Cyber Law Certificate Course
Here are some of the images for Cyber Law Certificate Course that we found in our website database.

Certificate Course on Cyber Law Legal Research And Analysis

Certificate Course on Cyber Law Legal Research And Analysis

Cyber Law Certificate Course Online UniAthena uniathena on Tumblr

Certificate Course In Cyber Security Fundamentals

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co
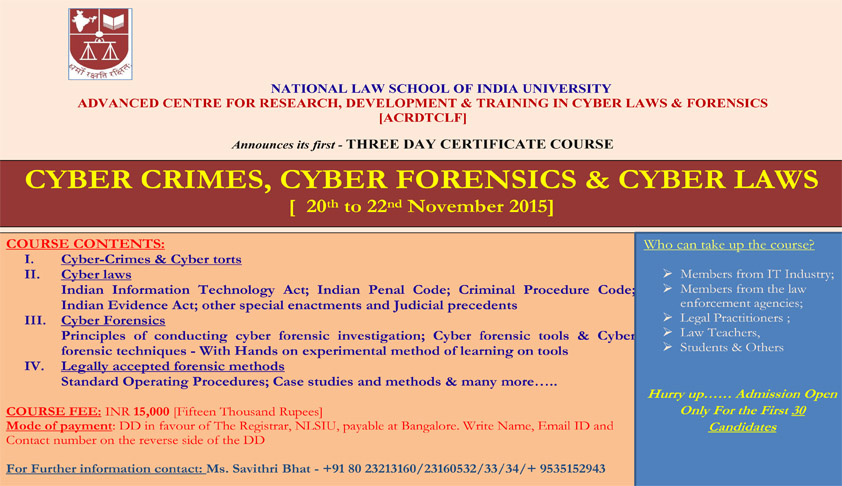
Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Cyber Law Certificate Course prntbl concejomunicipaldechinu gov co

Certificate Course On Cyber Law (Basic) Batch XVII : Register By March

INTERNATIONAL CYBERCRIME LAW CERTIFICATION COURSE Cyberlaw University

Shubhra on LinkedIn: Completed Cyber Law certificate course

Ramaiah College of Law P G Diploma in Cyber Law IT Law

Environmental Law Certificate Legal Issues Research Course

ADVANCED CERTIFICATE COURSE ON CYBER LAW BY PATH LEXIS AND LEGAL FUMES

Cyber Law Course: Specializations Career Options and Job Prospects

CERTIFICATE COURSE ON AI AND LAW Legal Research And Analysis

CERTIFICATE COURSE ON BANKING AND FINANCE LAW Legal Research And Analysis
Cyber Law course Everything you need to know about this course

Cyber Law Certificate Course Batch 4 Now Open for Enrolment by Legal

Diploma in Cyber Law course by Asian School of Cyber Laws

Online Cyber Law Certificate Course PDF Cyberspace Computer Security

Diploma in Cyber Law

Certificate Course on Labour Laws

Free Online Certificate Course on Intellectual Property Rights by E

Certificate Course on Labour Laws

Online Legal Research Course with Certificate Courses in Law

Career Tips: साल भर में जानें साइबर लॉ ऑनलाइन अपराधों को दें चुनौती

Advanced Certificate Course on INSOLVENCY AND BANKRUPTCY CODE Legal

Certificate Course on Women #39 s Rights

Certificate Course on Women #39 s Rights

Online Legal Research Course Start Boost Your Law Skills

Certificate Course on the Constitution of India Legal Research And

सर्टिफिकेट इन साइबर लॉ (Certificate Course in Cyber Law After 12th

Best Legal Online Certificate Course and Certificate Program

Best Legal Online Certificate Course and Certificate Program

Best Legal Online Certificate Course and Certificate Program

Law

Online Certificate Course On Contract Drafting Legal Research And

Karun Sanjaya

Submission Guidelines Legal Research And Analysis

CALL FOR PAPERS Legal Research And Analysis

Online Certificate Course on Legal Drafting Legal Research And Analysis

Online Certificate Course on Legal Drafting Legal Research And Analysis

Online Certificate Course on Legal Drafting Legal Research And Analysis

Upholding Human Rights: Latest Violations and Advocacy Efforts

Environmental Crimes and Legal Provisions Legal Research And Analysis

General Principles of Drafting

Environmental Crimes and Legal Provisions Legal Research And Analysis

Comprehending the Municipal Solid Waste Management in India through the

LEGAL FRAMEWORKS FOR REFUGEE PROTECTION IN INDIA: A FOCUS ON VULNERABLE

LEGAL FRAMEWORKS FOR REFUGEE PROTECTION IN INDIA: A FOCUS ON VULNERABLE
Aparajita Bill Road to Justice Challenges and Opportunities

Copyright Infringement in Digital Age: Challenge Solution Legal

Copyright Infringement in Digital Age: Challenge Solution Legal

Beyond Legislation: Evaluating the Efficacy of the PWDVA 2005 Legal