Best Threat Hunting Certification
Here are some of the images for Best Threat Hunting Certification that we found in our website database.

Hunting Certification Explore Outdoor Hawaiʻi DLNR
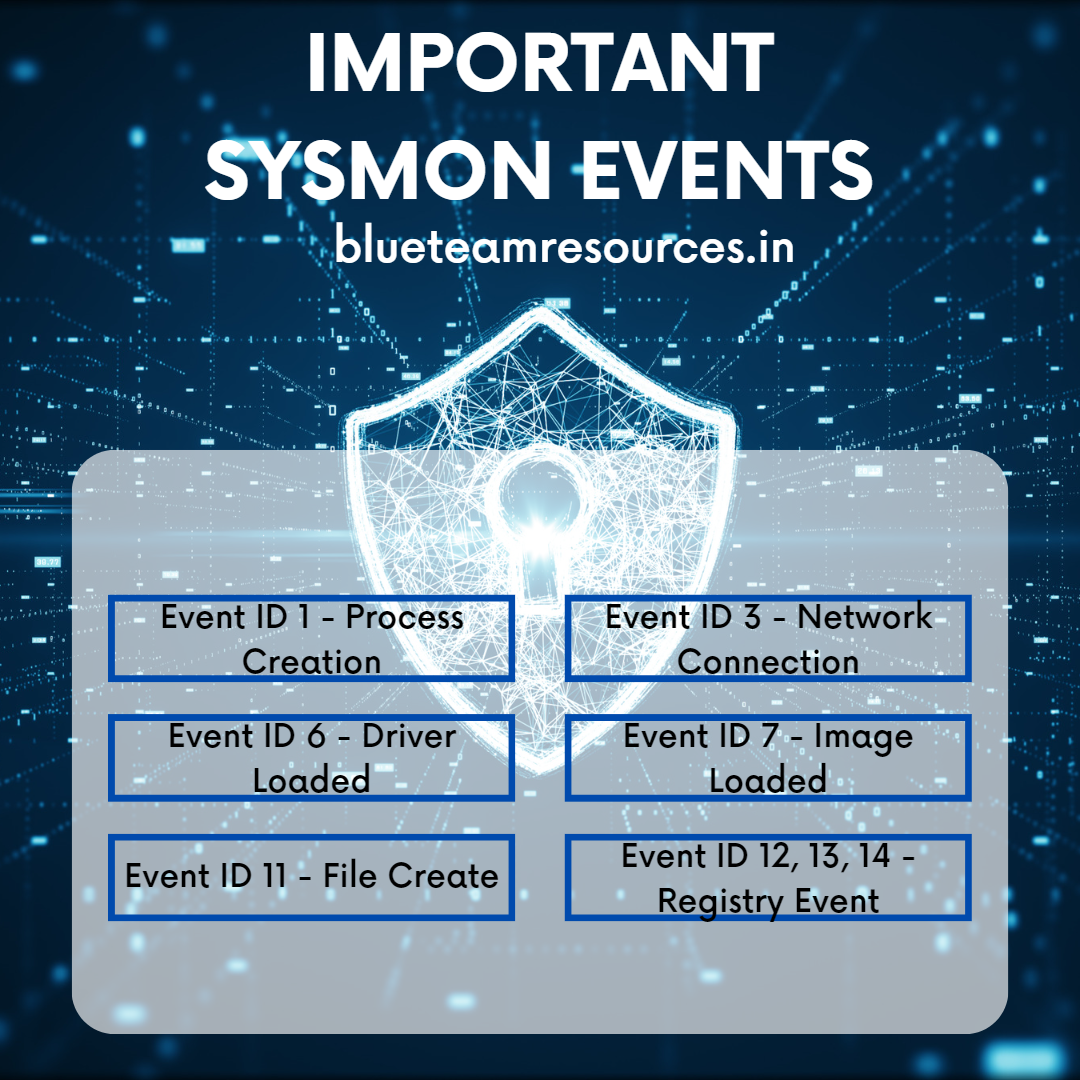
Threat Hunting Blue Team Resources
Threat Hunting Tools Top 3 Types of Threat Hunting Tools with Example

INE Enhances Threat Hunting Certification for Modern Cybersecurity

Threat Hunting Training Certification and Online Learning : r/SOCPrime

Cyber Threat hunting training CTH Training CTH 1191
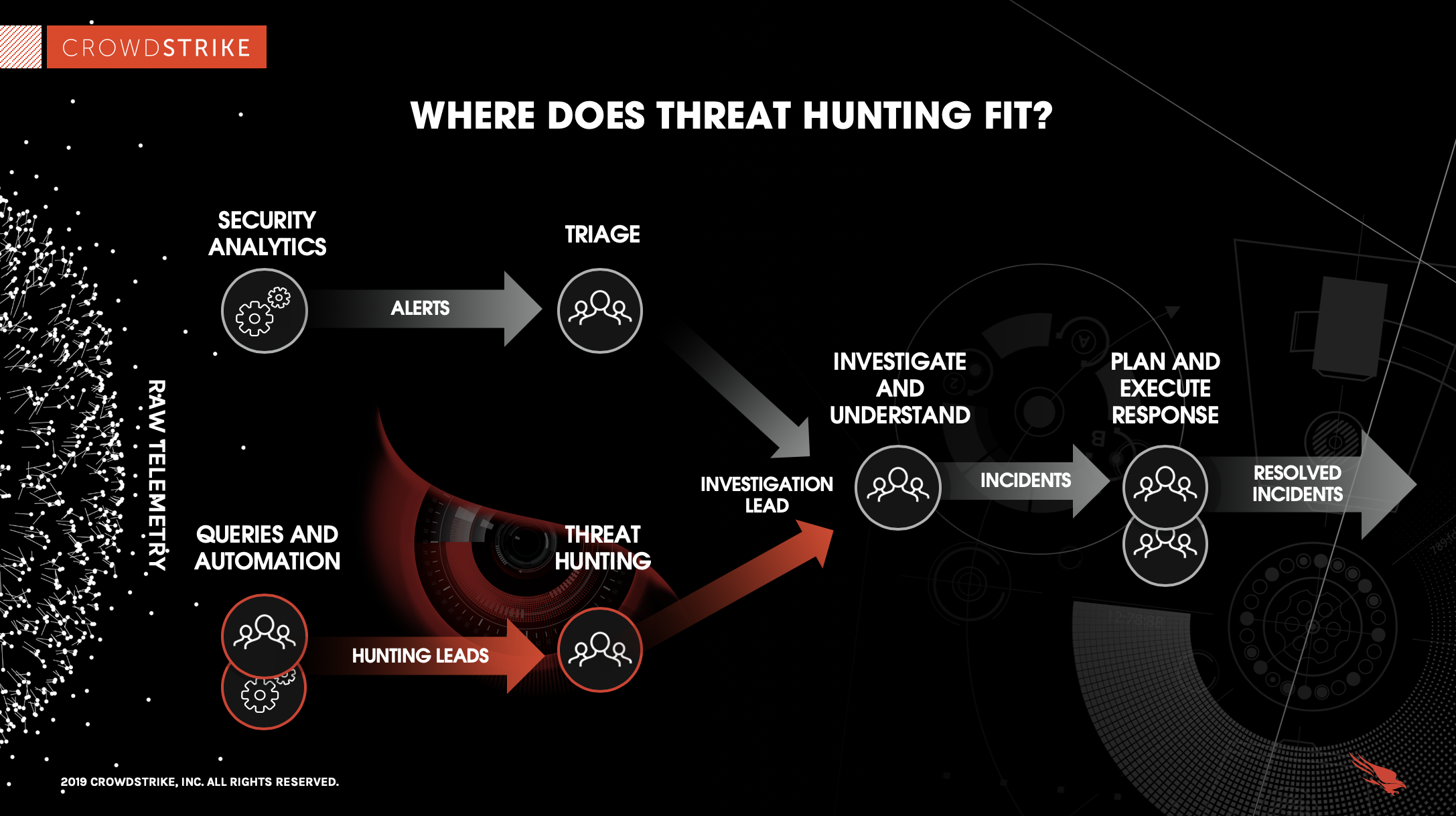
Threat Hunting Tools: Unveiling the Arsenal Against Cyber Threats
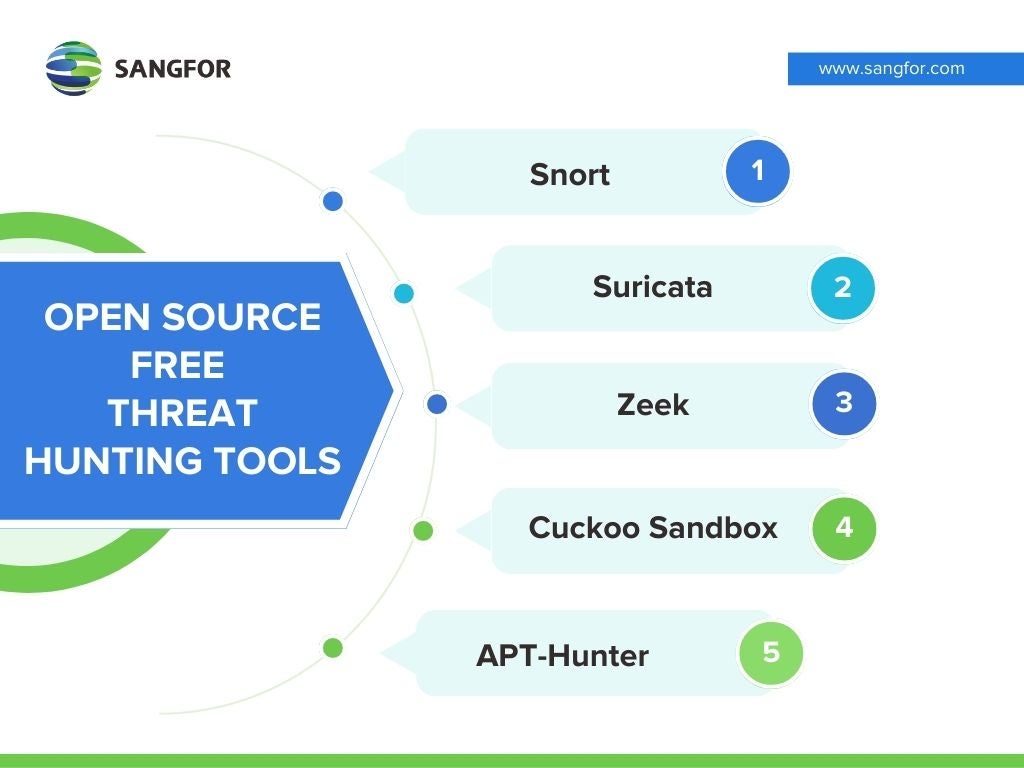
Best Threat Hunting Tools for 2025 Top 5 Open Source Tools

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Cyber Threat Hunting: Types Methodologies Best Practices

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Threat Assessment Certification prntbl concejomunicipaldechinu gov co
(PDF) Trophy hunting certification

Cyber Threat Hunting 101 Guide Methods Tools Techniques Frameworks

Threat Hunting and Detection Engineering Certification Credly

#cyberthreathunting #threatintel #cyberdefense #infosec #

Cyber Threat Hunting Certification Training Boot Camp Infosec

Earned eCTHPv2 Certification from INE Mastered Threat Hunting

Pranav Nair on LinkedIn: #cybersecurity #threathunting

Threat Hunting Using Memory Forensics Course Completion Badge Credly
Threat Hunting for Windows Event Logs by Alican Kiraz Medium

Ohio Online Hunter Education Course Recademics™

CEH Certification Overview PenTesting Org

Just completed a comprehensive course on threat hunting with

Certified Threat Hunting Professional v2 (eCTHPv2) Review by Ismayil

Earned eCTHP certification from INE for advanced threat hunting

Kentucky Hunting License: Everything to Know About the Permit

Best Blue Team Certification: #1 Cybersecurity Career Guide

Threat Detection Response Specialization Certification Credly

How to Prepare for AI Security Certification Practical DevSecOps

OffSec Threat Hunter (OSTH): Everything You Need To Know

Angelo Oliveira PhD on LinkedIn: {Graphs} ∩ {Threat Detection} ⊆

Joud AlSuqair on LinkedIn: eCTHPv2 Certification eLearnSecurity

Learn Bug Bounty Hunting Web Security Testing From Scratch Best

NIOSH Certification ISO 37001:2025 The Updated Standard in Anti

ATT CK Threat Hunting and Detection Engineering Certification • MITRE

SentinelOne Training SentinelOne Administration Threat Hunting

MN Check one thing off your to do list today: Sign up your kid for

Tekikons Academy

GuideM 🔒 2024 is the Year of Security Excellence Make

Pediatric Geriatric Massage Certification Massage Therapy Diploma

I m happy to share that I ve obtained a new certification: Threat

Thrilled to announce that I have successfully completed another