Cyber Security Incident Report Template
Here are some of the images for Cyber Security Incident Report Template that we found in our website database.
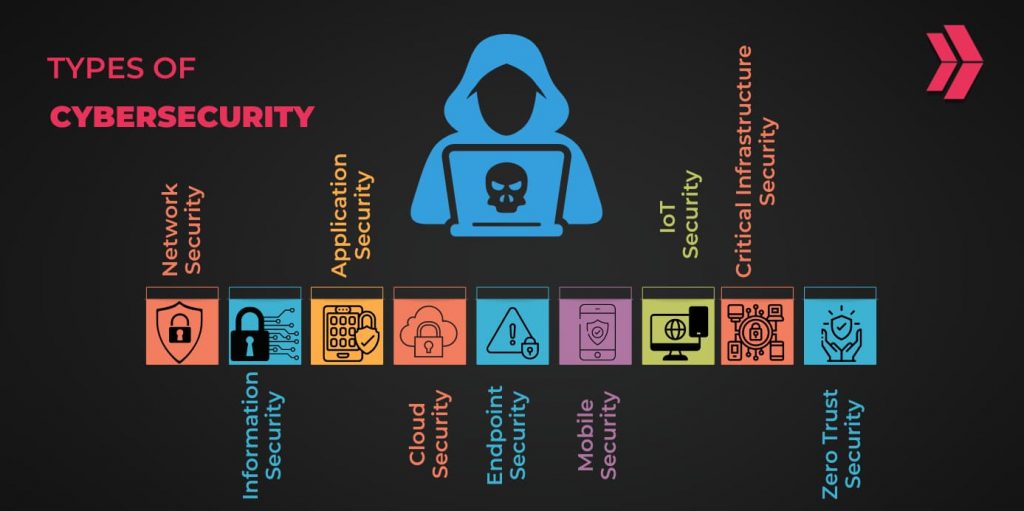
Types Of Cybersecurity: A Comprehensive Overview

SAFER INTERNET Cyberpolicy NASK

teiss Cyber Skills Gap Internal threats: the importance of culture

Helping to shape the RMIT Centre for Cyber Security Research and

900 Free Cybersecurity Certifications Cybersecurity Images Pixabay

2300x1000 Resolution Cybersecurity Core 2300x1000 Resolution Wallpaper

K Cyber

Cyberattacks can be prevented: Try some of these established practices

The Future of Cybersecurity: Trends and Predictions for 2023 and Beyond

Five Cyber Security Trends to Watch for in 2025 Flood IT Support

Cyber Security Protocols That You Should Know Logsign

Cyber Threats

Digital Technologies and Cybersecurity in Naval Applications Thales Group

What Is Cybersecurity? Forage

Cybersecurity Plan: 3 Keys for CISOs Trend Micro (US)
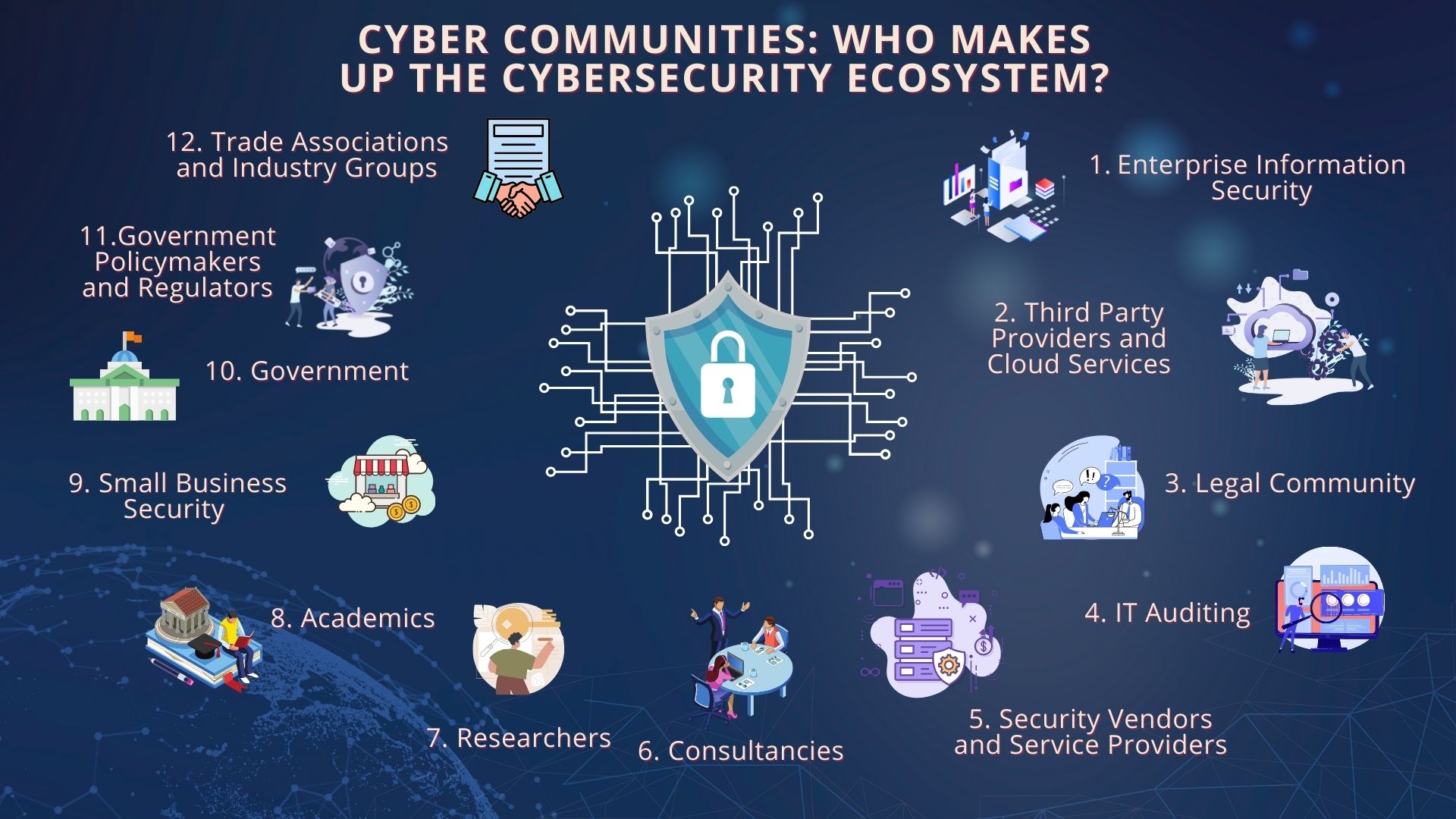
Cybersecurity Ecosystem Strategy Of Security vrogue co

Cyber Attack Wallpaper

Cybersecurity Wallpaper

How To Get Started In Cyber Security With No Experience

Cyber Security Fraud Whistleblower Law Collaborative

How AI Creates a Cybersecurity Force Multiplier Identifying and

Aviation Cybersecurity Register Cyber Senate Leaders in Cybersecurity

Tamil Nadu tender for creating cyber crime labs: what you should know

أمن سيبراني ـ المخاطر وتدابير وسياسات أوروبية (ملف) المركز الأوروبي

40 Free Cybersecurity Vpn Photos Pixabay

How AI is Revolutionizing Cybersecurity

Brace Yourself Cybersecurity Threats Are On The Rise

ENISA: Cyber Attacks Becoming More Sophisticated CDE Almería Centro

Types of Cybersecurity Attacks and How to Prevent Them

Siemens USA launches cybersecurity analytics lab to help protect

atodorov org you can logoff but you can never leave

Download Cyber Security Is A Key To Your Business Wallpapers com

Underwriters Predict Continued Growth of Cyber Risks in 2024

Personal data of over 3 million US populace leaks in a data breach

What is a Cybersecurity Audit and Why is it Important? EasyDMARC

Cybersecurity Architecture Approaches Overview Cybersecurity Memo

Pure play cybersecurity firms in your backyard CSO Online

Cyber security concept with padlock on blue background 3D rendering

Cyber Security: saiba o que faz um profissional de cibersegurança

Australia s Latitude Group and IPH Hit by Cyber Attacks Continuing

BroadBand Nation: Cybersecurity Career Pathway (INFOGRAPHIC)

Cyber Security Wallpapers Wallpaper Cave

New cybersecurity technology 2022 Security Magazine

Download Cyber Network Technology Royalty Free Stock Illustration

Cyber Desktop Wallpapers Top Free Cyber Desktop Backgrounds

Cyber World Wallpapers Top Free Cyber World Backgrounds WallpaperAccess

Cabinet to Approve First #39 National Cyber Security Policy 2021 #39 today

What is Cybersecurity? Types Threats and Cyber Safety Tips

Russia develops an AI Cyber Threat Tool to put a jolt in US democracy

Why You Should Choose Cyber Security As A Specialization In Computer

200 Cyber Backgrounds Wallpapers com
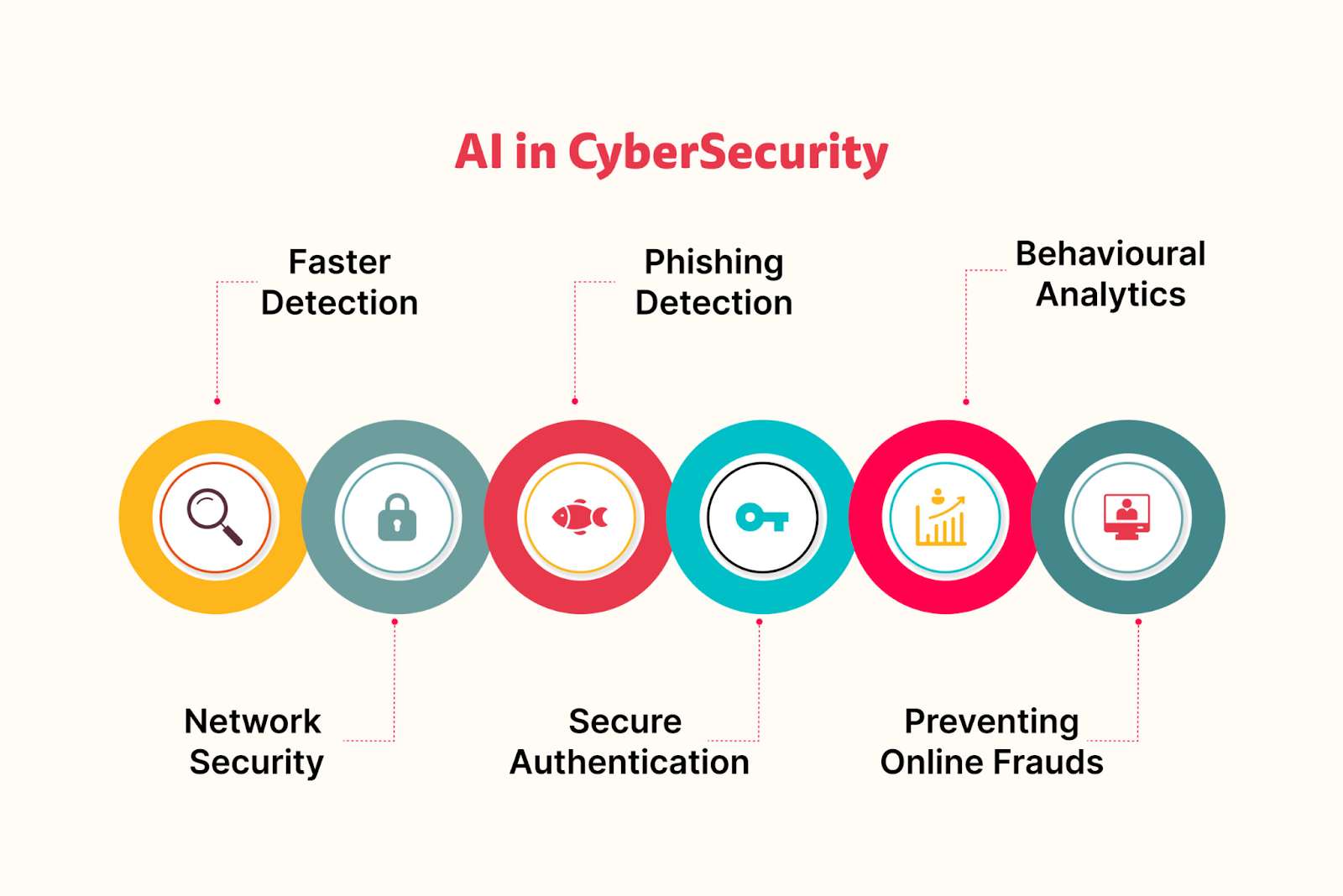
Using Ai To Enhance Cybersecurity

Importance of Cyber Security in Business AeoLogic Blog
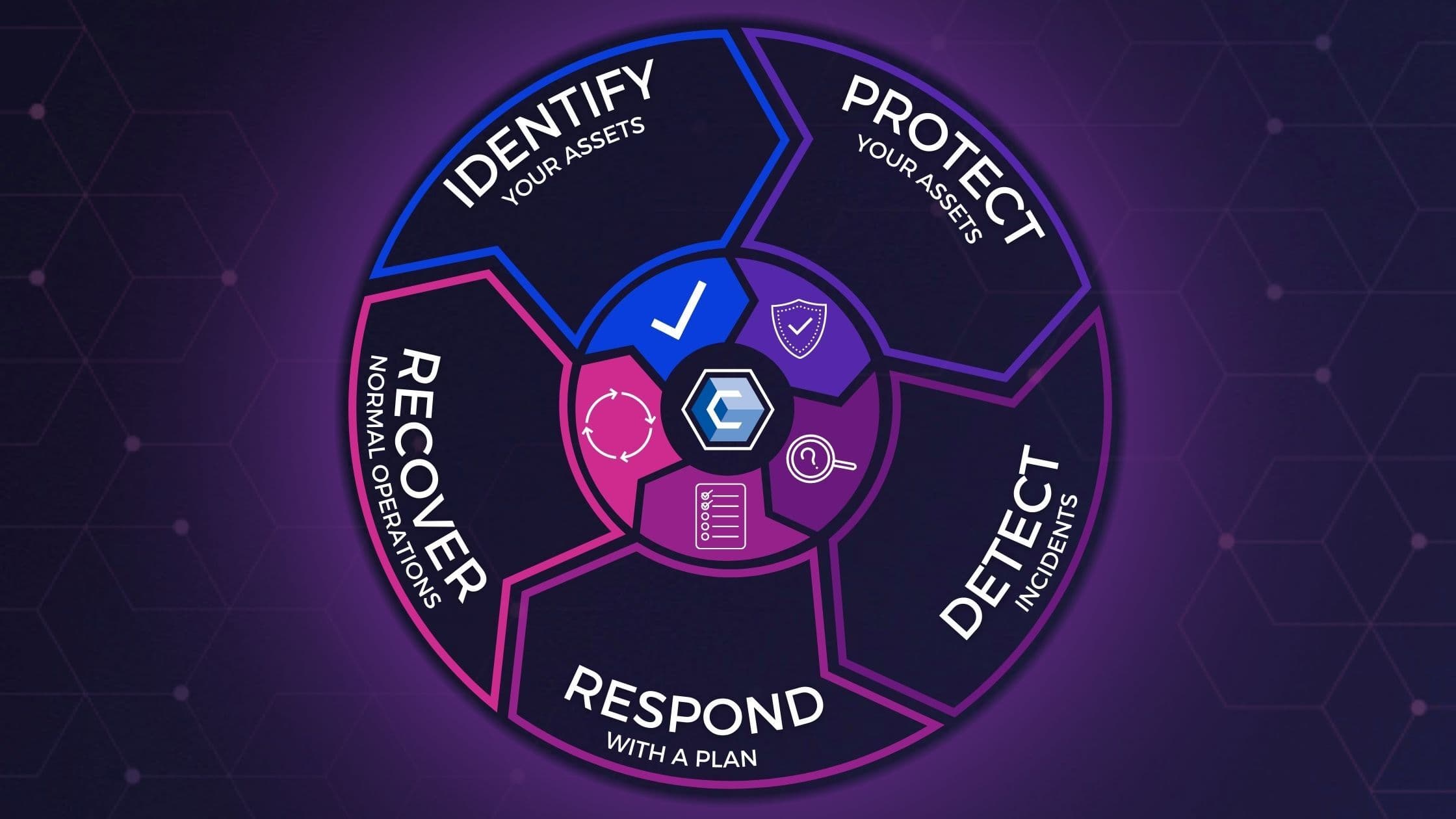
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES
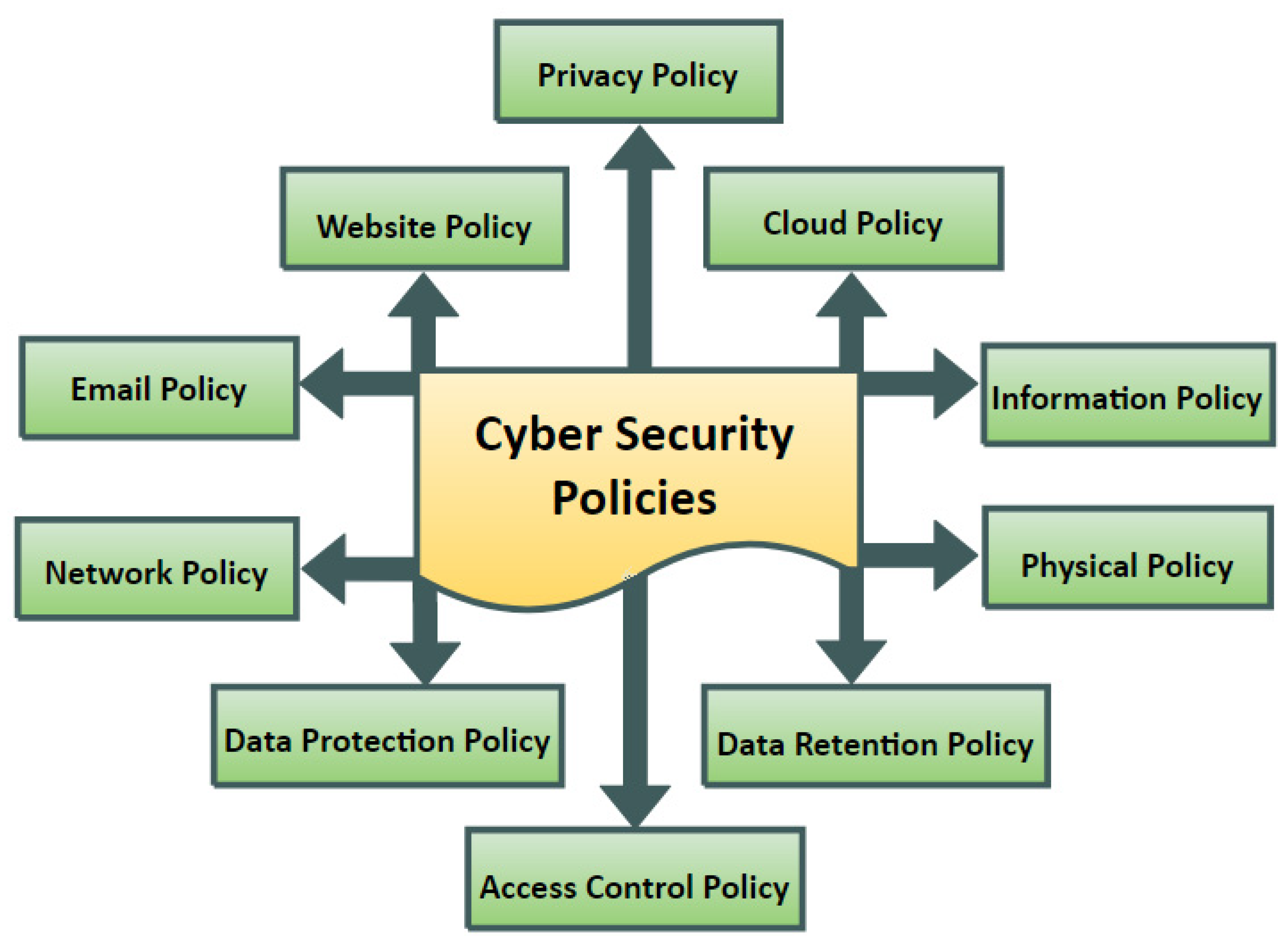
Sensors Free Full Text Cybersecurity Enterprises Policies: A

What Is Cybersecurity? Gartner

Cybersecurity Background Images in IT Stable Diffusion Online
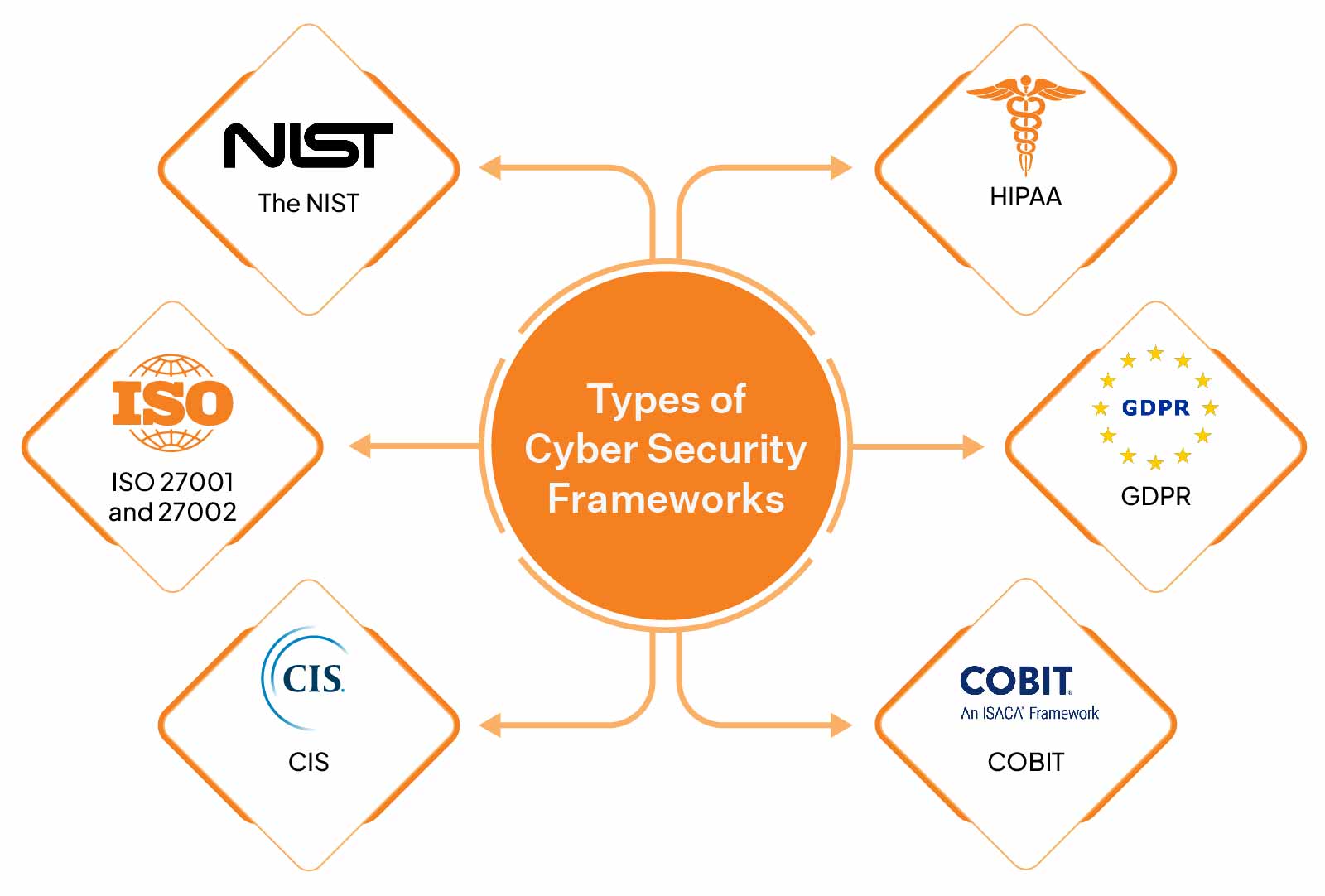
List of Top 6 Cybersecurity Frameworks Sprinto