Cyber Incident Response Report Template
Here are some of the images for Cyber Incident Response Report Template that we found in our website database.

What Does the Cybersecurity Landscape Look Like in 2023? BusinessWest

teiss Insider Threat Internal threats: the importance of culture to

A Beginner #39 s Guide to AI in Cybersecurity: What You Need to Know

Cyber Threats
Unlocking The Future Of Cybersecurity And Ai

Cyber Security Technology And Online Data Protection In An Innov

Ai On Cyber Security

10 000 Free Cyber Security Cyber Security Images Pixabay

3980x4480 Resolution Cybersecurity Core 3980x4480 Resolution Wallpaper

What Is Cybersecurity? Forage
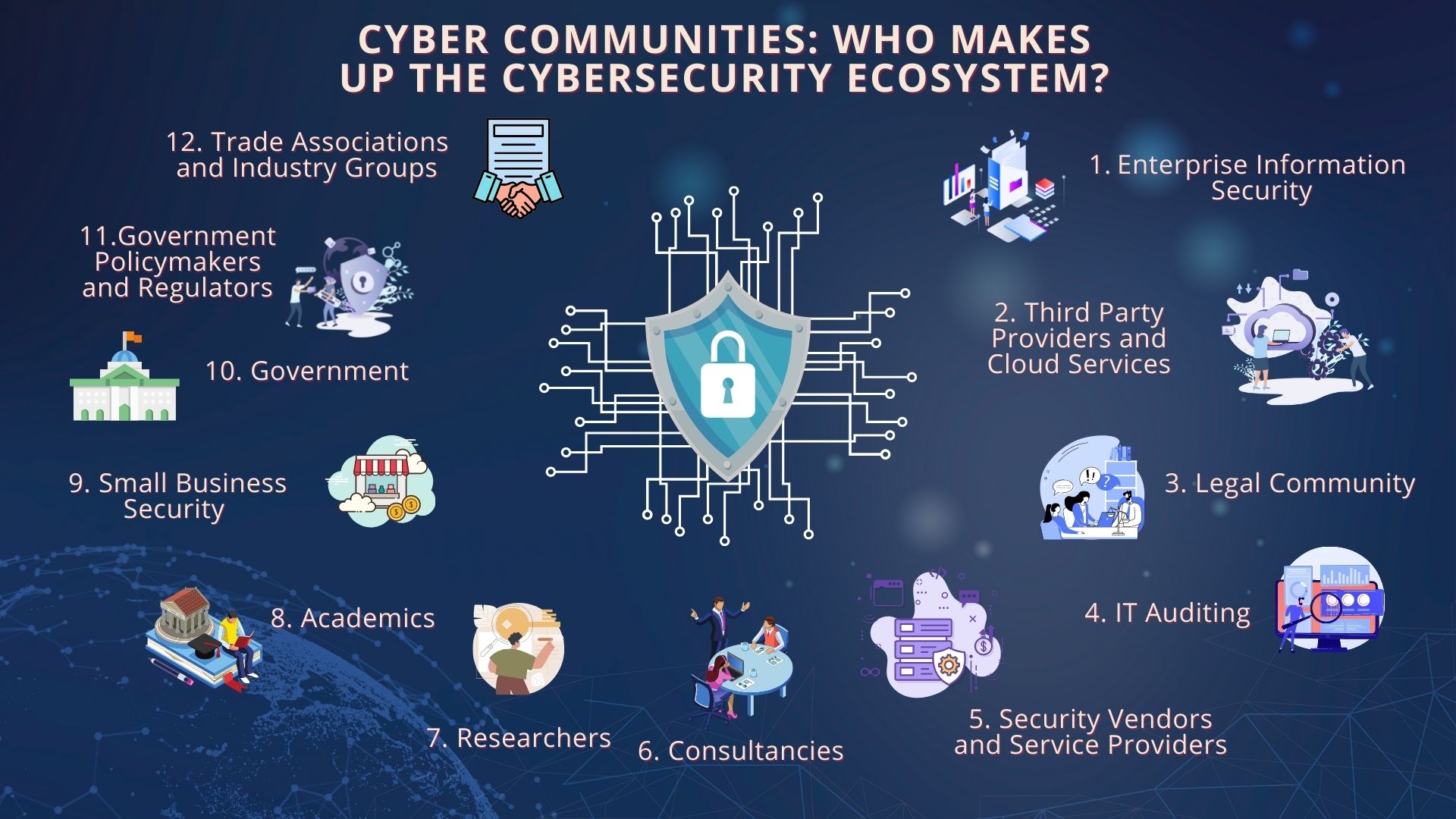
Cybersecurity Ecosystem: 12 Cyber Essential Communities

7 Cybersecurity Threat Trends in 2022

What Is Ai Cybersecurity
Research Note: SentinelOne Autonomous Cybersecurity Announcements

Cyber Security: saiba o que faz um profissional de cibersegurança

Pengertian dan Manfaat Cyber Security untuk Keamanan Data Bisnis di

Why Should Cybersecurity Be Taught In Schools?
.jpg)
Cybersecurity

100 Cyber Security Wallpapers Wallpapers com

The Best CVE Sources and Cyber Security News: Stay Informed and Secure

Who #39 s Behind the Screen? A Comprehensive Guide to Cyber Threat Actors

Download Cyber Security Is A Key To Your Business Wallpapers com

Peris ai Cybersecurity on LinkedIn: Cyber Attacks on Critical

Cybersecurity

Is Cyber Security Hard to Learn? How to Get Started in 2023

6 Tips for Implementing Cybersecurity Measures in Your Project

4 000 Free Cyber Incident Response Cyber Images Pixabay

Potential Risks for Not Providing Regular Cybersecurity Training

Cyber Security and Segregation of Duties Security Boulevard

Insights: Top 8 cyber travel tips to keep in mind

Zurich and Barrier Networks partner to Offer Enterprise Cyber Risk

Cyber Security Intern Salary

BroadBand Nation: Cybersecurity Career Pathway (INFOGRAPHIC)

Enhance Security with KnowBe4 #39 s PhishER Newtech

Cyber

Pakar Ungkap Serangan Cyber Jadi Ruang Perang Modern Aktual com

types of cybercrime in malaysia Ian Mills

45 Cybersecurity Statistics and Facts 2025

teiss News China Taiwan trade accusations over cyberattacks

10 ways to protect your business from cyber attacks

Cyber security tech globe concept 1268575 Vector Art at Vecteezy

New cybersecurity technology 2022 Security Magazine

UNK Cybersecurity Team wins regional builds reputation as top training

Five Ways To Protect Your Company Against Cyber Attacks

Cyber security in software development: 12 outsourcing tips

Cabinet to Approve First #39 National Cyber Security Policy 2021 #39 today

What Is Cybersecurity? Gartner
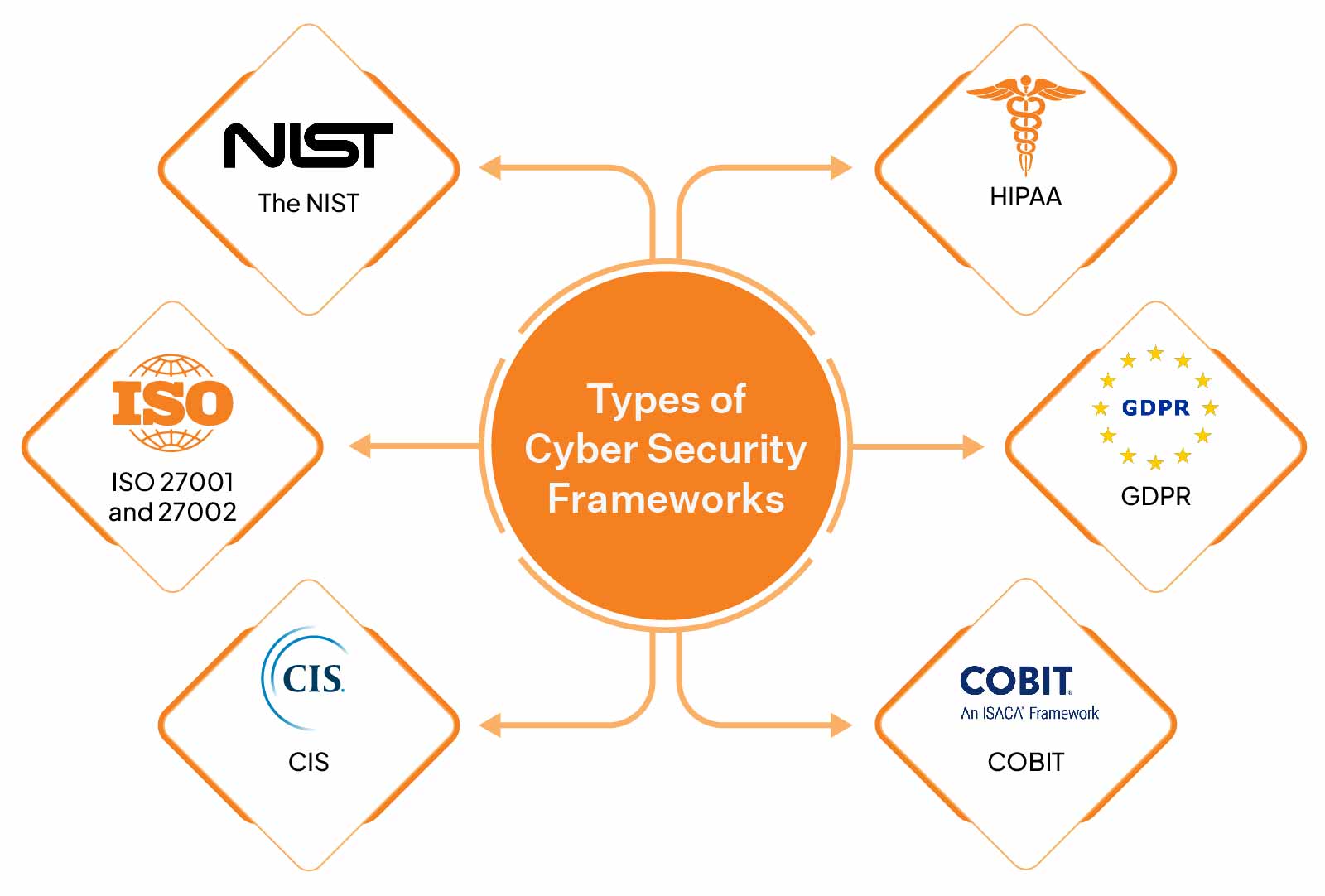
List of Top 6 Cybersecurity Frameworks Sprinto

Car Selling Phishing Lure by Threat Actor

What is GLBA Compliance? Key Requirements and Concepts BD Emerson

Types of Cyber Security Threats NEIT

¿Qué es el Cybercovid y cómo NETEC Noticias y blog

How Businesses Can Prepare For and Ultimately Prevent Cyber Attacks
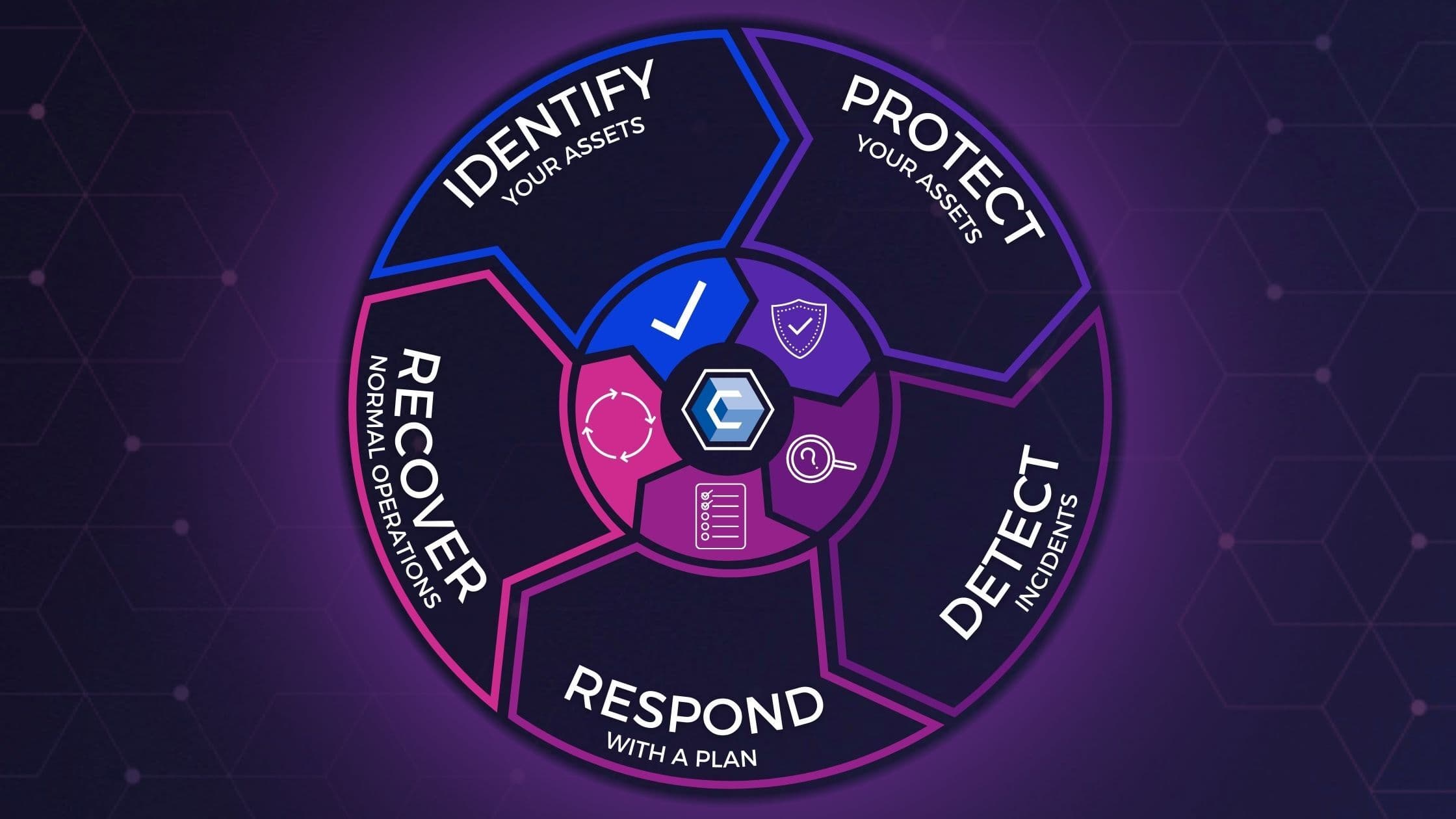
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

TechBytes Blog

U S Security Agencies Issue Advisory on Russian Cyber Attacks on

Understanding the 3 Phases of Cybersecurity Architecture Ardoq

Security Deposit Refund Letter Template prntbl

Commvault Advances Cyber Resilience with Cleanroom Recovery

Navigating the Virtual Crime Universe arch magazine