Certificate Management Best Practices
Here are some of the images for Certificate Management Best Practices that we found in our website database.

Certificate Management Best Practices

5 Certificate Management Best Practices You Need to Know
5 Certificate Management Best Practices You Need to Know

5 Certificate Management Best Practices You Need to Know
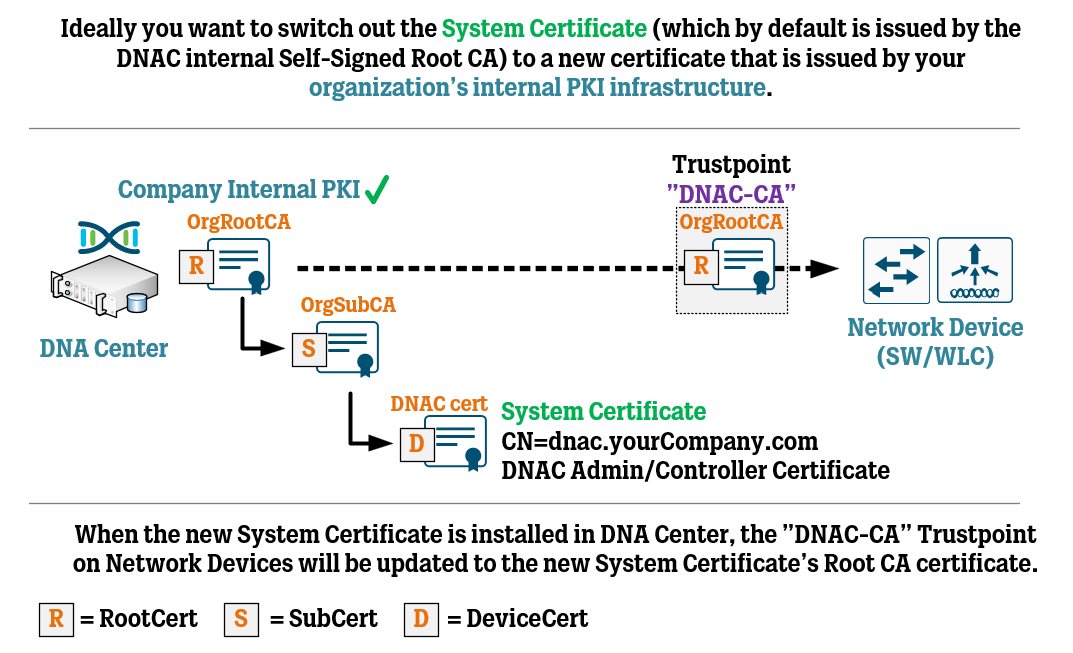
Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI
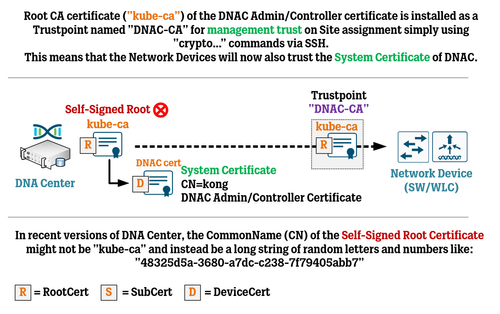
Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI
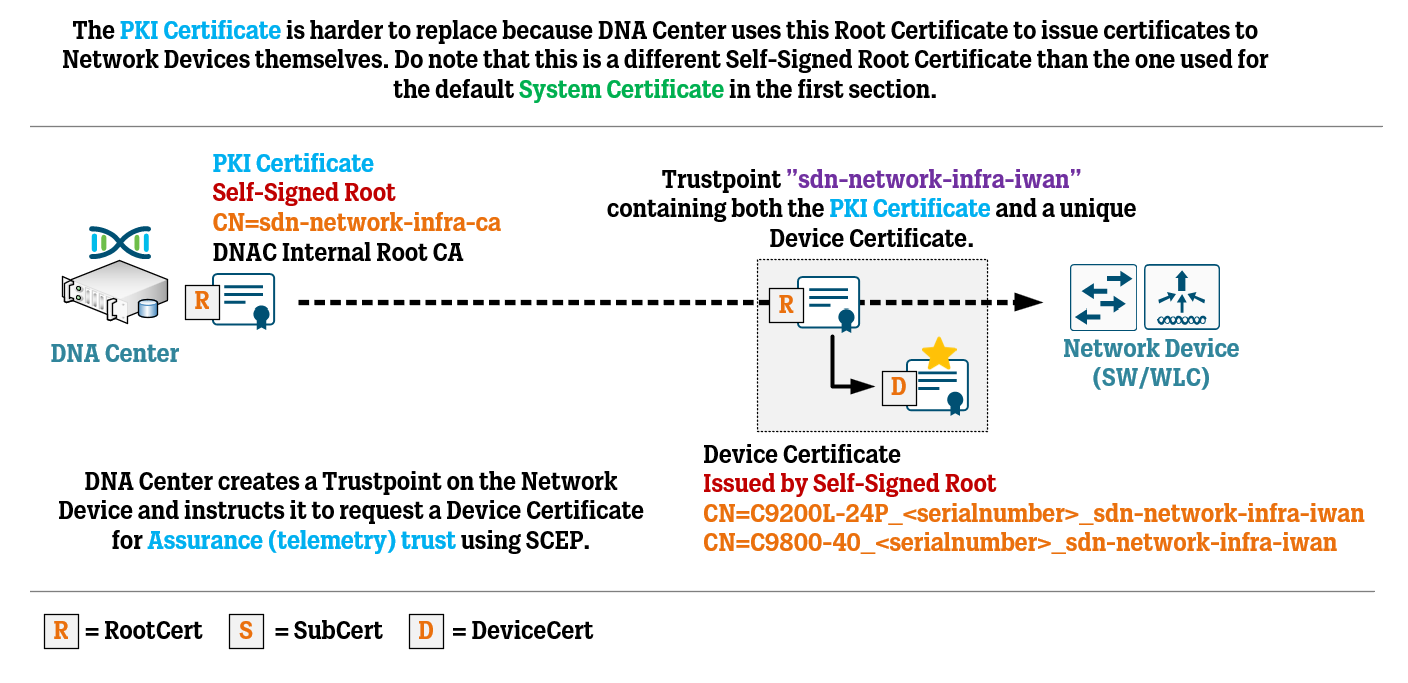
Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI

Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI
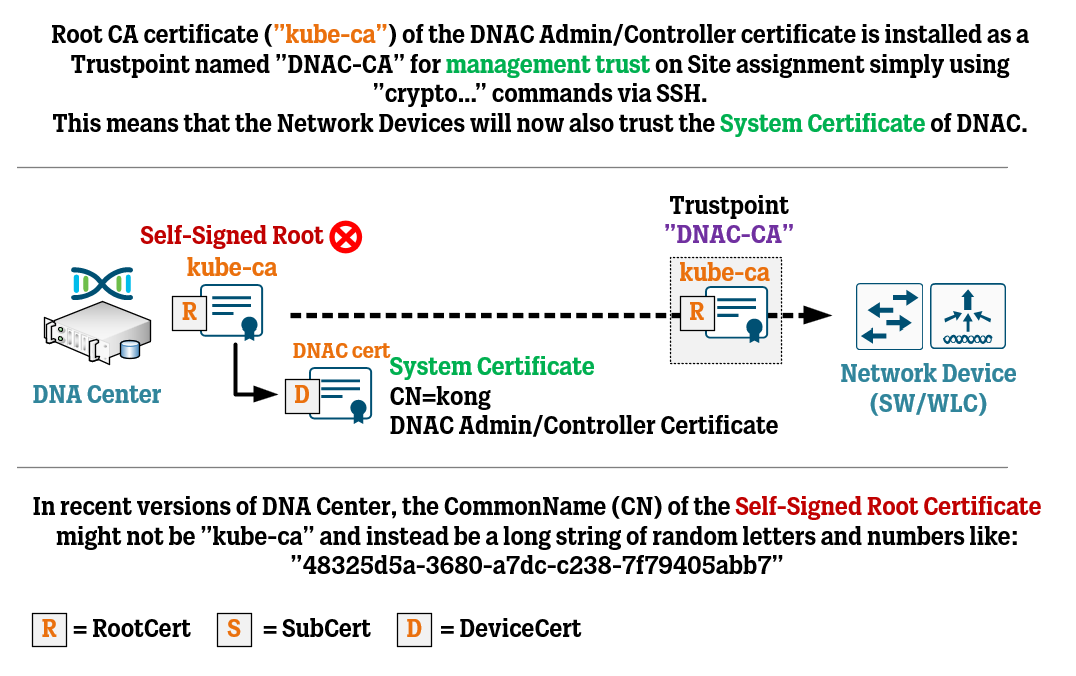
Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI
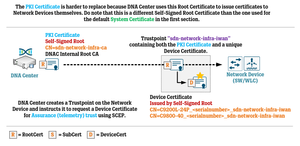
Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI

Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI
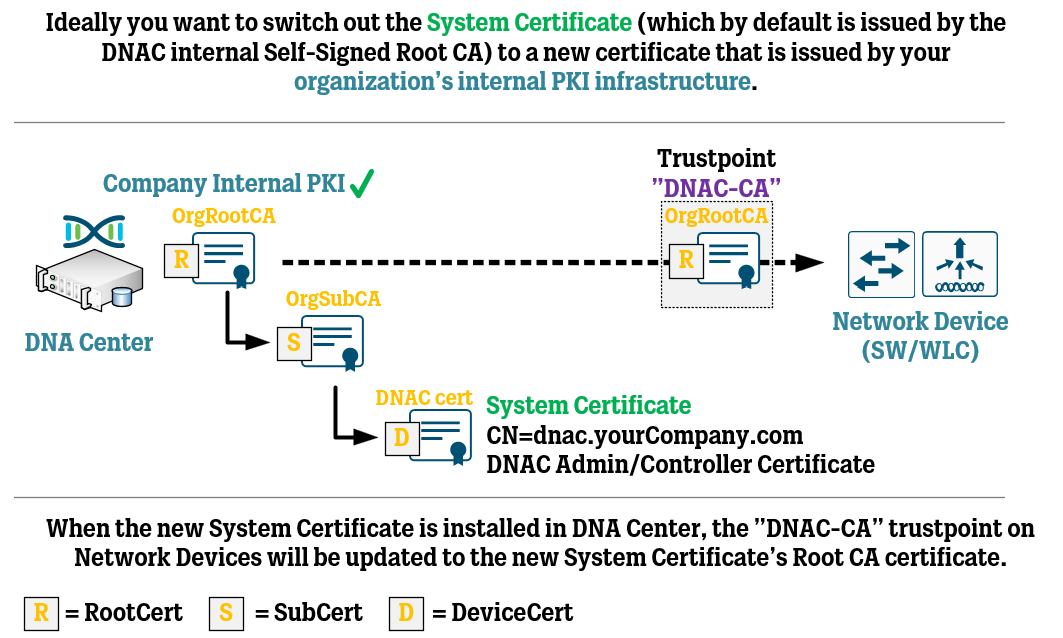
Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI
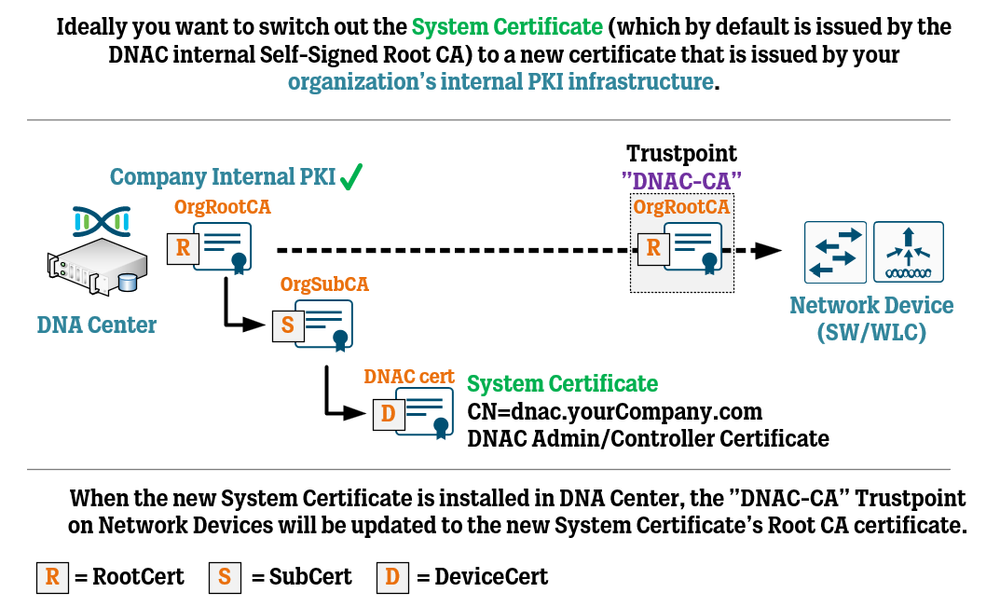
Cisco DNA Center Certificate Management Best Practices WIRES AND WI FI

Best Practices in Certificate Management GlobalSign

Certificate Management Best Practices to Stay Cyber Secure This Holiday

Migheil Du Plessis on LinkedIn: TLS/SSL certificate management Best

PKI and SSL Certificate Management Best Practices Security Boulevard

PKI and SSL Certificate Management Best Practices Keytos

(PDF) Digital Certificate Management Best Practices to Avoid Outages

Certificate Lifecycle Management Best Practices Hashed Out by The SSL

Certificate Lifecycle Management Best Practices Hashed Out by The SSL

Certificate Lifecycle Management Best Practices Hashed Out by The SSL

Top 8 Software Quality Management Best Practices TestEvolve

10 Password Management Best Practices 2025

SSL Certificate Management WebsiteDomain com

SSL Certificate Management WebsiteDomain com

12 Enterprise Encryption Key Management Best Practices Hashed Out by

SSL Certificate Management Best Practices SSL Dragon

Kalyani More on LinkedIn: emCA: The Best Certificate Lifecycle

Code Signing Best Practices: A Guide for Developers DevOps Hashed
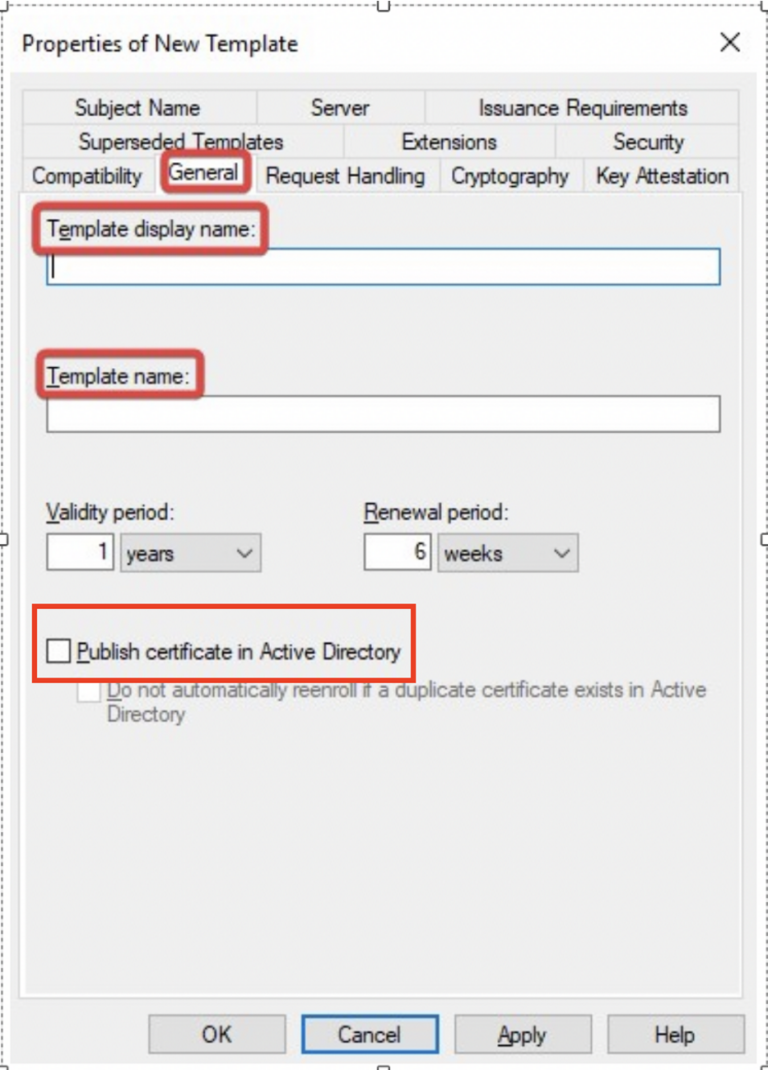
Certutil Request Certificate Template
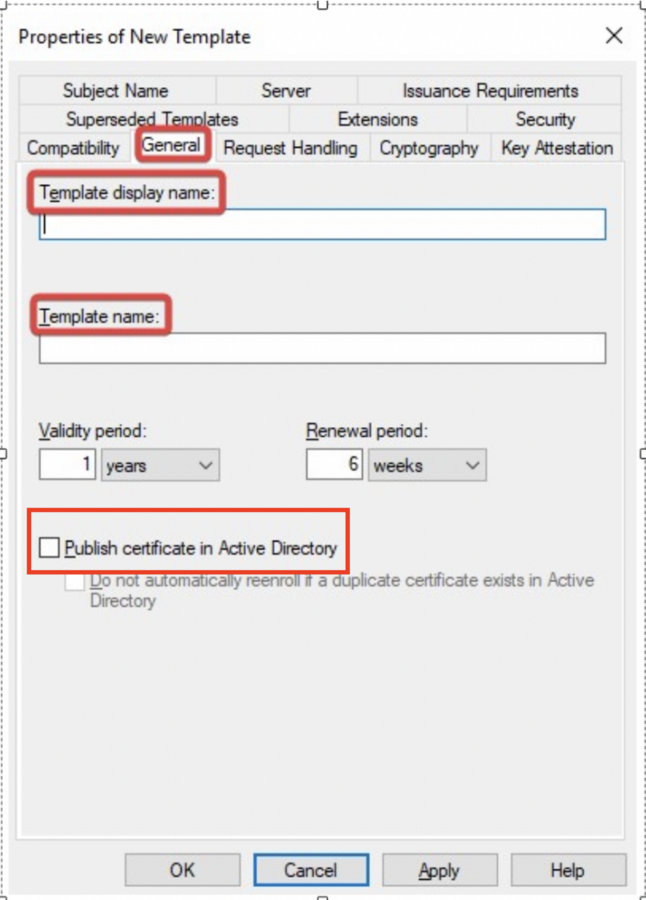
Certutil Request Certificate Template
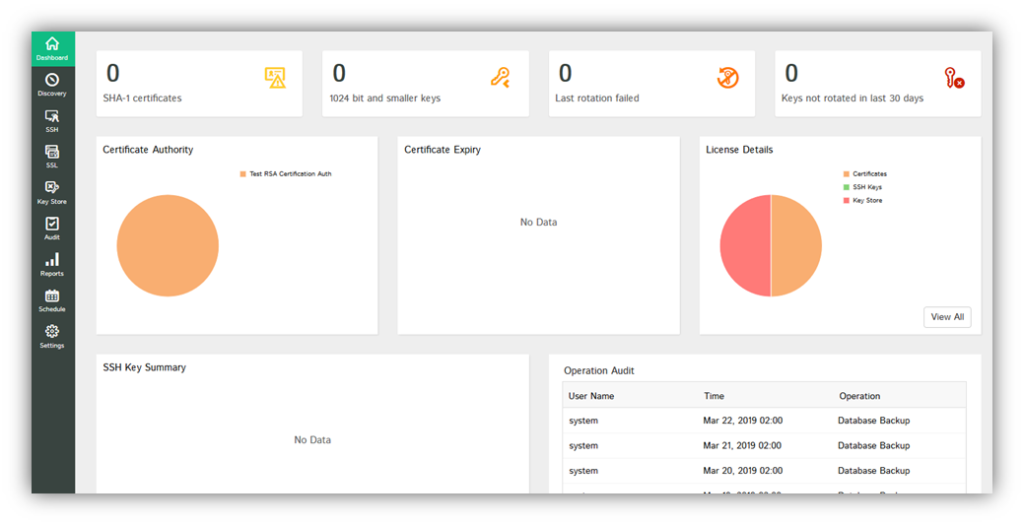
The SSL Store and ManageEngine team up to simplify Certificate

What is OCSP (Online Certificate Status Protocol)? Keytos

What is CAA (Certificate Authority Authorization)? Keytos

What is CAA (Certificate Authority Authorization)? Keytos

Why Automating SSL Certificate Renewal is Vital for Your Organization

How to Deploy a CA in Azure Keytos

How to Migrate Your Microsoft CA to the Cloud Keytos

Best Practices for Certificate Authority (CA) Certificates Renewal

The #PKI and #certificate management best practices that every #CISO

Webinar CertifiCare: Best Practices for Certificate Management (2019

Matter IoT Security: A PKI Checklist for Manufacturers Hashed Out by

Certificate Management Best Practices: Practice Questions Course Hero

The Difference Between Root Certificates and Intermediate Certificates

Learn Exemption Certificate Management best practices with Matthew

Cisco IOS XE NTP Authentication Configuration WIRES AND WI FI

Cloud Security Best Practices Keytos

Cloud Security Best Practices Keytos

What is a Private Certificate Authority? Keytos

X509 Certificates: Definition and Details Keytos

What Is HTTPS? A 5 Minute Overview of What HTTPS Stands For Hashed
.png&w=1080&q=75)
CAA Records 101: Controlling Who Can Issue SSL Certificates for Your

SBOM: An Up Close Look at a Software Bill of Materials Hashed Out by

711652894 Implementation Plan for TechCorp s IAM Platform pptx

Is Email Encrypted? Sometimes Here s How You Can Tell InfoSec Insights

What Is Brand Impersonation? A Look at Mass Brand Impersonation Attacks

Public Certificate Authority vs Private Certificate Authority Keytos
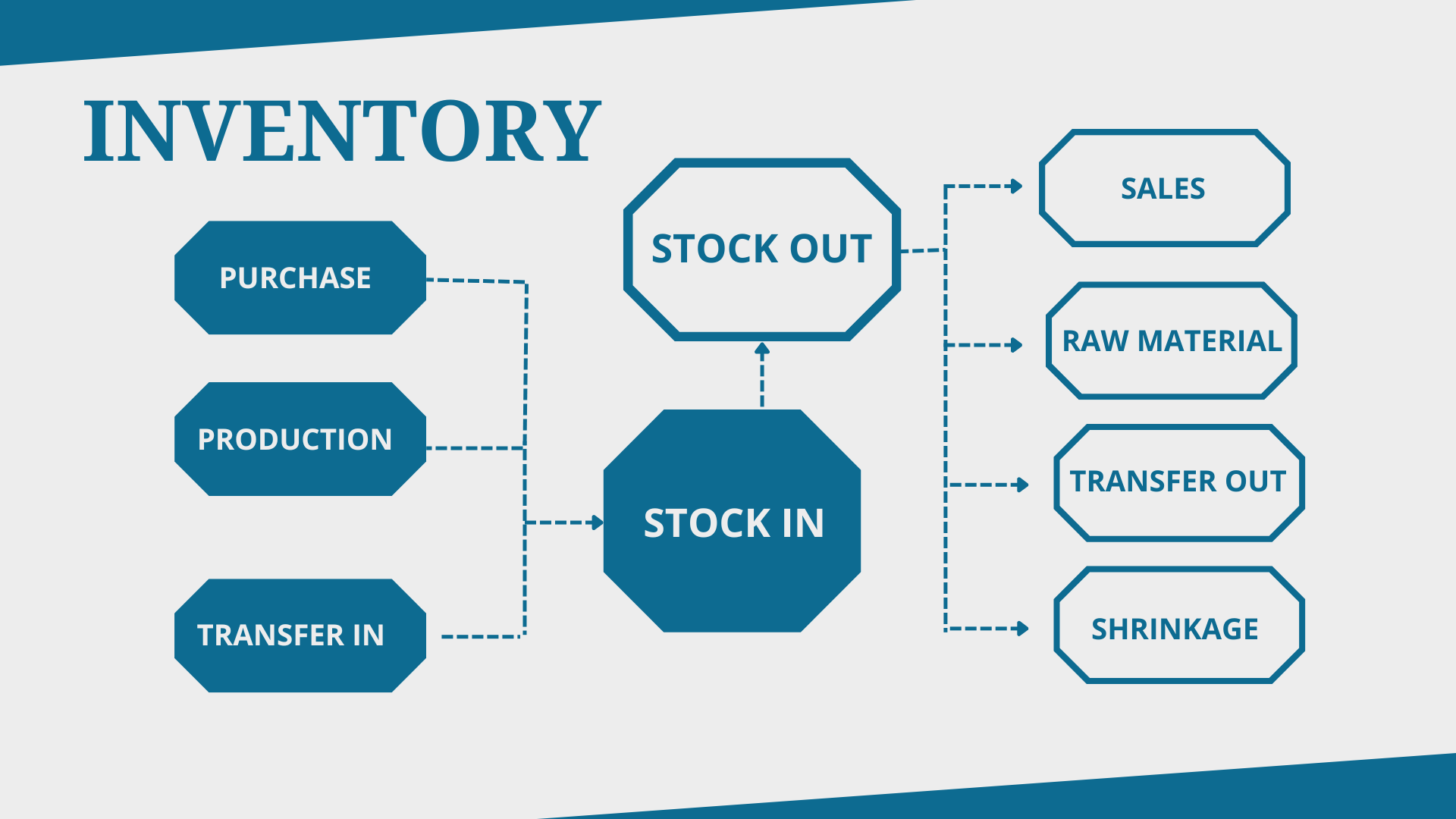
Business Inventory Management: A Comprehensive Guide to Optimizing