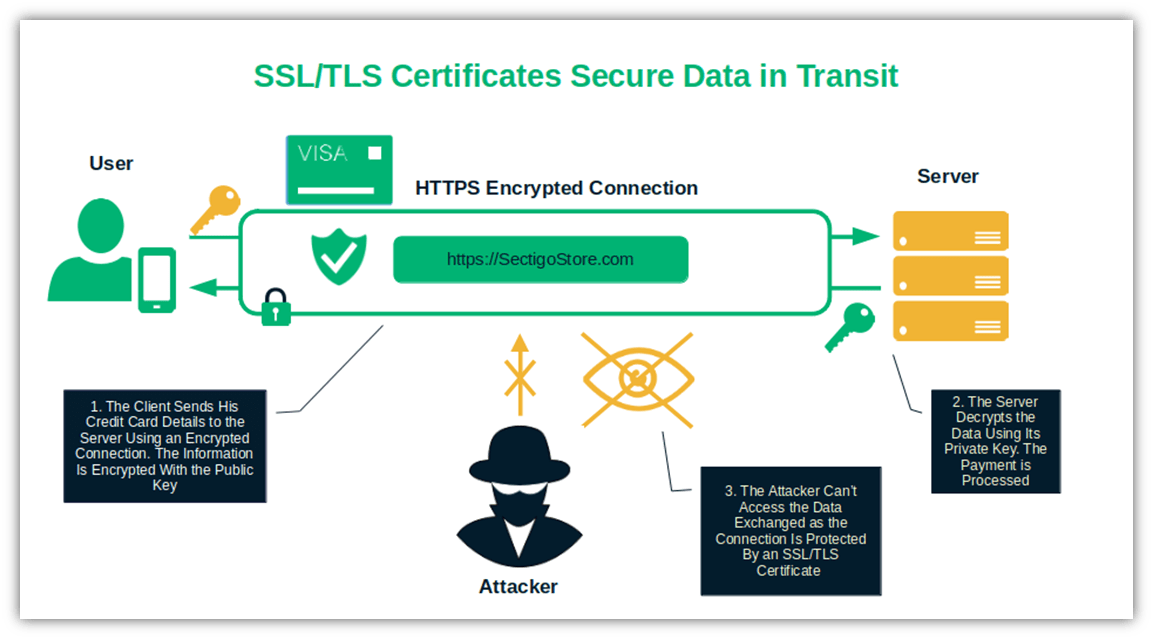
Up Your Game with This Small Business Cyber Security Plan Template
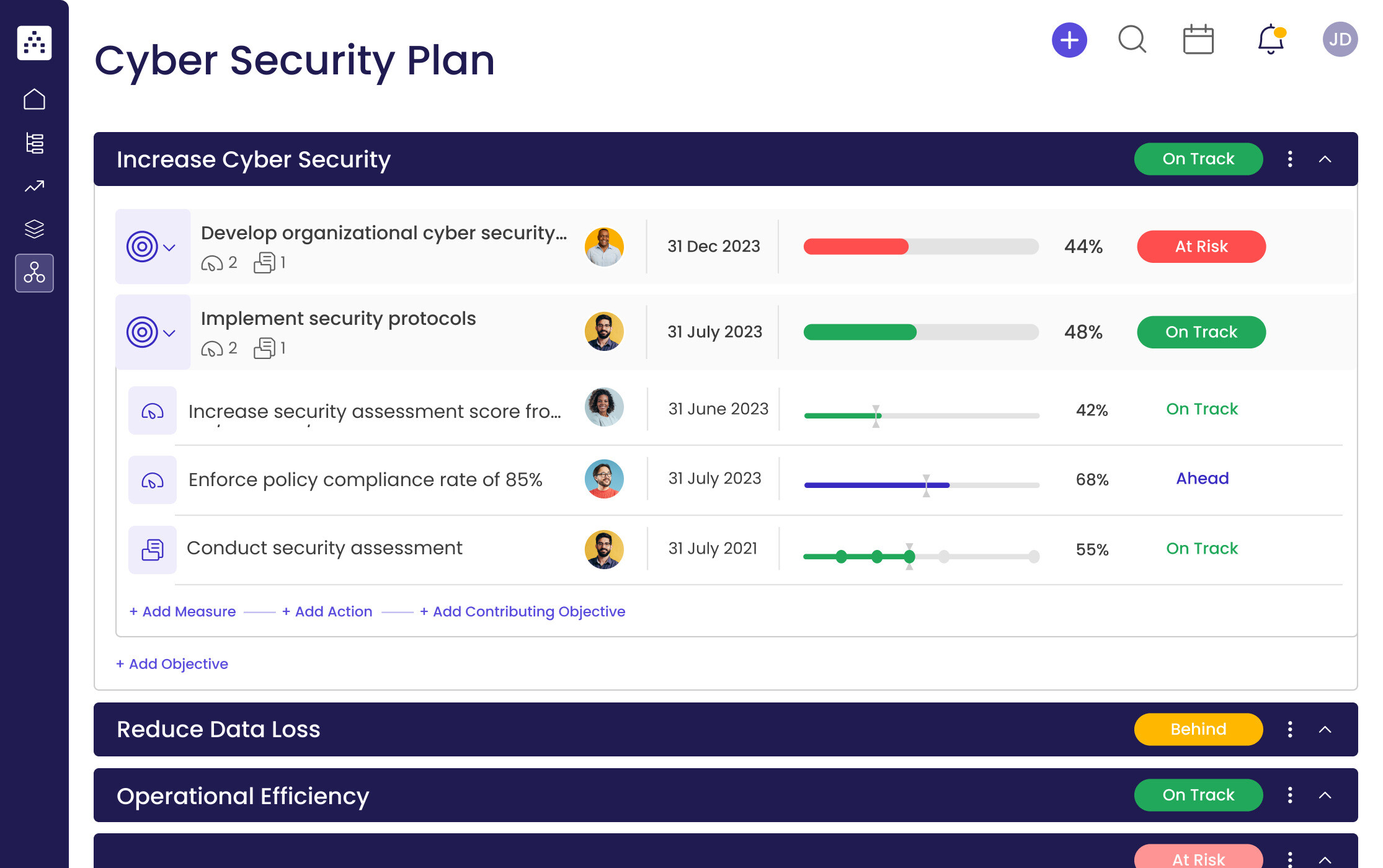
Cyber Security Plan Template
Up Your Game with This Small Business Cyber Security Plan Template

Cyber Security Plan Template For Small Business

Cyber Security Plan Template For Small Business prntbl
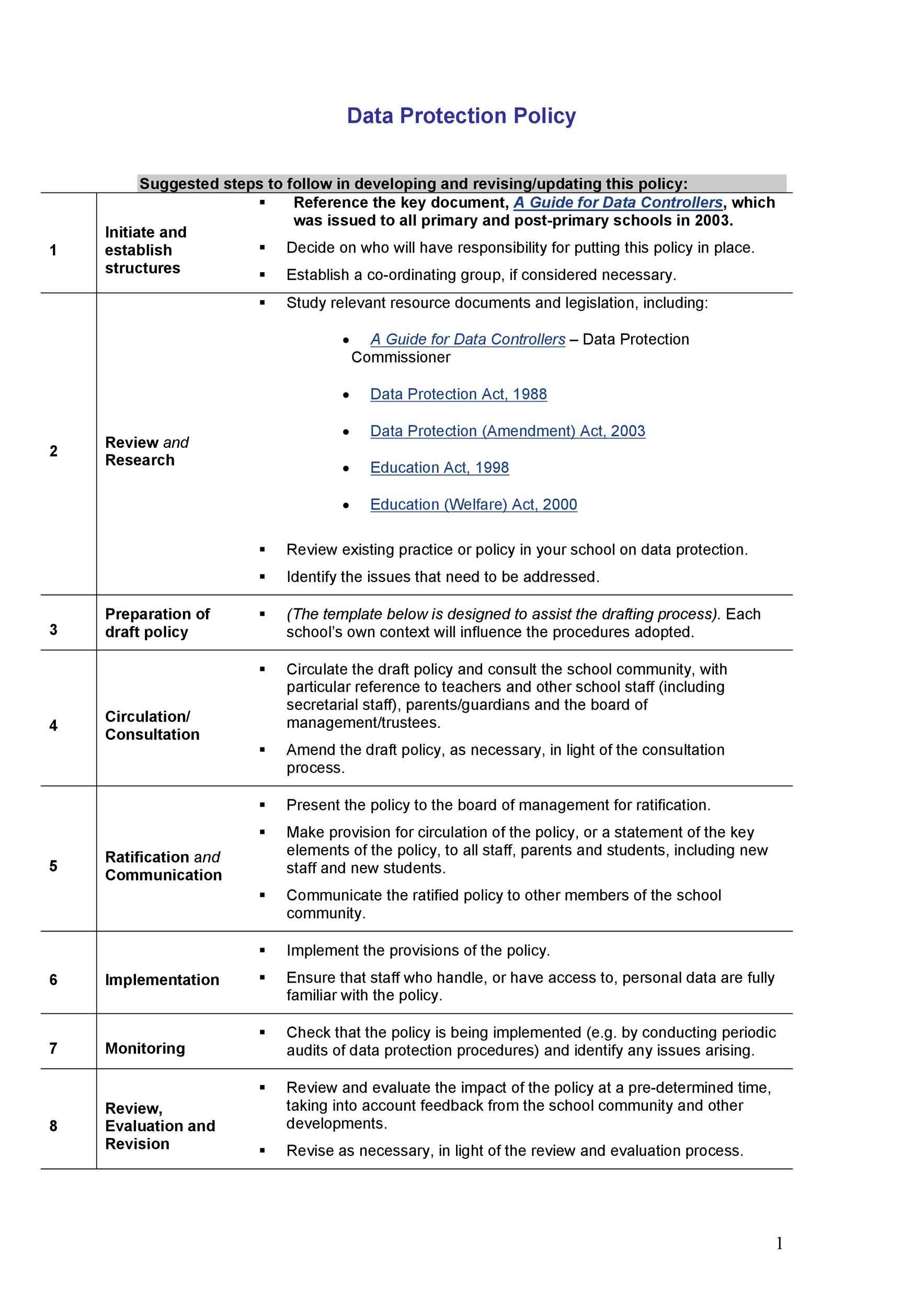
Cybersecurity Plan Template

Cybersecurity Plan Template

Cyber Security PowerPoint Template SlideBazaar
Cybersecurity Plan Template

Cyber Security Plan Template

Cyber Security Plan Template
Cyber Security Policy Template

SBA Business Plan Template in PDF Word Google Docs Download
10 Security Plan Templates Sample Templates

Cyber Security Implementation Plan Template

Cyber Security Management Plan Template
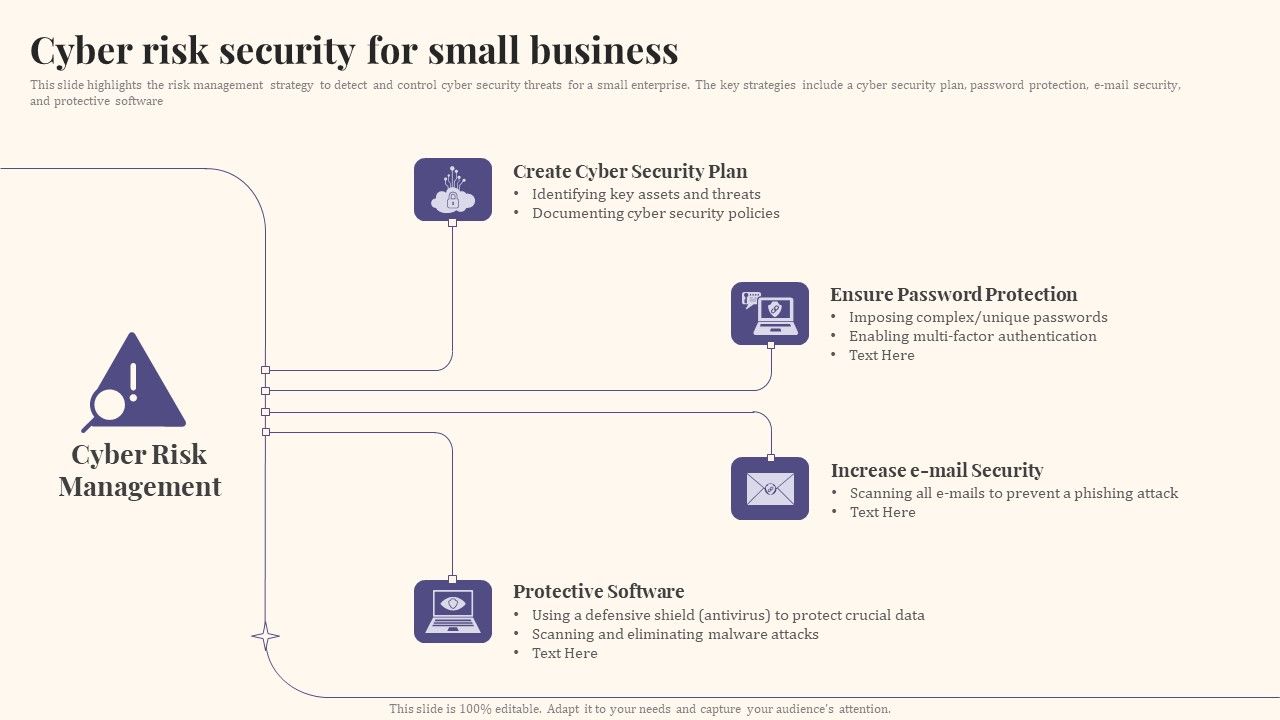
Cyber Risk Security For Small Business Presentation Graphics

How to build an effective small business cyber security plan: step by

Editable Security Policy Templates in Word to Download
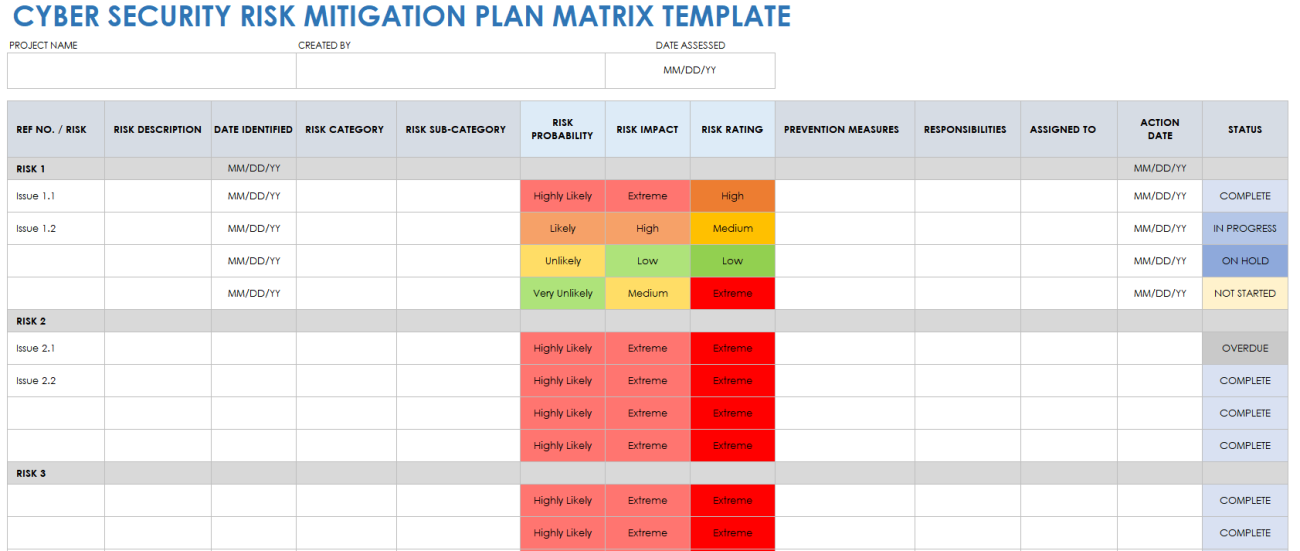
Cyber Security Risk Management Plan Template prntbl

Cyber Security Risk Management Plan Template prntbl

Security Plan Template

Cyber Security Plan Template Venngage

Database Security Plan Template

Information Security Plan Template
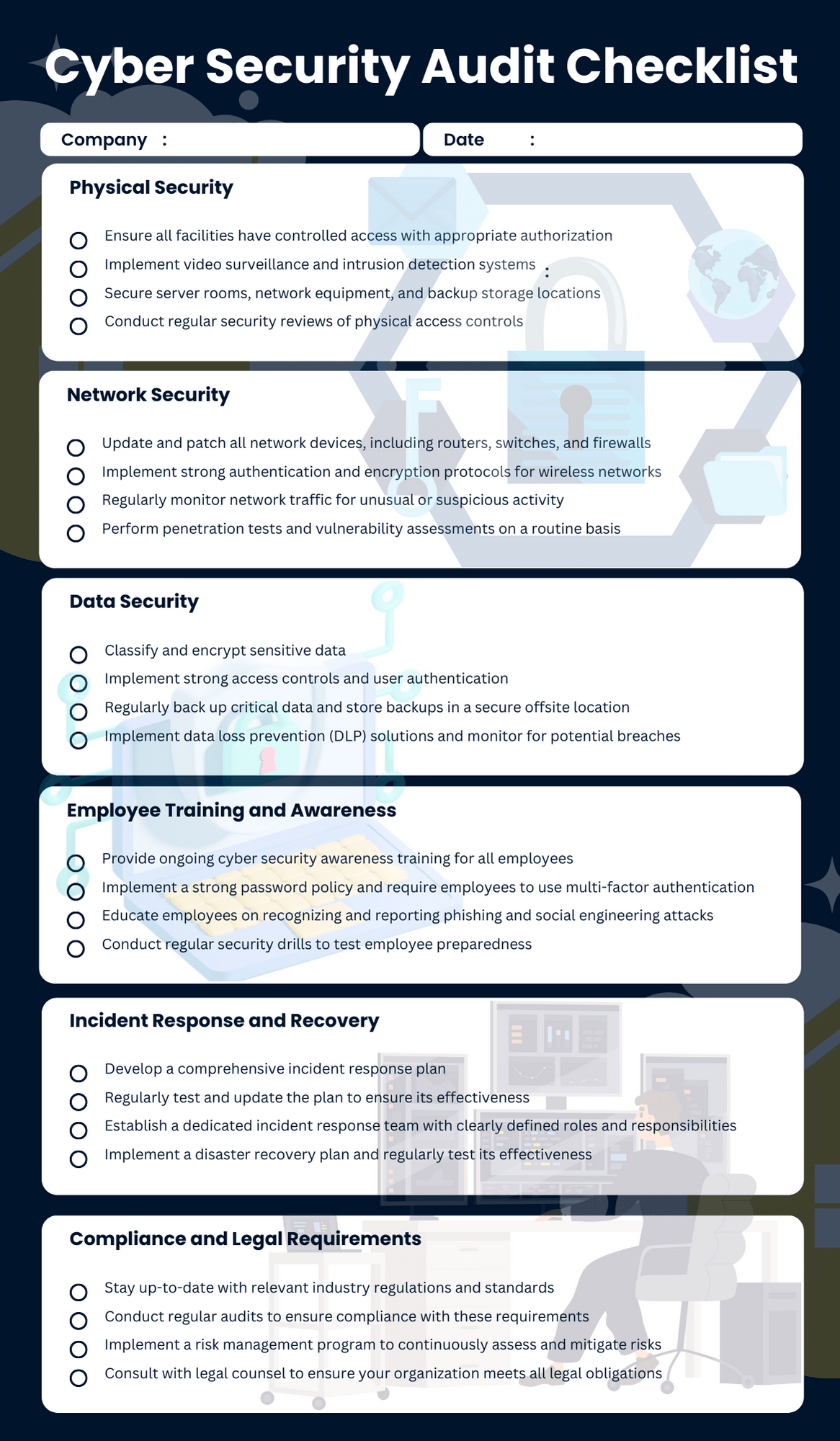
Cyber Security Audit Template prntbl concejomunicipaldechinu gov co
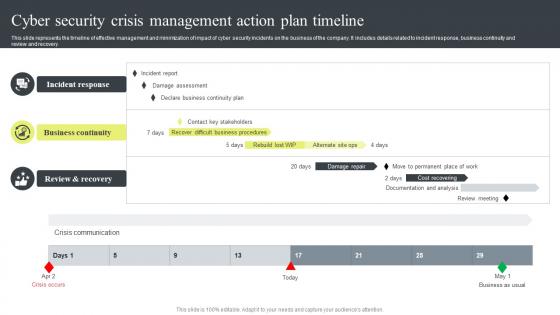
Cyber Security Plan Slide Team
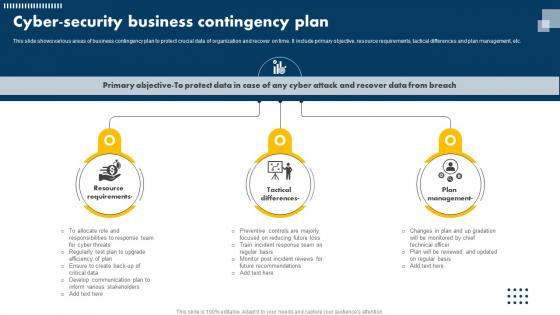
Cyber Security Plan Slide Team

Written Security Plan Template

Cyber Security Policy template Real World Help Centre
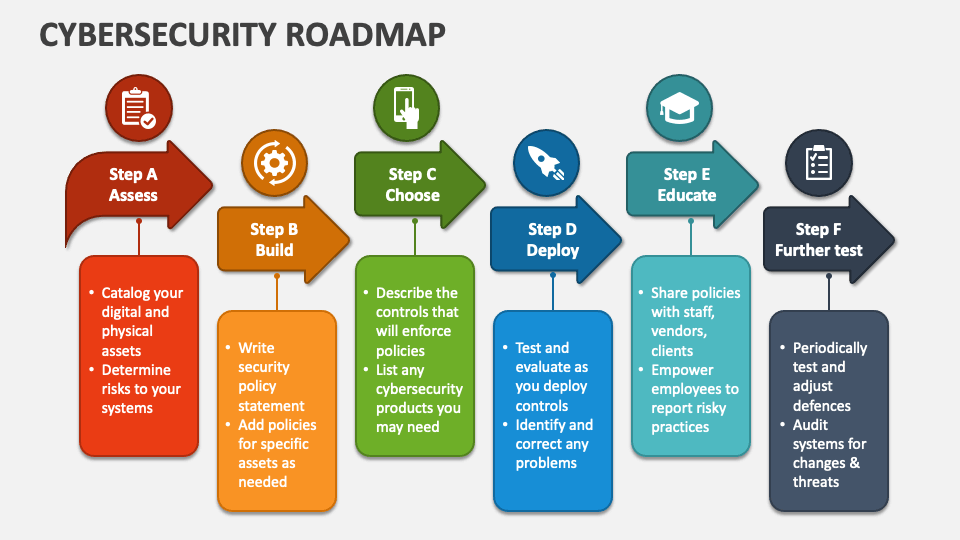
Cybersecurity Strategy Template prntbl concejomunicipaldechinu gov co

Information Security Policy Template For Small Business prntbl

Information Security Plan Template

Free Safety Plan Template to Edit Online

%%title%%

Cyber Security Planning Guide

Top 10 Layered Security PowerPoint Presentation Templates in 2024
UE5渲染编程 间接光计算 知乎